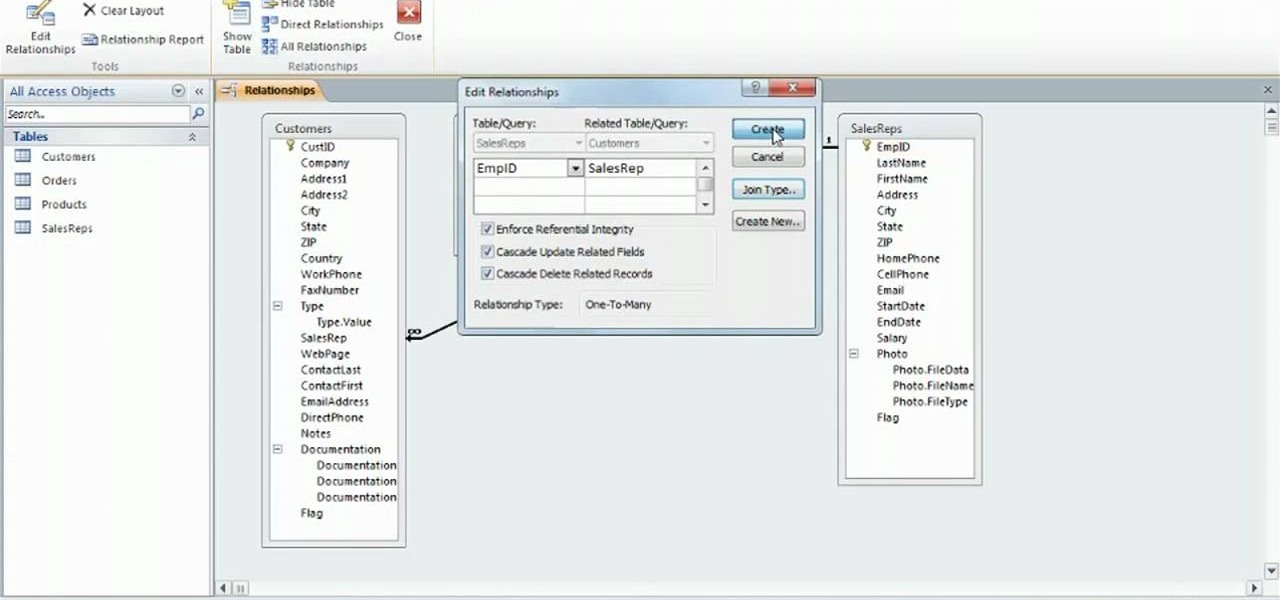
Learn how to use create relationships and enforce referential integrity when working in Microsoft Access 2010. Whether you're new to Microsoft's popular database management application or a seasoned MS Office professional just looking to better acquaint yourself with the Access 2010 workflow, you're sure to be well served by this video tutorial. For more information, and to get started creating and managing relationships within Access, watch this free video guide.

People put so much drama in their relationships sometimes. Well, for all of you out there who are enmeshed in a situation that just does not fit for the life you've always dreamed of having, this how-to video will help you get the kinks out of your thinker so that you can do what's best for both of you and end it. Remember, being in love with someone doesn't mean you're right for each other.

Fixing your Aviso Carbon Fiber surfboard is just as easy as fixing your old poly surfboard. You can remove the drain plug. Dry it out completely. There is no foam to rot or wood to break. If fixed properly Aviso surfboards will keep all of there integrity. This addresses a puncture and a cracked and severely damaged rail.

