For better or for worse, Google started the race towards smartglasses for everyday use with Google Glass before scrapping the Explorer Edition and pivoting towards enterprise customers.
Next to spam calls, few things are more annoying than being inundated with spam, scam, and smishing texts. Your iPhone's Messages app should be a place for your friends and family to stay in touch, not a minefield of phishing attacks, malicious links, and viruses. Luckily, there are quite a few methods to block and report your way to a more spam-free iPhone.

Apparently, we learned nothing from Jurassic Park, as scientists are still working on bringing extinct species back to life. Until that day comes, you can interact with long-lost animals through augmented reality...if you have a newer model iPhone.

The company augmented reality that Rony Abovitz was trying to build at Magic Leap apparently wasn't working out the way he hoped it would. That company, built on dreams, music, and future-looking entertainment, rather than truly new technology, came with a $2,300 price tag for a device using dynamics most mainstream consumers have never even tried.

Nearly every native app on the iPhone received an upgrade or new features in iOS 14 — and Safari is no exception. The web browser now has better password protection, faster performance, privacy reports, and built-in translations, just to name a few. Some of the Safari updates went unnoticed by many, but they're there and ready to use in iOS 14.

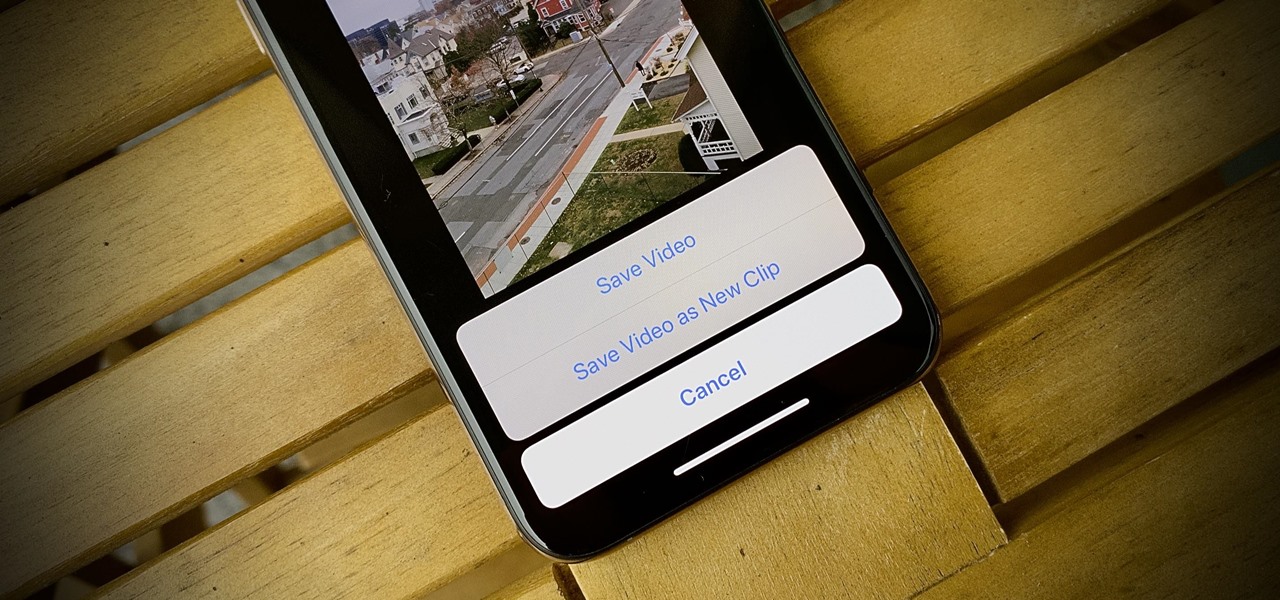
The new iOS 14 for iPhone arrived Wednesday, Sept. 15, 2020, alongside iPadOS 14, and there are a lot of features to uncover. Improved widgets. Better home screen customization. Exciting Messages improvements. New abilities in Camera and Photos. There's so much here that it'll take months for you to learn everything by heart.

With over two billion websites floating around cyberspace — only 400 million are estimated to be active — you need every tool you can get to stand out. Great design, fonts that capture attention, and SEO placement are all necessary ingredients to success.

Instead of using a single APK, YouTube Vanced recently started being distributed as a bundle that requires a third-party app to install. Some fans found this too difficult, so the Vanced developers decide to make the process easier.

