
How To: Save numbers in your iPhone
Don't lose your friends' numbers; save them to the address book. Watch this iPhone tutorial video to learn how to save numbers in your iPhone's address book. This how-to video is intended for new iPhone owners.


Don't lose your friends' numbers; save them to the address book. Watch this iPhone tutorial video to learn how to save numbers in your iPhone's address book. This how-to video is intended for new iPhone owners.

You can have as many iPhone e-mail accounts as you have addresses. Watch this iPhone tutorial video to learn how to add multiple email accounts to your iPhone. This how-to video is intended for new iPhone owners.

This baby carrying sling position is not intended for newborn babies. Since it does not offer much head support it is better to suite for toddlers. Watch and learn how to use a wrap sling to carry your child in the forward facing position. It is also called the Buddha or kangaroo position.

HD demo on how to set encoding parameters for proper Vimeo meady video at 720p resolution. This will give you crisp HD video ready for Vimeo upload right from iMovie 08.

See how to use a 1-1/2 inch x 15 ft. long 4,000 pound ratchet strap assembly with the twisted snap hooks. This device is intended for anybody carrying a heavy cargo load on their trailer or flat bed pickup truck.

Learn the differences between limit and no limit Texas Hold'em. Understanding the differences allows you to play two different ways and will help you determine which game is more suited for you, no pun intended.

Web application vulnerabilities are one of the most crucial points of consideration in any penetration test or security evaluation. While some security areas require a home network or computer for testing, creating a test website to learn web app security requires a slightly different approach. For a safe environment to learn about web app hacking, the OWASP Juice Shop can help.

Bokeh (which translates to "blur" in Japanese) is a photography technique referring to the blurred areas of a photograph. Basic bokeh photographs often have one point of focus, while the background falls away into a dreamy, blurred haze.

This is a really unique video that demonstrates how to make a basic friendship bracelet. It's unique in the sense that there is no one talking to you during the video. It's set to a catchy tune, with step by step instructions written on the screen, and then each step is demonstrated clearly in the video. There's a little humor woven in, no pun intended. Last, but not least, they show you what the end result should look like. Have fun with this one guys!

This video tutorial program is designed to promote ground crew safety when working under and around helicopters during external load operations. This is not a safety-training and is only intended to be used with the participation of a ground crew safety officer, trainer or other qualified personnel. All training and refresher courses must be done in accordance with federal and provincial regulations and the Canada Labour Code.

This medical how-to video details a robotic left aortic lymph node dissection in a patient with endometrial cancer using the Standard da Vinci system. The dissection on the right side of the aorta has been completed and the anatomy is outlined. The dissection on the left side of the aorta is highlighted in this video. Watch and learn how a dissection of a lymph node is performed on a patient. This surgical video is intended for medical students.

This experiment is intended to introduce students to hydrated compounds. These compounds have water molecules coordinated in their chemical structures. Examples CuSO4*5H2O, BaCl2*2H2O, and NaC2H3O2*3H2O.
Have you ever seen ads or a movie where the film goes on rewind, bring you back through time for whatever reason the director intended? This happens a lot in paper towel commercials, where you see a coffee stain get removed as the coffee pours itself back into a cup while the dog's footprints also disappear one by one as he gallops backwards to the front door.

It may sound like deja vu, but neural interface startup CTRL-labs has closed a $28 million funding round led by GV, Google's funding arm, for technology that reads user's nerve signals to interpret hand gestures.

Bacteria gets a bad rap. Most headlines focus on the danger and discomfort posed by pathogens like bacteria, but many of the bacteria that live on and in us are vital to our health. Many products out there, called probiotics, are sold with the implication that they're supporting these healthy bacteria that share our bodies — but do they actually work?

You must have read news about hackers dumping the data online, recent one was Ashely Madison. It's only the big companies' data, which gets noticed once it is out. There are many other small leaks which don't even get a mention. So this article is the first one of my series which will help you to find hacked accounts. Some of you must already know about this, but this post is intended for the new learners. This also serves as an example of my learning how a good service can be used in other w...

Beautiful Macrame Bracelet. This video tutorial is intended for people who know a little bit about macrame :)

How to make a Macrame Lagoon Earrings. A good accessory to wear everyday and for any occasion. (This video tutorial is intended for people who know a little bit about macrame)..

