This video will show you how you can easily find out what your IP address is for a computer which is running the Windows XP operating system. You will first need to go to the start bar and click on the button which says "Run". Choose to run a program called "cmd" by typing this into the bar that appears. This will then open up a black box, where you should type in "ipconfig/all". Typing this in will offer you a list of information about the internet service you are currently using and one of ...

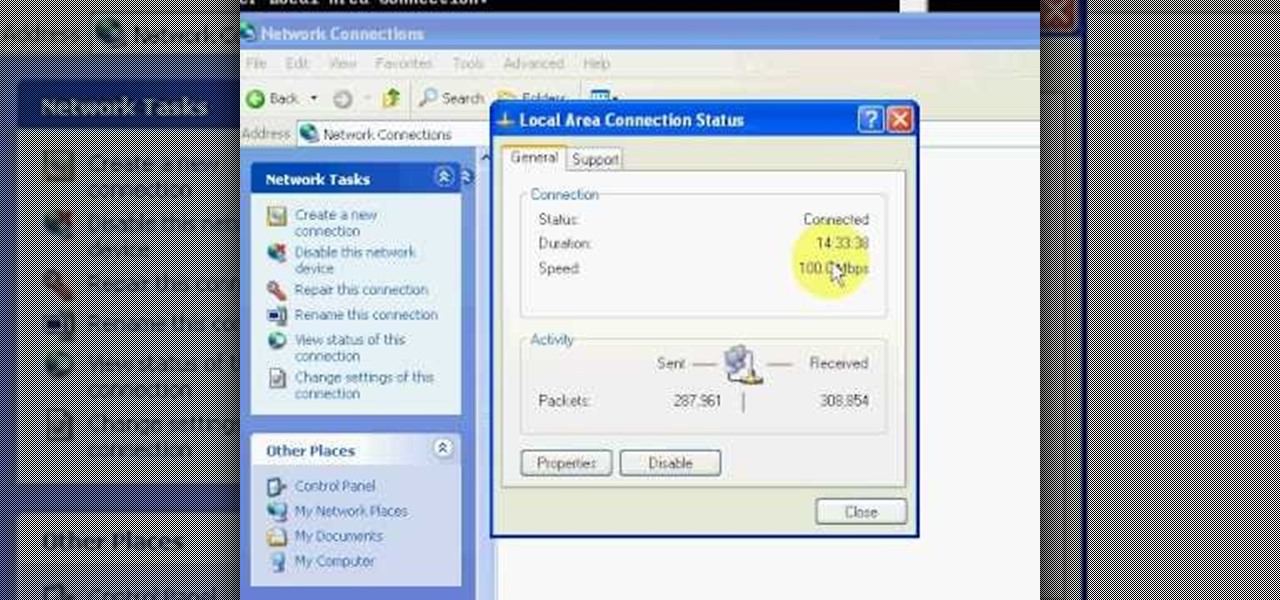
This video will show you how to find your own IP address in Windows Vista, which is more difficult and confusing to use than Windows XP was. First, you should go down to the bottom right hand corner and find an icon of two computers, which is your network connection button. Click on the Networks and Sharing selection and find the section which says "View status". After clicking on this, you will find a section which will be labeled "IPv4". The numbers which are indicated after this are the nu...

In this tutorial the author shows how to find, download and install Firefox 3. He points out to the Mozilla Firefox website which is [www.mozilla.org/firefox]. Now you reach the Firefox web page where there is a link to download the browser. After clicking the link you will be prompted to save the file and now you can download the software. Now after the software gets installed the author guides you through the various steps to get Firefox 3 installed. He also shows how to transfer settings a...

Is your PC too slow? Want your PC performance to increase without paying any money? Well, in this video the viewers will be taught how to speed up their PC and internet speed without spending a dime. First of all, the video goes through some of the potential applications that are draining the computers' resources, such as multiple anti-virus. The video teaches how to delete and remove unneeded applications and free up additional RAM. One of the key ideas is to close and disable applications t...

Learn how to browse the Internet at work and get away with it. Load Excel (Any version will do). Click on the Data tab. Click 'Import External Data'. Click 'New Web Query'. Once the window has loaded, click through the prompts, selecting Yes. When the window has loaded completely, go to your favorite website in any browser you want. For this example, Twitter is used. Go to the RSS Feed and copy the link that appears at the top. Paste the link into Excel and click the Import button. Accept any...

