By Ethical Traveler As the world becomes ever more interconnected, being an ethical traveler becomes both easier and more urgent. Travelers today have access to far more information than we did even 10 years ago. We can observe–almost in real time–the impact that smart or selfish choices, by governments and individuals, have on rainforests and reefs, cultures and communities.

This past Sunday, a group called Gnosis launched a massive hacker attack on Gawker media, one of the web's most popular blog networks (Lifehacker, Gizmodo, Jezebel, io9, Jalopnik, Kotaku, Deadspin and Fleshbot). 1.3 million registered users' passwords were compromised, and 188,279 of them were decoded and made public. The biggest takeaway? Many Gawker denizens use downright dumb passwords. (Guess they didn't see their own Lifehacker's story on avoiding such a thing.)

National Geographic recently published a retrospective of the lovely Jane Goodall, one of the world's most accomplished conservationists. The feature includes every image of Goodall to ever appear in the magazine for the past fifty years.

Picked up Metro 2033 from the Steam Sale. Wow is it pretty. At 1080p with DX11 and gorgeously detailed, it's hard to not stop and stare at every single thing! I wish there was a way to somehow convey this feeling..
Hello again ! This is the second part to Fingers from a Hand Analysis perspective.Where as the first Video just covers basic introductions to the Fingers, this part two Video takes things a little bit further and examines ......Finger Shape ;- Length suggesting mental speed, Methodical or Speedy thinker ?Finger Width ;- Suggesting which level a persons interests may lay, Mental or Practical realms ?Finger Prints ;- Amazingly interesting area to explore , Fingerprints do not change.. They star...

Earlier this month, the U.S. Army agreed to drop quite a big chunk of change ($461m to be exact) on 423 M1117 Guardian Armored Security Vehicles (ASV), made by Textron Systems.

Want to get professional looking results right at home? You can easily do it yourself. Your nails don't have to suffer anymore. A specialist at Sally Hansen gives you expert video advice on doing a salon perfect manicure right at home. Don't waste money at the salon, do it yourself!

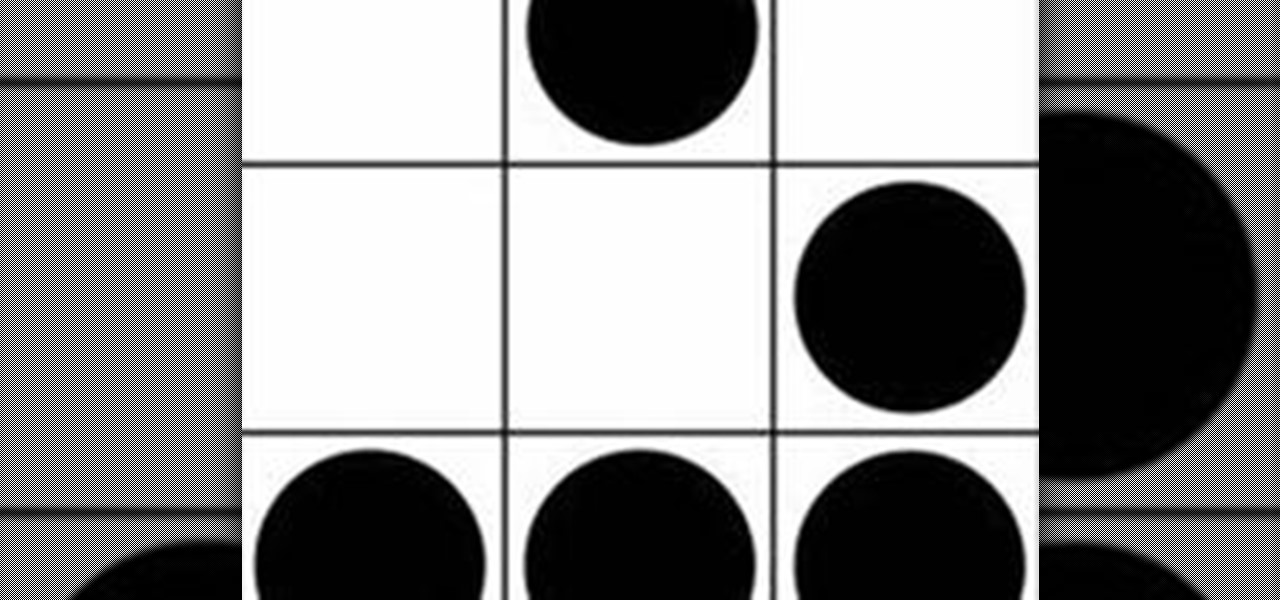
This method is easy, intuitive and requires very little math. You will need:

