Trimble is integrating its mixed reality applications into the DAQRI Smart Helmet to enable outdoor and on-site support for design, construction, and heavy industry as part of a collaboration the companies announced today.

The rate of preterm birth has been increasing in the United States for unknown reasons, causing increased health risks for infants born too soon. But researchers may have found a signal that could help doctors plan ahead for, or even prevent, early birth with a simple swab of the vagina and cervix during pregnancy.

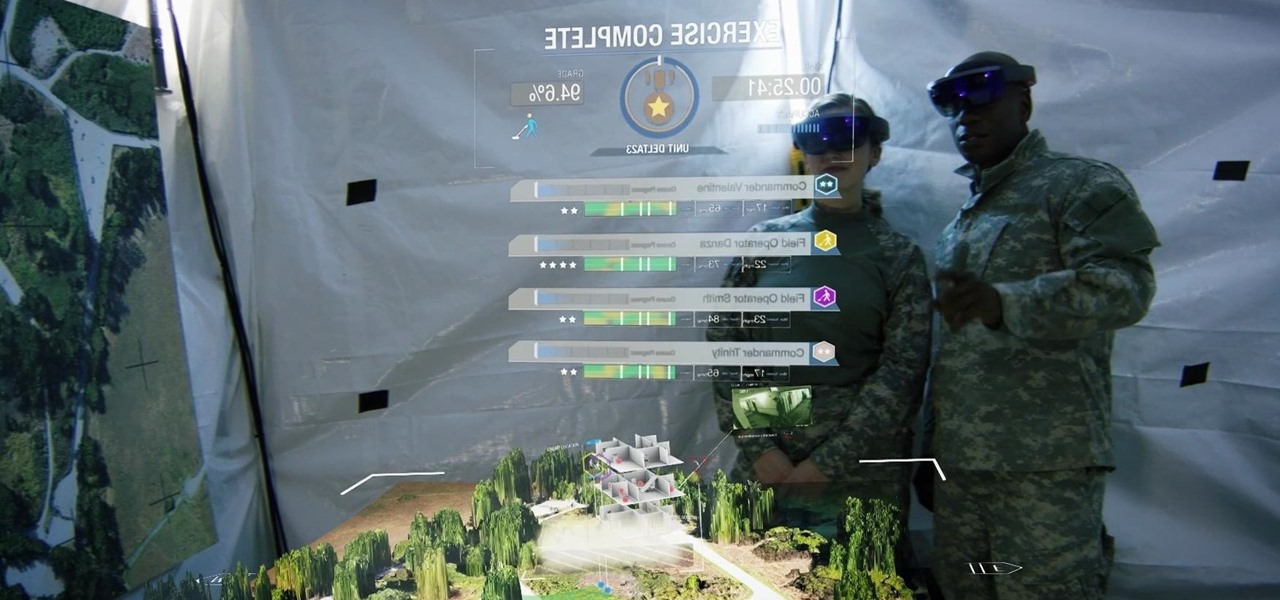
The HoloLens is a natural medium for 3D data visualization, which offers a far more ideal approach over 2D screens to managing multiple resources simultaneously and grasping the bigger picture. We've already seen how management is using holograms to oversee cities, firefighters, and the military, and now training for sports teams is being addressed with VAR Football.

All fields of study have their own language. For people interested in learning about microbes, the language can sometimes be downright difficult — but it doesn't need to be. From antibiotics to xerophiles, we have you covered in an easy-to-understand glossary.
The limitless applications of 3D data visualization will enable a more efficient approach to many of life's problems. Each day, developers exploring this technology are finding new ways to solve these problems in mixed reality; 3D modeling, easier house management, spinal surgery, and forest fire management are just a few recent examples of ways 3D data visualization can benefit us all.

Cyanogen, Inc., the for-profit company that spun off from its CyanogenMod roots several years ago, has announced that they're shutting down all of their services. The company's impending demise shouldn't directly impact many Android users, but the announcement does have one major repercussion: The servers that used to host the popular CyanogenMod custom ROM have now been shut down.

Being able to take screenshots on Android isn't something we were always able to do. It was added to stock Android in Ice Cream Sandwich 4.0 (Gingerbread 2.3, if you were a Samsung TouchWiz user) as a simple full screen screenshot, and that's the way it's remained ever since—until now.

Designing for mixed reality, especially for the HoloLens, can present unique challenges. Dong Yoon Park, a Principal UX Designer at Microsoft with a passion for typography, recently gave a talk to the Windows Holographic Users Group Redmond (WinHUGR) about the pitfalls he ran into trying to convert what started out as a 2D iOS app 5 years ago to the newer 3D Holographic frontier with Unity.

If you've ever been inspired to try out 3D modeling after enjoying computer-generated imagery in video games and movies, chances are you've checked out an paid applications like 3ds Max (previously called 3D Studio Max), or even free ones like Blender, then just went "No Way! It's way too complicated."

With the release of the HoloLens, Microsoft has put itself in both a great position while giving the competition a serious target to aim for. This is normally the case for anyone that is first to the market with a new idea, and now we've finally got a good competitor HoloLens coming. Stereolabs, a company known for its impressive 2K stereo camera, will be entering the mixed reality head-mounted display space with a Developers Kit as soon as early-2017.

We're on the verge of an amazing evolution of technology where we can work and play in virtual worlds that merge with our own—or let us escape into our imaginations entirely. But creating virtual, mixed, and augmented reality experiences requires resources and hardware that not everyone has access to. If you want to build something awesome with the Microsoft HoloLens (or one of the other awesome platforms), we want to help you do just that.

A VPN service is almost an essential these days. Good ones can block ads, prevent tracking cookies, encrypt your internet traffic for better security, and even spoof your device's location to bypass geo-restrictions — all things you should be concerned about in the age of NSA snooping and Facebook data mining.

Welcome back, my hacker novitiates! In the previous part of this series, we looked at how to use Metasploit's web delivery exploit to create a script to connect to a UNIX, Linux, or OS X machine using Python. Many members of the Null Byte community have asked me, "Can we do the same for a Windows systems?" The answer is YES!

Welcome back, NB community, to my series on sorting. I introduced in my last article the concept of complexity. When I say complexity, I'm talking about time complexity.

This article is to all the newbies on here wanting to become a hacker. Since I have seen many newbie questions on here, I need to address this.

I mentioned in 2015 I wanted to start a 'DoXing' series, and since I havent seen this on Null Byte, I am now going to introduce this to the community.

Hello everyone! I'm glad to post my first tutorial and hope you will appreciate it.

Those of you who have been a part of the Null Byte community for even a short while know that I sincerely and firmly believe that hacking is the most important skill set of the future.

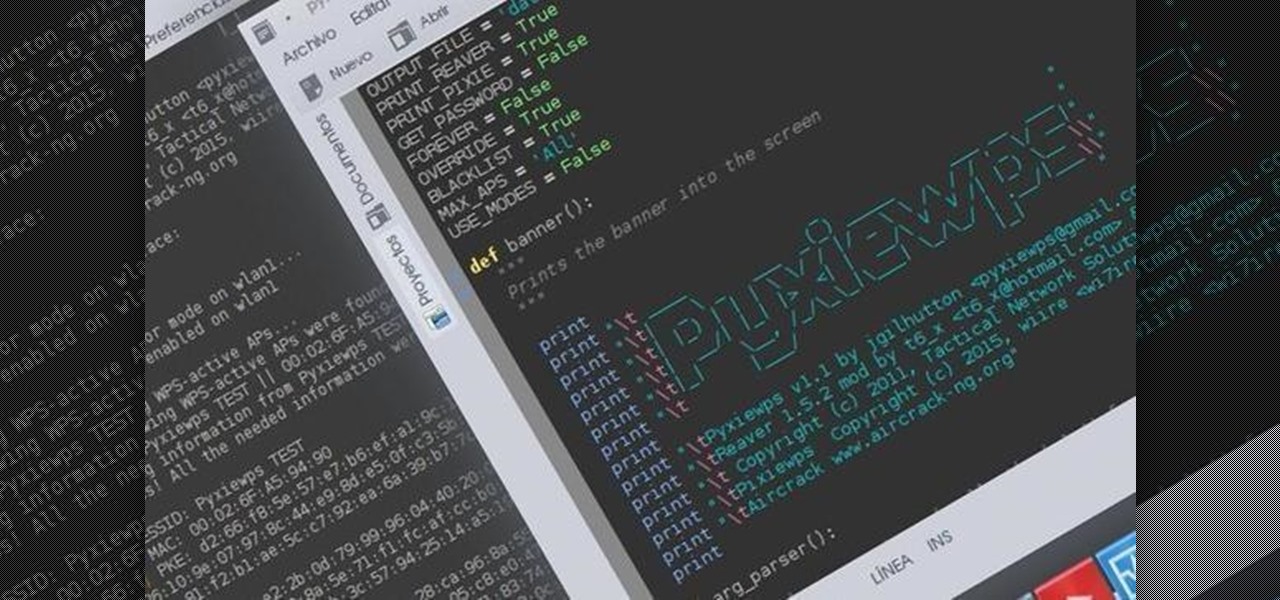
Hello dear friends! I'm jgilhutton and I want to show you guys a Python wrapper I made a few months ago.

Imagine this scenario: You exploited a system using metasploit and you want to install a backdoor. You have a few options;

While its hardware may already be a little outdated compared to newer flagship phones, the OnePlus One is still a great value thanks to the dedicated community that continues to develop ROMs for it. Cyanogen 12 and Oxygen OS are the two most popular ones, but neither offers the type of unique experience you get with Xiaomi's MIUI (pronounced "Me You I").

Food waste is a topic near and dear to my heart, but the truth is, no matter how dutiful we are about finding ways to double-down on food scraps, a lot of stuff goes into the trash needlessly.

Although this century is still young, with little fanfare we may have just witnessed the "Hack of the Century." AV software developer Kaspersky of Russia recently announced that they found that some hackers have stolen over $1 billion from banks around the world!

The Galaxy S6 won't hit shelves until later this spring, but that didn't stop the Android community from working its magic and pulling a handful of apps from the device's stock firmware. Several of these apps rely on framework elements that aren't present on current-generation Samsung Galaxy devices, but the new version of the Smart Remote app can be installed without much difficulty.

Welcome back, my novice hackers! As we saw in my first tutorial on Facebook hacking, it is not a simple task. However, with the right skills and tools, as well as persistence and ingenuity, nothing is beyond our capabilities.

Smartphones like the Nexus 6 and those in the Samsung Galaxy Note series border on being called tablets due to the sheer size of their displays. They are essentially "phablets," i.e., devices too large to be a typical smartphone, yet too small to be a tablet.

Due to their large size and added screen real estate, Apple included a new feature for the iPhone 6 and 6 Plus known as "Reachability." Essentially, this function makes reaching the top part of the display easier by double-tapping the home key to shift the screen down closer to your thumb.

From parents and other family members to friends and peers, personalities are built by environment. Though people are important in the development of our own individual personality, there are other, different influences, including what you choose to read. The books you take the time to enjoy can make you nicer and more understanding, or leave you overall unchanged.

Google's latest Nexus device is big, bold, and beautiful—and now it's got root. Thanks to some quick work by legendary Android developer Chainfire, the Nexus 6 already had a clear-cut root method before most stores even had it in stock.