How to make a wavy macrame snake necklace with beads. This necklace looks very interesting and not hard to make, perfect to wear everyday and for any occasion :) This video tutorial is intended for people who know a little bit about macrame.

Sun in the Sea waves - Macrame bracelet tutorial. This bracelet has some macrame design elements - waves, chevron etc, and this is my design. This video tutorial is intended for people who know a little bit about macrame :)

How to make a Macrame Bracelet with a big bead (eye) in the middle. This video tutorial is intended for people who already know how to macrame..
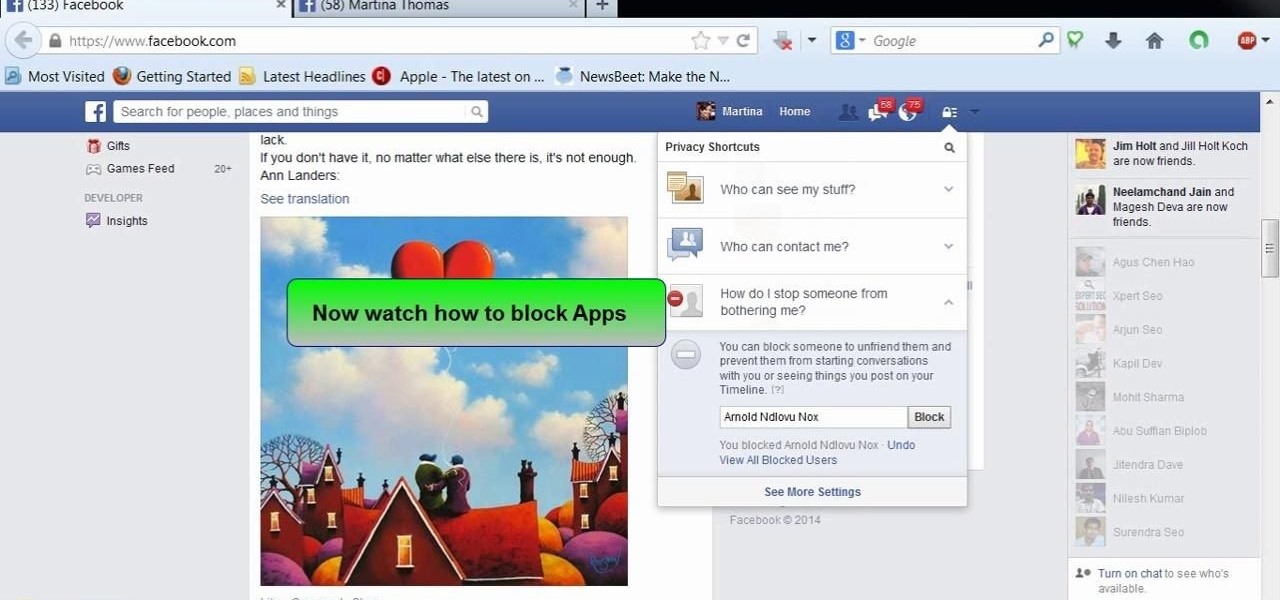
This video will show you how to block users and app invites on Facebook. You can also block apps from sending you notifications. If you accidentally blocked any user or app you intended you could unblock them easily. So please watch the video and employ the technique in your Facebook account.

Welcome back, my hacker novitiates! Many of you have probably heard of a man-in-the-middle attack and wondered how difficult an attack like that would be. For those of you who've never heard of one, it's simply where we, the hacker, place ourselves between the victim and the server and send and receive all the communication between the two.

Here is a manoeuvre that you won't see every day. It is intended for drivers in commercial vehicles who cannot see to the rear. By reversing with the flow of traffic it is possible to see approaching vehicles through the front windscreen and the right hand kerb by looking down over your shoulder. This manoeuvre sometimes occurs on the ADI, Part 2 Test of driving ability.

Guitars will need to be tuned continuously to ensure that it is tuned for the correct scale and notes so your music makes sounds the way you intend. If you haven’t been playing forever, you will probably need the assistance of an electric tuner to find the note. This video will show you how to tune your guitar using a tuner.

