A proxy is a server that lets a client to connect to it and forward its traffic. This enables a certain "layer" of protection by masking your IP. An IP address can be used to learn your location and track you on the Internet, thus eliminating any form of anonymity that you may have.

It's like the H-bomb. In slo-mo, it's stunning. In real life, it's terrifying. The footage below was uploaded by YouTube user NielsBorg, unfortunately lacking in description, but offers the following information via headline: "T90 shot taken by Photron camera at 18000 fps". The T-90 is a brute of a tank, a third-generation battle vehicle used by the Russian Ground Forces and Naval Infantry. The tank contains an autoloader which can carry 22 ready-to-fire rounds, loadable and ready to go in 5-...

Firesheep caused quite a stir when it was released last October, giving both hackers and non-hackers instant access to people's account information when on a public Wi-Fi connection. When logged into an insecure website on the same network as someone with Firesheep, you're giving them access to the cookies that keep you logged in. This is called session hijacking, and grants them easy access to your accounts, like Facebook, Flickr and Twitter. Now, there's an even easier way to do this—a mobi...

It's not uncommon for nature to inspire technology and innovative products. Airplanes were inspired by birds, Velcro by burrs and dog fur, bullet trains by owls and kingfishers, and gecko tape by... well, you can probably figure that one out. And one of the deadliest fish ever to swim the oceans has also influenced its share of merchandise; Sharks made humans faster in the water with Fastswim Suits, and now they've helped make one of the most rugged smartphone cases in the world—SharkEye's Ru...

In the wealthy oil man's world of Arabian camel racing, the tradition of using child jockeys has been replaced with the use of small robo-jockeys in recent years. But after finally ridding the game of the mistreatment of children, the sport is now under scrutiny again. The Dubai police have discovered a new feature illegally added to the torturous, whip-endowed robots: hidden stun guns.

For travelers on-the-go, or penny pinchers who like to surf the web for free in public places, there are necessary precautions one must take when accessing sensitive information over a public WiFi connection. For advice on doing this safely, check out Glenn Fleishmann'sguide to staying protecting your private information. Fleishmann outlines how to:
Welcome to Photography Contests World! The purpose of this world is two-fold. First, it will serve as a directory with featured listings of all types of current photography contests. If you have ever tried to search for a photography contest to enter, then you are aware of how many contests are scattered all over the internet. Photography Contests World will strive to bring you information on as many contests possible in one central location, beginning with mostly USA and international contes...

First Things First Before you can begin to work on a damaged panel, you must determine what type of material that you are working on. For instance, the panel may be mild steel, high strength steel, aluminum, plastic, sheet molded compound, or a number of other types of material.

PopSci's Gray Matter demonstrates again and again what the layman should absolutely Not Try at Home. Which is precisely what makes Gray's experiments so fun. Remember when the mad scientist fully submerged his hand in liquid nitrogen? Today's demonstration also plays with what is (quite reasonably) assumed to be extremely dangerous and painful: torching the human hand.

Gain control over your files online with Windows Live SkyDrive 2011, just one of the many new features of the newly released Windows Live Essentials 2011. You get 25GB of free online storage and tons of new features. You can store tons of documents, access all your important files and share the plethora of pictures you've amassed, all within SkyDrive.

IslandGirlzJewelry over on Etsy has transformed ordinary SCRABBLE tiles into elaborate jewelery that both SCRABBLE fans and Avatar fans will appreciate. If you're the crafty type, I'm sure you could use this as an example to create your own earrings or bracelets using some old SCRABBLE tiles. If not, you could always just buy theirs. But it seems like all the fun is in doing it yourself!

The rush to secure face masks and hand sanitizers in March left many Americans concerned for their safety. With an expected second wave this fall, consider stocking up on PPE now.

Turning your abode into a haunted house of horror for Halloween takes a lot of time and work. Finding ways to build props on your own can save you some money that's better spent elsewhere.