If you're using or need to use Zoom, the popular video teleconferencing service, you've almost certainly heard about "Zoombombing" by now. While Zoom has been adding security measures to address the problem, there are other things you can do to prevent or stop Zoombombers in their tracks so that your video meetings and chats go undisturbed and uninterrupted.

Arduino is a language that's easy to learn and supported on many incredibly low-cost devices, two of which are the $2 Digispark and a $3 ESP8266-based board. We can program these devices in Arduino to hijack the Wi-Fi data connection of any unlocked macOS computer in seconds, and we can even have it send data from the target device to our low-cost evil access point.

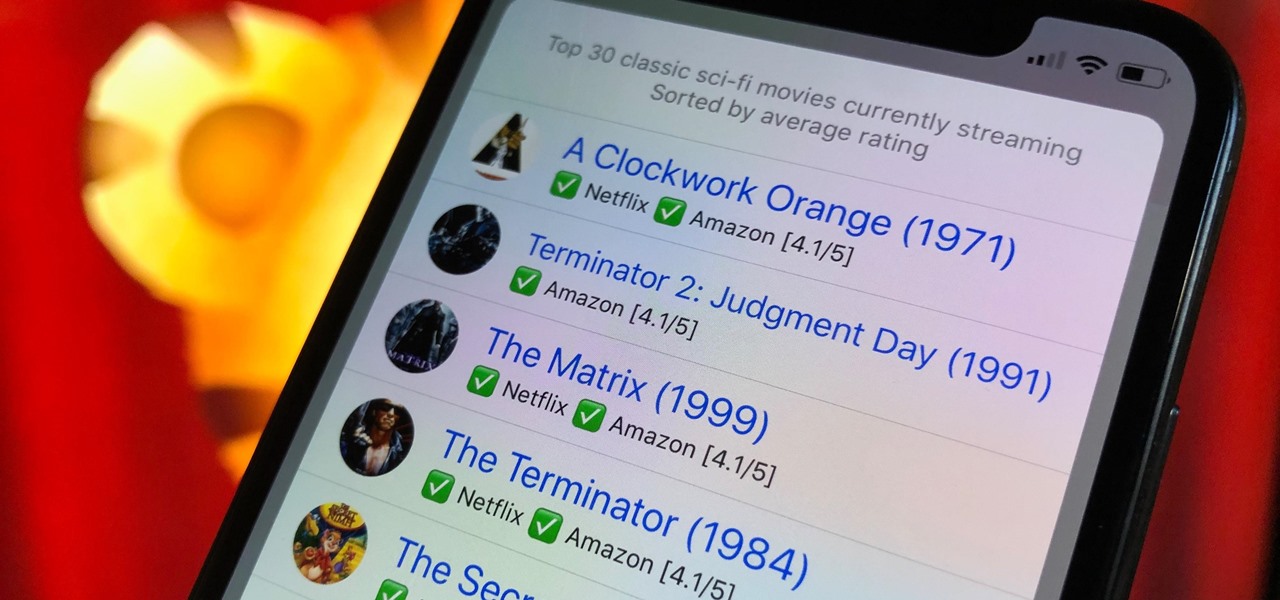
Choosing a movie to watch at home can be incredibly difficult when you don't already have one in mind. But there's a shortcut for your iPhone that can make it easier to browse your streaming media services for something good to play. More specifically, it lets you browse Netflix and Amazon Prime at the same time.

It wasn't long ago Apple released iOS 13.2 to the masses. The second major update to iOS 13 included 22 new features and changes that added a significant layer of depth to an already feature-filled experience. Apple isn't ready to stop the fun, however, as iOS 13.3, released Dec. 10, has a decent amount of new features too.

Smartphones are vital travel companions. While you're on the go, they connect you with loved ones back home, help you find tickets and passes for tourist attractions, and make it easy to find your way through foreign roads — but even the most powerful smartphone could use help from travel accessories.

The worlds of augmented reality and virtual reality are closely linked in many ways. That means it's smart for AR insiders to keep a close on new developments in VR. If you have been paying attention, you know that Oculus CTO John Carmack is one one of the most important thinkers in the VR space.

Beta testing certainly has its perks. While you do need to deal with bugs, you're introduced to new features before the general community. And if we're talking iPhones, there are over 200 new features in iOS 13 beta. If you're already on board with iOS 13 public beta 6 for iPhone, you can get an upgrade on that firmware as Apple just released public beta 7 today.

Life's pretty good for iOS public testers — we get to check out new iPhone features months before the general public even knows they exist. That said, we aren't first to the party. Developers get priority during beta testing, as evidenced by yesterday's iOS 13 dev beta 6 release. It's not all bad though since Apple just released the public version of that software, public beta 5, this afternoon.