This tutorial was written with Windows 7 in mind, but the principle applies to all versions starting from 7.
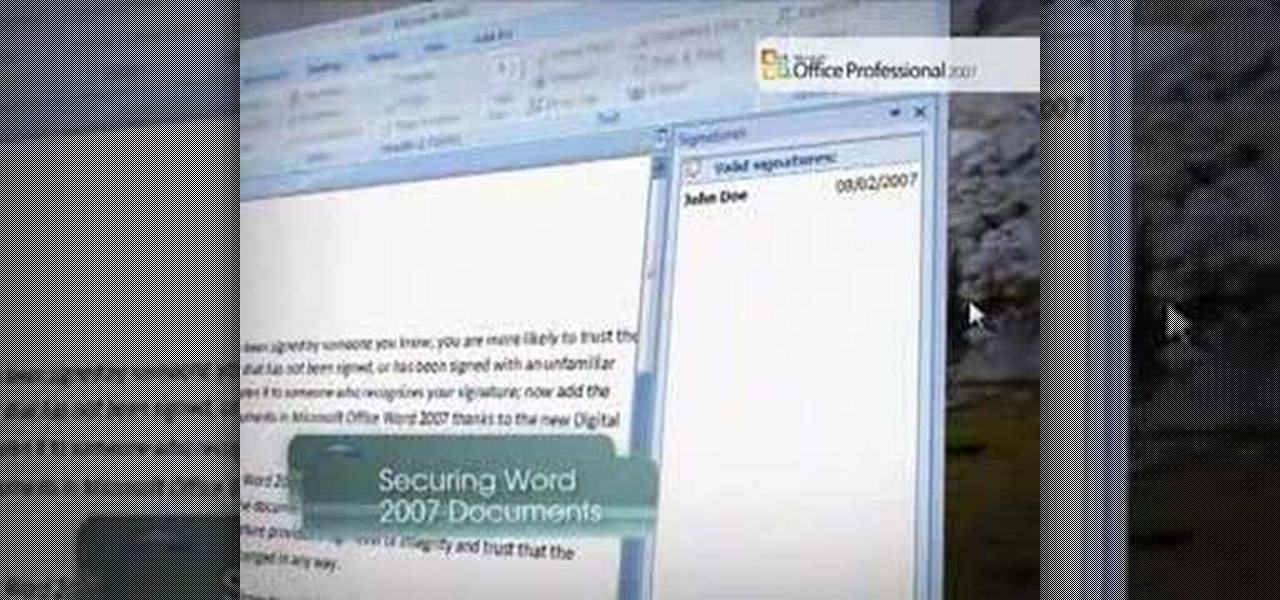
Securing Microsoft Office Word 2007 documents with Digital Signatures - When you receive a document that has been signed by someone you know, you are more likely to trust the contents than those of a document that has not been signed, or has been signed with an unfamiliar signature. Signing a document validates it to someone who recognizes your signature, now add the same degree of integrity to your documents in Microsoft Office Word 2007 thanks to the new Digital Signatures feature. For more...
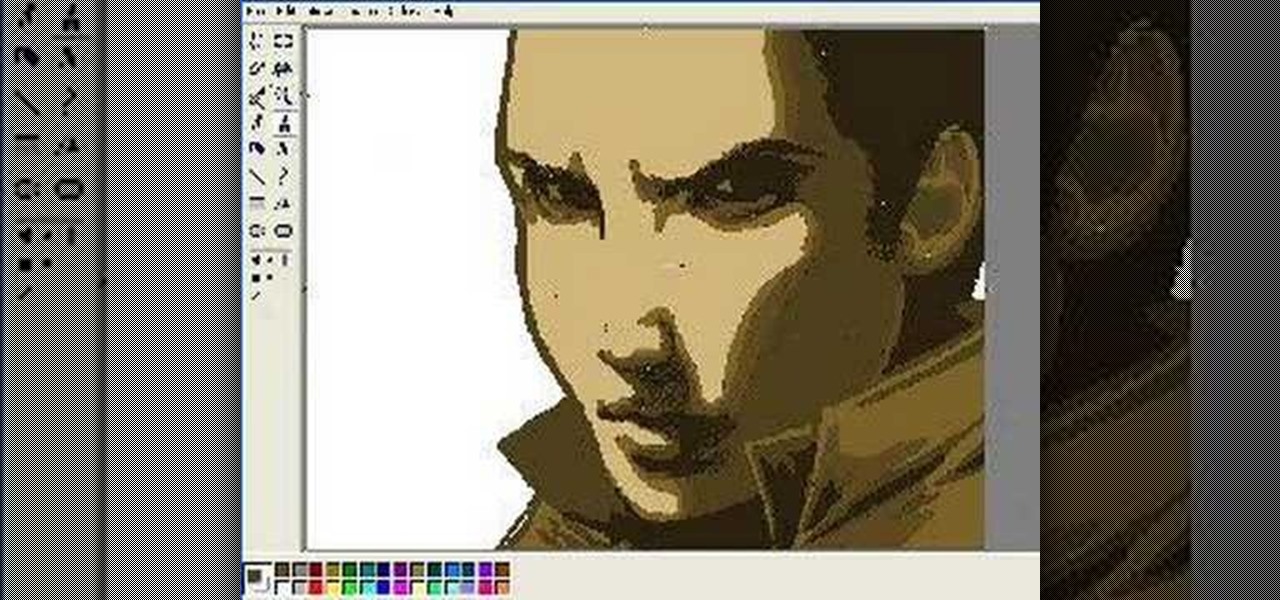
How to draw a face in MS Paint. The video is obviously made by a professional, it shows a sped up replay of a man using MS Paint to draw a very well done face. He starts with the basic outlines, then moves into coloration and shading. Notice all of the shading is done in unison and correlates with a particular direction that remains the same with all shading properties. Also take note of the fact, that the colors and lines are blending together, that the detail isn't as sharp as a high resolu...

