In this series you will learn how to use PHP to perform attacks, gather information, and setup backdoors. Along with performing attacks you will learn how to protect yourself from them. In this part you will learn about PHP as well as install Apache and PHP. What you'll need for this series

Hello fellow Nullbytiens, I'm Washu, a long time commenter but first time poster. Today we'll be making an IRC bot, if you haven't seen OTW's post about the new IRC channel I would encourage you to go check it out. He does a good job at explaining what IRC is and how to get set up.

Hello friends! This tutorial will teach you how to build a local pentesting lab on your Linux machine which will enable you to easily install common web applications so you can practice locating and exploiting their known vulnerabilities (or discover new ones!). In particular, this is an excellent way to learn how to hack Wordpress, Joomla, and Dupral plus many more!

Instead of suffering through long, dull meetings with your supervisors and coworkers, you can turn those office table sessions into your very own psychological experiment.

Welcome back Java programmers! In this tutorial we'll being going over Variables/DataTypes and Type-casting

I saw many people asking for a Tutorial about writing their own Remote Administration Tool, so I now introduce you in a basic kind of RAT. This program is not for real use, but for learning how you could write this kind of tool. It will be basicly coded and not very refined. I used Python 3, so you have to install it if you want to use this program unchanged. Also this RAT is for Windows and almost all features won't work under Linux.

First of all, Merry Christmas and Happy New Year to all Null-Byters that learn and teach in this wonderful site. In this article we will explore the basics of the meterpreter's IRB (Interactive Ruby Shell).

Many of our members here at Null Byte are aspiring hackers looking to gain skills and credentials to enter the most-valued profession of the 21st century. Hackers are being hired by IT security firms, antivirus developers, national military and espionage organizations, private detectives, and many other organizations.

BlackBerry has yet to find a home amongst the iPhone and popular Android phones, with sales plummeting over the last couple years, but this might be a thing of the past thanks to their latest device, the BlackBerry Priv. It has decent numbers so far and was even sold out on Amazon shortly after its initial release.

Hello my anxious hackers, the week has started and here we begin a new series that I think will help many here and not only, for those that have the opportunity to follow our tutorials but they are not yet part of the community.

Hello fellow training hackers. I do not know if many of you are familiar with ruby, but since it is a useful scripting language, that hasn't been covered too much here on Null Byte, I thought why not do some How-tos about it now and then.

In case you didn't know, Android has an awesome hidden settings menu called "Developer options" that contains a lot of advanced and unique features. If you've ever come across this menu before, chances are you just dipped in for a minute so that you could enable USB debugging and use ADB features.

Programming is an essential thing in hacking/pentesting, and at times, I do not feel that it is being addressed enough here, at Null-byte. I understand that this is a forum dedicated for hacking, but I'll address some of the stuff I feel is muy importante about programming. I am not a professional programmer, but I do have experience and I do want to share some of the stuff professionals have taught me.

hello my dear colleagues, I made a visit to nullbyte and found that there is not a complete tutorial about the google dorks, so I felt the need for this tutorial, and seeing that there are many newbies around, so here's a tutorial that will teach you how to use google to hack.

