With a cheap computer, smaller than the Raspberry Pi, an attacker can create a remote hacking device. The device can be attached to a target router without anyone's knowledge and enable the hacker to perform a variety of network-based attacks from anywhere in the world.

On Tuesday, the smartglasses startup known as North finally took the wraps off its Focals product, but in a very unique way: The team simply opened a couple of stores and invited the public in.

Our national month-long celebration of all things creepy and crawly comes to a climax on Wednesday with Halloween and will end with Día de Muertos on Friday, so now is the ideal time for the The New York Times to publish a mildly chilling augmented reality story for children.

New York-based startup CTRL-Labs has closed a $28 million Series A round of funding from Google parent Alphabet's GV and Amazon's Alexa Fund, among others, for its next-generation neural interface technology for AR/VR and robotics.
When playing word association with Star Trek, the first thing to come to mind with regards to augmented reality is likely Holodeck, not The Game, an obscure episode from season five of Star Trek: The Next Generation.

Welcome back everyone. I apologize for the lack of training articles, but I've been rater busy lately. I've recently picked up a second job and my college courses are now back in session, so I'm a bit strapped for time.

Long time reader, first time 'How To' poster. This tutorial has been highly requested. Here are the steps to perform a Pixie Dust attack to crack a WiFi password that has WPS enabled.

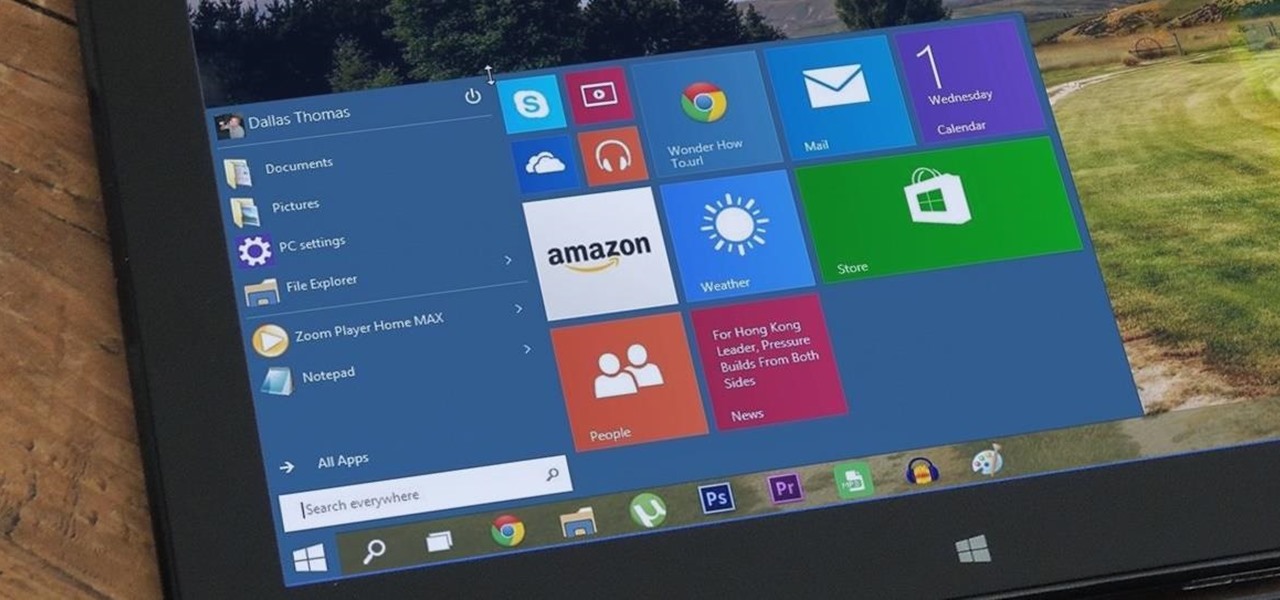
At a closed-door presentation on September 30th, 2014, Microsoft unveiled the latest iteration of its industry-leading operating system. Dubbed Windows 10 (seems as if Redmond isn't too fond of the "9" moniker), this new version brings along with it many UI optimizations and under-the-hood tweaks. With a particular focus on optimizing the interface for traditional mouse and keyboard computers, one of the most noticeable changes is the return of the Start Menu. While touch-optimized devices wi...