Social Profile Change the privacy settings on your social profile (Facebook, MySpace, Friendster, Twitter, etc.) so that the following information can't be found by a random person who you didn't accept you as a friend:

We've all been there before: We're in a hurry to get somewhere (often in bad weather), so we get in the car, turn the key in the ignition and.....WHUH! WHUH! WHUH! The darned battery is dead! After a stream of choice expletives (that is, if you're anything like me....;o)), we open the trunk and take out the jumper cables - but what if we don't know how to use them? Even if we do, we can often forget such things in crisis situations when we're pressed for time.

Etching your own circuit boards is tons of fun, but etching requires strong chemicals to dissolve the copper plating on blank circuit boards. The normal ferric chloride solution works well, but can be expensive and leaves permanent stains. Luckily, we can whip up our own etchant at home with everyday chemicals! Better yet, our new etchant will turn an eerie green color rather than the dull brown of ferric chloride.

In America, football has become religion. And that religion has blossomed into an unstoppable juggernaut, which has rocked the very foundations of both television and business. In an era where fragmentation has savaged traditional network television, the NFL's Nielsen ratings (both the season games and the Superbowl) have defied gravity and actually increased.
DRUM! Magazine — the leading magazine for drummers and percussionists worldwide — has announced the biggest drumming event ever to take place in Northern California. On Friday, August 13, drummers will descend on the San Jose Repertory Theatre in the heart of Silicon Valley to witness three of the world’s most exciting drummers — extreme drumming sensation Marco Minnemann, Tower Of Power funk master David Garibaldi, and former Mars Volta wunderkind Thomas Pridgen — for an evening of mind-blow...

We are embarking upon a new year. As usual, some of us will make "resolutions." There isn't anything wrong with setting goals for the year. It's actually a good idea. It may help focus the energy we bring to life.

Super Mario Brothers! No, wait... Super Meat Boy! Yep, that's right. Meat. As in "cube" steak. As in a square piece of beef with eyes and a shitty grin, who just happens to be in love with a band-aid. I have no idea why. And no matter how shocked you are to see your dinner on your screen, it doesn't change the fact that this platform game is AWESOME!

In this article, I'll show you how to make a high-powered, long-range, air-powered rocket gun. This launcher is based on a sprinkler valve, a modified propane tank, and a few other components. Though not hard to make, this device is VERY dangerous! The rocket can seriously harm, if not kill any living thing it's shot at. Here's a video of it in action, quite an accurate shot by my friend Chris... Parts

Taking apart batteries is one of those things that every adult you've ever known has warned you against. Today, we break the taboo and dive into a lithium battery. Lithium has some pretty cool properties—it burns instantly in water and glows blindly bright under flame. And with just one AA battery, you can make a blinding light beam inspiring supernatural awe in all dictatorial adults who doubted you.

I'm back with the third part to my laser weapon series (see part one and two), and I'll be explaining the function, application, and potential of semiconductor lasers, aka laser diodes.

Did you know there is hidden data in your digital pictures? Well, there is, and that data might be a security risk to you. Think back at all of those pictures you're in and are connected with. I'm sure some of those you'd like to distance yourself from. And surely you wouldn't mind checking out the metadata in a few of those images. In this article, we'll be going over how to do just that.

Today's tutorial will teach you how to erase data permanently so that it cannot be recovered. Many believe that having a file shredder on the computer means you are up to no good.

