Augmented reality is expected to eventually change everything, and the prevailing view is that those changes will be for the better. The converse view, however, is that the technology will further erode privacy.

Young girls, especially those who live in areas where HIV is epidemic, like sub-Saharan Africa, are particularly vulnerable to becoming infected with HIV. A vaginal ring containing the antiviral agent dapivirine has been shown to decrease the chance of developing HIV-1 in adult women over 21 and now in the first step for use in adolescents, the ring has been shown to be safe and well-tolerated in that younger age group.
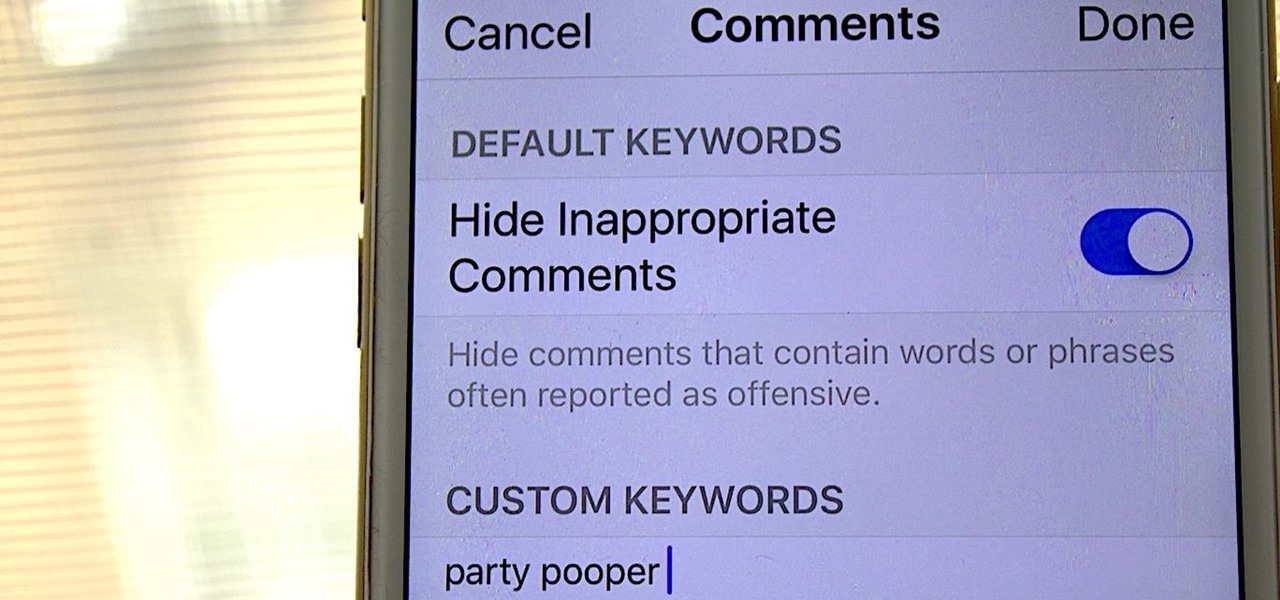
One of my favorite things about Instagram, and the reason why it's still my go-to app, is the fact that it's not like Facebook or YouTube. After our last presidential election, well, I think we've all been scarred from going anywhere near Facebook. And YouTube, I'm not sure why comments on that platform are some of the worst, but they are.

Think of the coolest, most unique way to create art that you can. Got it? Now think about creating that art out of living things.

The Samsung Galaxy Note 8 (or Galaxy Note8, depending on how you like it) is one phone which couldn't possibly have bigger shoes to fill. Samsung's latest flagship has officially been announced, so it's time to decide whether not it's capable of filing the void left by the failed Note 7. From the revealed specifications and details, the Note 8 is turning out to be one device worth pre-ordering.

When the HoloStudy Demo app for HoloLens came out in September, it was a pretty impressive start to what could be a very valuable science tool for education. Now, Moscow-based HoloGroup, makers of HoloStudy, started an Indiegogo campaign to improve their modular teaching app.
In this Tutorial I will show you how you can use the frequency of letters to decrypt the famous Caesar cipher. I hope it is easy to understand and helpful for getting in touch with basic cryptanalysis. If you find any mistakes or have questions feel free to ask me. Finally I ask you to give me feedback which I will take into account for the next part.

