A man-in-the-middle attack places you between your target and the internet, pretending to be a Wi-Fi network while secretly inspecting every packet that flows through the connection. The WiFi-Pumpkin is a rogue AP framework to easily create these fake networks, all while forwarding legitimate traffic to and from the unsuspecting target.

Since its debut 9 years ago, the iOS App Store has always had roughly the same functionality: Featured apps, categories, top charts, a search function, and a place to update your apps. But starting with iOS 11, that's all changing — drastically.

Sometimes it's impossible to concentrate — let alone direct your personal assistant Siri — when someone is blasting music on their phone or talking to thin air. I mean I'm loud, but not that loud.

Paranoid Android has always been one of the most popular custom ROMs because of the inventive features its developers add to Android. Two of the biggest draws in particular have to be the "Halo" notification bubble, and the "Pie" navigation buttons, which can both fundamentally change the way you interact with your device.
When Google issues an Android update, the changes are usually all over the place—fixing issues, adding functionality, playing catch-up with the latest thing Apple added to iOS. It's how the smartphone wars have evolved, where the two competing operating systems continually match and one-up each other.
Google Photos is one of the best photo management services out there. It allows you to back up an unlimited amount of high-quality images without ever paying a dime, the photos and videos sync flawlessly across all of your devices, and its neural network-powered visual search feature seems like something that was pulled directly out of a Sci-Fi movie.

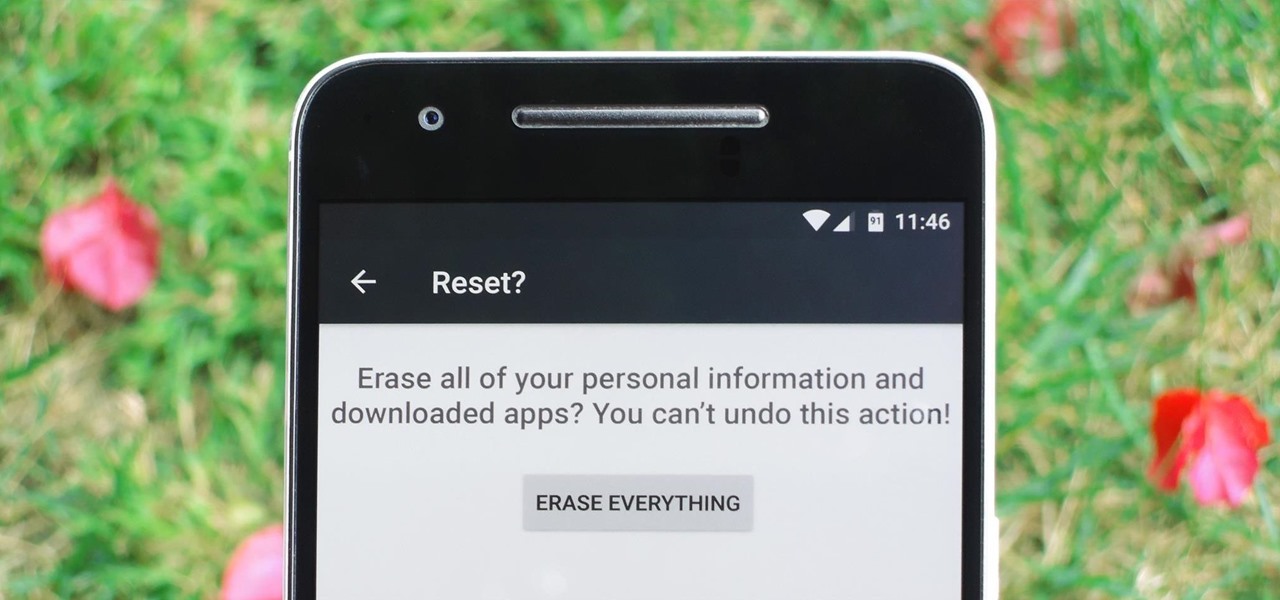
Whether you're performing a factory reset to get your device ready for sale or trade-in, or you're wiping your device in the hopes of fixing software issues, there's a right way and a wrong way to go about it. Sure, it seems like a simple task on the surface, but if you're not careful, you could end up wasting a lot of time or losing precious data.