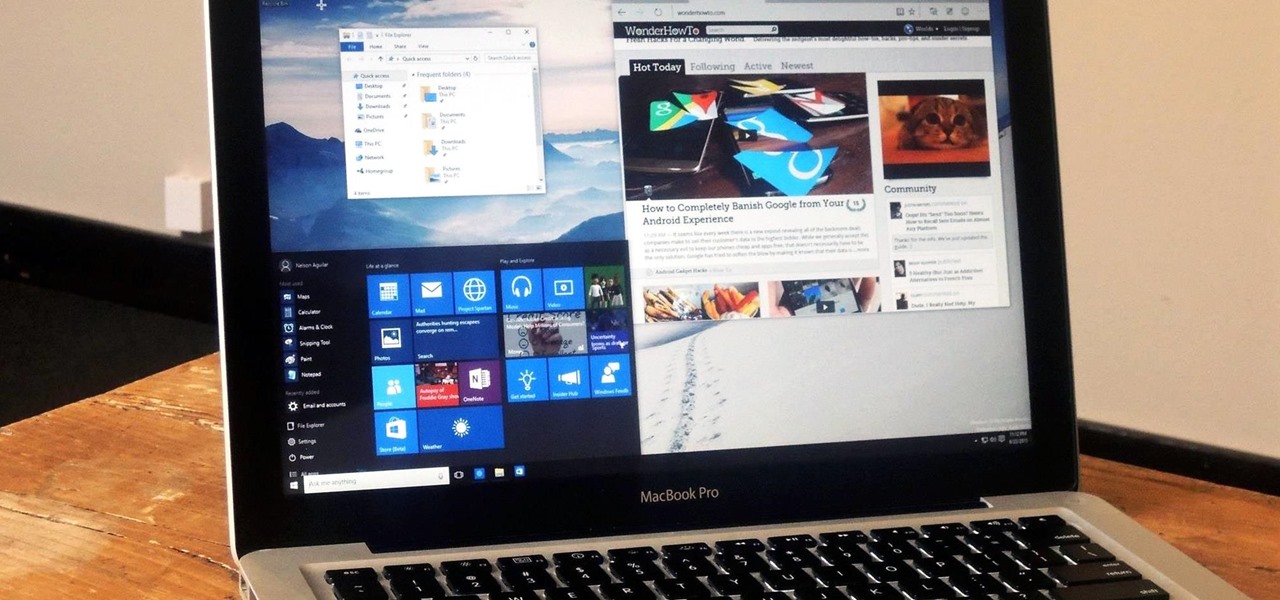
While Windows 10 is still a few weeks away from a public release, that doesn't mean you can't enjoy its brand new features right now. Anyone with an Insider Preview account can install Windows 10 on their computer. And that doesn't just go for those that own a Windows PC—Mac users can get their hands on Windows 10 as well.

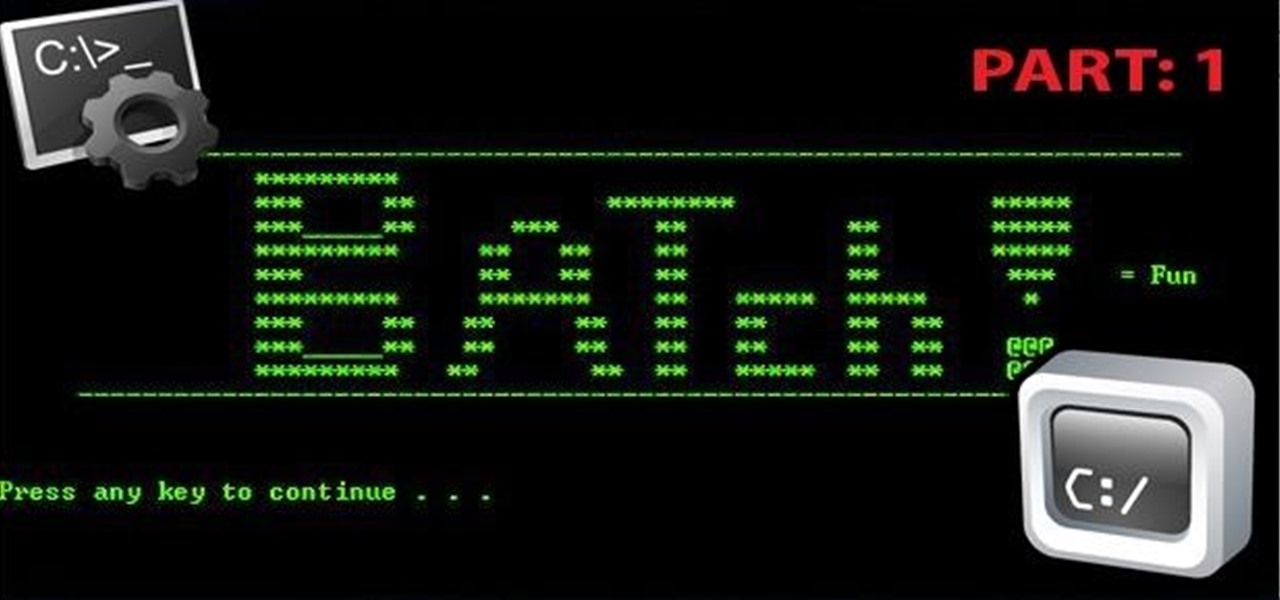
Hi there, Crackers, Welcome to my 7th post (Part-1), this tutorial will explain about the basics of Batch Scripting.

With our internet-connected devices growing in number by the year, it would be nice if they could somehow all be interconnected. This is becoming commonplace for our tablets, smartphones, and laptops, but our media streaming boxes still seem to be isolated in their own little worlds.