Now that we have our payload hosted on our VPS, as well as Metasploit installed, we can begin developing the webpage which will trick our "John Smith" target into opening our malicious file. Once he has, we can take over his computer.

Social media is kind of depressing. On one hand, we love knowing what's happening in the lives of others. On the other hand, everyone seems happier, better looking, and more successful than you. We're putting on a facade by posting statuses and writing comments that present the person we want others to think we are, rather than truly expressing ourselves. Yes, social media has facilitated movements and miraculous events, but let's be real. For the most part, none of it matters.

Welcome learners, lets us proceed further with the information we already have. In this post we will explore more about finding hacked accounts online. We will look into how to find juicy info in pastes which are deleted on Pastebin.

The $35 Raspberry Pi is an amazingly useful single-board computer (SBC) with a good balance of price, performance, and connectivity options. But for some projects, it just isn't enough. Whether you need more computing power, a smaller size, or better machine-learning capabilities, there are other options available.

Apple's macOS operating system is just as vulnerable to attacks as any Windows 10 computer or Android smartphone. Hacker's can embed backdoors, evade antivirus with simple commands, and utilize USB flash drives to completely compromise a MacBook. In this always-updated guide, we'll outline dozens of macOS-specific attacks penetration testers should know about.

Smartphones are still "phones," which means communicating with others is usually a primary use. Ranging from a simple "hi" to a more personal conversation and even sharing passwords, our messages should remain private so that only the intended recipient sees their content. While many apps tout end-to-end encryption, not all apps prioritize security and privacy.

There was a time when building a website required coding knowledge. Eventually, software came along that made the process easier, and then services like Squarespace made it dead simple for even a technical novice to design a website.
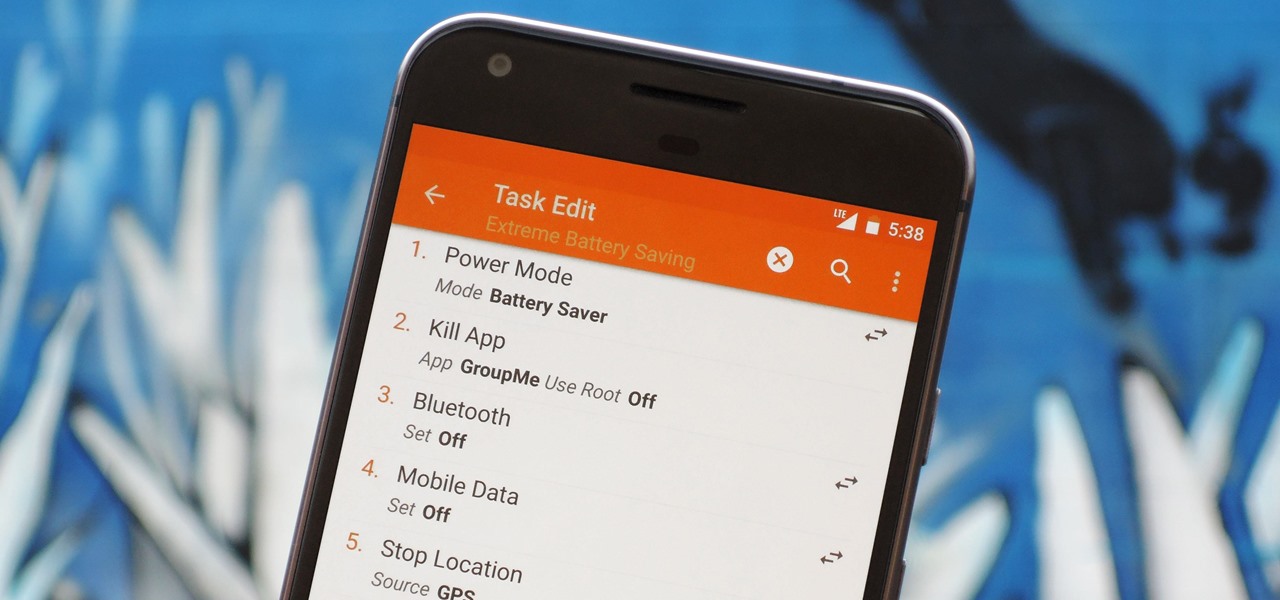
There are two core components to any Tasker automation: A profile and a task. Profiles are basically a set of conditions that must be met before Tasker will do anything. Tasks, on the other hand, are the actions Tasker will perform when your profile's conditions have been met. Think of them like triggers and actions, respectively. Or a cause and an effect.
I think it was 1986 when I first discovered my love for making computers say stupid things out loud. My older brother got a Commodore 64 for his birthday, which came bundled with software that would speak out any term you typed in—and boy, that computer sure made a fool of itself after my five-year-old imagination got a hold of the keyboard.