Check out this video tutorial to see how to tansfer blood specimens with the BD Blood Transfer Device.

Maybe one of the hardest jobs you can do around the house is cleaning the gutters. When cleaning the gutters by hand, you have to constantly keep moving the ladder to get to the various spots of the gutter which contain a mess. If not done properly, the gutters can get clogged, which will not help the appeal of your home. This video explains a simple and easy way to clean the hassle-prone gutters. The powerful leaf blower makes cleaning the gutters simple and easy. Just make sure to keep your...

These short videos show how to tie a 6 Lead by 7 Bight Turks Head on the Turks Head Tool. These videos introduce the Turks Head Tool, the Turks Head Cookbook recipe format, and some basic methods that may be used to tie Turks head knots.

Welcome back, my aspiring hackers and those who want to catch my aspiring hackers! As most of you know, this series on digital forensics is inspired by the motivation to keep all of you all out of custody. The more you know about the techniques used by law enforcement and forensic investigators, the better you can evade them.

Hello people again, I wrote my last post about crypto about 10 months ago, now I will introduce something not fresh for the science, but fresh for the people who wants to learn. In my http://null-byte.wonderhowto.com/forum/cryptography-0161538/ post of crypto concepts, there is just basics, today we will see something that targets wide concepts like Symmetric crypto, Public Key Cryptography, Hashing, Keys etc...

Welcome back, my rookie hackers! As hackers, we are often faced with the hurdle of cryptography and encryption. In some cases, we use it to hide our actions and messages. Many applications and protocols use encryption to maintain confidentiality and integrity of data. To be able to crack passwords and encrypted protocols such as SSL and wireless, you need to at least be familiar with the concepts and terminology of cryptography and encryption.

We need to take our privacy and security much more seriously. Whether it's malware-infected apps or the mishandling of our data by companies like Facebook, there are threats all around us in this digital world. Fortunately, some smartphones are simply designed to protect us better.

If you haven't read the last article, feel free to stop by and give it a read, but abstaining from reading it will not, for the most part, be detrimental to your understanding.

It seems like every day now that we see a new headline on a cyber security breach. These headlines usually involve millions of records being stolen from some large financial institution or retailer. What doesn't reach the headlines are the many individual breaches that happen millions of times a day, all over the world.

Intense exercise can cause problems with our digestive tract. It even has a name — "Exercise-induced Gastrointestinal Syndrome." Simply put, strenuous exercise can damage the gut and let the bacteria that reside there potentially pass into the bloodstream.

