This is a tutorial about how to browse the web anonymously on a Linux server. Requires some knowledge of Linux. Be sure to note that information sent through this system is ever MORE open to hackers than the normal Internet. Don't send any personal information this way.
An explanation of how to get access to your Linux desktop from any other computer connected to the Internet.
The popular javascript library jQuery is an amazing way to extend the design possibilities of your site beyond what CSS can do. But luckily, if you are already comfortable with CSS, you have a huge head start in jQuery! This is a very basic introduction to including jQuery on your web page and getting started writing a few functions. So you Internet website designers out there, this is a good video tutorial to check out.

Build a device that automatically takes and uploads pictures of your life every 30 seconds on the Internet.

Have you been on a "Safari" that you'd rather not let others find out about? Stop living in fear. Here's how to cover your tracks.

Debunk some of the Internet myths regarding the use of stripper to remove paint on vinyl dolls in preparation for "reborning".

Today's word is "ubiquitous". This is an adjective which means being or appearing to be everywhere at the same time.

This tutorial shows you how to crop and resize images in Photoshop so they can be used on the internet.

In this episode, Brandon Jackson joins D.Lee Beard to present an in-depth review of the Slingbox A/V, explore where to find free downloadable audiobooks online, and to answer viewer questions on using an iMac as a display and how to share files over a local network between a Mac and a Windows PC . Be sure to check out our next video to learn how you can win the Techies' Slingbox and begin watching your home TV from all over the world via the internet.

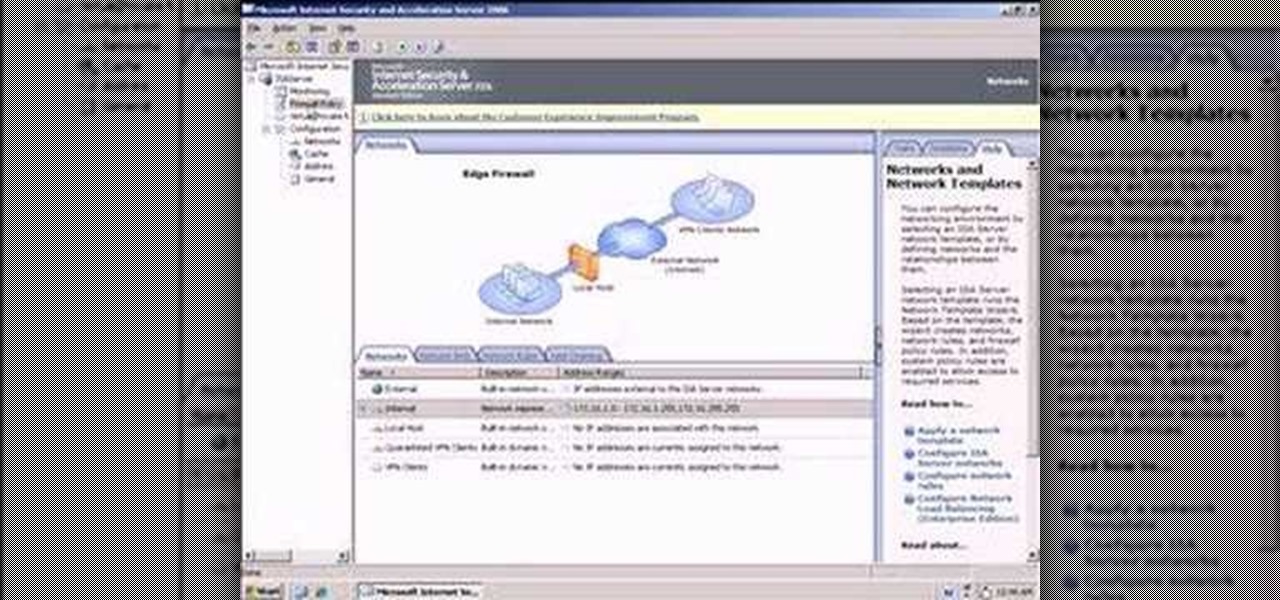
So what exactly is ISA Server? ISA Server, which stands for Internet Security and Acceleration Server, is Microsoft's software-based firewall, proxy, and web caching service/product. Now what does all of that mean? This video helps explain it!

