
News: Apple Has Secured Micro OLED Supply Partner for Future AR Devices, Says Report
Like the layers of an onion, 2021 continues to peel back new hints of Apple's kinda-secretive augmented reality device development.


Like the layers of an onion, 2021 continues to peel back new hints of Apple's kinda-secretive augmented reality device development.

Creating doodles on an iPhone is made easy thanks to the "Draw" tool in Notes and "Digital Touch" for iMessages, but these are limited in scope. Drawing in Notes has no animated effects, and while Digital Touch does, its drawing tools are lacking and the animations can only live within iMessages. If it's animations you want, Apple has another app that can help you create them.

While hackers have taken advantage of numerous vulnerabilities in Adobe's products to deliver payloads to Windows users via PDF files, a malicious PDF file can also wreak havoc on a Mac that's using the default Preview app. So think twice before double-clicking a PDF open on your MacBook — it might just be a Trojan with a rootkit inside.
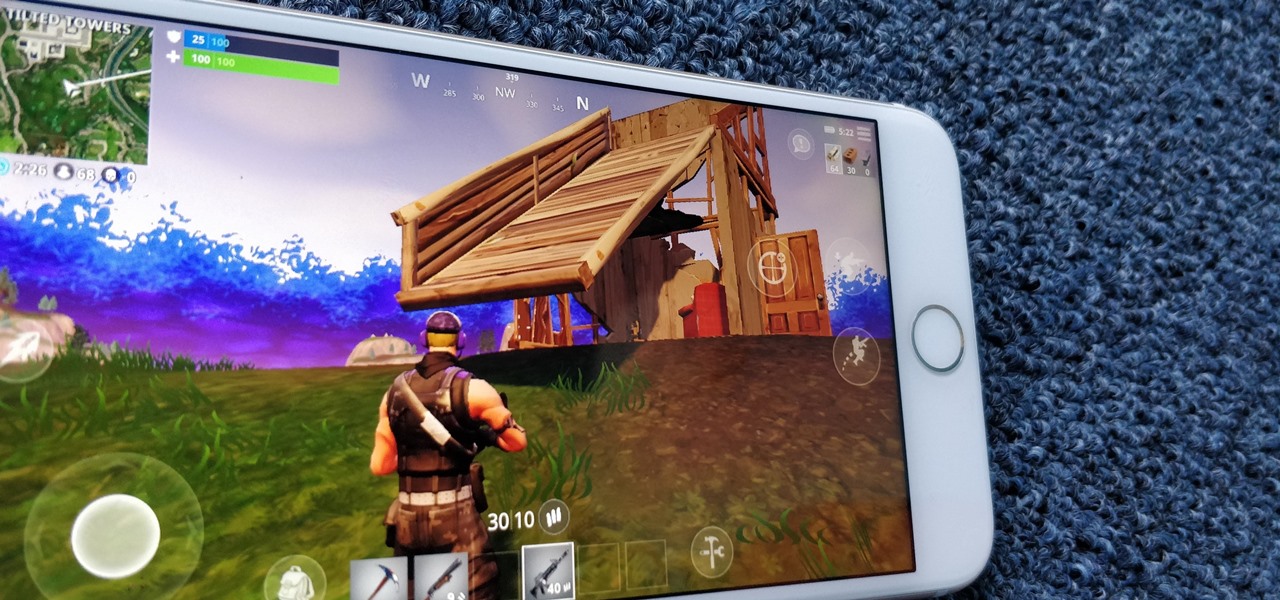
One of the more unique aspects of Fortnite Battle Royale is the ability to create structures. Using in-game materials, players can create walls and ramps for cover and to extend mobility. But creating isn't limited to just the basic generic structures. To really maximize their benefits, great players edit their creations to fit their needs.

At Build 2017, the annual developer's conference, Microsoft featured a Windows Mixed Reality Academy. This class was designed to get a developer started creating Mixed Reality experiences quickly. For those of us already developing for the Microsoft HoloLens, while the class — which is now available on the Microsoft website — did offer our first real chance to work with the new Acer HMD, there was not much depth.

