To say we're a nation of coffee-lovers is putting it mildly. Americans consume 400 million cups of joe in one day alone, but how well do we actually know our morning BFF? We know it comes from a bean, and that more coffee drinks exist than there are ways to skin a pig, but what else?

Update, November 12, 2014: Android 5.0 Lollipop is officially out now. If you haven't gotten the OTA yet, check out our new guide on installing the official Lollipop builds on any Nexus for download links and instructions, for Mac or Windows.

Update: June 19, 2014 Android 4.4.4 has been released, fixing a small security bug in 4.4.3. The factory images have already been made available to all current-generation Nexus devices, and I've linked them out below. This does not affect the process depicted, you can still use these same steps to bring your device up to date with this latest release.
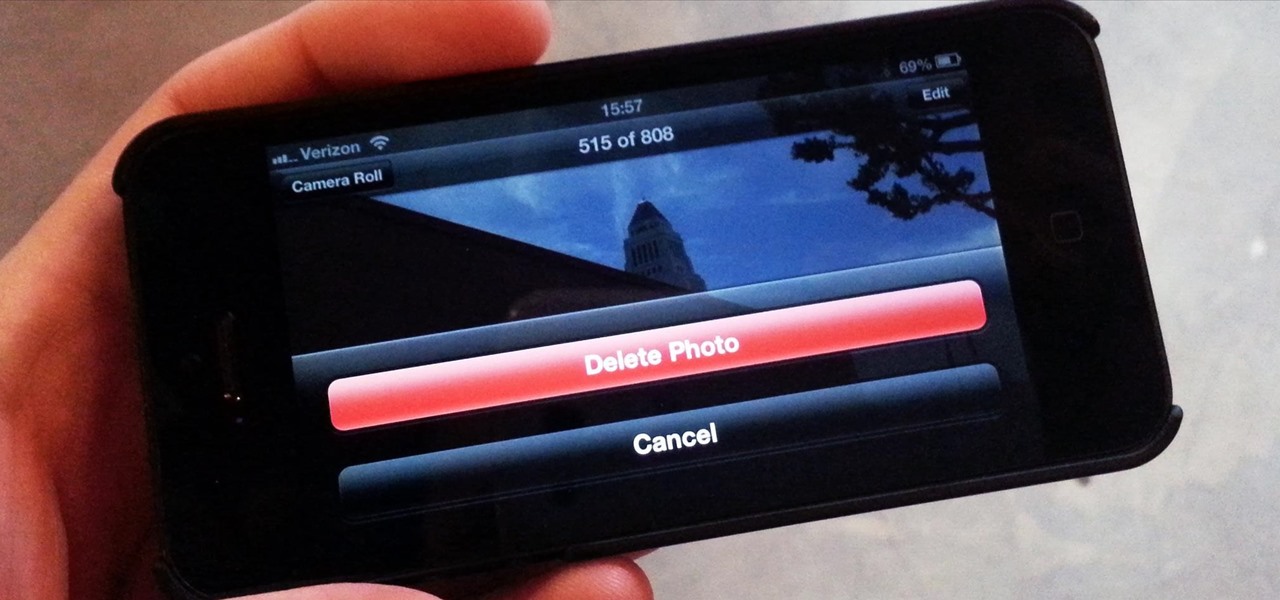
In one of Apple's newer ads, the company claims that "more photos are taken with the iPhone than any other camera." If this is in fact true, then it might also be appropriate to say that more photos are accidentally deleted on iPhones than any other camera.

Welcome back, my hacker trainees! A score of my readers have been begging for tutorials on how to hack Wi-Fi, so with this article, I'm initiating a new series dedicated to Wi-Fi hacks. This will probably be around 6-9 articles, starting with the basics of the technologies. I can hear you all groan, but you need to know the basics before you get into more advanced hacking. Then hopefully, developing your own hacks.

Millions of travelers pass through airports each day without understanding how powerful and insecure a boarding pass can be. Anyone can scan the boarding pass barcode with a mobile app, allowing access to frequent-flyer accounts and even a passenger's temporary airline account. In this guide, we will explore how hackers scan and decode the information contained in a boarding pass barcode and why.

The Watch Dogs video game series came out in 2014, enamoring audiences with the idea of a seemingly magical smartphone that could change traffic signals, hack web cameras, and even remotely control forklifts. This may sound like science fiction, but The Sonic uses a customized flavor of Kali Linux to allow you to unleash the power of Kali from any smartphone — all without the need to create a hotspot to control it.

