Very often we have processes in Linux that we want to always run in the background at startup. These would be processes that we need to start at bootup and always be available to us.

The Google Play Store hosts the largest collection of mobile apps on the planet, and it's the default app store for almost all Android devices. Ironically, though, while Google made its name with a powerful search engine, it can sometimes be difficult to find what you're looking for on the Google Play Store.

Welcome to an introduction on writing basic malware, an optional sub-series in which I expose you to malware and its technologies. This is written for those who wish to seek a beginning in malware analysis or enlightenment on the subject. We will be justifying the writing and covering types of malware.

Welcome back, my greenhorn hackers! The Holy Grail of any hacker is to develop a zero-day exploit—an exploit that has never been seen by antivirus (AV) and other software developers, as well as intrusion detection system (IDS) developers. In that way, you can exploit systems with your newly discovered vulnerability with impunity!

When attempting to compromise a target, we want as much control as possible over the victim. Metasploit's meterpreter allows us to have immense control over the victim, the only issue is that sometimes we can't land a meterpreter. We may only be able to land a standard shell, but fear not, there is a way to upgrade our shell into the all powerful meterpreter!

welcome back my masters , teachers and classmates , in this second part of this 0-day series we will learn the basic of fuzzing, and i bought some gift for nullbyte(a 0 day vuln that will be released today exclusively on null-byte) .

3D Touch is a new feature on the iPhone 6S and 6S Plus that's reinventing the way we interact with our smartphones. With just a little bit of added pressure when tapping on the display, you can perform Quick Actions from an app's home screen icon, "Peek" at emails, stories, and photos in-app, as well as perform other app-specific gestures. Since 3D Touch is such a new concept, here are some of the apps that currently support it, along with the shortcuts you can use.

In the world of breakfast, a great trench of injustice divides French toast and pancakes. Just look at the average brunch menu. While pancakes are treated to a wealth of variety (chocolate chip, silver dollar, blueberry, banana, and even some with pop culture references), French toast is often regarded with a one-size-fits-all attitude.

Offensive pictures, depressing tweets, political statuses, and just plain old dumb comments are only a few of the reasons why people unfriend or unfollow others on social media sites. Sometimes it's just social spring cleaning, other times there's no reason at all.

Apple's iOS 15.4 update for iPhone is out after 46 days of beta testing, and it has some exciting features you won't want to miss. Here's everything you need to know about the new software.

While Apple was one of the first to integrate LiDAR into mobile devices for depth sensing, headset maker Varjo has developed a truly remarkable feat with its implementation of the sensor.

Last week, Snap powered through a mountain of important software and (shock!) hardware updates, as well as a few very big business partnerships.

Consumers who haven't already delved into the interactive wonders of augmented reality are about to be pushed into the immersive waters by market forces.

With non-fungible tokens (NFTs), particularly those that are 3D in nature, holographic displays are becoming more indispensable for those looking to show off their valuable works of art.

Sure, Snapchat AR Lenses can be fun, but they can help communicate complex issues as well. While our Facebook news feeds were filled with references to 311 Day, March 11 is also World Kidney Day, the United Kingdom's National Health Service Blood and Transplant (NHSBT) used the occasion to educate its constituents about organ donation.

As businesses flocked to Zoom, Microsoft Teams, Google Meet, and other video conferencing platforms to bridge the gap, we wondered aloud -- why aren't more companies leaning even more heavily on augmented reality?

The virtual collaboration tool known as Spatial has consistently been one of our favorites due to its ability to leverage high-end augmented reality headsets to more easily facilitate remote meetings.