This tutorial demonstrates how to turn on Safari's Debug mode so you can use additional functionality like the JavaScript console, Web Inspector, and spoof Internet Explorer.

In this episode we demonstrate how to sniff Voice Over IP (VOIP) conversations, which basically means how to tap an Internet phone.

This video demonstrates how to discover the dating history of people by searching on the website www.rateabull.com. The site searches their own dating database, as well as several other social networking sites.

This video shows you how to make your item photos looks sharp and professional. From backdrops to cropping, learn how to make those JPEGS sparkle and shine! This is great for those who sell on Ebay or have an Etsy shop.

A tutorial on using LogMeIn.com to set up remote computing on your computer so that you can always access your computer from anywhere with the Internet.

Thread Heads Quickie: take some old clothes and using a basic pattern from the internet, construct a new reversible handbag for yourself.

This video shows different ways to save music from websites including using Google search and recording songs from websites using free software.

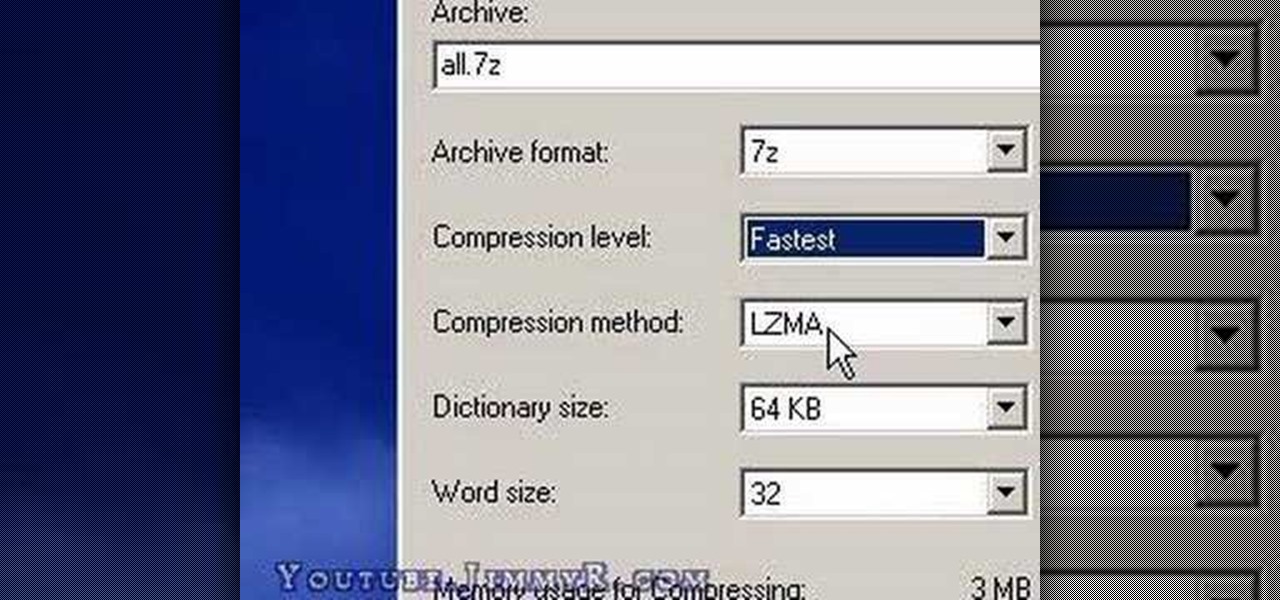
Sometimes you may want to send files larger than the file size limit that your email program will allow. Learn how to send larger files by email by using either free services on the Internet or free compression software like 7Zip.

Learning songs is the best way for a beginner guitarist to progress. Save learning scales and technical stuff for a little later. Besides this video, Justin gives some good recommendations for where to find songs and suggests staying away from the random "TAB" internet search since this won't help you learn if you're playing them wrong or not.

Get yourself on the internet. Learn how to master streaming video with Blip.tv and Andrew "Action" Schlack. Action Schlack is one organized guy: you can even see him looking down to read his off-camera cue cards, how professional!