Pokémon GO, the global augmented reality game that's brought fans out of their homes to catch Pokémon across the planet, has brought about plenty of real-world positives. Unfortunately, when players get power hungry and start taking game hacks too far, we all get a little screwed—both digitally and in real life.

Greetings my fellow aspiring hackers,

"It just ticked me off," he said. In March 2011, Neil Singh paid $50 to back the Hanfree iPad stand on Kickstarter. The project was funded at $35,000, but production stalled, and the delivery estimates kept getting pushed back.

The autocorrect feature in Apple's default iOS keyboard is anything but perfect. Sometimes it can't autocorrect things on your iPhone to want you want, while other times there's a software bug that just flat out gets it wrong. These autocorrect issues can get even worse thanks to Apple's predictive text feature, QuickType, and the inability to edit your custom dictionary.

Welcome back, my novice hackers! The worst thing that can happen to any hacker is being detected by a security admin, the security technologies (IDS, firewall, etc.), or a forensic investigator.

Welcome back, my fledgling hackers! In the first part of my series on Wi-Fi hacking, we discussed the basic terms and technologies associated with Wi-Fi. Now that you have a firm grip on what Wi-Fi is exactly and how it works, we can start diving into more advance topics on how to hack Wi-Fi.

In my first installment in this series on professional hacking tools, we downloaded and installed Metasploit, the exploitation framework. Now, we will begin to explore the Metasploit Framework and initiate a tried and true hack.
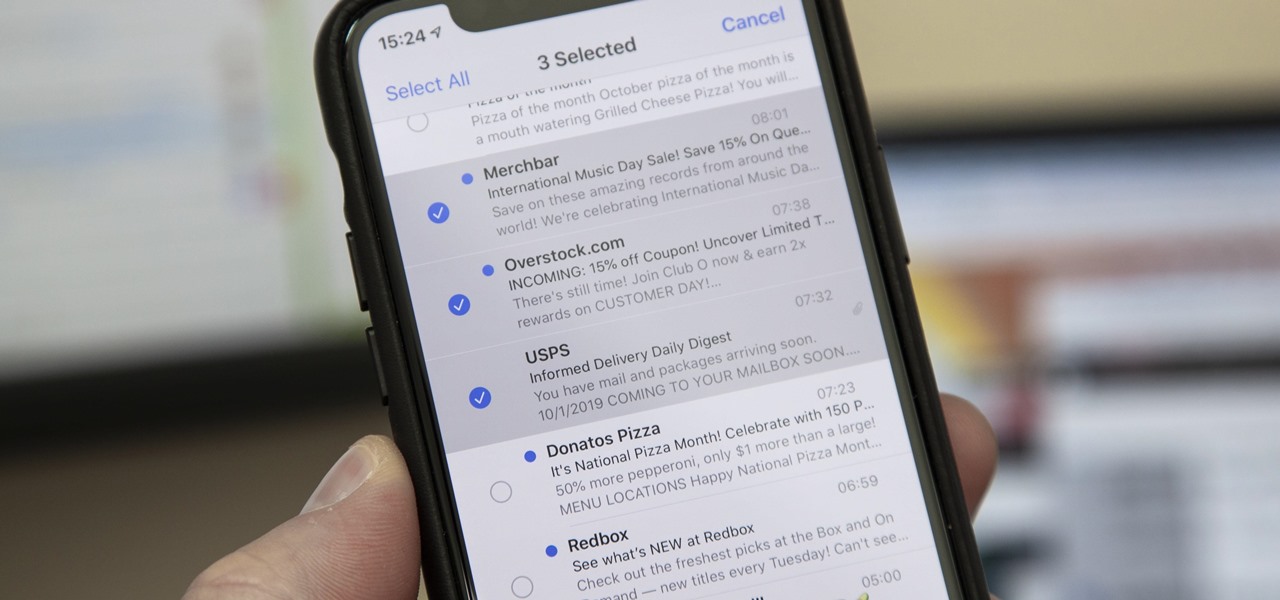
Normally, when you want to select multiple emails in the Mail app, you'd hit "Edit," tap all the bubbles next to the emails, then mark them, move them, or trash them. But in iOS 13, there's a much faster way to do it on your iPhone.
The Pixel's "Flip to Shhh" feature may not be groundbreaking, but it is useful. Third-party apps are copying it for other phones because it's so convenient. But it's not enabled by default and it's fairly hidden in the settings. So to take full advantage of your Pixel's feature set, you should learn how to use Flip to Shhh.