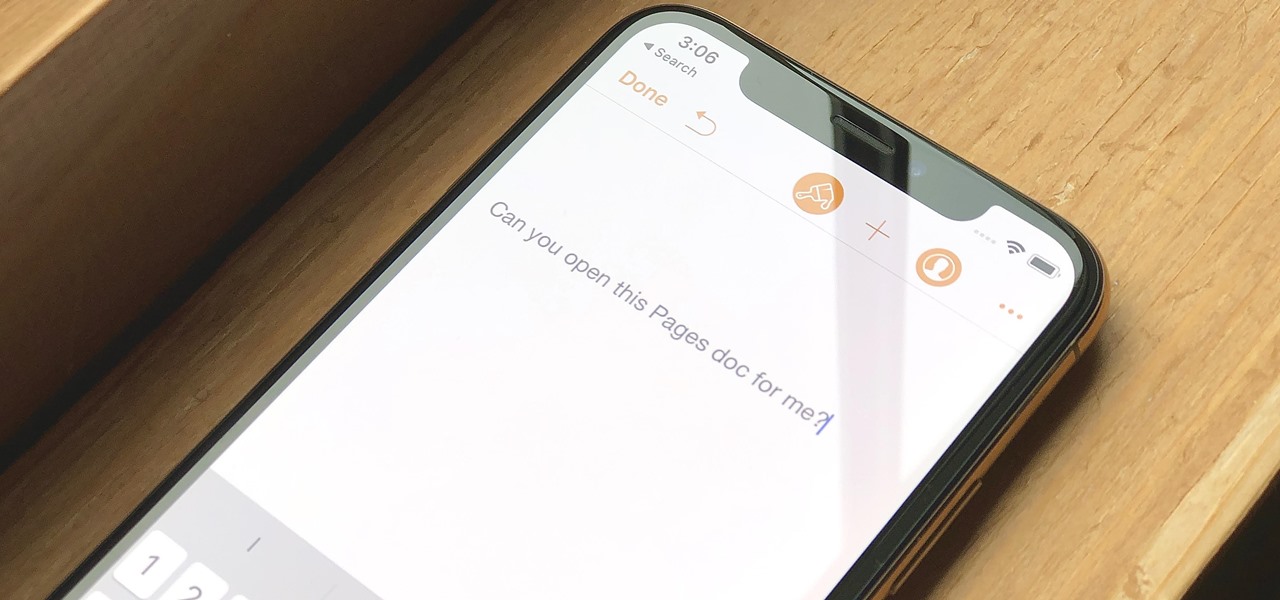
Let's say you have an important report to submit, but you want to check it over for any last-minute edits or changes. Times running out, and you simply can't find this Pages document anywhere. Wouldn't it be great if you could just ask your iPhone to open the report for you, so you could stop wasting time searching and finish the paper? Well, thankfully, Siri can help you out with that.

Firewall solutions for macOS aren't impervious to attacks. By taking advantage of web browser dependencies already whitelisted by the firewall, an attacker can exfiltrate data or remotely control a MacBook, iMac, Mac mini, or another computer running macOS (previously known as Mac OS X).

In the technology space, there are certain brands you grow to depend on. Whether it's due to a long, multi-decade track record of success, or new innovations that blow you away, some tech names accrue a rare kind of brand equity with users that's difficult to earn.

By far the most significant development for AR in the coming months and years — the development that will drive AR adoption — will be our reliance upon the AR cloud.

The year in augmented reality 2019 started with the kind of doom and gloom that usually signals the end of something. Driven in large part by the story we broke in January about the fall of Meta, along with similar flameouts by ODG and Blippar, the virtual shrapnel of AR ventures that took a wrong turn has already marred the landscape of 2019.

