Windows 10 is the most cloud-oriented version of Windows to date—yet, while this means you get some nifty new features, it also means some of your personal data is being shared with Microsoft's servers.

With the amount of time we spend glued to our smartphones, they could be considered a second job (if only we got paid). I spend a large part of my day scrolling through Reddit, Facebook, Instagram, and countless other apps, and burn through hours and hours without even noticing.

Whether I'm in my car or making dinner, I always have music playing. And since I don't like to keep my headphones on me at all times, I end up using my Android's built-in speakers a good portion of the time.

Update (February 2019): The methods below will help on older Android versions, but we've recently revisited this topic. So if you have a newer Android phone and you want to get rid of Google, head here.
Hello and welcome to my article. I have made this article for anyone who wants to become a hacker, and wants to know how to get started.

Make no bones about it—Google is an advertisement company first and foremost. Nearly everything they do is geared towards targeting the right people with the right ads.

Welcome back, my tenderfoot hackers! As hackers, we often are required to get past antivirus (AV) software or other security measures. To do so effectively, we need to have some understanding of how AV software works. In this tutorial, we will take a cursory view of how AV software works so that you can better strategize on how to evade detection by it.

Food waste is a topic near and dear to my heart, but the truth is, no matter how dutiful we are about finding ways to double-down on food scraps, a lot of stuff goes into the trash needlessly.

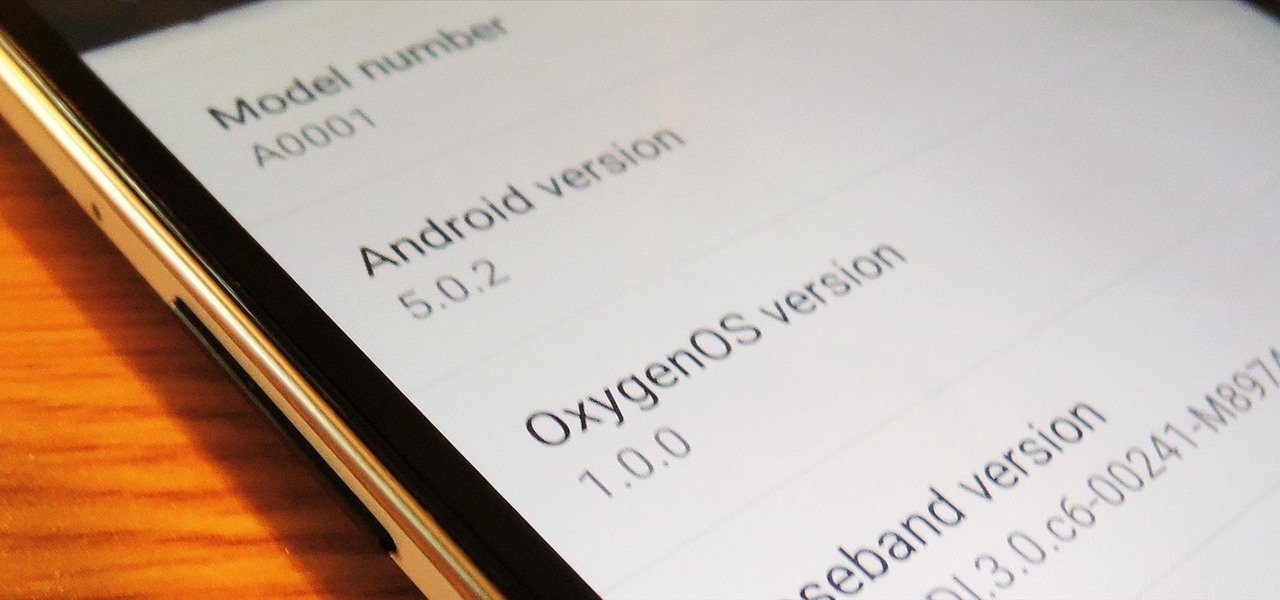
Despite CyanogenMod actively working on their CM 12S Lollipop-based ROM, OnePlus has opted to develop their own ROM, and after a few setbacks, OxygenOS is finally out. The OS is the result of OnePlus wanting to ship their devices without needing an outside company to create a ROM to power it. Like CyanogenMod's ROMs, Oxygen OS offers a vanilla Android Lollipop experience tailored for the OnePlus One.