Friday's Community Byte was weird. The intent was to do a HackThisSite mission, but upon time to begin, everyone in there was programming without my assistance, with the help of Sol Gates. This is great! It's really awesome that everyone enjoys programming that much and will make the effort to learn even when I am not present. So, a tip of my hat to Mr. Sol Gates and the rest of you fine people.

Cross-Site Request Forgery (CSRF, pronounce "sea-surf") is a common web exploit. However, for unknown reasons it's not used very often. It plays on a given website's trust in a web browser by executing another website's form action, for example, sending money to another person. It's usually placed in abnormal places like HTML image tags.

It's one of the greatest fears among parents and politicians the world over—video game violence spilling out into reality. The shooting at Columbine and the more recent tragedy in Utøya, Norway have touched deep nerves in Western consciousness. And that's why there's a giant pink, juggling elephant in the corner of every production meeting and press conference for each shooter game that comes out.

Even with Apple's forthcoming iOS 5 updates to its default camera application, those upcoming features can't match what already exists in Global Delight's Camera Plus Pro. For $1.99, Camera Plus Pro provides users with over 100 tools for every part of the picture taking process, including video recording. It works with all versions of the iPhone, iPod touch, and iPad 2 with iOS 4.1 or the later update. Let's examine what it can do, and why you will want to replace Apple's default camera with ...

If you want to install laminate flooring on your stairs I would recommend that you do a lot of research and find the information you will need to do it correctly. Installing laminate flooring on stairs can be tedious and time consuming and is a lot different than installing laminate flooring on a floor.

While a lot of internet threats are rather over-hyped, there are some serious things to be cautious of when going online. Probably the biggest risk to the average internet user is malicious software. Commonly knows as "malware," this term refers to any program that exists solely to do harm. This may include damaging your computer or accessing your data without you knowing. Viruses, trojans, and spyware are all forms of malware. Now, malware can seriously mess up your system, and the idea of s...

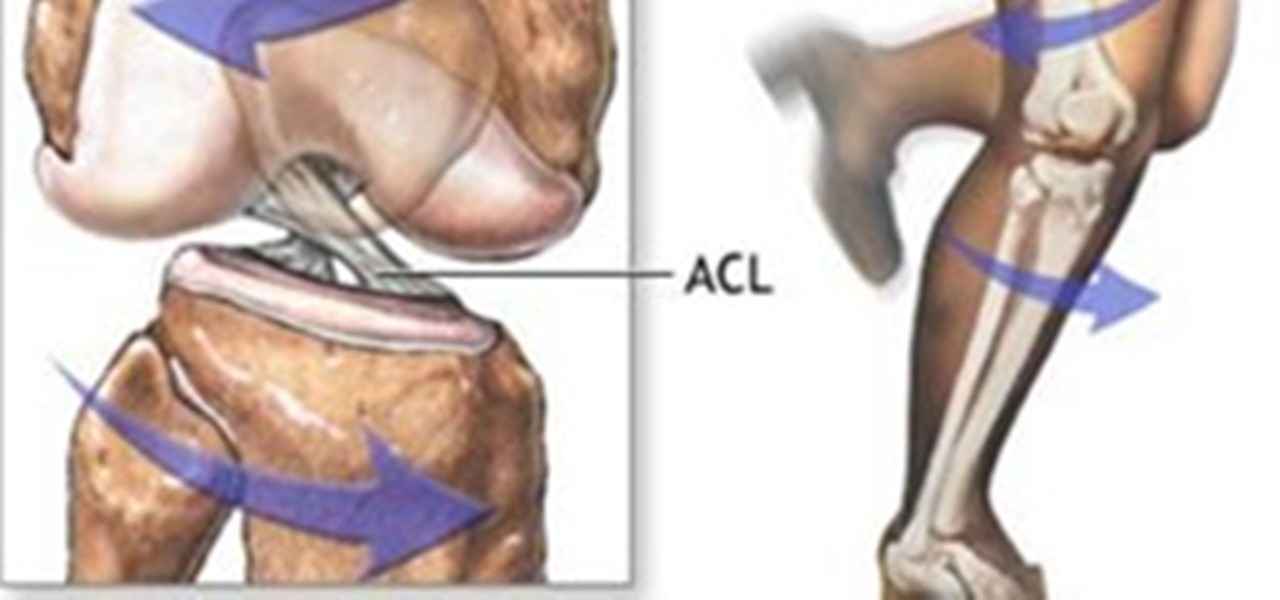
The sudden deceleration, shifting in the knee, popping sound and screaming from the intense pain that immediately follows is becoming increasingly common among our young athletes. Those who

