
Hacking macOS: How to Create an Undetectable Payload
Encrypting payloads and encoding stagers are more effective against macOS than one might think. It's very easy to evade VirusTotal and macOS antivirus software using a few simple tricks.


Encrypting payloads and encoding stagers are more effective against macOS than one might think. It's very easy to evade VirusTotal and macOS antivirus software using a few simple tricks.

Many operators use elevators to control access to particular floors, whether it be the penthouse at a hotel or a server room in an office building. However, the law requires them all to have a fire service mode, which gives emergency access to restricted floors, and a hacker can use that to bypass security altogether.

With the macOS stager created and the attacker's system hosting the Empire listener, the malicious AppleScript can be designed and disguised to appear as a legitimate PDF using a few Unicode and icon manipulation tricks.

In the previous article in this short series, we learned how to find our neighbor's name using publicly accessible information and how to monitor device activity on their home network. With this information at our disposal, it's time to get into installing and configuring the necessary tools to begin our attack on John Smith's computer.

Using just a small sticky note, we can trigger a chain of events that ultimately results in complete access to someone's entire digital and personal life.

Dating websites allow you to see a person in a very intimate context, framing their successes and accomplishments in life to an important audience. The information contained in these profiles often can't be found elsewhere, offering a unique look into the personal life of the user.

An incorrectly scaled object in your HoloLens app can make or break your project, so it's important to get scaling in Unity down, such as working with uniform and non-uniform factors, before moving onto to other aspects of your app.

Threats to your privacy and security are everywhere, so protecting your data should be the highest priority for anyone with a smartphone. However, one threat many people overlook is the company who supplies the operating system your Android phone runs — Google.

Networking is built largely on trust. Most devices do not verify that another device is what it identifies itself to be, so long as it functions as expected. In the case of a man-in-the-middle attack, we can abuse this trust by impersonating a wireless access point, allowing us to intercept and modify network data. This can be dangerous for private data, but also be fun for pranking your friends.

There are more than 2 billion Android devices active each month, any of which can be hacked with the use of a remote administration tool, more commonly known as a RAT. AhMyth, one of these powerful tools, can help outsiders monitor a device's location, see SMS messages, take camera snapshots, and even record with the microphone without the user knowing.

You may not have heard of visceral leishmaniasis, onchocerciasis, or lymphatic filariasis, and there is a reason for that. These diseases, part of a group of infections called neglected tropical diseases (NTDs), impact more than a billion people on the planet in countries other than ours. Despite the consolation that these often grotesque illnesses are "out of sight, out of mind," some of these infections are quietly taking their toll in some southern communities of the US.

In a world increasingly regulated by computers, bugs are like real-life cheat codes. They give you the power to break the rules and do good or bad without ever leaving your seat. And government agencies around the world are discovering and stockpiling unreported bugs as cyberweapons to use against anybody they see fit.

It looks like Chris Urmson has spent the six months since he left Google's Self Driving Car Project trying to build a get-rich-quick self-driving unicorn, along with Sterling Anderson, formerly with Tesla Motors. At least that is one of several scandalous accusations in a Tesla lawsuit aimed at the pair, and their secretive startup Aurora Innovation, LLC.

There's a common saying that separates cooks from bakers: baking is a science, while cooking is an art. When baking, one little misstep can alter the texture, taste, and consistency of any recipe.

Greetings my fellow hackers, In the previous article, I discussed briefly about ransomwares and their devastating capabilities. Devastating in a way that ransomwares are not only known to encrypt files but to also lockout some specific functions of the system and hold it up for a ransom.

Many of our members here at Null Byte are aspiring hackers looking to gain skills and credentials to enter the most-valued profession of the 21st century. Hackers are being hired by IT security firms, antivirus developers, national military and espionage organizations, private detectives, and many other organizations.

Welcome back, my fledgling hackers! Over the years, we have examined multiple ways to own, exploit, or compromise a system. On the other hand, we have not spent a lot of time on denial-of-service (DoS) attacks.

In case you didn't know, Android has an awesome hidden settings menu called "Developer options" that contains a lot of advanced and unique features. If you've ever come across this menu before, chances are you just dipped in for a minute so that you could enable USB debugging and use ADB features.

Welcome back, my rookie hackers! As hackers, we are often faced with the hurdle of cryptography and encryption. In some cases, we use it to hide our actions and messages. Many applications and protocols use encryption to maintain confidentiality and integrity of data. To be able to crack passwords and encrypted protocols such as SSL and wireless, you need to at least be familiar with the concepts and terminology of cryptography and encryption.