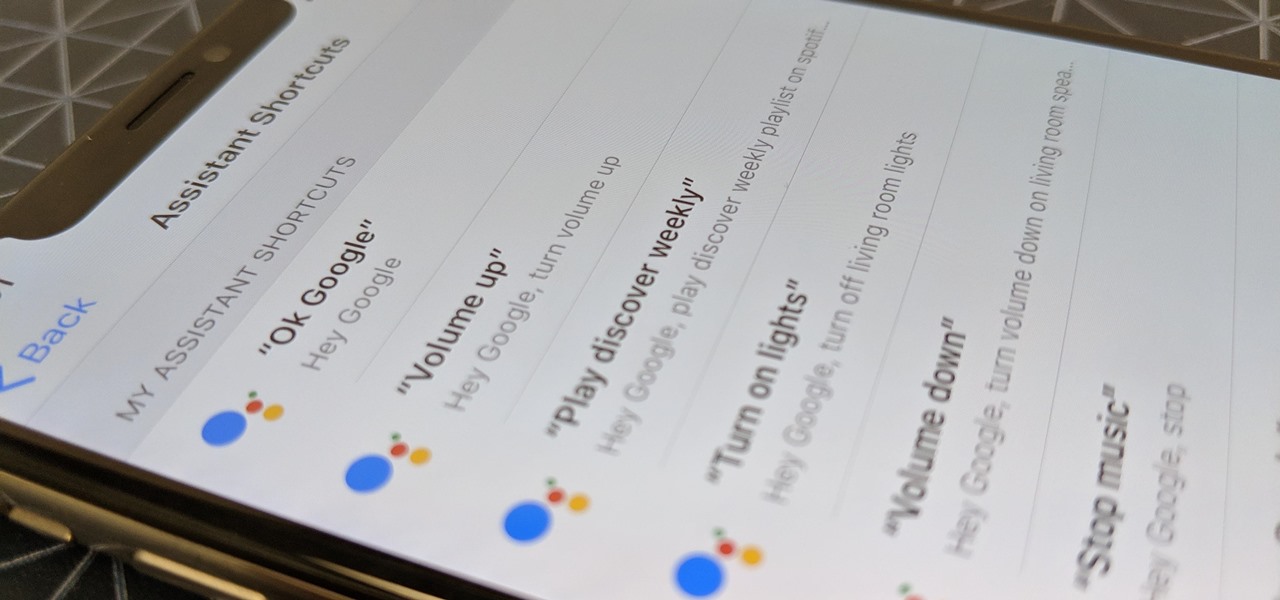
Using Siri to perform tasks on your Google Home device was never possible until Apple released Siri Shortcuts in iOS 12. Actually, it wasn't possible until Google added support for Siri Shortcuts for Google Assistant in Nov. 2018. No matter the timing, the important thing here is that you can use Siri to command Google Assistant which, in turn, can command Google Home.

On Monday, Apple unveiled its Apple Card, the company's boldest move yet toward becoming a truly mainstream mobile payments company. And the product has vast implications for our augmented reality future, some of which may not be immediately obvious to many.

Among the younger generation, Roblox rivals major titles like Minecraft as one of the most popular online games out there. In fact, it's common to hear children tell new playmates to "friend me in Roblox!" so they can play together online. There's nothing inherently sinister here, but with all the online interaction, kids' safety becomes a factor.

There is no shortage of defenses against cross-site scripting (XSS) since it is so prevalent on the web today. Filters are one of the most common implementations used to prevent this type of attack, usually configured as a blacklist of known bad expressions or based on regex evaluation. But there is hope with a wide variety of techniques that can be used to defeat these filters.

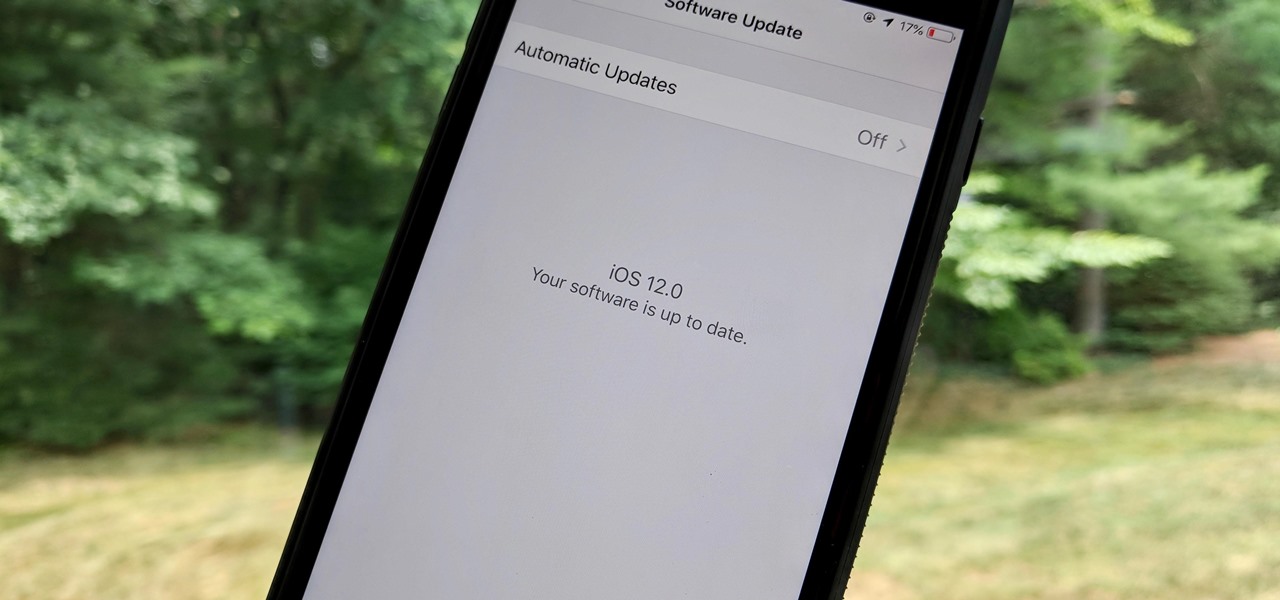
While the iPhone XS and XS Max come equipped with 4 GB of random access memory, and the iPhone XR with 3 GB of RAM, Apple's latest flagships are still susceptible to occasional slowdowns in performance in iOS 12. This can be fixed by clearing RAM, but the process is now a little trickier compared to iPhones with Home buttons.

After the first image leaked of the upcoming successor to the Razer Phone, many were taken aback by its design, specifically how familiar it was. Last year's Razer already stood out with its boxy design and large bezels, and many thought the successor would change this. It didn't. But what if the reason for the familiar form factor is a project they teased earlier in the year?

Web 2.0 technology has provided a convenient way to post videos online, keep up with old friends on social media, and even bank from the comfort of your web browser. But when applications are poorly designed or incorrectly configured, certain flaws can be exploited. One such flaw, known as CSRF, allows an attacker to use a legitimate user's session to execute unauthorized requests to the server.

As the official release of iOS 12 nears closer each day, Apple continues to update its betas. The company released the fourth beta of the upcoming software to developers Tuesday, July 17, exactly two weeks after the release of the third developer beta which came out just a few days before the second public beta.

Magic Leap CEO Rony Abovitz doesn't engage in tweetstorms often, but when he does, those tweets are bold, exceedingly confident, and there's usually a strong takeaway regarding what the company is or isn't doing. But on Thursday, Abovitz's latest tweetstorm sent an unusually flustered message: We promise, the magic we're telling you about it better than anything you've seen on video.

A new study published by American University demonstrates how Pokémon GO and other augmented reality games can help city governments bring communities closer together.