Slow down? What!?! You've got to love the simplicity when it comes to long drive tips from long drive competitors. The long hitting Jamie Sadlowski shares his simple tip for more power, and it's not what you might think. See how to slow your golf swing down for more power.

This video explains how to make an Origami Icosahedron (designed by Heinz Strobl) using 50 strips of paper. You need 20 strips of a single color for the triangles and 30 of a contrasting color to connect the triangles.

Learn how to fold an origami dragon with instruction by Ancella Simoes. Ancella Simoes is the author of the Origamiancy Blog and creator of all the Origamiancy origami tutorial videos on WonderHowTo. From Ancella's site:

VNC stands for Virtual Network Computing. It is remote control software which allows you to view and fully interact with one computer desktop (the "VNC server") using a simple program (the "VNC viewer") on another computer desktop anywhere on the Internet. The two computers don't even have to be the same type, so for example you can use VNC to view a Windows Vista desktop at the office on a Linux or Mac computer at home. For ultimate simplicity, there is even a Java viewer, so that any deskto...

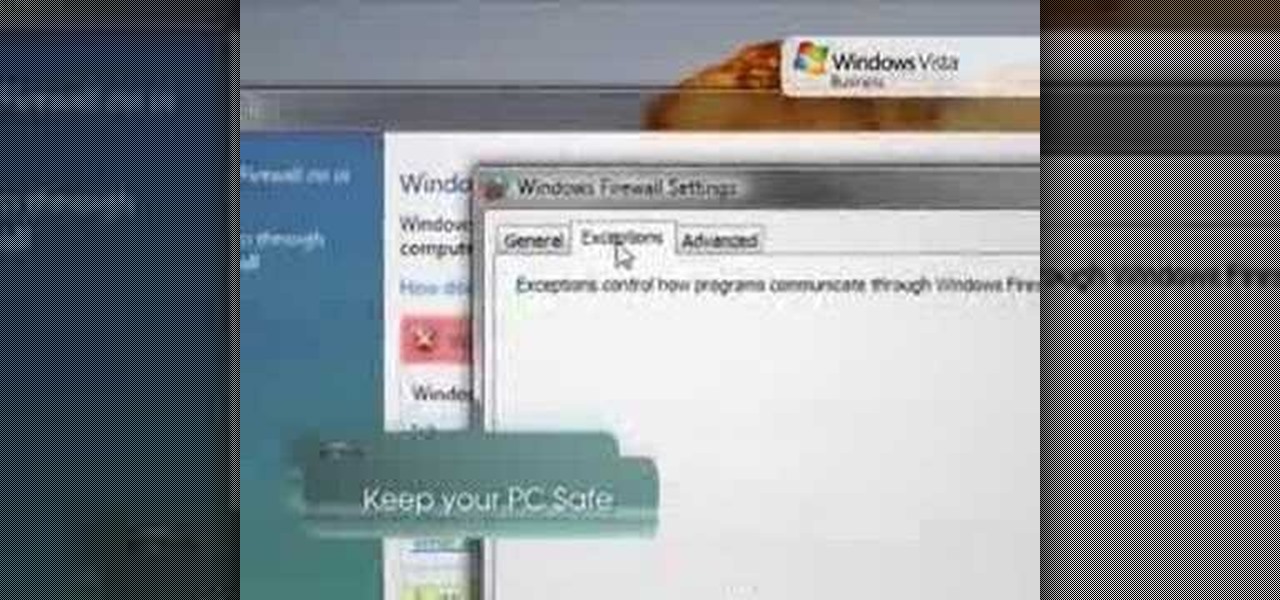
In order to keep your PC safe from annoying or potentially dangerous threats on the Internet, a properly-configured firewall is a crucial item in helping prevent your system from becoming compromised. The Windows Firewall in Windows Vista™ is the first line of defense in helping to keep your computer safe. By preventing your computer from being infected by malware, Windows Firewall is designed to be easy to use and is automatically enabled to protect your computer as soon as Windows starts. T...