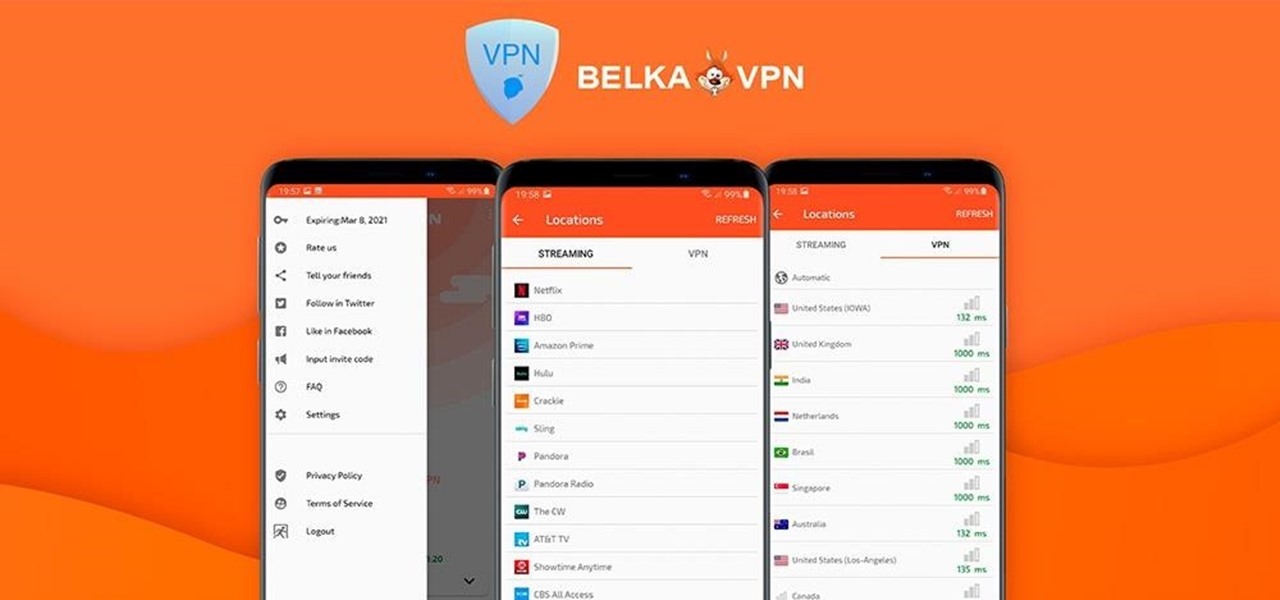
If you're looking to improve your browsing experience, then a VPN is the right way to go. If you're tired of censored or geographically blocked sites and wary of companies selling your data, then a good VPN can be your answer to a problem that limits every aspect of your experience online.

If you're concerned about your data ending up where you don't want it online, then a VPN is something you'll want to consider. A VPN can prevent your bank account information from leaking, your data from being taken directly from your device, and it doesn't come at the cost of any of the convenience we've grown to expect and require from the internet.