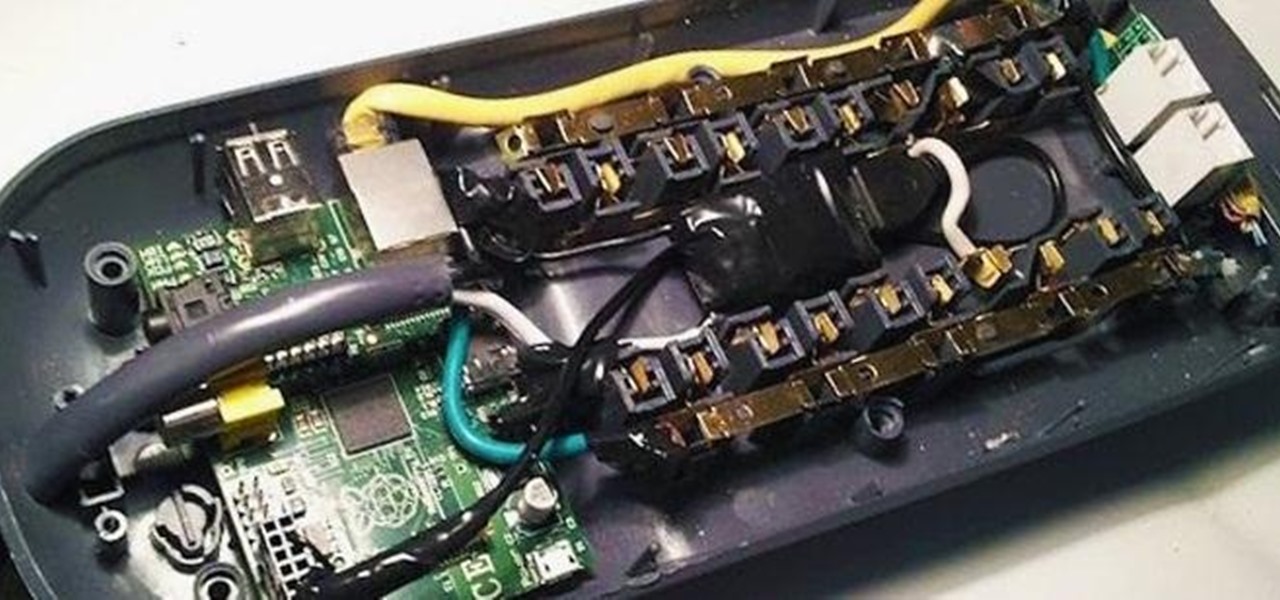
Remember the Power Pwn, the clever little hacking tool disguised as a power strip? It's great in theory, but with a $1,295 price tag, it definitely doesn't fit into most people's budgets.

When you have expensive camera equipment, the last thing you want to do is just throw it all in a bag without any kind of protection. If you don't want to buy a separate bag, you can always use an insert, but they can get pretty pricey, too.

Have you ever wondered how to create an invisible folder? I mean an invisible folder, not a hidden folder. Nowadays, we are facing lots and lots of problems requiring us to keep our data safe and secure. There are millions of hackers all around the world that are trying to steal our information whenever we get onto the internet. Even some of our friends are trying to lay their hands on our personal and confidential information.

Been hacked once? Twice? Maybe more? You thought abc123 was the only password that is both 6 characters wide and easy to remember? I have some suggestions in store for you. Just read on...

CRISIS MANAGEMENT PLAN A FORM TO FILL OUT FOR WHEN CRISES ENTER YOUR WORLD

Check out this discussion on ouija boards and spirit boards including how to cleanse and seal them with protection. Cleanse and seal your ouija board or spirit board.

Watch this "Grease On Your Hands" video tutorial from the Washington Post to see how to change the engine oil in your car properly.

Watch this "Grease On Your Hands" video tutorial from the Washington Post to see how to check and charge car air conditioner properly.

Watch this "Grease On Your Hands" video tutorial from the Washington Post to see how to change your dead car battery properly.

As you may have seen in your city or town, red light cameras are on the rise in the United States. In many instances in my area, these cameras have sprung up seemingly out of no-where, and mostly without any reason. Over use of these systems can make privacy (even on the road) a fleeting possibility.