We've already seen the visual changes that Android 5.0 Lollipop has brought to the table, but Google spent just as much time altering things under the hood. Awesome new functionality and hardware capabilities have been added left and right, and with the OS already out now, it's high time we had a look at some of these tweaks.

Welcome back, my hacker apprentices! Last week, I started off my password cracking series with an introduction on the principles and technologies involved in the art of cracking passwords. In past guides, I showed some specific tools and techniques for cracking Windows, online, Wi-Fi, Linux, and even SNMP passwords. This series is intended to help you hone your skills in each of these areas and expand into some, as yet, untouched areas.

One of the biggest problems in data security is authentication of data and its source. How can Alice be certain that the executable in her inbox is from the venerable Bob, and not from the not-so-venerable Oscar? Clearly Alice wants to know because if this file is actually sent to her by Oscar, the file might not be a game, but a trojan that can do anything on her computer such as sift through her email and passwords, upload her honeymoon pictures, or even turn on microphones and webcams. Thi...
Below are the official rules and guidelines for submitting content to WonderHowTo. Please look over them before publishing any articles. Ignoring the rules could result in deletion of your article or being flagged as a spammer. Most of these rules apply to comments as well.
Previously, losing an AirTag or Find My network accessory meant relying on tech-savvy strangers to contact you via phone or email if they found it. With a new Find My update, you can ditch the passive approach and be more proactive about recovering your tracker by sharing its information with trusted contacts and even airlines, allowing them to track your tracker for you.

To celebrate YouTube's 17th birthday, Google has gifted the app with new features, including pinch to zoom, precise seeking, and a darker dark theme. But the highlight is a new cosmetic upgrade called Ambient mode, which makes the viewing experience more immersive. Here's everything we know about the new background effect.
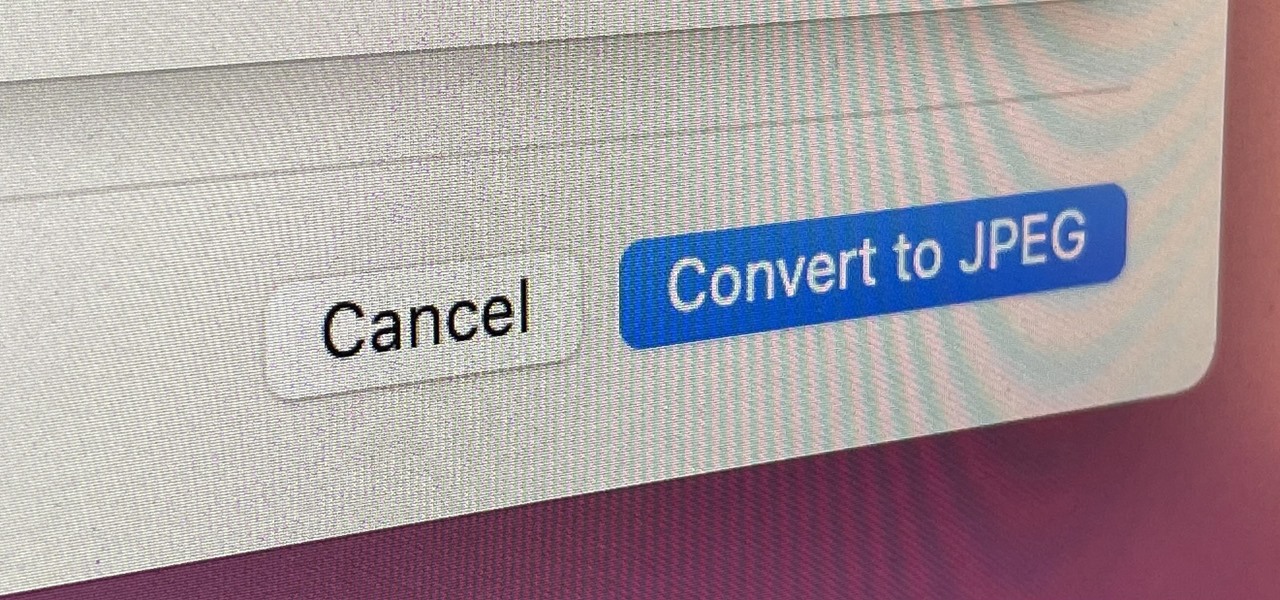
If you regularly run into issues opening images that use the .heic extension, the easiest solution is to convert the file into a more compatible format. Using apps like Photos and Preview on a Mac makes the process simple, but macOS Monterey just streamlined the process so that you don't even have to open an app anymore.