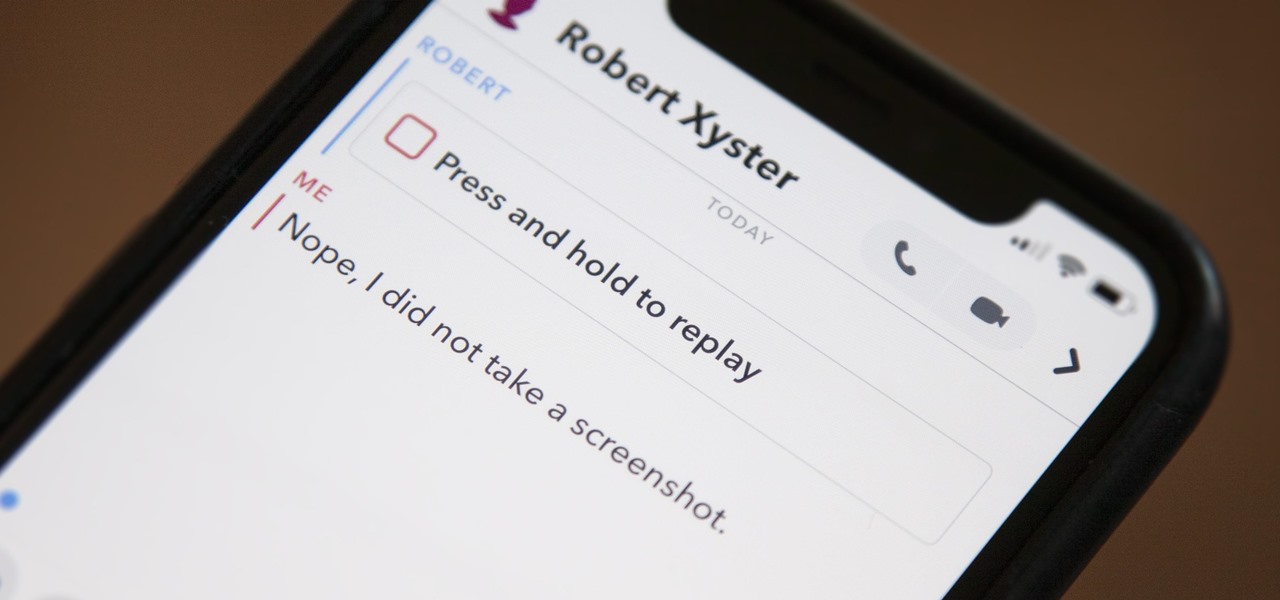
Snapchat doesn't prevent you from taking screenshots of snaps received, but the other user will get an alert either as a prominent push notification or a subtle note in the app. Snapchat has improved its screenshot detection abilities over the years, so it's much harder to circumvent its technology for truly undetected screenshots — but not impossible.

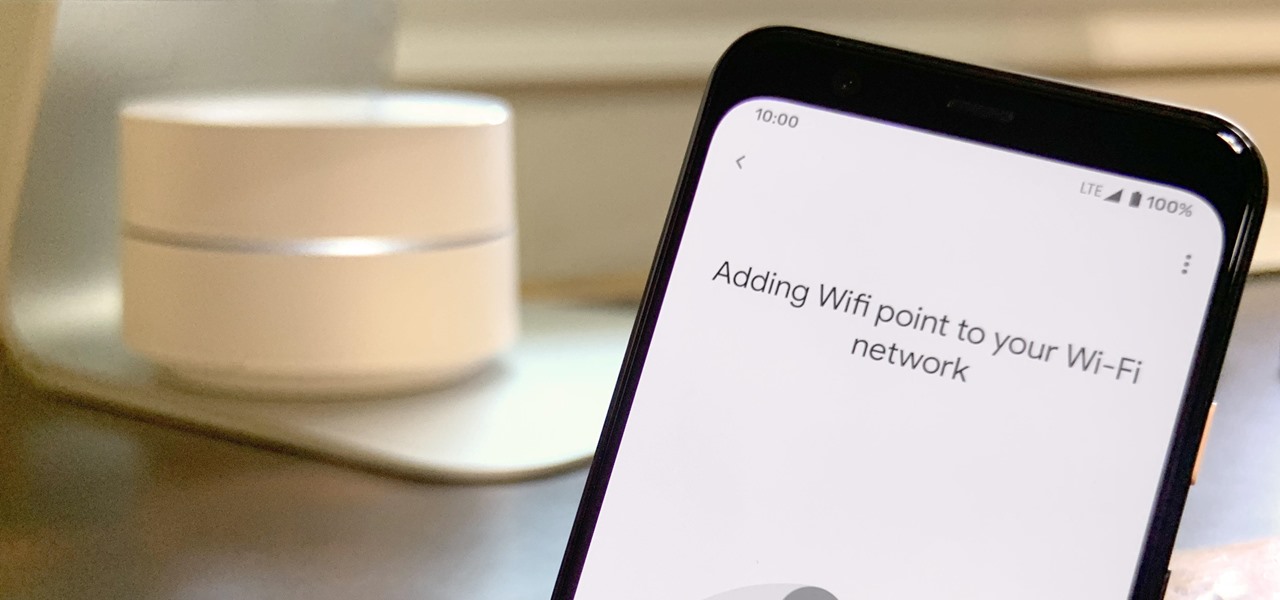
Google is known for merging older products into a new one's ecosystem for ease of use. The transition can take time, and that's the case with the old Google Wifi system now that Nest Wifi is out. Google is working on phasing out the dedicated Google Wifi app in favor of using the Google Home app for all your IoT needs.