Welcome back, my tenderfoot hackers! In continuing my series on digital forensics using Kali, I want to introduce you to two complementary tools, both built right into Kali Linux. These are Brian Carrier's tools Autopsy and Sleuth Kit.

After years of struggling, it appears BlackBerry has finally figured out how to update its iconic design for modern times. The BlackBerry KEY2 pays homage to past devices such as the Bold 9000 while adapting to modern times with the Android OS. The result is a device that might be the best BlackBerry to date.

When using Linux, we often need to install new software, a script, or numerous large files. To make things easier on us, these files are usually compressed and combined together into a single file with a .tar extension, which makes them easier to download, since it's one smaller file.

The biggest change this year for iPhones comes with the cameras. All three iPhones get a new ultra-wide camera, which allows the device to capture more of what's in front of you. Not so new this year is the 64 GB base storage, which will fill up fast when shooting in 4K at 60 fps. A new feature will also add to your storage concerns, however, a feature that captures more video than it really should.
1 Identify the child's talents, and discuss the opportunities he has to use them in productive ways. If you notice that the child you're mentoring is excellent with counting money, talk about how the child should consider a career in banking or running a business one day.

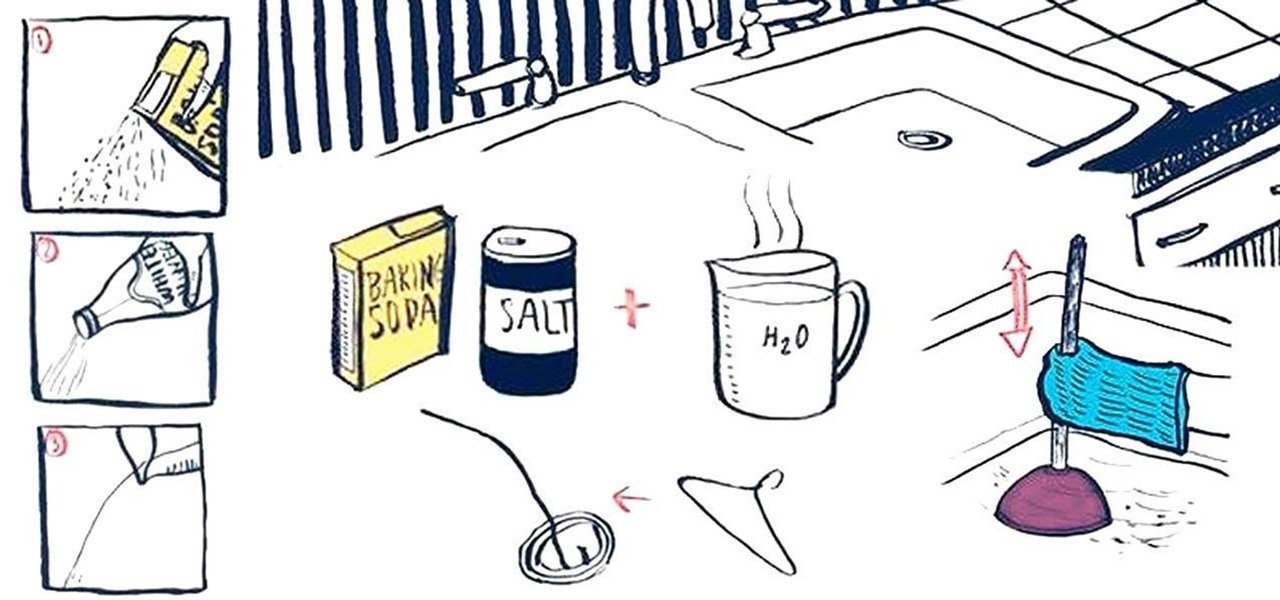
Oh, boy. A stopped-up drain. It'll inevitably happen with any home plumbing system and your kitchen sink is no exception. That clog won't go away on its own and will require immediate attention to keep any standing water from rising. But you don't have to resort to calling an expensive plumber or using a bottle of hazardous chemicals. Using simple kitchen staples or common household objects, as well as some determination, you can unclog your kitchen sink on your own without paying a dime.