A good video can turn a mediocre song into a smash hit, while a bad video. Well, that's just embarrassing. While MTV doesn't really play music anymore, the internet is flooded with good old fashioned music videos. This how-to video will offer some tips for making yours stand out of the crowd. You don't need to be too literal, but try picking a style. Watch this video tutorial and learn how to make a music video.

This tutorial teaches you how to warm up your cello playing for an audition. By working the "pulling" muscles of your left hand you will create stronger more precise fingers, like "core training" for your hand. When you add these variations you will wake up and warm up your brain, open up new connections by challenging the coordination between your left and right hands. Watch this how to video and you will improve your cello playing with these warm up exercises.

Here are five different techniques you can use to create rounded corners for boxes on a website. There are always different ways to do things with CSS and rounded corners is a great example of that. Each of these five techniques has advantages and disadvantages. Knowing all of them so you can choose the perfect one in each situation is the kind of thing that makes you the best CSS ninja you can be! So if you want to make cool Internet websites and be the best designer around, why not start he...

Do you have the perfect timing? Timing your swing is important, but sometimes a clock can do a whole lot more to help your golf swing. By imagining the face of a clock, you can effectively train your body to calculate the proper swing length for shots from various distances. Sound intriguing? Let Doug Hammer, PGA, show you the way. Watch this video golf tutorial and learn how to clock wedge shots.

This new episode of Full Disclosure shows you how to use a SSH Tunnel to secure your data when you are on an untrusted LAN (ex. Coffee Shop, School's network, or Defcon). Furthermore, you can use the SSH Tunnel to bypass the LAN's internet filters. The SSH tunnel protocol works by encapsulates your data into an encrypted payload and transmitting it to the SSH Server which is setup on a trusted LAN.

So, AOL might not be mailing as many internet CDs as they did in the past, but chances are you have a few of those junk discs lying around. Chances are you have tons of junk CDs and DVDs laying around, not necessarily from AOL. And now... it's time to turn them into something useful, or at least fun! Kipkay shows you how to build a mini-disco ball from those recycled discs, with scissors, hot glue and a styrofoam ball also needed.

Smartphones are inherently bad for privacy. You've basically got a tracking device in your pocket, pinging off cell towers and locking onto GPS satellites. All the while, tracking cookies, advertising IDs, and usage stats follow you around the internet.

Samsung, like other OEMs, partners with third-party companies to include their apps on Galaxy devices. For example, Microsoft pays Samsung millions to pre-install certain Office apps. But one of these partners might not be on the up and up.

While SSH is a powerful tool for controlling a computer remotely, not all applications can be run over the command line. Some apps (like Firefox) and hacking tools (like Airgeddon) require opening multiple X windows to function, which can be accomplished by taking advantage of built-in graphical X forwarding for SSH.

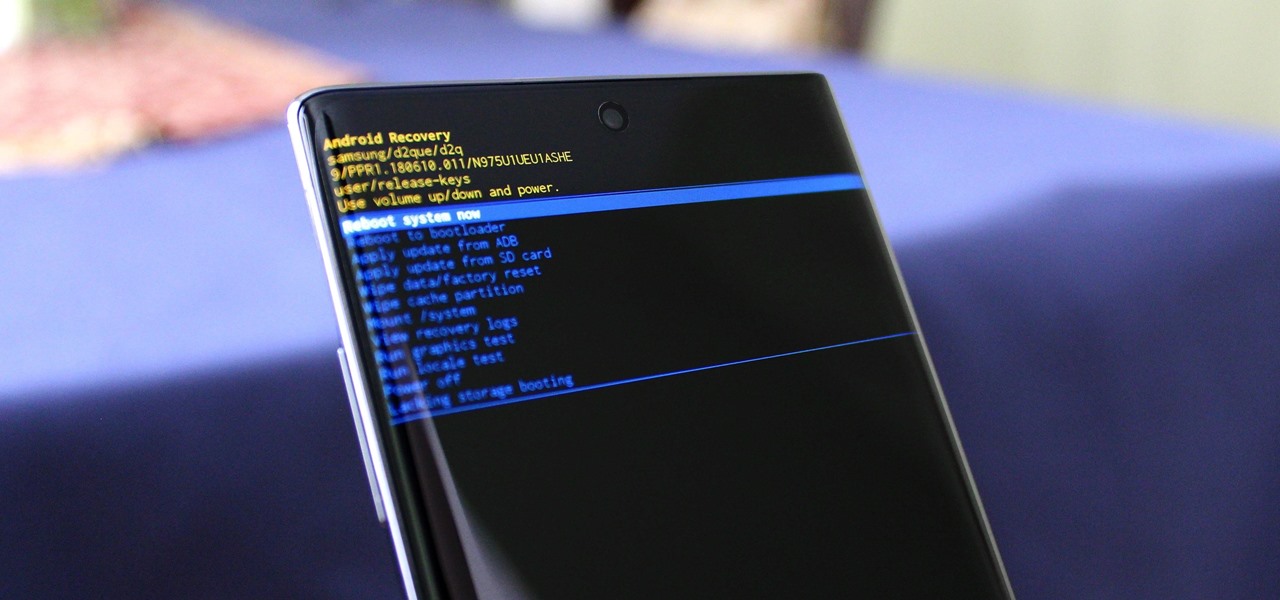
You can't call yourself an Android pro without knowing about Recovery or Download Mode. These menus are critical to do more advanced tasks on your phone, include sideloading software updates and un-bricking a device. But this year, Samsung changed the button combinations that will get you there.