With iOS 13 and Android 10 adding built-in dark modes, app developers are working tirelessly to make their apps match the rest of your phone. Several are ahead of the curve, such as IMDb, who already offers a dark theme in their app.

Apple's Gatekeeper security software for macOS (Mac OS X) is vulnerable to remote attacks up to version 10.14.5. An attacker that's anywhere in the world can exploit MacBooks and other Mac computers by sharing a single ZIP file.

Apple officially released iOS 12 to everyone on Sept. 17, and while the new iPhone XR, XS, and XS Max will come with the software by default, you have a choice on whether or not to update your current iPhone model from iOS 11. There are a lot of tempting features to want to update right away, but there are also some compelling reasons to wait it out and install at a later time.
Over the past few weeks, a trio of developer lessons (one of which was revealed in Magic Leap's most recent Twitch livestream) have revealed samples of experiences that are possible while using the Magic Leap One.

Just nine days after the official release of iOS 11.2, Apple has released iOS 11.2.1. The update initially seems to have been seeded to only a handful of users and is intended to fix bugs in 11.2.
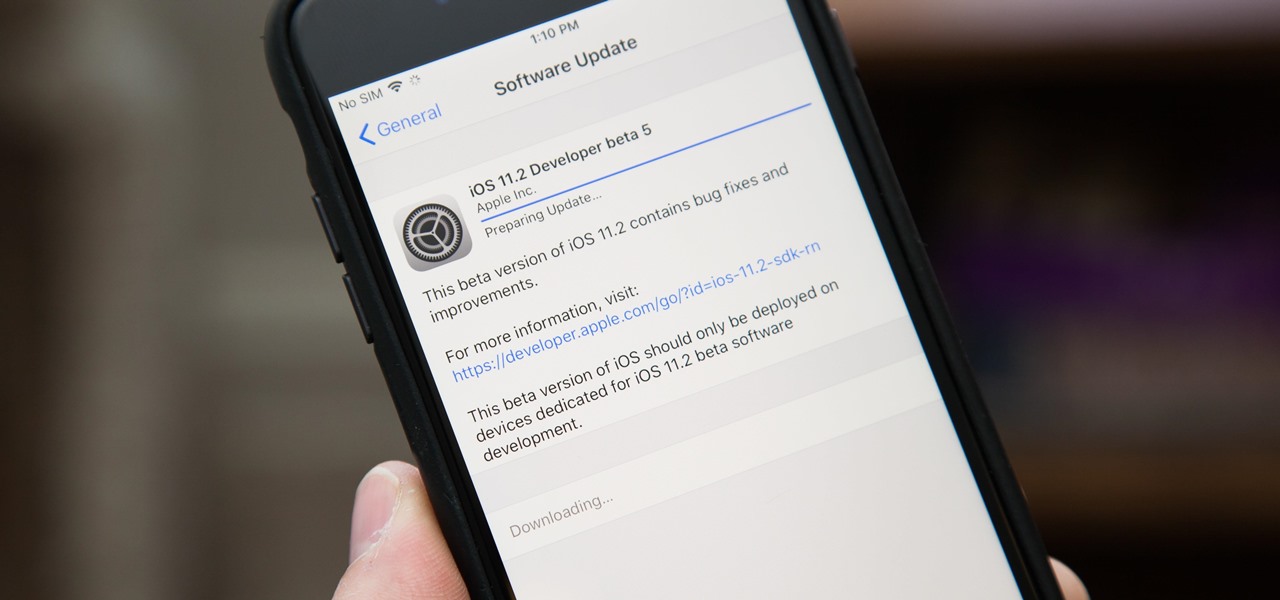
We're getting closer and closer to a final iOS 11.2 release for everyone. Apple just pushed out beta 5 for iOS 11.2 to developers and public testers on Tuesday, Nov. 28, and much like its predecessor from a few weeks ago, there's not much included but bug fixes and security patches.