Apple is known for its dedication to design, attention to detail, and for its apparent belief that its products are half device, half art. If you've ever felt similarly about that latter point, or had a desire to hang your iPhone on the wall, Grid Studio might just have the piece for you.
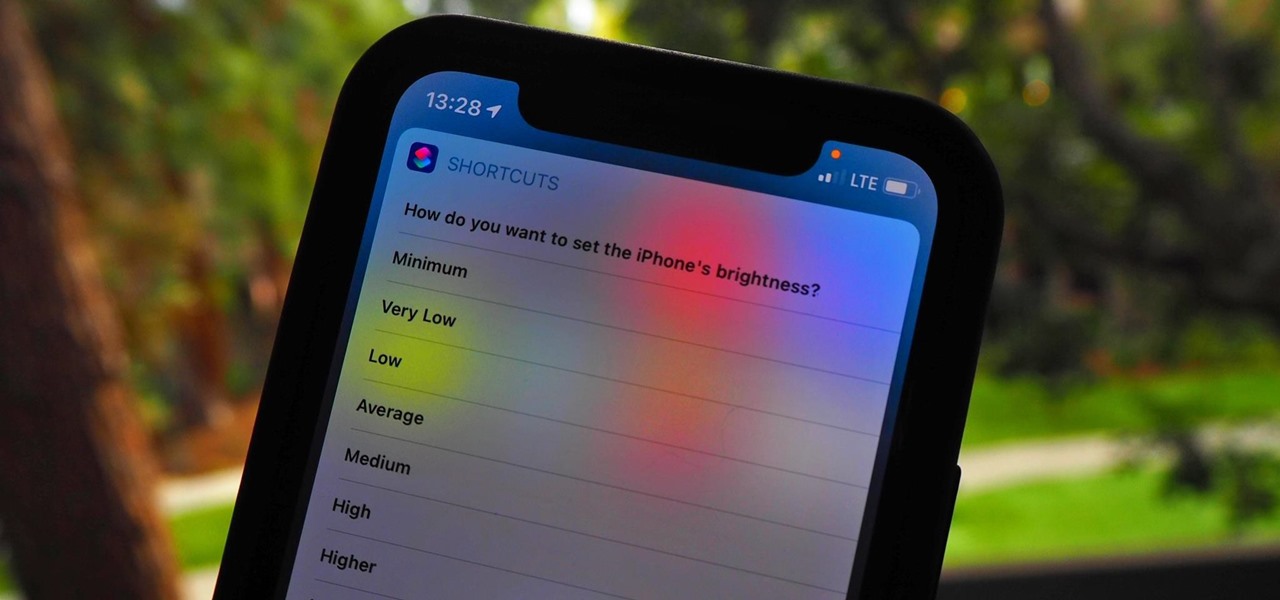
In the dark, even the lowest brightness option on the iPhone can still feel a thousand burning suns. No matter whether you're in bed or at the movie theater, you don't want to create a distraction with your smartphone. That's why you might want a brightness that isn't readily available on your device — but luckily, there may be a way to go lower than the lowest brightness.
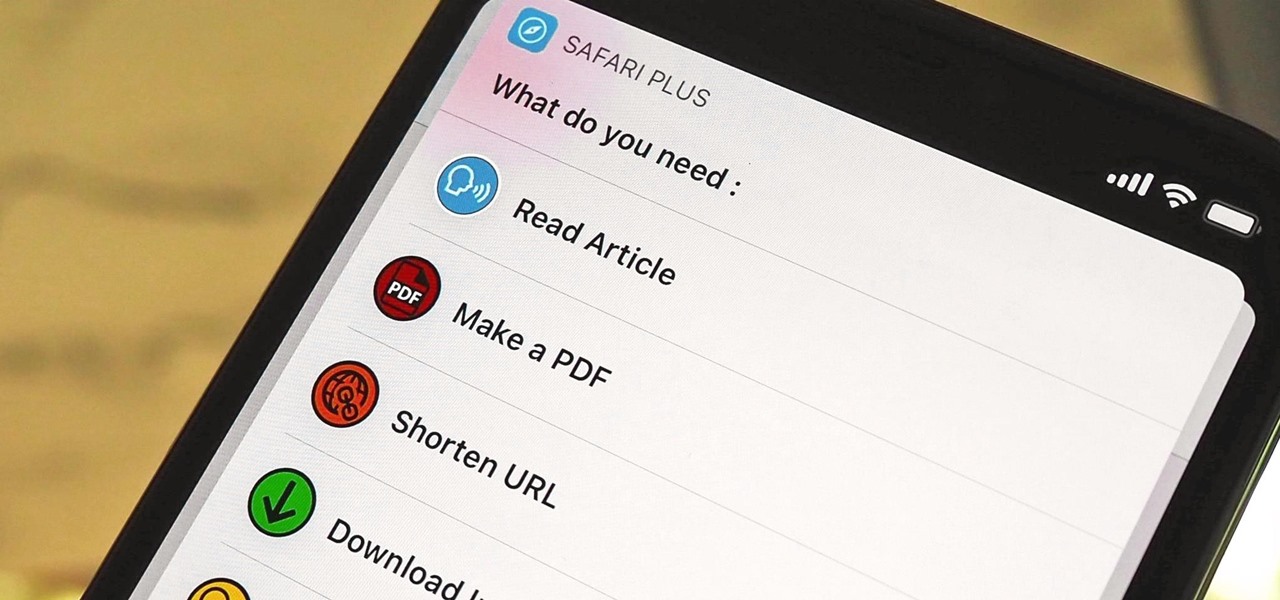
Safari saw many new features and improvements with Apple's latest iOS update, including webpage translations, privacy reports, and picture-in-picture. While the updates were well-received, Apple's mobile browser is still lacking some very basic features. Thankfully, there are shortcuts to bridge the gap.