Welcome back, my greenhorn hackers! Before we attempt to exploit any target, it is wise to do proper reconnaissance. Without doing reconnaissance, you will likely be wasting your time and energy as well as risking your freedom. In previous guides, I have demonstrated multiple ways to perform reconnaissance including passive recon with Netcraft, active recon with Nmap or hping3, recon by exploiting DNS or SNMP, and many others.

I have never been a morning person, and that's a trait that I don't think is going away. Combine my distaste for early hours with being a heavy sleeper, and it adds up to a lot of alarms being dismissed in a haze, with no real intention of ever waking up.

Google's upcoming Android release hasn't even received a name or version number yet, but the third-party development community is already having its way with the firmware.

Hi! Let me get started on this subject as it is a very "touchy" subject. We all want to "hack" these days, and that's logical. Te be real honest here, i was inspired once by the words someone from the Null byte community said. In the (near) future, wars will be ended by computers and not a nuclear missile. That's something i really do believe in. But let us take a defensive measure instead of the offensive one. Sure, Full frontal bryte forcing is an option, but when it'll come that far we'll ...

Due to its constant delays and lack of public invites, the OnePlus One is the equivalent of a unicorn in the Android community. I was lucky enough to win an invite in the OnePlus Storm of Invites promotion and have loved every minute with my new Nexus Killer since receiving it.

Imagine that you're the last person alive. After losing all of your loved ones, you thought you'd never see another human being in your life. Then, they arrive. The hoard of 15-year-old zombies looking for a cute British YouTuber so they may feast on his brains.

Last year, The New York Times wrote that certain restaurants in Manhattan and Brooklyn banned patrons from taking photos of their meals. That means no flash photography, no standing on chairs for a better angle, not even a quick pic for your Instagram followers before the first bite. Little do these restaurants know, this ban can actually make their customers' food taste worse, so to speak.

Yesterday, the Free Software Foundation published an article written by Paul Kocialkowski. A software developer for the the Android fork system Replicant, Paul stated that his organization discovered, and later patched, a "backdoor" vulnerability that existed in older Samsung Galaxy devices, including our beloved Galaxy S3s. Only problem is, it's kind of bullshit—but we'll get to that later.