Video: . This is how I replaced the warn ball joints on my 2000 Pontiac Grand Prix GTP. This should be similar for Buick Regals from 1997-2003, Grand Prix from 1997-2008, and Chevy Monte Carlos from 2000-2007.
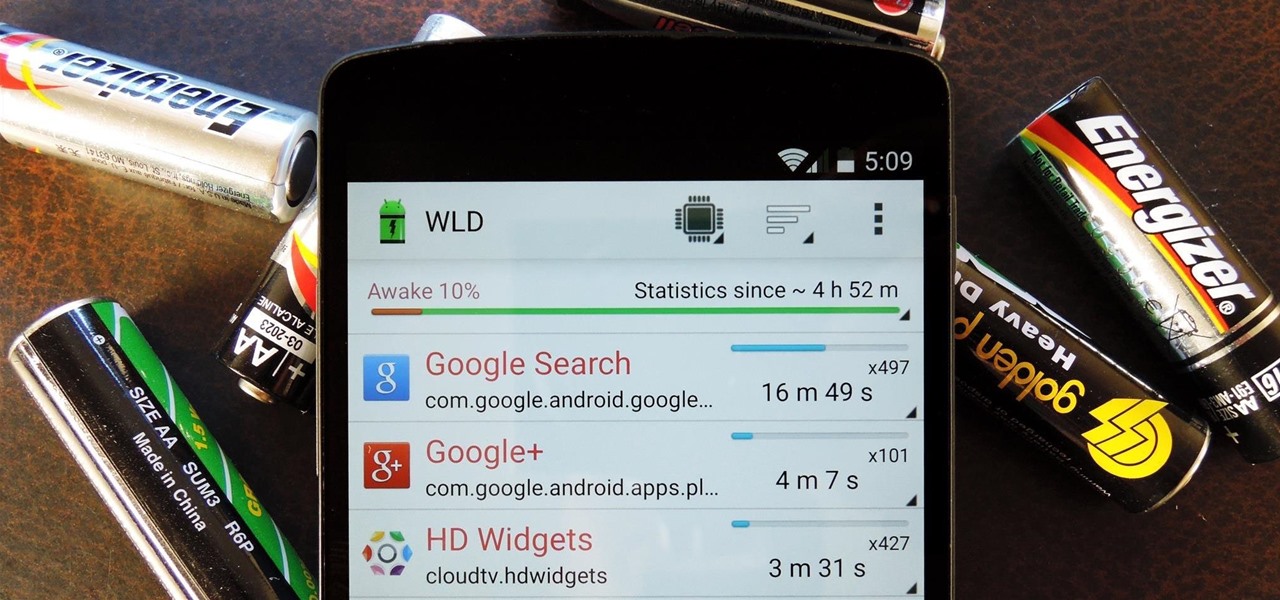
Android uses a set of permissions that apps can request to perform certain actions, and you're notified of these permissions each time you install an app. The problem here is the fact that you aren't given any built-in way to deny apps these permissions (although Danny just showed a workaround for this).

If you're an avid PC gamer, then you're probably well familiar with the term overclocking, which is basically just tweaking your computer hardware to run faster than it was originally intended.

Opening a brand new carton of juice can be disastrous if you're not careful. The air pressure on the inside of the carton is waiting to exit, but does so in a vigorous force when opening a carton for the first time.

Video: . Steel wool fire Photography

There are loads of reasons for somebody to want to recover a Windows password, and there are lots of different ways of doing it. My favorite of all of these ways is to use a piece of software called Ophcrack because: