
It may not be your number one spot for finding cool apps for your Android device, but the Amazon Appstore for Android is running a new promotion this week called "Geek Week," where eight of the most popular productivity and utility apps are now on sale for 48 percent off or more.
One of the things I consistently notice amongst fellow internet users is that many people don't know how to properly search for stuff. Google may have served you well in the past, but I'm going to share a few little tricks with you to help make your search results even spiffier.

Want to stay up to date with the emails in your inbox? Most mobile phones, like the Samsung Instinct, have an email feature and internet capability to keep you connected. Watch this video cell phone tutorial and learn how to send and receive email on a Samsung Instinct. Check email on a Samsung Instinct cell phone.
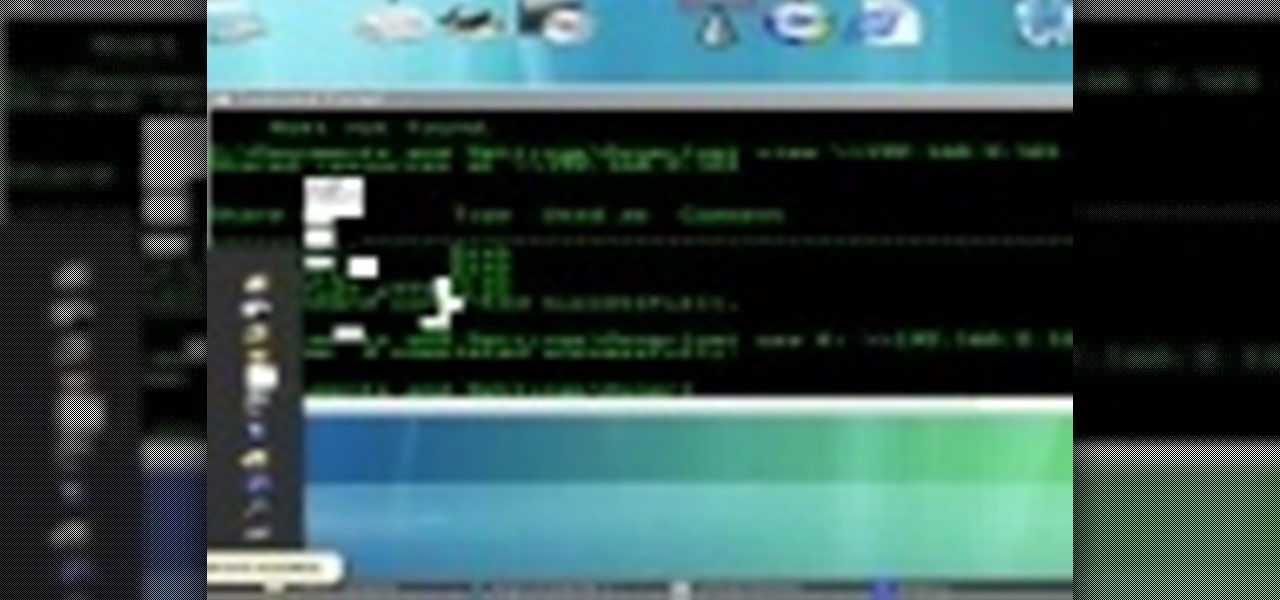
See a basic netbios hack, showing what happenes to ppl who leave files and folders shared over the Internet. Hack computers with open shares.

Your IP address or Internet Protocol address is your computer's unique identifier. Here is our quick guide on how to change your IP address when using Windows. Change your IP address when using Windows.

This is my list of programs that I must have on my PC, but I think you can also use them, so here is the list:

Not all people can catch up with formulas, and problem solving skills, but with the right attitude and proper time management there's no doubt you'll pass the subject.

Anonymity is very important to many internet users. By having your "e-identity" exposed online, you can be stuck with a number of unwanted issues, such as:

Have you ever gone on a long internet binge, researching and surfing mindless things, and thought to yourself: I wish I could make some money surfing the internet and sharing the (sometimes useless) information I had just acquired? Well, now you can!