In the last tutorial, we learned how to make functions and how they work on the high level. This time, we will take a peek under the hood again, stare deep into its soul and see its ugliness face to face to see how it works in the lower level.

I'm back. School's an ass. On my quest for knowledge, which started approximately 3 years ago, I can upon an interesting little artifact. It is called the Arduino.

This is my first ever how-to so I apologize in advance for any grammar mistakes or spelling errors. Introduction

In python, or any scripting language for that matter, there are certain things that you will carry with you throughout your entire scripting career. Some of the most basic things that you will keep with you are output, variables, and their value types. We'll start by going over output, then cover variables and their types. So, let's get started!

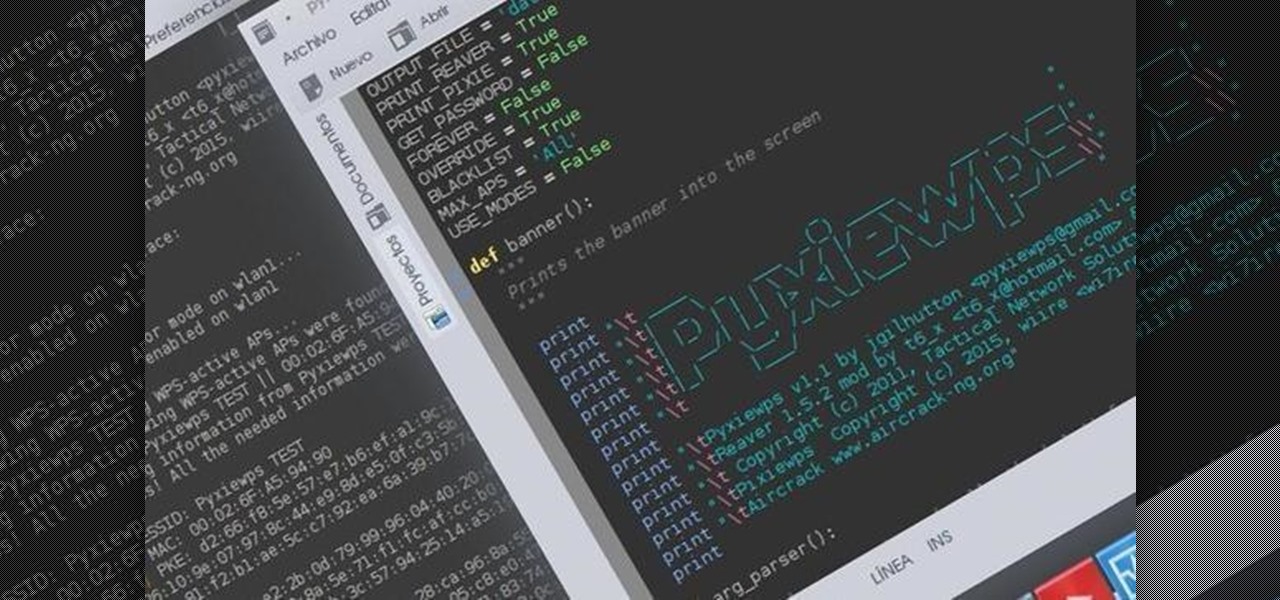
Hello dear friends! I'm jgilhutton and I want to show you guys a Python wrapper I made a few months ago.

After several weeks of testing out the public beta, Apple has finally released iOS 8.3 to the general public. The latest iteration of iOS for iPad, iPhone, and iPod touch serves mostly as an update to fix many of the bugs that plagued earlier versions, but there are still a couple of awesome new features included in the new build.

Welcome back, my novice hackers! This is the third installment of my Python scripting series. If you haven't read the previous two articles, take some time now to go back and read Part 1 and Part 2 before you proceed here.

Today, I want to share a tutorial on one of the most useful but old methods which you could use to hack websites, that is using the Dot net nuke (DNN) vulnerability . I know some of you already know about this method.