When we are building programs that communicate over a network, how can we keep our data private? The last thing we want is some other lousy hacker sniffing our packets, so how do we stop them? The easy answer: encryption. However, this is a very wide-ranging answer. Today we're going to look specifically at how to encrypt data in Python with dynamically generated encryption keys using what is known as the Diffie-Hellman key exchange.

With autonomous technology being developed so quickly, auto companies have begun working on the next step in driverless development, passenger safety. German automotive supplier ZF has begun giving this some thought and has come up with a new kind of airbag, one that could define safety features in autonomous vehicles.

It was nice while it lasted. Samsung users who managed to get their hands on the Galaxy S8 or S8+ early enjoyed the ability to launch any app through the dedicated Bixby button. Unfortunately, Samsung wasn't all that down with us using the Bixby button for purposes other than its intended use — to provide quick access to Samsung's new virtual assistant.
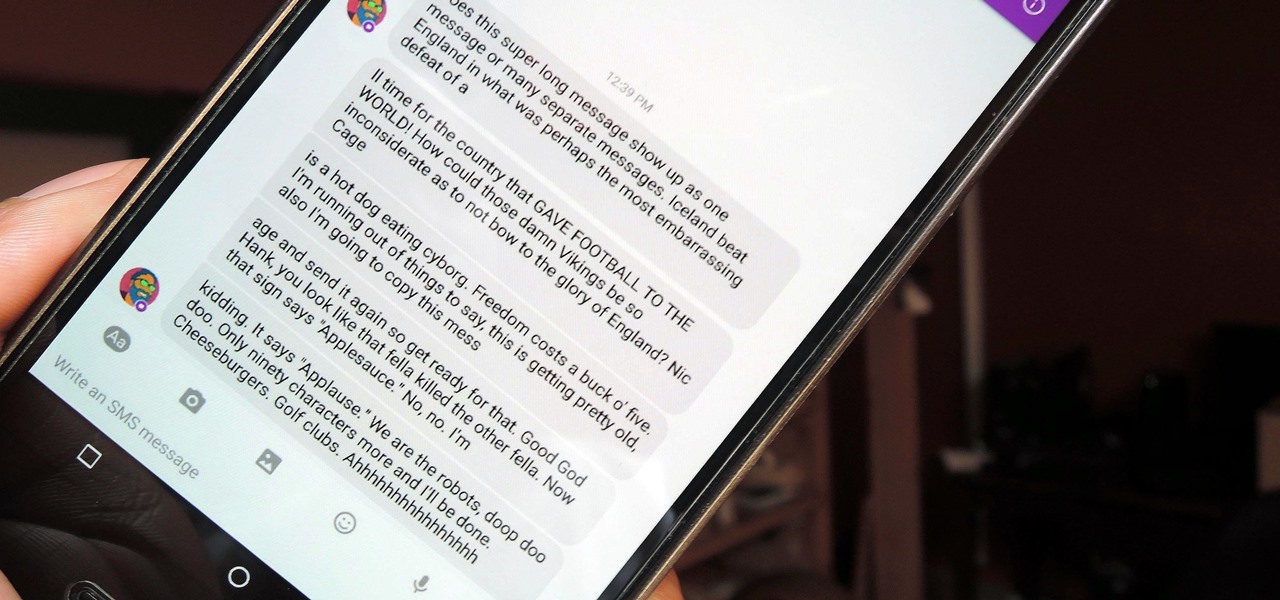
Depending on your carrier and the texting app that you use, sending long SMS messages from an Android phone often results in the recipient being hit with a barrage of fragmented, out of order texts.