Privilege escalation is one of the essential skills a hacker can have and often separates the newbies from the pros. With a continually changing landscape and a plethora of exploits out there, it can be a problematic aspect of any attack. Luckily, some tools can help expedite the process. Linux Exploit Suggester is just one of many to help you get root.

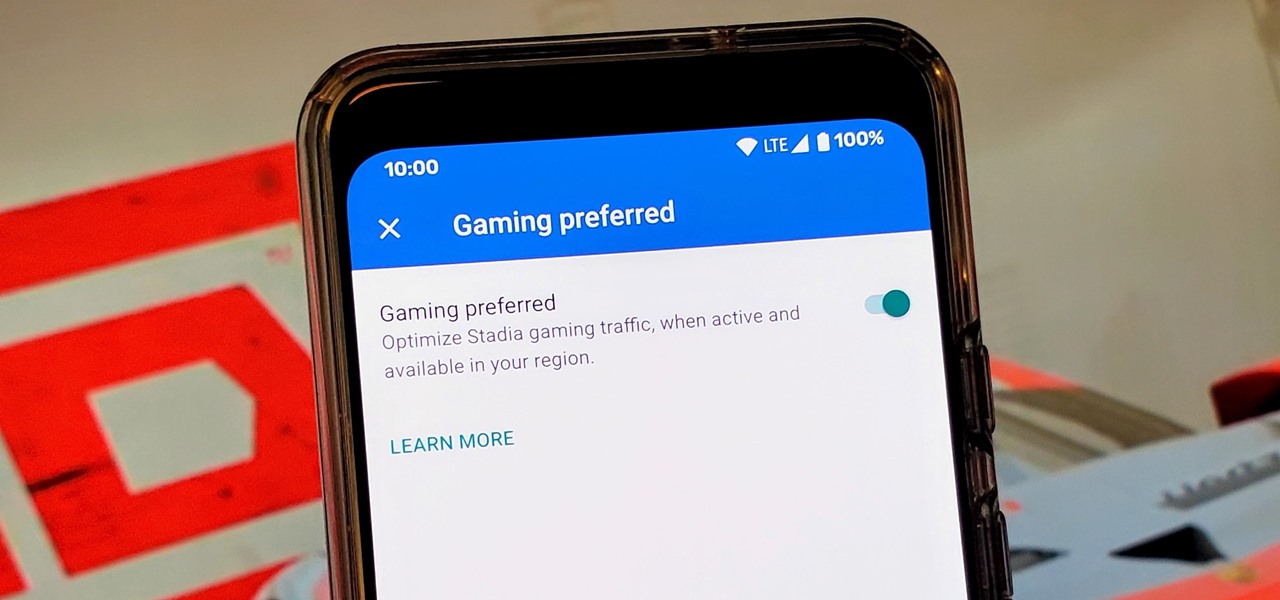
Although not quite as common today with the always-connected world we live in, you still might be having bandwidth wars in your home right now. If the internet connection in your area is mediocre, you know the feeling well. Google Stadia recommends having a 25 Mbps connection for playing in 4K, so you can expect to need at least that much to maintain a smooth, high-quality gaming session.