What you need All you need is little program named Cheat Engine, and you can download it from here. And it is totally free.

How to bypass Websense and other web filters in Internet Explorer. Bypass Websense and other proxies.

This video shows you how to access blocked websites using kproxy in school, using Internet Explorer. Access blocked websites using Kproxy.

If you are bored and surfing the internet, check out all the strange and hidden features of Google. Here are all the entries to type in google : google bearshare, google gothic, google linux, google l33t, google ewmew, xx-klingon, xx-piglatin, google bsd, google easter egg, google mozilla, google gizoogle. Find cool things in Google.

Last week Amazon set their sights on the mobile app market, launching their Appstore for Android. This week they're attacking Android devices once again, but that's not all—they're getting into the online storage biz.

Movie fans—it's that time again—the Oscars. You can finally see who wins for Best Actress, Best Director or Best Screenplay tomorrow night during the 83rd Academy Awards at 8 p.m. (EST) on ABC. For those of you on the west coast, that would be 5 p.m. (PST).

Back in the eighties, I used to hate television commercials, but I eventually got used to them. Had to, in order to enjoy my favorite shows. Then, the increasing number of billboard ads annoyed me in the nineties. They followed me everywhere I went—no escape—persuading me to buy the newest whatever. It seemed like Big Brotherism—like They Live. But, I got used to it. When I finally entered the digital age and became a web addict, I was peeved at the constant sight of online ads everywhere I v...

What happened to please and thank you? When did asking someone to come look at your build degenerate into COME NOW or FOLLOW or sending out teleport requests to any and all currently on the server without asking?

To those who may not know about this, the UK high court has ruled that all UK based ISP's are to begin blocking Piratebay. This comes in retaliation to Piratebay's action to take down all torrents and provide only magnet links to the pirated content - a move which releases TPB from liability should they be once more accused of hosting the actual content.

Today's digital cameras record not only the images themselves, but also the metadata behind the scenes, like camera settings, location, date, time, etc. But there's a lot more to say about a photograph. What's the subject? Is it night or day? Outside or inside? Person, place or thing?

Though under a lot of the average consumer's radar, the CISPA is now making rounds again with a coalition of advocacy rights groups. The act, known as the Cyber Intelligence Sharing and Protection Act, forces companies to ignore existing privacy laws and share information with the Federal Government. This short article will bring you up to date on this bill. The CISPA is another bill 'designed' to help prevent thefts and prevent them in cyberspace. But again, like all the previous bill before...

If you live in an urban environment, chances are that you've seen this: It's a program started by the FBI to prevent terrorism and general thievery in peaceful and innocent communities all around America. I myself have seen a lot of these, and my previous apartment community was part of this 'program'.

Some of you might be using Tor to host hidden services, and some of you might not even know what hidden services are. If the latter's you, do not miss this article. Why? Because you can host your websites and services on the I2P darknet. It's safe and secure—it's anonymous.

This article is going to talk about video and only about video. Why? Because video is very important for any size of business. Even small businesses can use video to promote themselves on the internet. And in the next few years, you’re going to see more and more businesses using video. Even now, I’m going to show you some articles that have been written on different websites talking about video and how small businesses can use them and how businesses need to use them now, especially to rank o...

As many of you Null Byters may know, I was planning on writing this article a week or two ago. Better late than never! So, let's get right to it then—choosing the right Linux distro for your needs.

How many Facebook friends do you have? The average person on Facebook has around 140 friends while some hit the ridiculous Facebook friend limit of 5,000. Facebook states that its services are for people you know in person. I don't think anyone has 5,000 friends in person, do you? Personally, I don't even think Megan Fox has 5,000 friends in person, so how could any regular person have that many? But that's beside the point.

Here's another delicious Byte. Ucha Gobejishvili, a Georgian Security Researcher under the handle of longrifle0x, discovered two cross site scripting (XSS) vulnerabilities on the official website of Forbes. He discovered the hole in two different locations on the site, and has already informed the website of the vulnerability.