As was mentioned by the great OTW last week, TOR, aka The Onion Router, has had its integrity attacked by the NSA. In an attempt to reduce the anonymity granted by the service, the NSA has opened a great many nodes of their own. The purpose is presumably to trace the origin of a communication by compromising some entrance and exit nodes. Once both are compromised, it is much easier to correlate traffic with a particular individual.

Kali Linux is probably the most well-known hacking distribution among penetration testers. However, there are alternative distros which offer versatility and advanced package management systems that are absolutely worth considering.

I was in college, and my 15-inch Sony Vaio laptop was my prized possession. It was my first PC and probably the most important thing I brought with me to my dorm — it was both how I completed my assignments and my primary source of entertainment. How could it turn its back on me in my time of need?

Clumsiness is the great equalizer when it comes to smartphones — it makes no distinction between the most expensive flagship handset and cheaper mid-range models. A hard drop onto pavement will usually result in a shattered screen, regardless of how pricey your device is. And with a smartphone breaking every two seconds, we're truly our own handset's ultimate nemesis.
Welcome back Hackers\Newbies!

Using a strong password is critical to the security of your online accounts. However, according to Dashlane, US users hold an average of 130 different accounts. Memorizing strong passwords for that many accounts is impractical. Fortunately, password managers solve the problem.

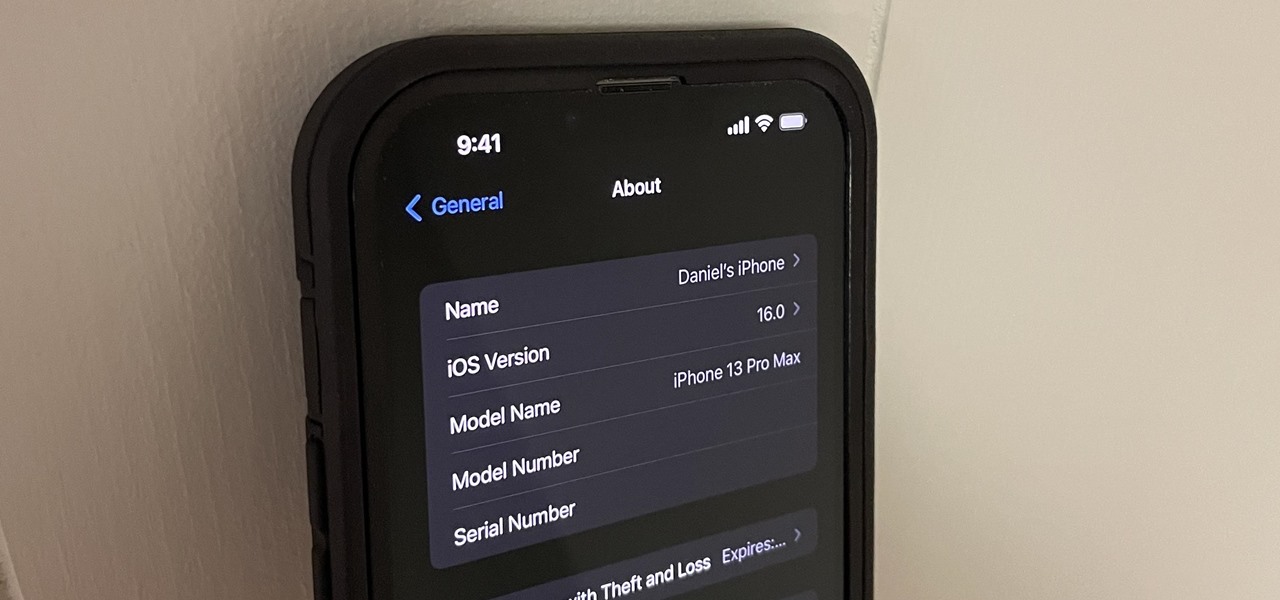
Beta software can be exciting because you get to experience cool new features before most other people. But it can have unwanted consequences such as bugs, UI glitches, and horrible battery life that'll make you wish you never installed it. If that sounds like you with iOS 16 beta or iPadOS 16 beta, you can downgrade to iOS 15.5 or iPadOS 15.5 for a more stable user experience.

Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself from cyberstalkers, advertisers, and hackers in a time when digital lives are a high commodity.