You might think your photo is amazing, but in the midst of editing it and getting ready to post it on social media, you notice something in the background. Maybe it's an unwelcome stranger or a wide-open dumpster, or it's the entire backdrop, but suddenly you realize that it's bad. Although you look good in it, the background just doesn't work — which is why you can always get rid of it.

The year is still off to a roaring start, with augmented reality at the center of nearly everything, from enterprise solutions, to entertainment, to safety.
The iOS 14.4 developer beta was pushed out a day ago, and now the iOS 14.4 public beta is out and ready for your iPhone. At first glance, there's not much to look at in the new beta release, and it's not yet known if it lays out the groundwork for missing features such as 5G data with dual SIMs, shared third-party app subscriptions, and Xbox Core Controller.
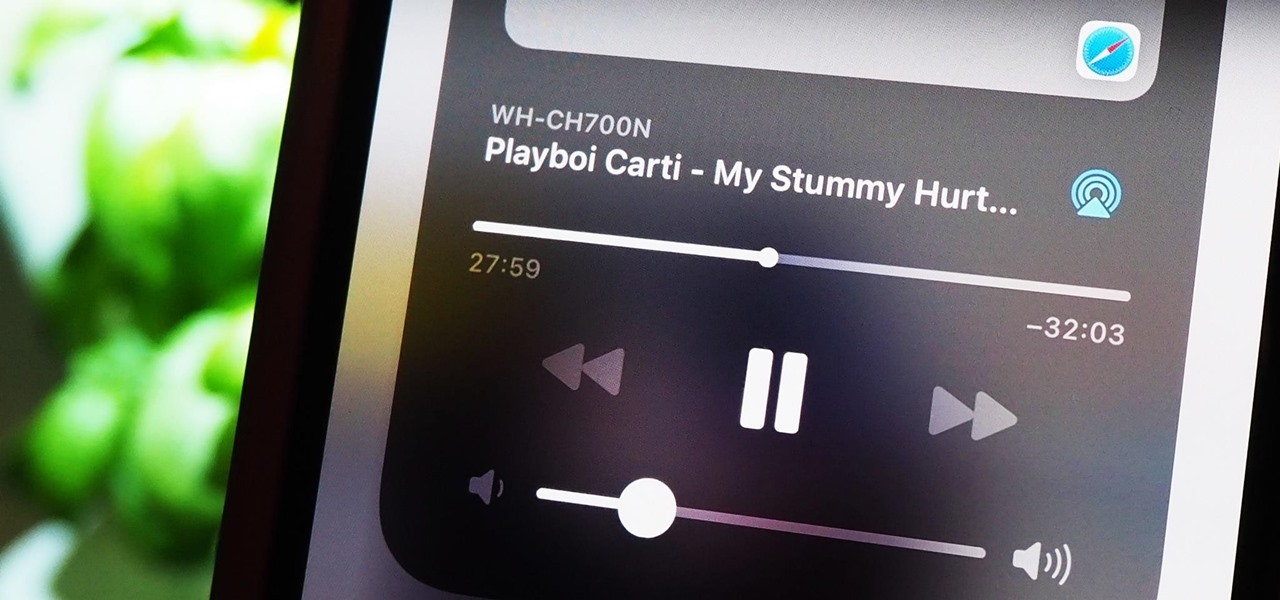
It's pretty clear with all of the annoying "Get YouTube Premium" pop-ups that litter the YouTube app that Google really wants you to pay for its Premium membership tier. That's why you'll see that "Get background play with YouTube Premium" ad after closing YouTube with a video playing — even in iOS 14 which supports Picture in Picture playback. But there are workarounds for background listening on iPhone.