Welcome back, my apprentice hackers! As many of you know, I have been hesitant to adopt the new Kali hacking system from Offensive Security. This hesitancy has been based upon a number of bugs in the original release back in March of 2013 and my belief that BackTrack was easier for the novice to work with.

Within the coming months, software startup Neurable plans to introduce the next paradigm in virtual and augmented reality: the brain–computer interface (BCI).

Now that Google Assistant is coming to all devices running Android Marshmallow or higher, roughly one out of every three Android users will no longer be able to access the old Google Now interface. The Assistant, which was previously exclusive to Pixel devices, takes over your home button long-press gesture and completely replaces all of the old Google voice search functionality.

Ever since the Google Play Store removed its "Designed for tablets" section, it's been a lot harder to find good, tablet-optimized Android apps. Not that it was all that great to begin with considering that they used to list apps like Facebook and Twitter, which only have oversized phone UIs on tablets, not actual customized UIs.

Welcome back, my greenhorn hackers! Sometimes, we don't have a specific target in mind, but rather we are simply looking for vulnerable and easy-to-hack targets anywhere on the planet. Wouldn't be great if we had a search engine like Google that could help us find these targets? Well, we do, and it's called Shodan!

Scosche Industries offers this instructional users guide for its TA07 radio replacement interface in a 2007 Toyota Tundra. The TA07 will work with select 2004 and up Toyota vehicles equipped with JBL and JBL Synthesis systems. The TA07SR radio replacement interface was designed to make installation of any brand name aftermarket head-unit simple. The TA07SR allows the customer to replace the factory head unit with an aftermarket head unit and utilize their factory amplifier without having to "...

There are a surprising number of hidden features in your iPhone's Phone app, from secret dialer codes that provide info or perform actions to special characters that dial extensions automatically. However, there's one little-known trick every iPhone owner should know when using the Phone app for calls — and it's the simplest and most useful of them all.

Magic Leap has done a great job of aggressively releasing new apps, software updates, and major franchise tie-ins. But aside from all the creative and entertainment apps, what's it like to use one of the apps the company hopes you'll use every day?

When you're playing videos, the actual content should be the focus, not the media app's interface. But with VLC's default theme on Android, the bright orange-and-white motif shocks your eyes in a dimly-lit setting and draws your attention away from what really matters. Let's change that.

In the music world, it's safe to say electric instruments are more versatile, but they lack the portability of their acoustic counterparts. However, with the aid of your smartphone plus an audio interface, you can play your electric instrument anywhere — with all the pedal effects you please — and even record your efforts.

With any continuously active software, it can start to become fairly complex after a few years of updates. New features and revisions both get layered into a thick mesh of menu systems and controls that even pro users can get bewildered by. If you are new to a certain application after it has been around for many years, it can be downright intimidating to know where to begin.

CyanogenMod has been building upon open-source AOSP apps for many years now. They've made improvements to apps like the stock SMS client, the stock Audio Mixer, and a whole slew of others.

After installing Ubuntu as your primary OS, you should have protected against USB Rubber Ducky payloads, defended against hard drive forensics, and reduced the overall attack surface against physical strikes. When defending against network-based attacks, you'll want to minimize hardware disclosures, prevent packet sniffers, harden firewall rules, and much more.

One of the first things you'll notice about iOS 11 is how the Notification Center now has the same interface as your lock screen. It's pretty confusing at first, and it's pissed off tons of users, but it's really not that bad once you learn all of its features.

When you're sitting at your desk trying to get some work done, your Android device can be a big distraction. If a text comes in, you have to pick up your phone, unlock it, then respond with the clumsy touch screen keyboard—and by then, you've probably forgotten what you were doing on your computer.

Android has a built-in browser called WebView that any app can use, which makes it easy for developers to display webpages without actually having to build an internet browser into their apps. But WebView is a stripped-down, bare bones browser with no ties to Android's default browser, Chrome, so none of your synced data like bookmarks, passwords, and history is available when an app is using WebView to display a page.

Android comprises an entire ecosystem of apps, games, functions, and features, so it would only make sense that it has its own lexicon. Words, phrases, and acronyms that didn't exist ten years ago are now used in an off-the-cuff style by developers and support technicians across the web.

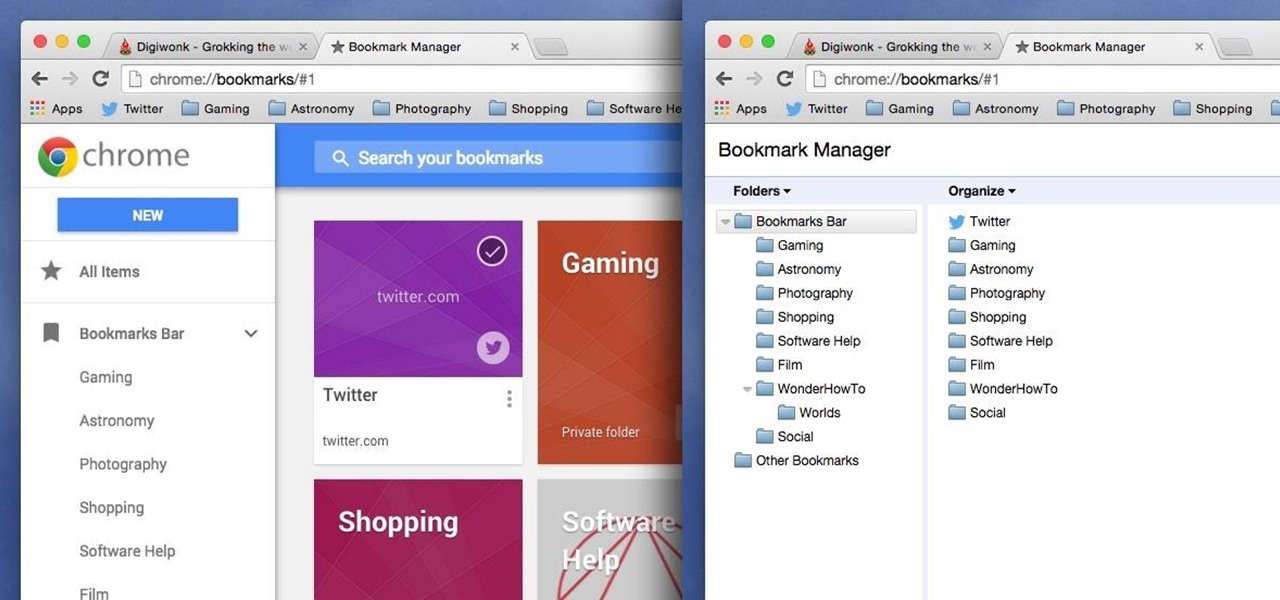
Chrome has been pushing out a lot of new changes lately, but not all of them are as good as they think they are. Earlier this year, there was an update that changed how user profiles worked, which made it harder to actually switch profiles. Luckily, there was a way to get back the old profile management interface, but now there's another "improvement" that you might want to change—Chrome's new Bookmarks Manager interface.

Your phone's volume panel is one part of the user interface that usually goes unnoticed to themers and developers. With themes capable of changing the look and feel of the fingerprint scanner, keyboard, and other system apps, this central aspect of the UI seems to get lost in the shuffle.

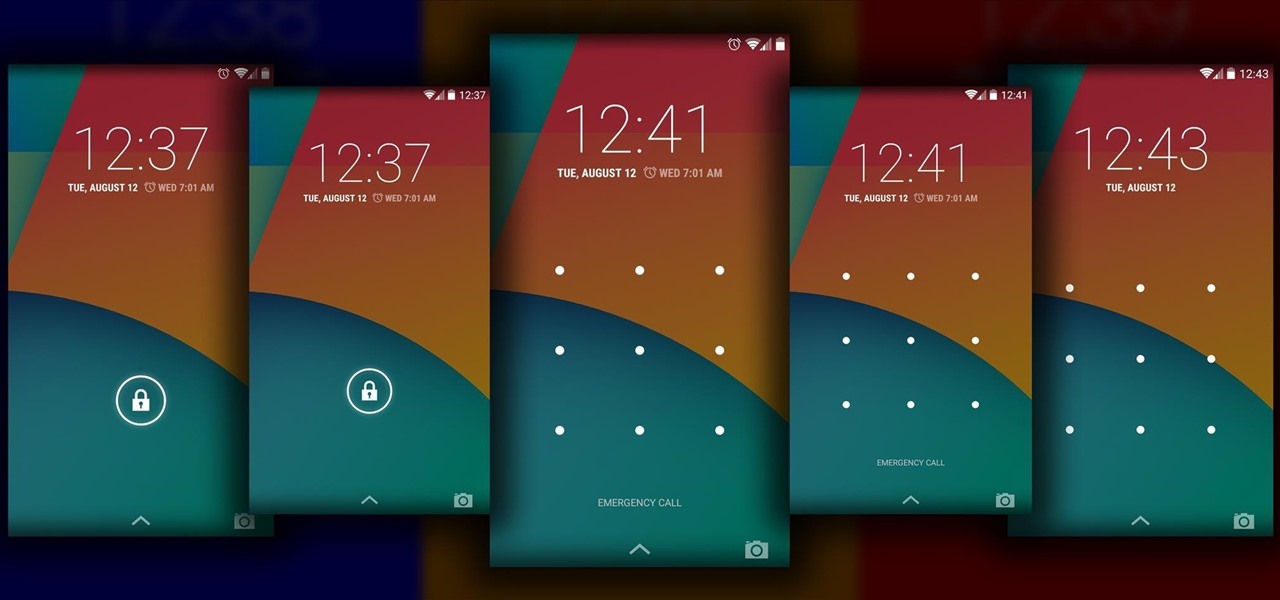
The Android lock screen interface is an integral part of our everyday use. For those of us who use lock screen security, it functions as a barrier between the sensitive data contained within our smartphones and potential outside access. Even if you don't use a pattern or PIN to secure your phone, you still interact with the lock screen every time you go to use it.

Most users don't realize how much valuable data is in their network traffic. With a few simple tools, an attacker can quickly pick out cookies, passwords, and DNS queries from a macOS device as it covertly streams the victim's network traffic to the attacker's system. Here, we will cover two methods for analyzing packets flowing from a Mac.

The default tool for payload generation is MSFvenom, a Metasploit standalone payload generator as well as encoder. This tool is an incredibly powerful tool for payload generation, but it can be difficult and requires a bit of reading for newer users.

When anyone brings up Tasker, the first topic that always gets discussed is how powerful the Android automation app can be. But all of that power can be overwhelming for some people, so even if you're a Tasker pro, it's hard to share your awesome creations with friends that don't quite understand what's going on.

Let's say you're flush with Google Opinion Rewards credits, or you just got a Google Play gift card for your birthday. This is a perfect opportunity to remove ads and unlock new features by upgrading some of your free apps to their paid counterparts, or to finally purchase that app you've been lusting after that doesn't offer a free version.

The price of hacking Wi-Fi has fallen dramatically, and low-cost microcontrollers are increasingly being turned into cheap yet powerful hacking tools. One of the most popular is the ESP8266, an Arduino-programmable chip on which the Wi-Fi Deauther project is based. On this inexpensive board, a hacker can create fake networks, clone real ones, or disable all Wi-Fi in an area from a slick web interface.

Whether you're new to Android or you just haven't kept up on the app scene lately, we hand-picked over one hundred essential apps that are all designed to improve your experience. From custom launchers and icon packs to weather apps and file explorers, there's something for everyone in this list.

The Watch Dogs video game series came out in 2014, enamoring audiences with the idea of a seemingly magical smartphone that could change traffic signals, hack web cameras, and even remotely control forklifts. This may sound like science fiction, but The Sonic uses a customized flavor of Kali Linux to allow you to unleash the power of Kali from any smartphone — all without the need to create a hotspot to control it.

Apple has a new flashlight feature for iPhone models with Dynamic Island on iOS 18. This feature lets you adjust not only the brightness level but also the beam pattern, giving you control over how wide or narrow the light shines.

If you want to carry a variety of network adapters without looking suspicious, a perfect solution is accessing them through Airserv-ng. Tucked away in the Aircrack-ng suite, this tool allows a hacker to plug any number of network adapters into a Raspberry Pi and access them over a Wi-Fi or Ethernet connection.

Trying to figure out which music streaming service to subscribe to can be a difficult task when the playing field is so crowded. Each has its benefits, as well as downsides, so finding the right one for your needs and wants can take a lot of overwhelming research. But we've done all the research for you to help you find the best music subscription your money can buy.

In a previous guide, I demonstrated how to extract images from a security camera over Wi-Fi using Wireshark, provided you know the password. If you don't know the password, you can always get physical with the Hak5 Plunder Bug. Using this small LAN tap, we can intercept traffic like images from a Wi-Fi or IP security camera if we can get physical access to the Ethernet cable carrying the data.