With a cheap computer, smaller than the Raspberry Pi, an attacker can create a remote hacking device. The device can be attached to a target router without anyone's knowledge and enable the hacker to perform a variety of network-based attacks from anywhere in the world.

Encrypting payloads and encoding stagers are more effective against macOS than one might think. It's very easy to evade VirusTotal and macOS antivirus software using a few simple tricks.

Having a dropped call can be incredibly frustrating, especially when you look down and see that your iPhone has full reception. While there's any number of issues that can cause this, one common and often overlooked issue is your iPhone failing to switch cell towers as appropriately needed.

After finding and monitoring nearby wireless access points and devices connected to them, hackers can use this information to bypass some types of security, like the kind used for Wi-Fi hotspots in coffee shops, hotels, and in flights high above the ground. By swapping their MAC address for that of someone already connected, a hacker can bypass the MAC filter and connect freely.

In the previous article in this short series, we learned how to find our neighbor's name using publicly accessible information and how to monitor device activity on their home network. With this information at our disposal, it's time to get into installing and configuring the necessary tools to begin our attack on John Smith's computer.

PowerShell Empire is an amazing framework that is widely used by penetration testers for exploiting Microsoft Windows hosts. In our previous guide, we discussed why and when it's important to use, as well as some general info on listeners, stagers, agents, and modules. Now, we will actually explore setting up listeners and generating a stager.

The public leaks of NSA tools and information have led to the release of previously secret zero-day exploits such as EternalBlue, which was used in the notorious WannaCry ransomware attack. Despite multiple patches being released, many users have failed to update their systems, so many devices are still vulnerable to these now-public attacks.

Tor is an excellent obfuscation network for web traffic, and while instant messaging over the network is very useful, it can be relatively difficult to configure. In this guide, we'll look at two synchronous communications platforms (instant messengers) which can be routed over the Tor network, Ricochet and XMPP.

In my previous article, we learned how to generate a vulnerable virtual machine using SecGen to safely and legally practice hacking. In this tutorial, we will put it all together, and learn how to actually hack our practice VM. This will provide some insight into the methodology behind an actual attack and demonstrate the proper way to practice on a VM.