Representative Henry A. Waxman is in charge of California’s 30th Congressional district. He is part of the House Energy and Commerce Committee. Ever since he began his career in the government business, he has been involved with health and environmental issues. He represents cities such as Santa Monica, Beverly Hills, Agoura Hills, Calabasas, Hidden Hills, Malibu, Westlake Village and West Hollywood, as well as such areas of Los Angeles as Beverly-Fairfax, Pacific Palisades, Brentwood, Beverl...

Always falling asleep behind the wheel? The National Highway Traffic Safety Administration (NHTSA) estimates that there are over 56,000 sleep-related accidents each year, resulting in 40,000 injuries and 1,550 deaths annually in the United States. Don't want to be a statistic? Then you may want to try out ASP Technology's mobile application which aims to keep you awake when you're fatigued on the road.

First off, let's explain the story that inspired the phot I'm using for the post. Friday night, restaurant gig at Vallartas Mexican Restaurant in Lutz/Land O' Lakes, and I was making balloons for all the children throughout the evening. As I'm about halfway through my shift, I approach a table with two little girls (and their parents). One girl was about 6 with straight blond hair and the second girl, like pictured, had the most adorable little blond ringlets bouncing around her face as she g...

This German video is amazing. A joyously analog interpretation and deconstruction of the digital gaming experience. Malte Jehmlich is as primitive and inspiring as the the Vanuatu natives who devoted themselves to cargo worship after World War II!

Gather Supplies Ready to make the best Scrabble tile pendant possible? This easy tutorial will show you how to make your own custom necklace out of a Scrabble® tile.

Have a flat tire on your bicycle? No problem... let High Altitude 2U help you out with their video tutorial.

As you progress in the world of information security, you'll find yourself in situations where data protection is paramount. No doubt you will have files to hide and secrets to share, so I'm going to show you how to use the GNU Privacy Guard (GnuPG or GPG for short) to encrypt and decrypt as you need. GPG is a great open-source version of Pretty Good Privacy (PGP), a similar application used for encryption, but licensing and patent problems led to the development of GPG in its wake.

It's mid-January and some of you happy tax-paying citizens have already started receiving your W-4s and 1099s in the mail. But before you start filling out your 2010 Federal Tax Return, make sure you're hip to all the tax tricks in 2011. You could end up saving some money!

As many of you know Windows is not the most secure Operating System in the world, but then again no OS is really secure if the user doesn't know how to protect themselves. Later I will show you how to lower the risk even more on your (the user's) end.

To those who may not know about this, the UK high court has ruled that all UK based ISP's are to begin blocking Piratebay. This comes in retaliation to Piratebay's action to take down all torrents and provide only magnet links to the pirated content - a move which releases TPB from liability should they be once more accused of hosting the actual content.

Though under a lot of the average consumer's radar, the CISPA is now making rounds again with a coalition of advocacy rights groups. The act, known as the Cyber Intelligence Sharing and Protection Act, forces companies to ignore existing privacy laws and share information with the Federal Government. This short article will bring you up to date on this bill. The CISPA is another bill 'designed' to help prevent thefts and prevent them in cyberspace. But again, like all the previous bill before...

Here's a delicious Byte of information for you. A proof of concept program on Linux was coded to exploit a known bug in how the Linux Kernel (versions 2.6.39+) handles permissions for the

Keyloggers are a must-have tool in your arsenal. Hardware keyloggers have the advantage of being undetectable through anti-virus or other protection programs. They also capture keystrokes before the OS even boots up, so they are pretty handy tools.

With the globally rampant use of such social networking platforms as Facebook, Twitter, and Foursquare, the issue of privacy has become a prevalent concern for many. And for good reason—there's the violation of Facebook employing user names in ads, the Etsy slip-up, and of course, the everyman act of recklessly sharing too much information via common social media outlets: a night of drinking results in morning after embarrassment, or worst case scenario, sloppy Facebook posts and tweets resul...

Enjoy rolling around at night in the sleek luster of silk? Also afraid of a mobster finding out you're rolling around with his cousin's wife? Solution: bullet-proof silk sheets. All you need is the strongest biomaterial ever found--Darwin's bark spider silk. So, grab a loom and start weaving.

There can be areas of preparation you may not have anticipated before you start your project of installing your laminate flooring.