It's common knowledge these days that Apple puts great cameras into their iPhones. So, it probably comes as no surprise to learn that the iPhone 12, 12 mini, 12 Pro, and 12 Pro Max sport some excellent shooters. What you might not know, however, is that these cameras are quite literally capable of Hollywood-quality video. So don't be surprised to see one of these filming a Netflix series.

The 2020 Chromecast is full of new features, but one glaring omission is Stadia, Google's cloud gaming platform. The search giant confirmed Stadia wouldn't officially arrive on the new streaming dongle until the first half of 2021 — but there's an unofficial way to get it now.

Aside from home screen widgets, one of the most exciting updates to the iPhone with iOS 14 is Picture in Picture mode. With it, you can watch minimized versions of videos on top of other apps so you can multitask like a pro. However, not every service is on board with Apple's new features. YouTube is the primary culprit, but there is a workaround.
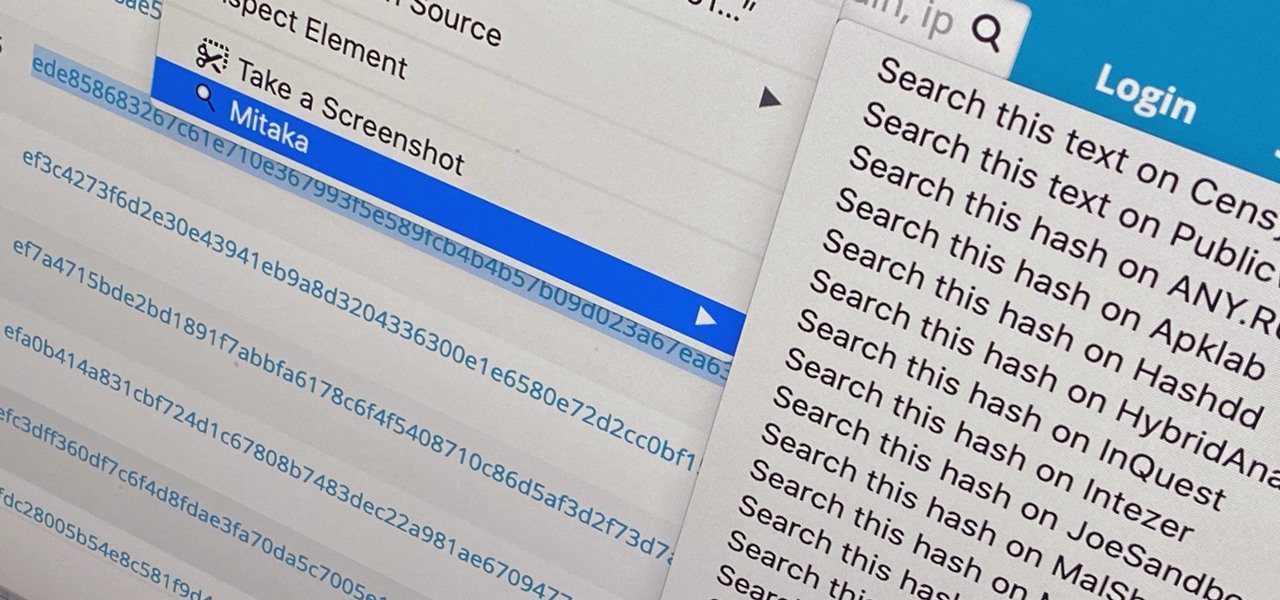
Web browser extensions are one of the simplest ways to get starting using open-source intelligence tools because they're cross-platform. So anyone using Chrome on Linux, macOS, and Windows can use them all the same. The same goes for Firefox. One desktop browser add-on, in particular, makes OSINT as easy as right-clicking to search for hashes, email addresses, and URLs.

Many apps on your iPhone want to use your location, most of which are for valid reasons. But some apps can function perfectly fine without location permissions, while others have no business even requesting it. If you want to be more selective about which apps and services you give away your coordinates to, the best thing you could do is start from scratch.

You may be familiar with image-based or audio-based steganography, the art of hiding messages or code inside of pictures, but that's not the only way to conceal secret communications. With zero-width characters, we can use text-based steganography to stash hidden information inside of plain text, and we can even figure out who's leaking documents online.

The original iPhone SE was, for some, the perfect iPhone. It brought back the popular one-handed form factor of the iPhone 5 but packed in the internals of the then-new iPhone 6S. Now, the second-generation iPhone SE is here for 2020, but can it live up to what made the first-generation iPhone SE so popular?