Most of you already know that a zero-day exploit is an exploit that has not yet been revealed to the software vendor or the public. As a result, the vulnerability that enables the exploit hasn't been patched. This means that someone with a zero-day exploit can hack into any system that has that particular configuration or software, giving them free reign to steal information, identities, credit card info, and spy on victims.

Holidays are a time for good food and good drink, but more often than not, we substitute good drink for, well, cheap drink. However, cheap wine doesn't have to be bad.

While most of us don't think twice about dragging a pattern or using Touch ID to open our phones, or entering a password in for our email and bank accounts, these features are there to protect some of our most private information. Only problem is, they don't do a good job of it.

Android's new Material Design language is truly a thing of beauty. Slated to make a full debut alongside the upcoming Android "L" release, the vision and simplicity of this UX design recently won Gold Prize at the annual User Experience Awards.

My phablet has incredible battery life, but that doesn't mean I wouldn't like it to last even longer. Unlike the Samsung Galaxy S5, the Note 3 does not come equipped with Ultra Power Saving Mode, which can keep the phone running for another 24 hours with only 10% power remaining.

While FIFA may be one of the most corrupt organizations in the world (depending on who you talk to), that won't stop millions of us from tuning in this Thursday, June 12th, to watch the first game of what's going to be a month-long World Cup affair.

As with most OEMs, HTC would like you to think that you can do virtually anything with your new HTC One M8, but as a softModder, you know that isn't true. To actually unleash the full potential of that device, you need access to the whole system, not just the parts that HTC deems okay for you to mess with.

By this point, you've definitely come across an app or two that wasn't designed with the HTC One in mind. Either the resolution is too small, the status bar stays active when it shouldn't, or the font isn't the ideal size. There are ways out there to get that changed, but up until now it wouldn't just change one app—it would change all of them.

A picture is worth a thousand words, and depending on what you're taking a picture of, it could be worth a lot more. Our phone's camera can easily capture high quality photos, scan barcodes, and make us Instagram famous. You can compare prices of items and download applications just by scanning a QR code. Of course, we can always do this stuff a little bit better on our iPhones.

The space on your phone is extremely valuable, so getting the most out of your screen real estate can help you out when multitasking or for just making your device feel bigger. One thing that is often overlooked when it comes to saving space on the screen is the keyboard.

In this article, I'll be continuing my series on microcontrollers. If you haven't read part one, I'd recommend heading over there and reading it!

As you know, it's impossible to be a Steampunk without a pair of goggles. In fact, there are entire communities dedicated to judging other Steampunks based solely on their goggles. A Steampunk without goggles is like Samson without his hair, or a duck without a beak—totally powerless. As I'm sure you also know, the right pair of goggles can instantly render any outfit Steampunk, no matter what it looks like.

If you already know HTML or XHTML, you can create some pretty cool websites. The Javascript programming / scripting language allows you to make them much more interactive, dynamic, and professional. This video series will walk you through basic and advanced Javascript coding and leave you prepared to make really great websites.

In this how to video, you will be introduced to the concept of a movable NU in Greek as well as have the Greek accent marks summarized. The movable NU is used at the end of Greek texts in the present active indicative third person plural form. The movable NU is comparable to the English article "a" or "an". This lesson in perfect for those who wish to study this ancient language of Greece. Watch this language tutorial and you will be speaking biblical Greek in no time.

Learn how to pronounce the OUGH sound in American English. This video language lesson from Rachel's English provides a basic guide for pronunciations for ESL students. Say "ough".

If you're constantly writing money amounts using rupees, which is the basic monetary unit India, Pakistan, Nepal, Seychelles, and other South Asian and East African countries, then you'll be relieve to know that there is a font you can use to create the rupee symbol in any word processor on your computer.

Don't sit back and take verbal abuse! This tutorial will teach you how to dish it back out and craft the perfect insult.

If you're serious about keeping your diary for your eyes only then you might have to take some drastic steps. There are some very clever ways to distract from, encrypt, hide, or disguise a diary if you're willing to put in the work.

The best way to win friends over in a foreign country is by breaking the ice and showing your enthusiasm with your best effort at their language. Practice your Gaelic for travel or just for fun with friends.