The only knock on Samsung's last round of flagship devices is that TouchWiz is still alive and kicking. Aside from this overbearing skin that's been applied on top of Android, the Galaxy S6, S6 edge, Note 5, and this year's Galaxy S7 models are some of the best phones money can buy.

Very often we have processes in Linux that we want to always run in the background at startup. These would be processes that we need to start at bootup and always be available to us.

Welcome back, my neophyte hackers! Digital forensics is one of the fields often overlooked by aspiring hackers. In a rush to exploit every and any system they can, they often ignore learning digital forensics—the field that may lead to them being traced.

Welcome back, my novice hackers! More and more, the world is turning to and adopting the smartphone platform as the digital device of choice. People are not only using smartphones for voice communication, but also web services, email, SMS, chatting, social networking, photography, payment services, and so on.

Not too long ago, Sony was looking to create a method for theming the interface of their Xperia smartphones and came up with a framework called Runtime Resource Overlay (RRO). They then contributed this framework to Android's main code base, and Google has since taken over the development of RRO as a way for manufacturers to implement themes in their skinned versions of Android.

Welcome back, rookie hackers! We recently began an exploration of ways to hack using the Bluetooth protocol. As you know, Bluetooth is a protocol that connects near field devices such as headsets, speakers, and keyboards. Its minimum range is a 10-meter radius (~33 feet) and maximum is at 100 meters (~328 feet).

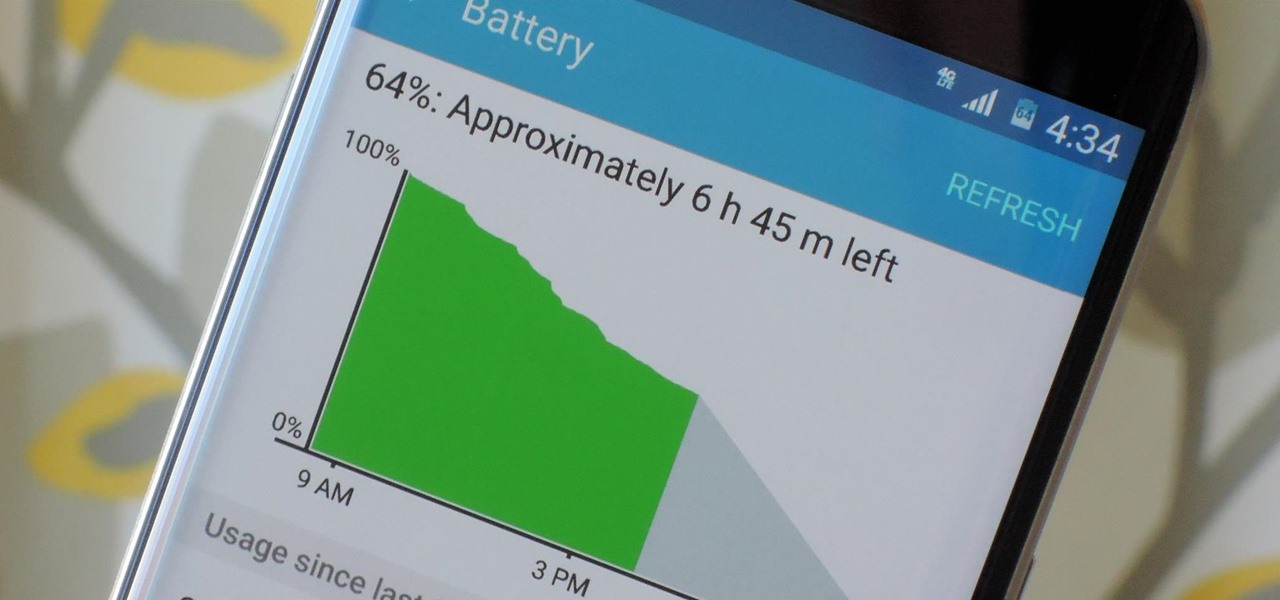
Smartphones have otherworldly specs these days, so it's relatively uncommon that you hear someone complaining about display resolution, build quality, or general speed and performance. At best, these are secondary concerns, with the number 1 issue almost unilaterally being battery life.