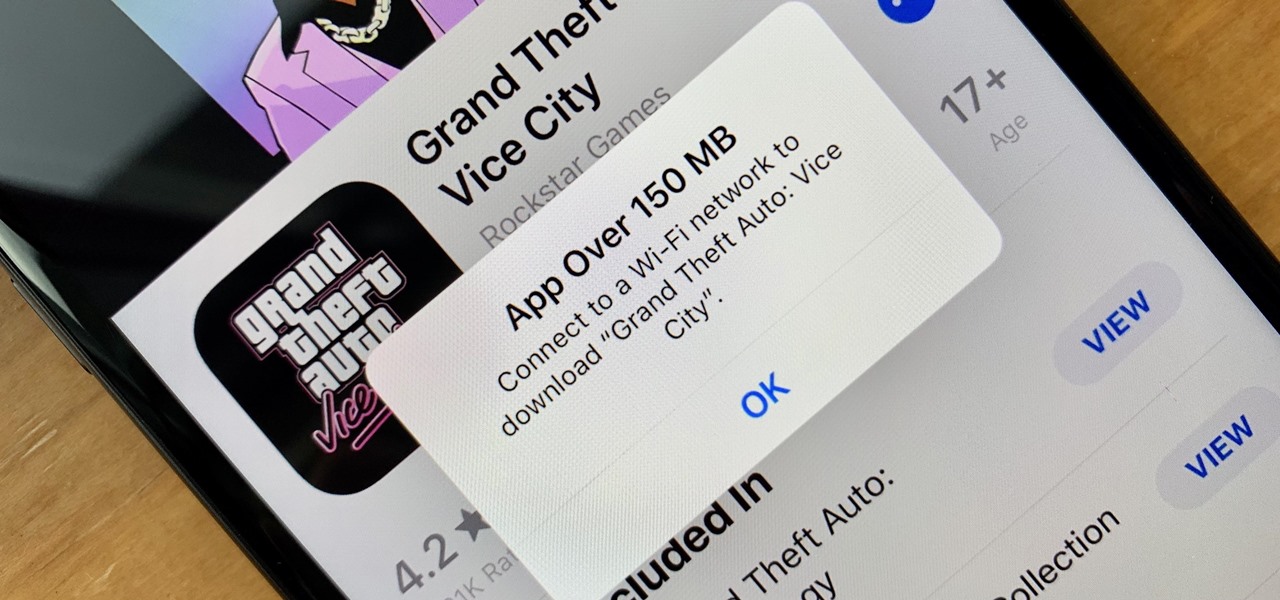
These days, cellular connections can be just as fast — if not faster — than traditional internet providers. That, coupled with the prevalence of unlimited data plans, means less worrying about hopping on a Wi-Fi network to download something. However, try to install an app or update over 150 MB, and your iPhone will insist you switch to Wi-Fi. We don't think this is very fair, so here's a way out.

Hacking Wi-Fi is a lot easier than most people think, but the ways of doing so are clustered around a few common techniques most hackers use. With a few simple actions, the average user can go a long way toward defending against the five most common methods of Wi-Fi hacking, which include password cracking, social engineering, WPS attacks, remote access, and rogue access points.

Whichever web browser you use, each comes with a way to surf the net "secretly." While nothing on the internet is truly anonymous, private browsing modes can help keep your movements hidden from those who might have access to your data. The "secret mode" for the Samsung Internet app goes a step further on Android, by locking your private browsing behind a unique password.

Your homepage should be the site you most likely need to check whenever you start a new session with Samsung Internet. However, times change — perhaps the site you're currently browsing is just what you need to see multiple times a day. In that case, you'll want to know a quick and easy way to set it as your default homepage.

The internet is constantly under siege by bots searching for vulnerabilities to attack and exploit. While conventional wisdom is to prevent these attacks, there are ways to deliberately lure hackers into a trap in order to spy on them, study their behavior, and capture samples of malware. In this tutorial, we'll be creating a Cowrie honeypot, an alluring target to attract and trap hackers.

While it might be a little past its prime now, the running gag about Nokia phones never breaking was one of the internet's favorite jokes. "If you buy one," they would say, "you'll never need another phone again." I think if those users could see into the future, they'd change their tune, as the Nokia 6 is now available to preorder — and I'm guessing it would give any of Nokia's old bricks a run for their money.

Most of us skip through documents like privacy policies and EULAs (end-user license agreements) because they're long and boring. But, as Congress just passed the SJR34 bill in early April, you're probably a little concerned about your personal data, so we summarized the privacy policies for major ISPs and mobile carriers in the US.