A lot more people are about to be able to use Android Auto. Google announced at I/O 2016 that you'll soon be able to use the app with only your phone, so you won't need a compatible car or third-party display unit. And if (or more likely, when) Google brings the app to iOS, Apple may lose the precious "infotainment" system battle very early in the game. The update isn't coming until later this year, but once it arrives, you'll be able to mount your phone and use Android Auto the same way that...

Greetings aspiring hackers. I have observed an increasing number of questions, both here on Null-Byte and on other forums, regarding the decision of which USB wireless network adapter to pick from when performing Wi-Fi hacks. So in today's guide I will be tackling this dilemma. First I will explain the ideal requirements, then I will cover chipsets, and lastly I will talk about examples of wireless cards and my personal recommendations. Without further ado, let's cut to the chase.

As we're all aware, recon is vital to a successful hack. We need to know everything we can about the target in order to perform the best possible attack. Port scanning is a basic recon concept that is introduced very early in learning proper reconnoissance. The issue with port scanning is that is makes a lot of noise. Every connection to every port will be logged. This is where stealth scanning comes in. Also known as SYN or half-open scanning, stealth port scanning is a bit quieter, and is l...

Some variants of the Galaxy S6 will allow you to silence the camera shutter sound with an option in the app's settings menu. But this is not true of all models, plus there's an additional annoyance—when you're filming video and you get a notification, you'll actually hear this tone on the final recording.

With 16 megapixels and optical image stabilization technology, it's safe to say that the Samsung Galaxy S6 is well-equipped to take badass pictures. Packed with additional camera modes, like Panorama, Selective focus, and Virtual shot, there's always a way to capture an image as intended.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

Not too long ago I showcased ReCam, a free app that lets you schedule recordings and use your Android device as a security or spy camera of sorts. While useful, this app required you to schedule when to record in advance, resulting in you possibly missing the footage you intended to record (assuming your scheduling wasn't as on-point as you wished).

I know where I bought my phone, and I definitely know who I'm paying money to every month for cellular service, so there's absolutely no need to see my carrier's name draped all over my device. Fortunately, with Android Lollipop, the carrier label is only present on the lock screen. Nevertheless, that label can keep your phone from feeling just right, so let's go ahead and show you how to get rid of it.

Google Earth has long served as a great tool to explore the furthest regions of our beautiful planet from the comfort of our own homes, but for those with more than just a recreational interest, a bundle of pro features had always cost $399... a year.

Automatic brightness adjustments are supposed to make it easier to maintain good visibility on your phone, but it really never works as intended. It usually doesn't adjust properly, leading you to manually pull up the Control Center to adjust brightness via the slider.

So, you want to cause a little mischief, do you? Here are six super-easy pranks to help you make the most out of April Fool's Day (or pretty much any other day of the year). There's something here for everyone—TV fiends, magic trick lovers, fruitoholics, and even spam companies.

Carving pumpkins into creepy looking jack-o’-lanterns for Halloween can actually become fairly boring and tedious if you’re doing the same thing year after year. This time, jump into a whole new realm of Halloween fun with some exploding pumpkin faces! I like to call them blast-o’-lanterns, but can call them whatever you want.

Most of us have conducted an investigatory science project without even knowing it, or at least without knowing that's what it was called. Most science experiments performed, from elementary to high school students and all the way up to professional scientists, are investigatory projects.

For the majority of my math classes in middle and high school, a graphing calculator was a must. While the calculators were very useful to have, they were quite steep in the price column. After losing the TI-83 graphing calculator my parents bought me in high school, I had to save up my own money to buy the next one.

Polaroid photographs have a charming old-fashioned feel to them, evoking nostalgic memories of past days. My younger sister used to carry her Polaroid camera everywhere she went, transforming even the most trite moments into something wonderful.

Anything free is cool, but getting a fully upgraded operating system for the great price of nothing is downright awesome. A recent exploit was uncovered that allows users to get a free copy of Windows 8 Pro directly from Microsoft's own website. Seriously.