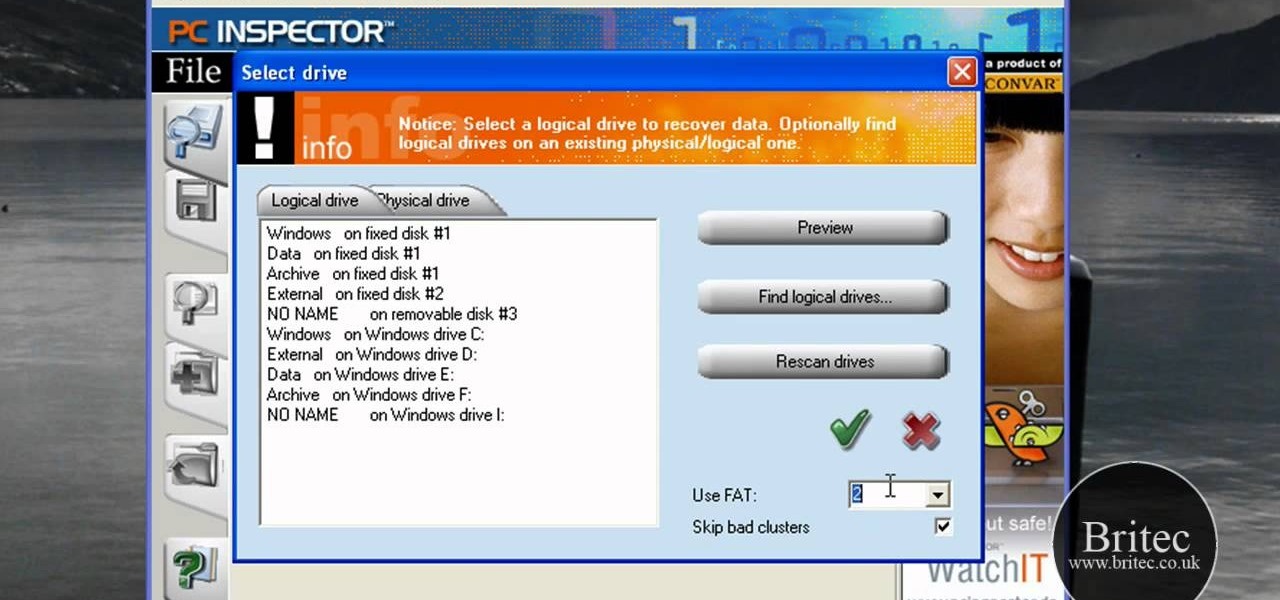
In this data recovery tutorial the instructor shows how to recover deleted files and lost data using a free software called PC Inspector. On your computer you may loose data sometimes due to a corrupted hard drive, or because you deleted it accidentally or some other reason. Now some times you will need to recover that important data and it will cost you hundreds of dollars to get it done outside by the professionals. Now you can avoid this and use a free software called PC inspector and reco...

Body language is one way to tell if a guy likes you. He will lean towards you or look at you a lot. If he likes you, both feet will be pointed towards you. If he doesn't like you, one foot will be pointed at the door. Eye contact is another way to tell if he likes you. If he is shy, he will turn his head quickly when you catch him looking at you. He may try to catch your gaze and hold it, which could be uncomfortable to you if you don't like him as much. Guys will try to make themselves seem ...

In today's data-driven world, being well-versed in Big Data and analytics can help land an exciting and high-paying career. Whether you're interested in working for a major tech company or pursuing freelance work in development, you need to have a thorough understanding of the latest and greatest platforms in analytics if you want to succeed.

The term "hacker" often has negative associations attached to it, yet the world is in dire need of professionals with hacking skills. White hat hackers are ethical computer hackers that use their hacking skills to pinpoint network vulnerabilities and patch them up before they can be exploited by the bad guys.

Whether you're coding a simple app, trying to learn a new programming language, or building an entirely new operating system from scratch, being able to quickly and clearly organize your thoughts is absolutely paramount — even as an ethical hacker or penetration tester.

Microsoft Excel is one of the most powerful programs for modern businesses. By allowing you to manage, sort, and analyze large collections of data, Excel provides an essential service for any company interested in using the power of data science to its advantage.