Apple's latest iPhone software update — iOS 17.5 — is finally ready for prime time. Released on May 13, it includes at least 32 new features and changes you need to know about, from a new game and offline news access to new wallpapers and anti-stalking capabilities.

If you are looking to sell a lot on eBay, while maintaining satisfaction and product integrity then you are in prime position to be an eBay PowerSeller. As long as you stay within the bounds of the requirements, you can hold this particular title.

I saw this on the Food Network and tried it out. We loved it. It is a great way to use leftovers and with the holidays upon us, I know you'll want to try it. I think it was Jamie Oliver who presented it although I couldn't find it on the website. It was described as a common thing done in the UK as the evening meal after a Sunday lunch. It is great with leftover turkey, dressing, and potatoes and gravy. The name comes from the sounds that it makes when it cooks. When you put the patties in th...

Part science, part bar magic, this simple tutorial will help you impress five year olds. As long as you are not John Wayne Gacy, we encourage you to learn how to stick a needle through a balloon and maintain the full integrity of the sphere. Oh, did we mention,you need vaseline? Pierce a balloon without popping.

Good mornings are used primarily to work the lower back muscles. The hamstrings and gluteus muscles are also involved in the movement.

The bicycle crunch is traditionally used to work the oblique muscles. While that may be true, this exercise is good for overall abdominal strengthening. The rectus abdominis (the "six pack" portion of the abs) is probably more active than are the obliques. Nevertheless, it is still an effective ab exercise. Instructions for the bicycle crunch are listed below:

PC Gamer represents all that was awesome about games journalism in the '90s, now sadly diminished. Brilliant, funny, full of integrity, and solid print sales were always present, and with the tragic exception of the latter, still are. Video game magazines were hit harder than nearly any other magazine vertical when the internet began its uncoordinated, but inevitable assault on print media. Magazines are now struggling to find their place in a world filled with more competitors than paying cu...

These are the KGB Agent Guidelines as taken from 542542.com/guidelines. kgb Guidelines

When your bootloader is unlocked, your phone shows a screen that tells you the bootloader is indeed unlocked and how software integrity can't be verified. But if you're the one who unlocked the bootloader in the first place, all this message does is slow down the bootup process dramatically.

"Life is difficult." That's how Scott Peck's best-selling book, "The Road Less Travelled", begins. That life is difficult is not news. Over two-thousand years ago the Buddha said it too: Life is suffering. The sanskrit word the Buddha used for suffering is dukkha. Dukkha doesn't refer to physical pain, necessarily. It refers to something more akin to our English word 'dissatisfaction'. Adages abound in our language which attest to the universality of dissatisfaction in our daily lives. "The g...

The United Kingdom has long been known as an international hub of yellow tabloid journalism. The News Of The World, one of the nation's largest tabloids, is famously in court right now because of the deplorable methods it used to acquire salacious information about interesting people. It appears, given their recent string of video game related reportage, that daily newspaper Metro has also had its fair share of morally dubious reporters on staff.

Update: New Trailer (7/9/10) In July of 2008, Fawaz Al-Matrouk, director of "To Rest In Peace", brought me on to shoot his USC graduate thesis film. Two years, 3 cameras, and over 15,000 miles later, the film is in its last week of post, having completed our final color correction at Light Iron Digital in Culver City yesterday.

If you're a frequenter of Null Byte, I bet you have at least some interest in information security. Furthermore, you have a hobby that if applied in certain ways, will get you arrested. I've received quite a few messages from the community here about federal cybercrime law and how it applies to them, so I decided to get together with my lawyer to come up with some answers.

In 1988, John Langley created COPS for the fledgling FOX network. 23 years later, the show is still running. It is the Energizer bunny of prime time television. Since John has followed more police officers and witnessed more crime than any human being on earth (absolutely no question), I had to ask some advice for hypothetical unwanted encounters with the men in blue.

Who could resist a retro SCRABBLE board game for two bucks? Suereal definitely couldn't, especially with the challenge of totally revamping a board game into something genuine and creative. Craftster's Craft Challenge #51 last June was meant to bring life back to an old board game with the following expectations:

Math Craft admin Cory Poole posted instructions on How to Make a Cube, Octahedron & Icosahedron from Sonobe Units, plus some great complex models in his article, How to Make a Truncated Icosahedron, Pentakis Dodecahedron & More. These models use the standard sonobe unit and a coloured variant.

Choose the Right Path Making a choice