Cryptography is the science of keeping secrets, or more specifically, the science of disguising them. As a point of fact, cryptography has progressed quite a bit farther and now encompasses file and message integrity, sender authentication, and pseudo-random number generators.

Augmented reality headset maker Meta Company unveiled Meta Viewer, its first software application, during its keynote at the Augmented World Expo in Santa Clara on Wednesday.
Hello guys I am ROMEO 64 (sounds weird I guess but who cares. :D).. Alright....Ever wondered what happens when you login to your Facebook account?

When my girlfriend told be about a Trivia Crack cheat she discovered, I was a little dubious. Then, after witnessing her trick in action and trying it out myself, my faith in the popular trivia game was forever tainted.

I love making stock. It's thrifty because you get extra use out of poultry bones and vegetable peelings, plus having homemade stock on hand makes so many things taste better, from soup to stews to pasta sauces. If you deglaze a pan, homemade turkey stock, booze of some kind, and butter will create an eye-rollingly good sauce in mere moments. One task I do not love? Figuring out how to skim the damn fat off the stock (or soup) after I've made it. It's necessary to skim the fat as you boil down...

Ever wonder why when you defrost meat, there's all that pink liquid at the bottom of the plastic bag? That liquid is called "purge," and it's not good.

When it comes to Easter, I usually dig plastic eggs with money or chocolate inside but hard-boiled eggs shouldn't be missing from the party. And simple hard-boiled eggs won't do. You need to decorate them because we all know bunny eggs are extravagant. What's even better than bunny eggs, though? Spider-bunny eggs.

In this project, you'll learn how to re-purpose low-cost sprinkler parts into a high-powered CANDY CANNON. Be the coolest person on the block by building a pneumatic device that will launch candy 100 feet in the air—you can make it rain down all kinds of sugary treats!!!

The Augmented World Expo is winding down in Santa Clara, where Qualcomm, Vuzix, and Meta Company were among the companies making big announcements.

The first wave of iPhone X preorders, the ones with a delivery date of Nov. 3, sold out in ten minutes. You can still preorder one and skip the lines next week at Apple Stores across the country, but if you want that bezel-less beauty in your hands ASAP, brick and mortar might be the way to go.

Mitochondria are known as the powerhouses of our cells because they generate energy to power them. But they also play a key role in the death of cells when they're damaged, infected, stressed, no longer needed, or at the end of their life.

Yep, Google just put in place a new thing called the dun dun duuuun .... "Device Catalog!" No, not like the Macy's catalog of your smartphone dreams. This is quite the opposite.

How's it goin'? In this tutorial, we will learn about the security issues of the popen and system functions. I've seen a few people attempting to run command line utilities or whatever it is they require with calls to these two functions but may not know the security implications which come along with it. I will show you using an example from the wargame IO Smash The Stack.

Hello World ! Well, welcome in my post. This will be in series, and this is first part. Throughout the series, I will share my research and findings with you. And that will be on topic, Encryption Is Not Enough. We will see, how Encryption is broken & what countermeasures should be implemented to secure it. Let's begin, Why do we encrypt ?

Pop-Tarts are a pretty iconic breakfast food. And while I'm more of a bacon, eggs, and toast person myself... sometimes a sweet, gooey, artificially-flavored treat is just what you need in the morning. Yet, despite the fact that I do enjoy Pop-Tarts, I've always found them a little bit bland. Therefore I decided to make them better—by cooking with them.
It's been a while, since I have just started High School. I have put a hiatus to my pentesting for a few weeks, and now, I am making a return. I have taken time to read about code, (even did a research article analysis on how humans can write "beautiful" code and something like that) and pentesting, but never made a full return. I will be occasionally coming back for a while.

Let me start by saying something controversial: I despise the gluten-free fad. I think gluten is delicious (I go through at least two loaves of bread a week, with a healthy dose of pretzels and pasta in there as well), and I think many of the health myths surrounding gluten are either fabricated or hyperbolic.