No one is safe anymore, it seems. Google's Project Zero has just uncovered how easy it is for attackers to target your phone's Wi-Fi chip, which is essentially a mini processor for Wi-Fi that detects and processes networks.

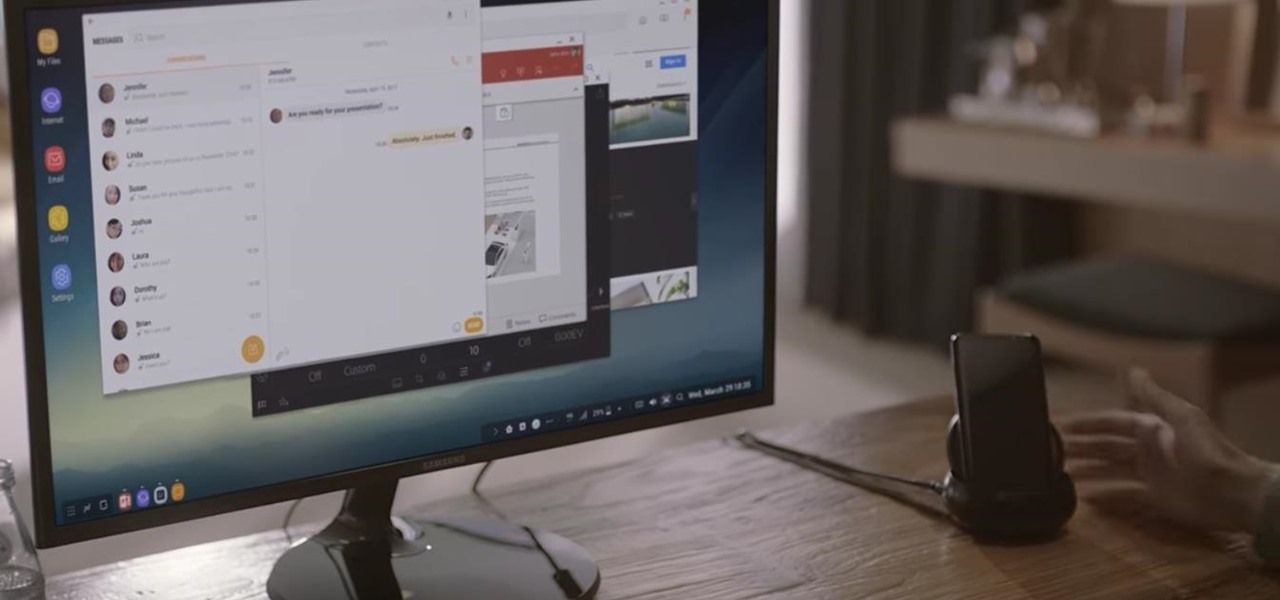
Samsung's new Galaxy S8 can turn into a PC with its DeX dock, but while that may sound like the future of mobile computing on the surface, there are definitely a few issues with the entire setup.

The Snapdragon 820 and 821 were met with praise last year, receiving almost no complaints compared to their overheating predecessor, the Snapdragon 810. But now, all eyes are on Qualcomm to see what goodies they have in store for us this year, as their new SoC, the Snapdragon 835, will be revealed this week at CES 2017.

Hello everybody. I'm back with Part-2 of this series. In this part we will be programming in C our server and i will be explaining one more "key concept" so everybody got a better understanding on this.

Shopping around for a good broadband company or mobile carrier may soon be as easy as shopping for cereal, thanks to the introduction of broadband consumer labels by the FCC for both fixed and mobile broadband.

Watching the NCAA Men's Division I Basketball Tournament without cable used to be easy. As long as you had an internet connection, CBS and Turner (TBS, TNT, and TruTV), which co-broadcast March Madness, let you watch all 67 games online free of charge.

Hello ladies and gentlemen, PySec here coming at you with another informative(hopefully) article for you all. In the last tutorial, we finally finished our discussion about IP Addressing and I intentionally didn't mention a really important concept with which IP Addressing wouldn't be feasible without it. What I'm talking about is how our network device gets the IP Address in order to communicate with other devices on the network/Internet. There are many different ways for that to be accompli...