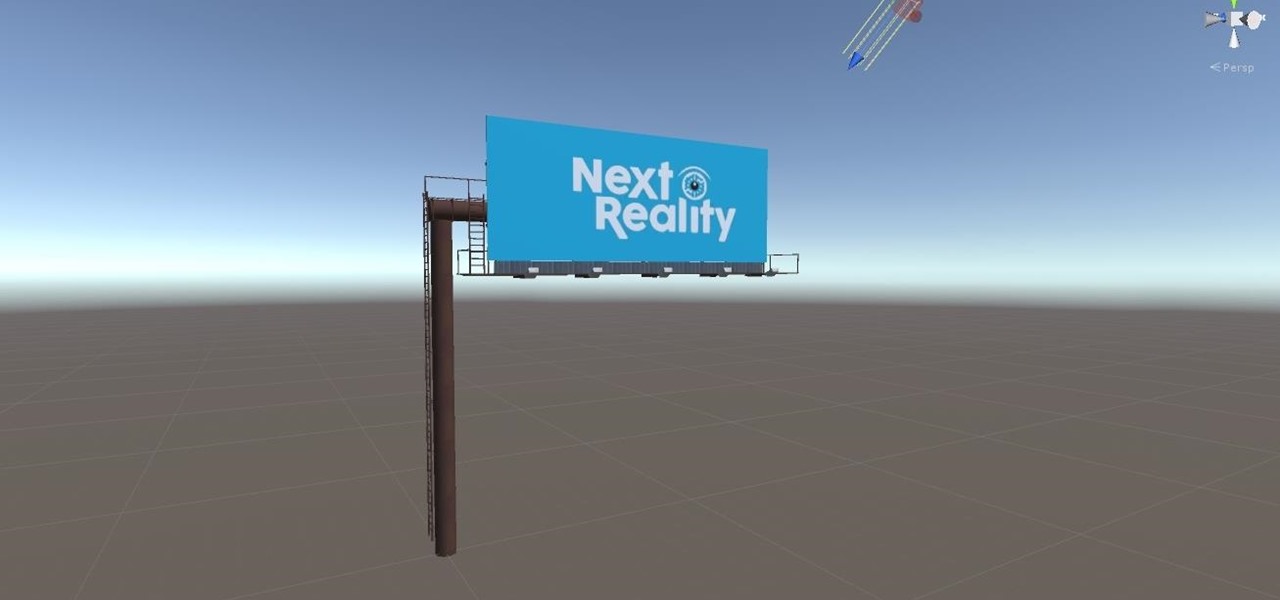
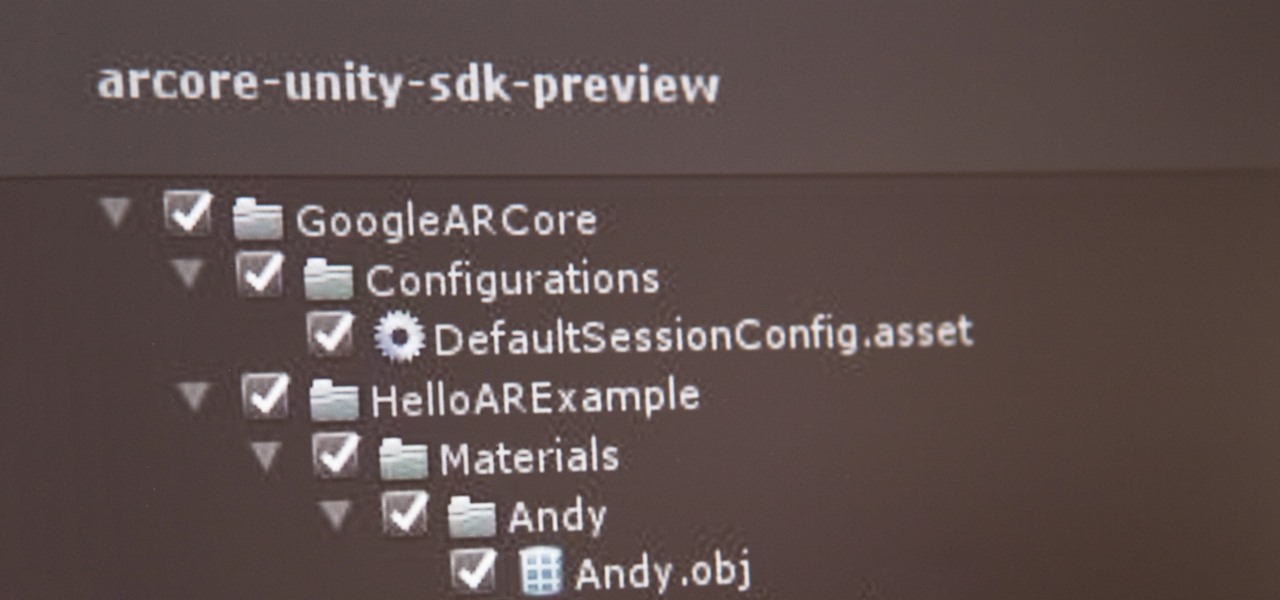
With the software installation out of the way, it's time to build the framework within which to work when building an augmented reality app for Android devices.

If you've contemplated what's possible with augmented reality on mobile devices, and your interest has been piqued enough to start building your own Android-based AR app, then this is a great place to to acquire the basic beginner skills to complete it. Once we get everything installed, we'll create a simple project that allows us to detect surfaces and place custom objects on those surfaces.