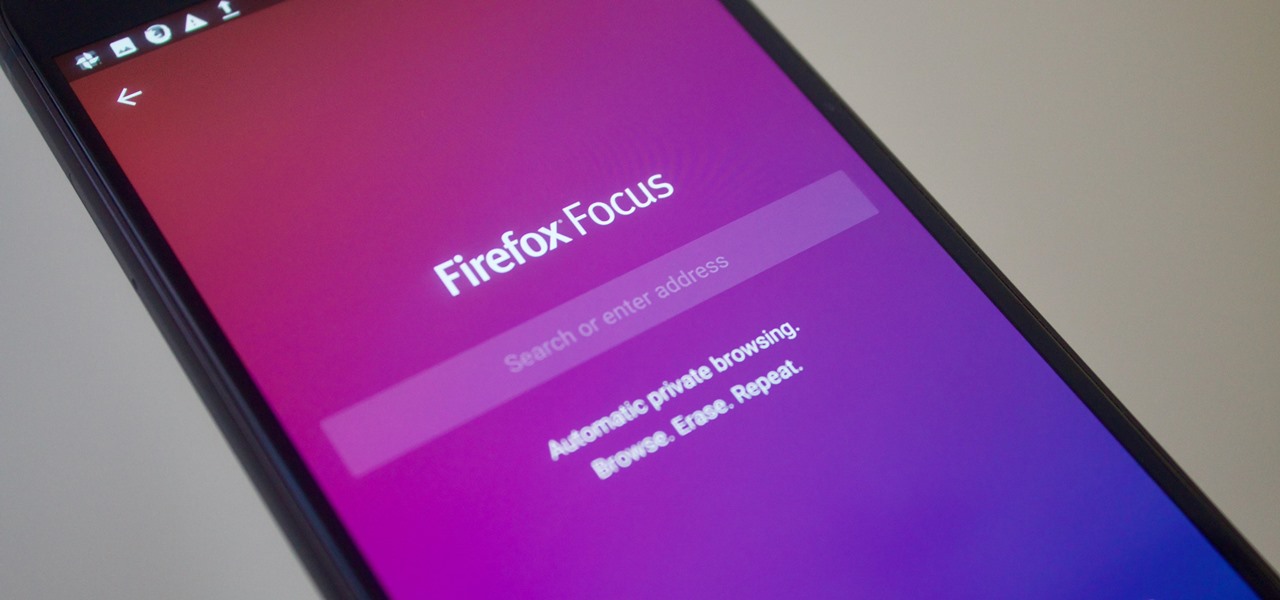
Firefox Focus is Mozilla's effort to make your internet experience a little more secure. Originally released in November 2016 for iOS, Focus blocks internet trackers, search history, anything that gets in the way of a clean, private browsing experience.

Several recent research studies have pointed to the importance of the microbes that live in our gut to many aspects of our health. A recent finding shows how bacteria that penetrate the mucus lining of the colon could play a significant role in diabetes.

When you do an internet search, you'll see ads that are relevant to your query mixed in with the rest of your results. Nothing surprising there—it's how the internet is funded. But then, when you click one of the search results, you'll also see ads that are related to your initial search. Now that's a bit creepy, because it demonstrates that one webpage knows what you typed into a different webpage.

While it may not sound scary right off the bat, Blue Coat Systems now has an intermediate certificate authority. If you don't know what a certificate authority (CA) is, or who Blue Coat is, who cares, right? But you should... whether you use Mac or Windows.

"It just ticked me off," he said. In March 2011, Neil Singh paid $50 to back the Hanfree iPad stand on Kickstarter. The project was funded at $35,000, but production stalled, and the delivery estimates kept getting pushed back.

Hello, everyone. Stealth is a large part of any successful hack; if we don't get noticed, we're much less likely to be caught. In these next few articles, we'll be building a shell based on keeping us hidden from a firewall. There are many ways to stay hidden from a firewall, but we'll only be incorporating a couple into our shell. This article will outline and explain these evasion concepts and techniques.

Welcome back, my budding hackers! As I have mentioned many times throughout this series, knowing a bit of digital forensics might keep you out of a lot of trouble. In addition, digital forensics is a burgeoning and high paying career. Some knowledge and certifications in this field will likely help you land a Security Engineer position or put you on the Incident Response Team at your employer.

When attempting to gain access to a server, there may come a point when you need to get around file upload restrictions to upload something. If we can find a way to get around the restrictions, then we can upload anything we want to the server, effectively compromising it. That is what we'll be doing here today, so let's get started!

Welcome back, my novice hackers! Episode 6 of Mr. Robot has come and gone and, as usual, it did not disappoint. Once again, our hero, Elliot, has used his extraordinary intellect and hacking skills to awe and inspire us.

Welcome back, my novice hackers! Previously in my "Spy on Anyone" series, we used our hacking skills to turn a target's computer system into a bug to record conversations and found and downloaded confidential documents on someone's computer. In this tutorial, I will show you how to spy on somebody's Internet traffic.

If beauty is in the eye of the beholder, music lies in the ear. Even within a group of friends who share enough common interests to sit around and socialize over, music tastes can vary dramatically.