If tradition holds, we're roughly one month away from Apple's big iPhone announcement. While we're excited to see what will mainly be a significant camera upgrade, it's not all about the hardware. Apple will also release the official version of iOS 13 to coincide with the iPhone XI. Before then, however, iOS 13 needs beta testing, and developer beta 6 just hit on August 7.

Apple just seeded the fourth public beta for iOS 13 to software testers today, Tuesday, July 30. AppleSeed participants saw this beta one day early, alongside the release of developer beta 5. Now, developer and public testers alike are up-to-speed with the latest in iOS 13.

Beta testing for Apple's big upcoming iPhone update, iOS 13, is well underway. So far, each of the four beta versions we've seen brought new features and changes to the table, many of which were never even mentioned by Apple during WWDC in June. Now, it's time to do it all over again, as Apple just released the fifth developer beta for iOS 13.

With a tiny computer, hackers can see every website you visit, exploit services on the network, and break into your Wi-Fi router's gateway to manipulate sensitive settings. These attacks can be performed from anywhere once the attacker's computer has been connected to the router via a network implant.

My autistic son loves music. One afternoon, when he was nine, I downloaded GarageBand to his iPhone to help with the boredom of a long wait at a doctor's office. Instead of pacing or escalating into a meltdown, he spent the entire hour and a half practicing, learning, and composing. When we finally left that day, the rest of us exhausted and irritated, he shared his first composition with a big smile.

It feels strange to be walking through an open field in a small village in the English countryside. There's no one else around — just the four of us: me, my husband, my 12-year-old son, and my adult niece. The day is spectacular, particularly for England. The sun is shining, and the temperature is in the low '70s.

There have been concerns with how much personal information Google tracks and all the things they know about us. Of course, that's what makes Google services so useful, they can use that information to cater to each of us individually. So yes, it serves a purpose, but it's not great for personal data security.

Encrypting payloads and encoding stagers are more effective against macOS than one might think. It's very easy to evade VirusTotal and macOS antivirus software using a few simple tricks.

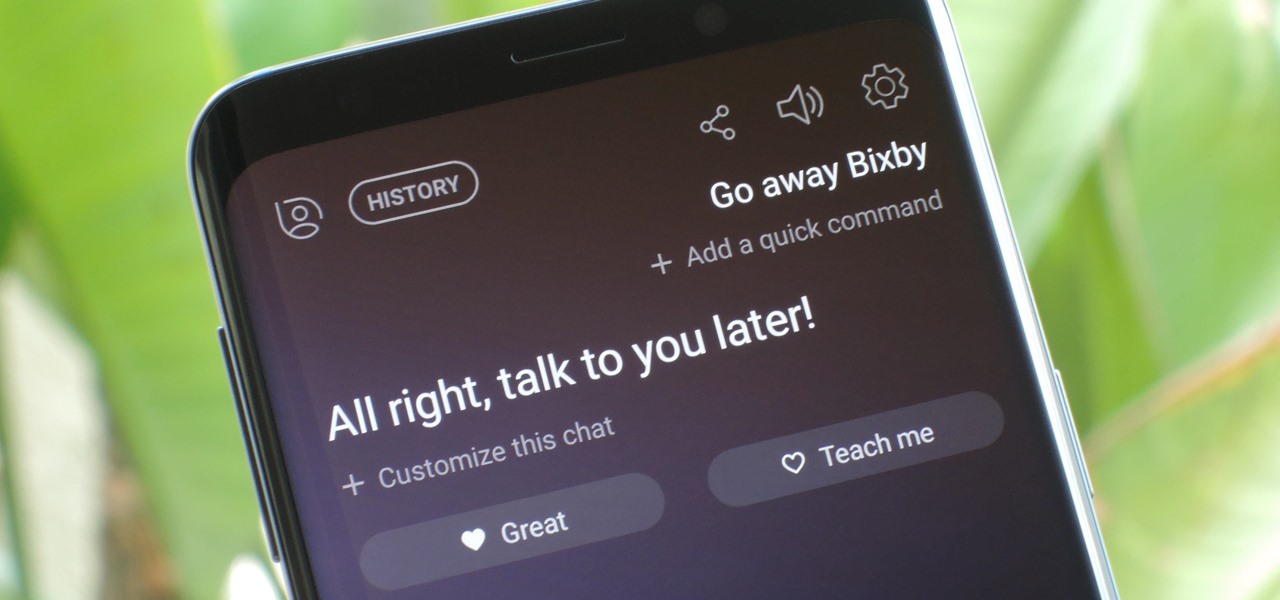
Sorry Samsung. I know you really wanted Bixby to be the next Siri, Google Assistant, or Alexa — but it just isn't. Burying the option to disable the app won't change that. Sure, Bixby has some redeeming qualities, but there are many of us who don't want it shoved down our throats. We'll show you how to disable the app to prevent it from launching every time you try to access just about anything.