The sudden deceleration, shifting in the knee, popping sound and screaming from the intense pain that immediately follows is becoming increasingly common among our young athletes. Those who have witnessed or suffered a torn anterior cruciate ligament (ACL) are familiar with the pain, surgery and intense 6 to 8 month rehabilitation that accompanies the injury, not to mention the disappointment of ending a season. Nationwide, this will occur more than 500,000 times this year, and female athlete...

So I have Followed since the first CKY, I love the work you guys have created over these many years, I have wanted to meet and kick it with the crew and just have a good time and here is my opportunity.

Wireless networks. Nowadays, everyone uses 'em, but most don't secure 'em. On average, I can drive up and down any block in my city and find at least one or two open or semi-open networks on any given day. With some changed MAC addresses for good measure, an attacker can use your network as a spring board for who knows what. When the police come a few days after, they are coming to your door—and not to talk about how nice your lawn is. Don't be that guy.

I want to write this article because in my childhood, I had experienced internet stalking which ultimately ended in physical stalking which then lead to several attempted abductions. I have now learned how to use the internet safely, who to communicate with and I've learned how stalkers work.

Now, I know what you're thinking... "I need an extra sexy coffee table that is like no other."

Just a couple Saturday's ago, we were blessed with the Supermoon, where the moon was at perigee with our planet, creating a larger than usual Moon for us here on Earth. Now, we've got another spectacular show in the skies coming up, only this one isn't at night. There will be an annular solar eclipse on Sunday, May 20th!

As hard as you try to protect your valuable information with strong passwords and anti-doxing measures, there's nothing you can really do when someone else gives up your goods. And that is the case with the recent Global Payments breach.

As a web developer, I often read articles about hackers (from the lowly to the knowledgeable) infiltrating websites via the dreaded 'SQL Injection' method and completely taking control, changing, gaining access, or destroying the owner's data. As a fellow web developer, I'm sure you want to know how to protect against it. Well, here it is! In this article, you will find out what SQL Injection is, what you can do to protect against it, and additional recommendations that are easy to do and onl...

In my second article of the laser weapon series (see the first part here on CO2 lasers), I'll be expanding on the potential of pulsed lasers.

There are so many hackers around these days, and they are becoming very smart. So smart that they have successfully taken down many government websites. The most recent attack was on the Department of Justice (DOJ). To read about the history of these hackers, check out Wikipedia.

This is Part II in the Lockdown: The InfoSecurity Guide To Securing Your Computer series. Before beginning, check out Part I. This article will cover using alternate software to increase your security and will provide you with some information about websites and programs that test a computer's security. It will also guide you to software you can install or follow so you know what programs need to be updated on the computer. Lastly, I will talk about some features that should be disabled when ...

Previously, we talked about how to secure Firefox. Today, we will talk about securing a Chromium based Browser. Why? Because Chrome recently beat Firefox in holding more customers.

Back in the eighties, I used to hate television commercials, but I eventually got used to them. Had to, in order to enjoy my favorite shows. Then, the increasing number of billboard ads annoyed me in the nineties. They followed me everywhere I went—no escape—persuading me to buy the newest whatever. It seemed like Big Brotherism—like They Live. But, I got used to it. When I finally entered the digital age and became a web addict, I was peeved at the constant sight of online ads everywhere I v...