There are plenty of legitimate reasons that you might want to record a phone conversation. Let's say you operate a business and take orders over the phone, and you don't want to miss an item. Or perhaps you need to jot down some notes from a recent conference call, and things were just happening too quickly in real time.

These days, operating systems are becoming more and more touch-oriented, or at the very least, heavily mouse-driven. Nonetheless, while novice users will find it easier to tap and click their way around, power users know that keyboard shortcuts are still the fastest way to get things done.

Man-in-the-Middle attacks can prove to be very useful, they allow us to do many things, such as monitoring, injection, and recon.

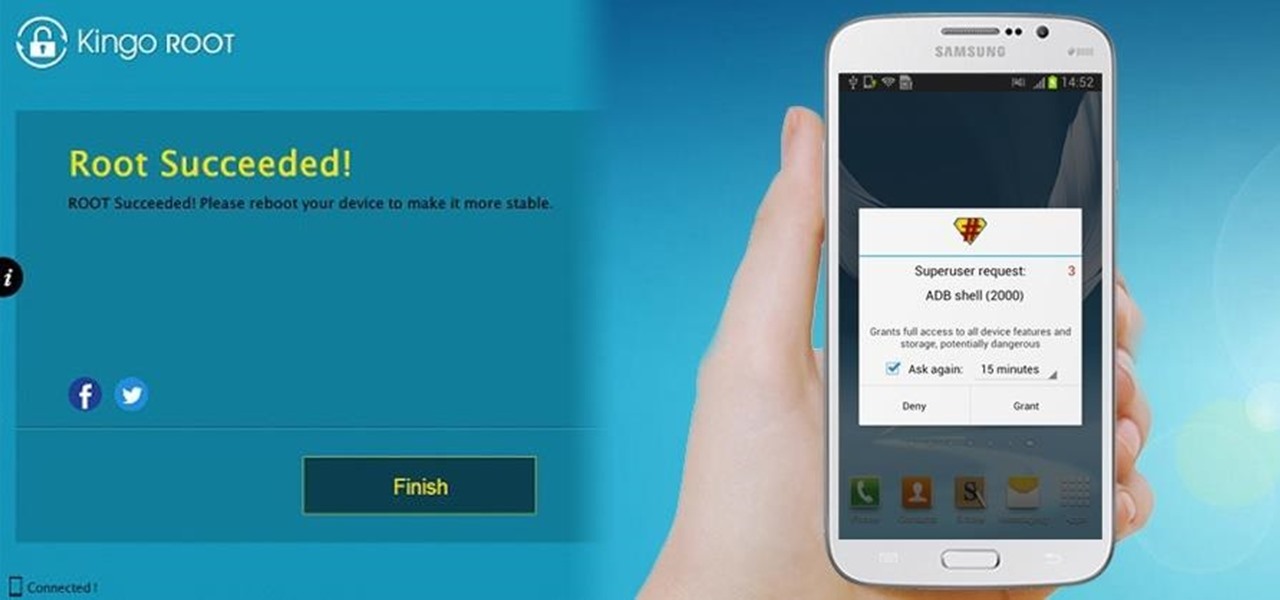
To Android users, especially advanced ones, rooting their phones or tablets is becoming a necessity. Rooting Android could be complicated, if you do it all by yourself, even with a step-by-step tutorial. However, what Kingo Android Root offers you is a true one-click experience when rooting your Android.

When it comes to getting your computer and smartphone to work well together, there's no service more robust and capable than AirDroid. For years, it's been the go-to tool for users looking to transfer files between their devices or access contact lists and call logs from their computer.

It's that time of year again, folks. Each fall, Google debuts a new device alongside the latest iteration of its mobile operating system—but this year marked the release of three new Nexus gadgets.

With Safestrap bringing custom recovery functionality to the AT&T and Verizon Wireless variants of the Samsung Galaxy S5, it's high time we covered this process for all other versions of the GS5.