Reverse shells are useful for issuing commands to a remote client when the client is behind something such as a NAT. You might say, "But can't a normal shell or simple SSH tunnel do the same thing?". No, it can't. All over the internet I see a lot of confusion regarding the difference between a normal shell and a reverse shell. Let's clear this up before we get started.

Haven't you ever wanted to live in a futuristic home? I think that homes are headed towards an era where they will be controlled by our computers and smartphones. No longer will you have to find your keys to unlock your door, or wait until you get home to monitor your security, because X10 is here.

UPDATE: New York Giants WON! Super Bowl XLVI has concluded. The New York Giants beat the New England Patriots 21 to 17. If you missed the big game, there doesn't seem to be a full replay of all the action, but you can visit NBC.com or NFL.com to get information and video highlights on the game and player interviews, as well as a list of all of the records broken and tied.

How to Crack Passwords Faster by Putting Your GPU to Work with HashcatSecurity on the internet is always changing. Not too long ago, having a 10 character password meant that you were safe from all forms of hash cracking. Hash cracking is when you take a string of characters that have been passed through a cryptographic hash and try to reverse them. The normal processors that are housed inside of our computer cases are general purpose. The processors are not meant for handling complex math an...

When your computer first connects to a nework, it sends out a request on the network to lease an IP from the router. The router then leases your computer an unused IP address, which is used as a unique routing address for sending traffic that is meant for you, to you. As everything tends to, this method has its flaws.

Google+ is the greatest social network to emerge since Facebook annoyed everyone into joining, but that doesn't necessarily mean that our relationship with it is all rosy. Although Google+ has amazing innovations, like hangouts and circles, users are spending a lot of time begging for core features that take what seems to be an eternity to emerge.

As we all know, security is a big thing here in Null Byte. We've talked quite a bit about ways to encrypt traffic and become anonymous on the internet, some of which entail using proxies, VPNs, and SSH tunnels. We've also talked about preference using SSL pages in practice for safe logins. These are all great protocols and tools, but aren't without their flaws and inconveniences.

"How do I install Arch Linux?" That question was bound to come up eventually. And with me using Arch, it's no coincidence that all of you want to use it as well. Arch is arguably the best Linux distro available. Distros that come close are Gentoo and some aspects of Ubuntu, but Arch is meant for building your OS from the inside out. Arch is built around minimalism, so you won't get anything by default. It doesn't even come with sound!
Best quotes: "A supply of tea with milk and sugar would be nice. If it is tea I really like, I like it without milk and sugar. With milk and sugar, any kind of tea is fine. I always bring tea bags with me, so if we use my tea bags, I will certainly like that tea without milk or sugar.

Social networks like Facebook and Google+ are great for staying connected with family, friends and coworkers—even fans. But sharing and communicating with practically anyone in the digital realm has alienated us from most of the flesh-and-blood beings we see everyday—our neighbors. How well do you know your neighbors?

Formerly ipchains, iptables is a script-based firewall that's included with both Mac and Linux operating systems. In my opinion, it's the best firewall in existence. The only downfall is that it's complicated for some people to use due to its script-based nature. But this should be disregarded, as firewalls are nearly the entire security of your computer.

PayPal has, all in all, been great for allowing Web 2.0 economy to grow. For most entities, it's the best way to send money between two people on the internet.

PC Gamer represents all that was awesome about games journalism in the '90s, now sadly diminished. Brilliant, funny, full of integrity, and solid print sales were always present, and with the tragic exception of the latter, still are. Video game magazines were hit harder than nearly any other magazine vertical when the internet began its uncoordinated, but inevitable assault on print media. Magazines are now struggling to find their place in a world filled with more competitors than paying cu...

This Week's Workshop: Music To My Ears The heart of WonderHowTo's Minecraft World is, naturally, “How-To” and so in the spirit of all things tutorial and DIY we will be hosting a weekly workshop showcasing the best and newest tutorials, builds, and inspiring ideas. We hope to inspire creativity and create a place where the community can share ideas and practice skills, right here on our server.







