Today I am going to teach the various ways that you can use social engineering to hack a system. For those of you that have followed my past tutorials, you know that social engineering can unlock a world of possibilities. This is because no matter how many firewalls, no matter how many patches there are on a server, the password is kept in the minds of people...and people, are not as smart as computers.

Welcome back, my rookie hackers! "How can I travel and communicate over the Internet without being tracked or spied on by anyone?" It's a question many Null Byteans have asked me, so I have decided to write a comprehensive article addressing this issue.

The only mail I like getting comes in the form of an Amazon package, but when I go to my mailbox, it always ends up being a pile of credit card offers and catalogs I could never see myself ordering from. Those pieces of junk mail usually end up in the trash, which is horrible when you think about all the trees that had to get cut down in order to produce them.

What type of person are you in group settings? Are you the social butterfly, eager to get to know everyone and interested in the people more than the setting? Or are you a wallflower, afraid to catch anyone's eye out of fear?

2015 is quickly shaping up to be the year of the cord cutter, with various media companies finally warming up to the concept of offering live streaming content. In the wake of Dish Network announcing a streaming cable service called Sling TV and Sony unveiling a similar platform in PlayStation Vue, NBC has decided to stream the Super Bowl and all of its festivities online. Before we get to all of the many ways you can stream Super Bowl 49 between the New England Patriots and Seattle Seahawks ...

When streaming services like Spotify or Pandora compete for customers, the main differentiating factor is the size of their libraries. While these and comparable services usually run somewhere around $10 per month, a completely free alternative may actually have the most expansive library out there.

Are you a follower or a leader? No matter how you respond, we all know that leader is a more desirable position to hold. Great leaders typically share a few qualities—confidence, intelligence, and strength, to name a few—but one of the most intriguing is their appearance. With the right facial structure, and some well-rehearsed expressions, you can trick others into thinking you're leader material.

You've probably tried just about every method of hanging your holiday decorations: nails, thumbtacks, sticky hooks, and, in desperation, even tape. Each method can leave a host of complications when removed, though, from chipping paint to visible holes.

Welcome back, my greenhorn hackers! Before we attempt to exploit any target, it is wise to do proper reconnaissance. Without doing reconnaissance, you will likely be wasting your time and energy as well as risking your freedom. In previous guides, I have demonstrated multiple ways to perform reconnaissance including passive recon with Netcraft, active recon with Nmap or hping3, recon by exploiting DNS or SNMP, and many others.

Accessing your favorite and most recent contacts on your iPhone is now faster than ever before, thanks to the iOS 8 update. Just double-click your Home button, select your contact above the app switcher menu, then choose how you want to contact them.

Coffee liqueur is pretty easy to make at home, and if you've read our guide on why instant coffee is a pantry essential, you know that we recommended the powdered stuff over fresh-brewed when making your own Kahlua at home...until now.

Welcome back, my budding hackers! People often ask me, "Why are you training hackers? Isn't that illegal?" Although I usually give them a short version of this post, there are MANY reasons why YOU should be studying hacking.

Apple has Siri, Google has its Now service, and Microsoft has Cortana. All of these voice-activated services can bring you information quickly and easily without having to type anything into your smartphone. Speak and within seconds you're provided with either an answer or somewhere you can find it.

As this generation continues to evolve, we become more involved with social media. For example, you may have a Facebook, Twitter, and a Google+ account, and be heavily involved in using all three, but the constant switching between sites, logins, and conversations can get very tedious.