When the Samsung Galaxy S5 launched a few months ago, I was pretty envious of the new UI elements Samsung included on it, as I'm sure you were. The flatter interface provided for a more polished and less cartoony feel, bringing the device more in line with Google's design elements.

This year's I/O was all about bringing Android into the future and onto new devices. On top of announcing the upcoming "L" release of its mobile OS, Google showcased Android Wear, Android Auto, and Android TV.

It's the biggest day of the year for all things Google. Their developer conference, dubbed Google I/O, gives us a peak at what the guys at Mountain View have been working on over the course of the past year, and this year, Android was center stage.

Back in August, Google introduced Android Device Manager. This new service allowed you to locate, lock, or wipe a lost or stolen Android device from either a companion app or a web interface. Effectively, this is the "kill switch" that legislators are clamoring for.

When OS X Yosemite was first announced, there were a number of features that struck my attention, but one in particular that stood out above them all was the ability to make and receive texts and phone calls from your Mac, which Apple calls Continuity.

Now that Hangouts is Android's default messaging app, it's given us a lot of cool new features. A bouncing ellipsis lets you see when the other party is typing, and an indicator shows you whether they've read your message or not. You can even answer the age-old question of "Where you at?" with a tap of a button, sending a map of your location.

Nokia's recent foray into the world of Android brought a plethora of goodies along with it. The Finnish smartphone manufacturer offers a slightly different take on our favorite mobile operating system, with customizations ranging from ringtones to its very own app store.

Seemingly lost in the fanfare of the numerous features and specs of the Nexus 5 were a few highly innovative and handy add-ons—a low-power step detector and step-counting sensor—useful for tracking fitness data.

Unless you like paying exorbitant prices for out-of-contract phones, most of us are stuck with the one we already have for two or more years. The tech industry moves fast, and as new phones are released seemingly every month, your Samsung Galaxy S4 might start looking older by the week.

Welcome back, my rookie hackers! When Wi-Fi was first developed and popularized in the late '90s, security was not a major concern. Unlike wired connections, anyone could simply connect to a Wi-Fi access point (AP) and steal bandwidth, or worse—sniff the traffic.

Welcome back, my fledgling hackers! In one of my recent articles, I showed you how to install BackTrack as a dual boot system on a Windows computer. In this tutorial, I will walk you through BackTrack, giving you a tour of the most salient features for the hacker-to-be.

Captioning your YouTube videos not only makes them more acessable for the hearing impaired, but they also make the contents of your video more accessible to YouTube. Once YouTube knows exactly what is being said it your video you will be more likely to rank when people search for related words or phrases.

After a two-month delay, Apple has finally released iTunes 11, which was initially slated to be released alongside iOS 6.

Automator is a built-in Mac utility found in Mac 10.4+ and can be used to convert a PDF file to text format.

The new Windows 8 is set to launch on October 26th, and developers and early adopters are still getting used to the new interface. Windows 8 borrows a lot of its functionality and look from the touchscreen-friendly Windows phones. As with Windows phones, Windows 8 uses the now ubiquitous tiles as part of the new Metro Desktop. These tiles, much like the vintage iPhone icons, can get a little stale. But unlike the iPhone, Windows 8 users can in fact create custom tiles in their own without any...

This is my first contribution in an ongoing series on detailing the best free, open source hacking and penetration tools available. My goal is to show you some of the quality tools that IT security experts are using every day in their jobs as network security and pen-testing professionals. There are hundreds of tools out there, but I will focus and those that meet four key criteria:

Instagram is one of the hottest mobile apps to date, yet they have no way to upload photos straight from your computer. You can log into the Instagram web app to like and comment on photos in your feed, but that's about it. Fortunately, there are third-party apps that let you do more on Instagram from your Mac or Windows computer, so you can enjoy Instagram pics on the big screen instead of your tiny iPhone or Android device.

Apple just released the third public beta for iOS 14 today, Thursday, July 23. This update comes one day after the company released iOS 14 developer beta 3, and two weeks after the release of iOS 14 public beta 2.

Apple just released iOS 14 developer beta 3 for iPhone today, Wednesday, July 22. The update comes 15 days after Apple released the second developer beta for iOS 14, and 13 days after the release of iOS 14 public beta 2.