After more than a year and a half of silence, the rumors have morphed into reality: Microsoft has finally released an update for the HoloLens. And with that update comes a collection of new features that hint at big plans for the HoloLens this year.

When your iPhone is being sluggish, one thing you can do to get performance back up to snuff is clear the device's random access memory. It's not a publicized feature from Apple, but it's there nonetheless. And while it's easy enough to utilize on iPhones with Home buttons, the iPhone X is a little trickier.

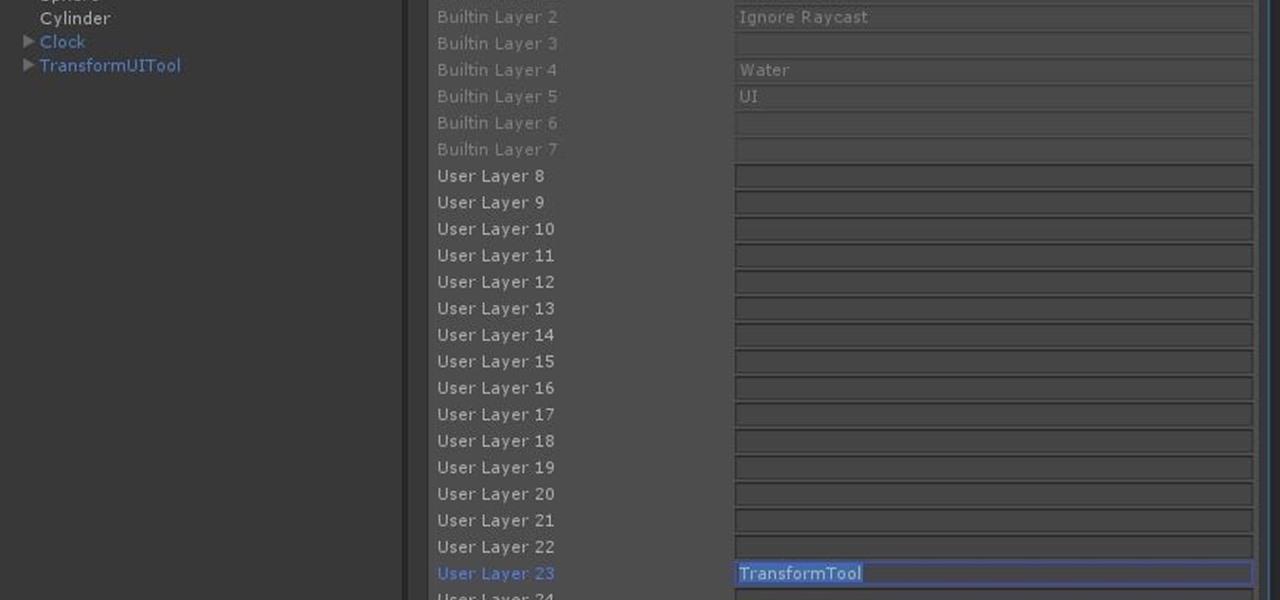
So after setting everything up, creating the system, working with focus and gaze, creating our bounding box and UI elements, unlocking the menu movement, as well as jumping through hoops refactoring a few parts of the system itself, we have finally made it to the point in our series on dynamic user interfaces for HoloLens where we get some real interaction.

Hak5's products get a lot of attention. Popping up in popular shows like Mr. Robot, their hacking tools are bold proof of concepts with space built into the design for the community to add their own tweaks and modifications. On Friday, Oct. 27, Null Byte attended the Hak5 release event in San Francisco to check out their latest devices, including the new Packet Squirrel.

Now that we have unlocked the menu movement — which is working very smoothly — we now have to get to work on the gaze manager, but first, we have to make a course correction.

The Pixel 2 is a solid upgrade when compared to the 2016 model, but we've reached a point where the latest generation of a smartphone is never leaps and bounds better than the last. It's hard to justify dropping nearly a grand on a phone when it doesn't improve your situation much — especially when a few software tweaks will give you most of the upgrade for free.