I'll freely admit that I'm a SwiftKey diehard. I've used the keyboard since its inception in 2010, and it was one of the first apps I ever paid for back in the days of my beloved Sprint Evo 4G. Since then, I've kept up with all its beta iterations, and have unabashedly installed it on various friend's devices.

Welcome back, my greenhorn hackers! Lately, much of the discussion here on Null Byte has revolved around evading detection and not getting caught hacking. Several of you have written me asking for a series on evading detection and forensics, and while I began a series 5 months ago on just that, we have changed hacking platforms from BackTrack to Kali, which has a much more highly developed forensic toolset.

Instagram is not only a great platform to easily share some of your favorite moments with friends and family, it's a useful service for peering outside of your physical location. While you share a picture of your dog in Los Angeles, you can almost instantly view and like a picture someone posted of their breakfast in Tokyo.

The way you use your camera just got a bit more interesting. Phogy, a brand new camera app for Android, allows you to capture pictures with a 3D effect that comes alive when shifting your phone from side to side.

You don't always plan on getting drunk, it usually just sort of happens, right? You finish one beer, move on to the next, and all of a sudden you're a six-pack in and feelin' it. And when you're drinking in places you're not supposed to, it can get ugly.

It's been rumored ever since the 2012 release of the Kindle Fire, and now Amazon's first smartphone is set to debut a little later this year.

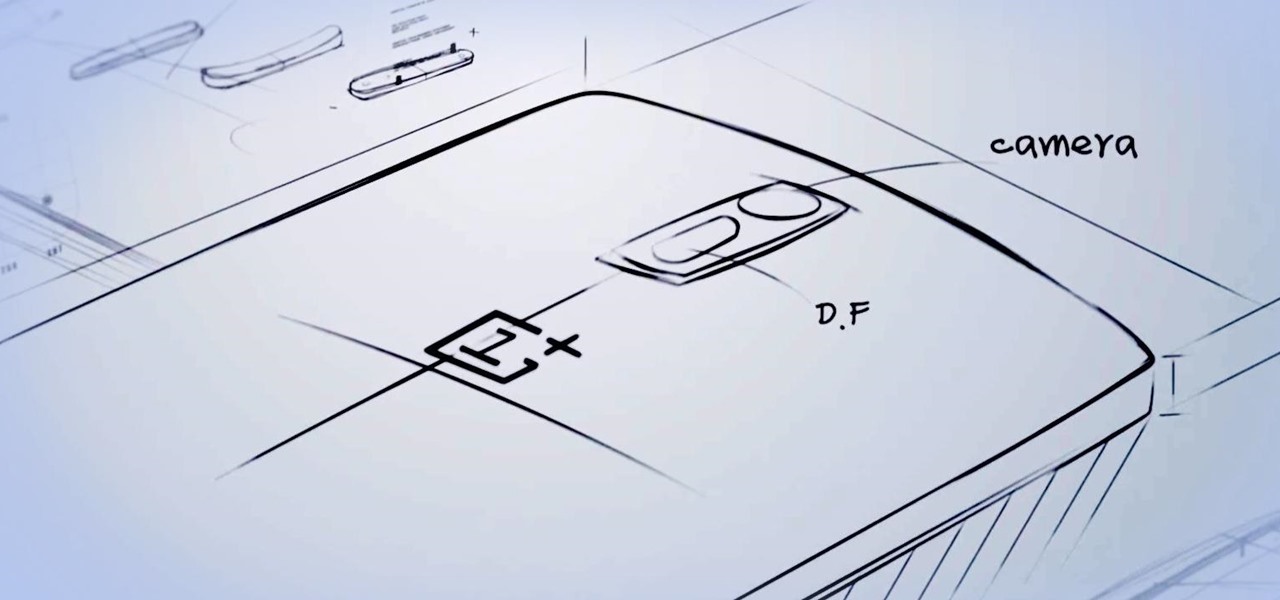
After lots of waiting and anticipation, the OnePlus One Android smartphone has been unveiled, and it's ready to take down the Nexus.