For anyone using open source information to conduct an investigation, a balance between powerful tools and privacy controls are a must. Buscador is a virtual machine packed full of useful OSINT tools and streamlined for online research. This program can easily be set up in VirtualBox, and once that's done, we'll walk you through some of the most useful tools included in it.

Hackers and makers are often grouped under the same label. While hackers draw on computer science skills to write programs and find bugs, makers use electrical engineering to create hardware prototypes from microprocessor boards like the Arduino. We'll exercise both sets of skills to program a $6 NodeMCU to display the status of a Wi-Fi link via an LED, allowing us to monitor for jamming attacks.

You can feel it in your bones. You may die if you don't get this phone. There's just one problem — the price. Suddenly, you come across what seems like manna from heaven. That very device, at a deeply discounted rate, can be yours.

Developers creating login systems know better than to store passwords in plain text, usually storing hashes of a password to prevent storing the credentials in a way a hacker could steal. Due to the way hashes work, not all are created equal. Some are more vulnerable than others, and a little Python could be used to brute-force any weak hashes to get the passwords they were created from.

Don't think because your MacBook is using FileVault disk encryption your device is secure or immune to hackers. Here's how to find out if that FileVault password is strong enough to withstand an attack from a motivated attacker.

Developed by Open Whisper Systems, Signal is a free, open-source encrypted communications app for both mobile and desktop devices that allows users to make voice calls, send instant messages, and even make video calls securely. However, a vulnerability was recently discovered for the desktop version that can be turned into a USB Rubber Ducky payload to steal signal messages with a single click.

For SQL injection, the next step after performing reconnaissance and gathering information about a database is launching an attack. But something seems off .. in the real world, it's usually not quite as simple as passing in a few fragments of SQL code to an input field and seeing all that glorious data displayed right in the browser. This is when more advanced techniques are needed.

Single sign-on (SSO) lets users login across different sites without having to manage multiple accounts. I'm sure most of us appreciate the convenience of seeing "Sign in with …" buttons that let us login with a single username. Hackers, however, see a possible avenue for exploitation, and you'll soon learn how an attacker can exploit a SAML vulnerability to assume another user's identity.

There's a feature in the Gboard keyboard that enables people who cannot talk, type, or swipe normally to still have a way to communicate in the digital age on their smartphones. While it's mainly an accessibility feature for those who actually need it, it's a good way for anyone to learn or brush up on their Morse code skills — and it works on both Android and iOS.

When OnePlus announced the 5T, many were disappointed that it wasn't shipping with Android Oreo. To curb some of this disappointment, OnePlus quickly introduced an open beta for both the 5 and 5T and promised that each would receive the official version by Q1 2018. Well today, OnePlus has met this promise and pushed the OTA out for the official stable version of Android Oreo.

PowerShell Empire is an amazing framework that is widely used by penetration testers for exploiting Microsoft Windows hosts. In our previous guide, we discussed why and when it's important to use, as well as some general info on listeners, stagers, agents, and modules. Now, we will actually explore setting up listeners and generating a stager.

For all those times when an app either isn't available or simply won't cut it, your phone's internet browser provides access to your favorite websites and services. But some browsers are flat-out better than others, and chances are, the browser that came pre-installed on your phone isn't the best option out there.

Ransomware is software that encrypts a victim's entire hard drive, blocking access to their files unless they pay a ransom to the attacker to get the decryption key. In this tutorial, you'll learn how easy it is to use the USB Rubber Ducky, which is disguised as an ordinary flash drive, to deploy ransomware on a victim's computer within seconds. With an attack that only takes a moment, you'll need to know how to defend yourself.

In this chapter, we want to start seeing some real progress in our dynamic user interface. To do that, we will have our newly crafted toolset from the previous chapter appear where we are looking when we are looking at an object. To accomplish this we will be using a very useful part of the C# language: delegates and events.

As augmented reality becomes more and more integrated into the mainstream, people have been wondering the future of AR is going to look like. Jay Samit has a pretty clear idea.