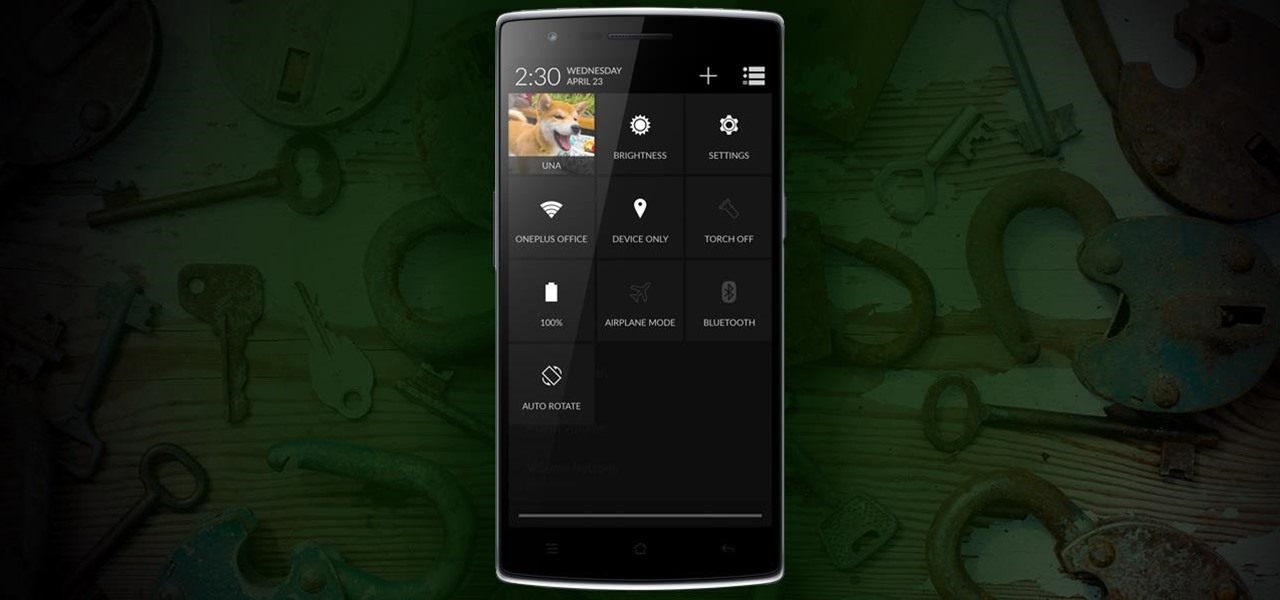
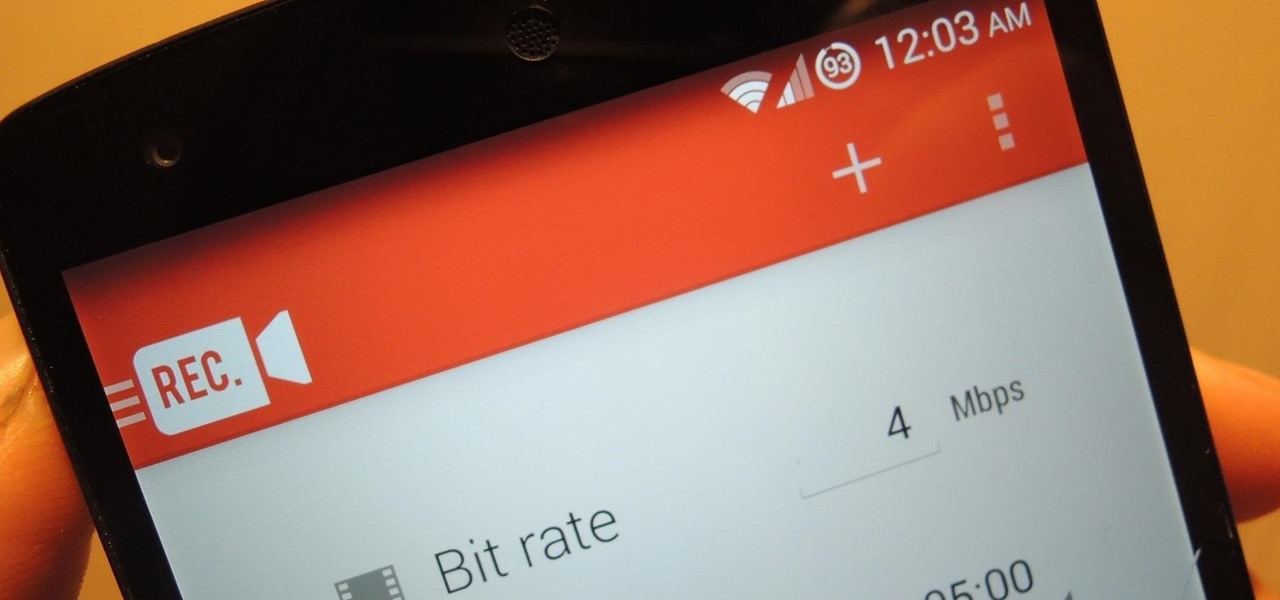
Not too long ago, we told you about a new feature within Android KitKat that allowed for video recording directly from the screen of your Nexus 5. Though functional, the method was a bit clunky and involved hooking your phone up to your computer and sending over an ADB command to start the recording.

In spite of the degree of difficulty it is to install, CyanogenMod has steadily climbed the ladder to become one of the most popular third-party firmwares for Android devices.

Twitter's video-sharing app, Vine, had some very stiff competition once Instagram added video sharing to its repertoire. Recent figures show Instagram at 130 million followers compared to Vine's 40 million. Many think that Vine is on its way out, but on the contrary, I think it's here to stay.