You can read at 500 words per minutes. Don't believe me? Here, see for yourself. This amazing technology comes from the startup Spritz, and they're ready to unleash it onto the smart device world, starting with the Samsung Galaxy S5 and the Galaxy Gear line of smartwatches.

Sometimes you need more than just your brain to split the bill at a restaurant or to calculate how much your cable company is ripping you off.

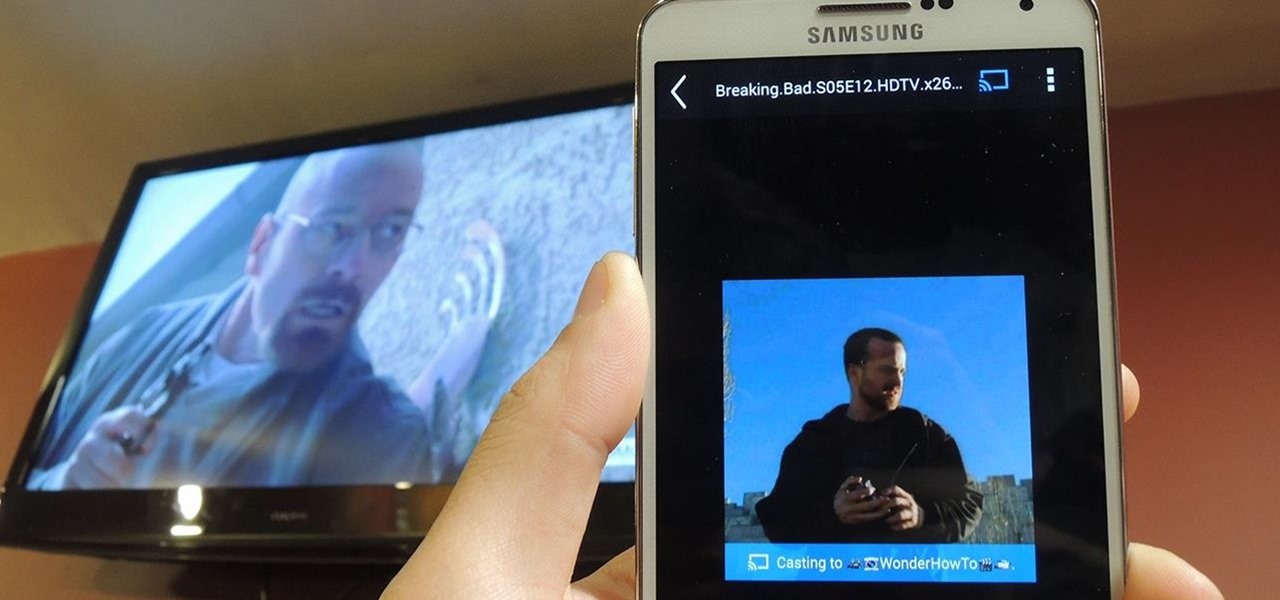
Recently, Google unleashed the Chromecast development kit, which lets developers add Chromecast streaming functionality to their own apps. However, there aren't many apps with Chromecast capabilities yet, and big companies and devs are still working on polishing their final products.

Fresh off the heels of their latest agreement, Google and Samsung may soon be further aligned in their mobile technology outlook. The two tech giants signed a cross-licensing patent agreement, but that doesn't mean that Samsung was just going to start putting out stock Android devices. Quite the opposite really, as we saw from leaks of its new Magazine UX. The new user interface was shown during Samsung's presentation of it's latest Galaxy tablet at this years CES, and as reported to Re/code,...

Welcome back, my fledgling hackers! As nearly everyone has heard, Target Corporation, one of the largest retailers in the U.S. and Canada, was hacked late last year and potentially 100 million credit cards have been compromised. Happening just before Christmas, it severely dampened Target's Christmas sales, reputation, and stock price (the company's value has fallen by $5B).