The Apple Watch is finally here! We'll have loads of guides and videos for you guys to check out in the following week and beyond, but we thought it'd be best to start off showing you how to set up and pair that brand new beautiful Apple Watch of yours to your iPhone.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

Welcome back, my hacker novitiates! A short while ago, I introduced you to regular expressions. Regular expressions are a language that is particularly useful for finding complex text patterns in streams of data.

As soon as third-party keyboard compatibility was announced for iOS 8, Apple loyalists and the newly curious both looked to the popular Android third-party keyboard developer, SwiftKey, to see if they'd be offering their services to iOS.

At the core of your Galaxy S5's hardware lies the central processing unit, or CPU for short. Practically every piece of data, every binary bit, has to pass through your CPU before it can be used to display a video or execute a game command.

Google's upcoming Android release hasn't even received a name or version number yet, but the third-party development community is already having its way with the firmware.

As Matias Duarte and the team over at Google's Android Design department ready their wares, they've given us a preview version of the upcoming "L" release of Android to try out.

Developing an imperceptible lie is difficult, especially when you're lying right to someone's face. Thanks to smartphones, getting people to trust you is now easier than ever. You can craft a lie in seconds and hit send, all without ever seeing their untrusting faces.

I am not a morning person. This is a fact that has been proven with science. I need every bit of help to get me out of bed in the morning—multiple alarms, extremely loud tones, Pandora—I've tried everything.

Imagine that you're the last person alive. After losing all of your loved ones, you thought you'd never see another human being in your life. Then, they arrive. The hoard of 15-year-old zombies looking for a cute British YouTuber so they may feast on his brains.

A friend of mine has a crazy amount of Reddit karma and gold, and yesterday he let me in on his secret. This person, who will remain unnamed for obvious reasons, created a Python script called Reddit Karma Crawler that finds rising posts before they get too popular.

I'll freely admit that I'm a SwiftKey diehard. I've used the keyboard since its inception in 2010, and it was one of the first apps I ever paid for back in the days of my beloved Sprint Evo 4G. Since then, I've kept up with all its beta iterations, and have unabashedly installed it on various friend's devices.

The new iOS 8 was just unveiled, and it looks pretty awesome. Apple showed off some of the enhancements and new features we can expect to receive in the fall at WWDC, and while not the huge facelift we saw with iOS 7, it does showcase what Apple does best—refinement. Continuity

Out amongst the ether of the internet lies a completely different version of the Netflix library you've come to know and love. Because of licensing and rights fees, the streaming media giant maintains separate libraries for each country it services. Ultimately, this means that certain movies and TV shows are only available in certain countries.

Windows 8's interface was met with criticism when it was released, mainly directed at the tiled Start screen, a departure from Windows versions of old. Many felt that this new home screen style was better suited for mobile devices like Microsoft's Surface tablets and Windows Phones.

Welcome back, my greenhorn hackers! I recently began a series on scripting and have received such positive feedback that I'm going to keep this series going. As I've said before, to graduate from the script kiddie to the pro hacker, you'll need to have some scripting skills. The better you are at scripting, the more advanced your hacking. Ultimately, we are leading up to developing the skills to build your own zero day exploits.

Welcome back, my greenhorn hackers! Recently, I asked the Null Byte community what subject they would most like me to cover in future tutorials. Many of you cited scripting, and I decided it's best to cover this subject soon, so here goes.

Last summer, Universal Pictures released the sequel to the popular 2010 animated film Despicable Me, bringing back everyone's favorite characters—the Minions. They're adorable, yellow, and they speak a gibberish "Banana Language." What's not to love? If you're planning on dressing yourself (or your kids) as Minions for Halloween this year, you'll be in good company. There are tons of costumes out there you can buy or make, and here are five of the best DIY options for you.

One of the best features on the new Moto X is Touchless Control, which lets you verbally ask the device questions or perform tasks without ever touching or turning on the display, a feature that would do quite nicely on the Nexus 7, if it could handle it.

These days, we increasingly have more and more devices in our everyday possession. While a notebook computer, a tablet, and a smartphone may seem like overkill, they do work to make our lives easier and even help reduce clutter in certain ways.

Samsung unveiled their new flagship device, the Galaxy S4, at a live event in New York City today. Here's a quick rundown of the specs and all of the new features that you can expect when you finally get your hands on one (whenever that will be). The GS4's Specs

Welcome back my fellow hackers! In my last few articles, I've concentrated on what is called a listener, which is basically the same thing as backdoor and rootkit, only "listener" sounds much less malevolent than the other two terms.