Welcome back, my novice hackers! In a recent tutorial, I showed how the SNMP protocol can be a gold mine of information for reconnaissance on a potential target. If you haven't already, I strongly suggest that you read it before progressing here, as little of this will make much sense without that background.

Assuming that you're not going to knit a sweater and celebrate New Year's Eve with Ryan Seacrest and Jenny McCarthy on ABC's “New Year's Rockin' Eve," it's a pretty safe bet to say that you're probably going to consume alcohol—a considerable amount of alcohol.

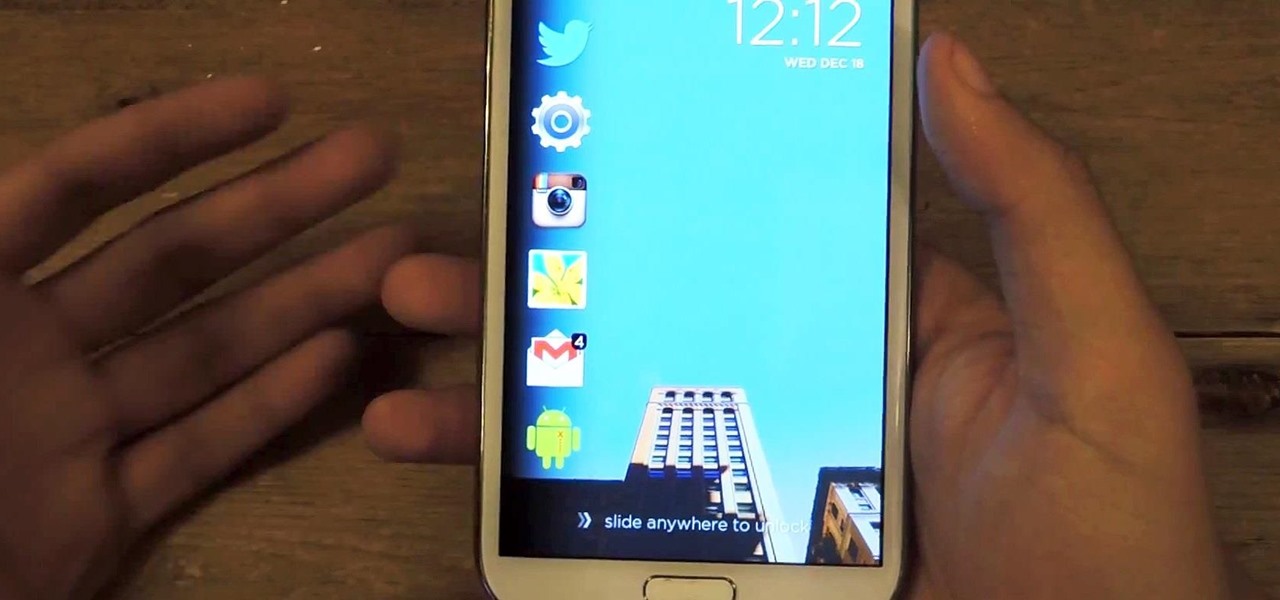
Not particularly good looking, TouchWiz's lock screen adequately supplements the clunky and almost cartoonish-look of the infamous user interface on the Samsung Galaxy Note 2. While there are hundreds of lock screen options in the Google Play Store, I've never quite discovered one that I've thoroughly enjoyed, due to the obfuscation from so many options.

Twitter's video-sharing app, Vine, had some very stiff competition once Instagram added video sharing to its repertoire. Recent figures show Instagram at 130 million followers compared to Vine's 40 million. Many think that Vine is on its way out, but on the contrary, I think it's here to stay.

Last summer, Universal Pictures released the sequel to the popular 2010 animated film Despicable Me, bringing back everyone's favorite characters—the Minions. They're adorable, yellow, and they speak a gibberish "Banana Language." What's not to love? If you're planning on dressing yourself (or your kids) as Minions for Halloween this year, you'll be in good company. There are tons of costumes out there you can buy or make, and here are five of the best DIY options for you.