This sun dried tomato pesto-stuffed pork roast is ready for the oven in ten minutes. Follow along and learn how to make this pork recipe. This cooking how-to video is part of Quick Fix Meals with Robin Miller show hosted by Robin Miller. Busy people everywhere face the same dilemma, how to get healthy weeknight dinners on the table when you've only got minutes to spare. Cookbook author, nutritionist and food journalist Robin Miller guides you through the landmines of getting food on the table...

For a health conscious change of pace, try a tuna burger! They are so easy to make, all you have to get is some canned tuna, which you probably already have in our pantry. This cooking how-to video is part of Quick Fix Meals with Robin Miller show hosted by Robin Miller.

Bake an incredibly simple side dish of honey roasted sweet potatoes, Follow along to learn how easy it is to incorporate healthy vegetables into your diet. This cooking how-to video is part of Healthy Appetite with Ellie Krieger show hosted by Ellie Krieger. Cooking healthy food can be quick, easy, but most of all, delicious. Nutritionist and author Ellie Krieger has created fast and simple healthy recipes for the real world. She'll show you how simple it can be to stay on the healthy track n...

Is your kid's desk all cluttered? Help them stay organize by making an easy desk desk set for your child's school supplies. Watch this how to video tutorial as our host shows you how to make a pencil holder using a can, paper and some glue. Have your children help you with this fun activity.

This tutorial illustrates how a wireless pinhole spy video camera can jam wireless internet or WiFi signals.

A basic introduction to Registry Editing. Learn how to hack Internet Explorer's text.

This video shows how to check your hosts file for spyware. This is a valuable tool, if your computer has spyware it can greatly affect the performance of your computer.

Did you know that you can improve the Wi-Fi in your home without the stress of changing providers or using a costly professional? The answer lies in a simple app you can use yourself at home, and right now, the NetSpot Home Wi-Fi Analyzer With Lifetime Upgrades is on sale for just $39.99. That's 41% off the regular price of $68.

For all the benefits 5G brings to cellular data, it isn't without weaknesses, the biggest being privacy. Yes, the latest standard comes with breakneck downloads speeds up to 4.3 Gbps, but at what cost? Like with all things on the internet, 5G devices open opportunities for both good and bad actors.

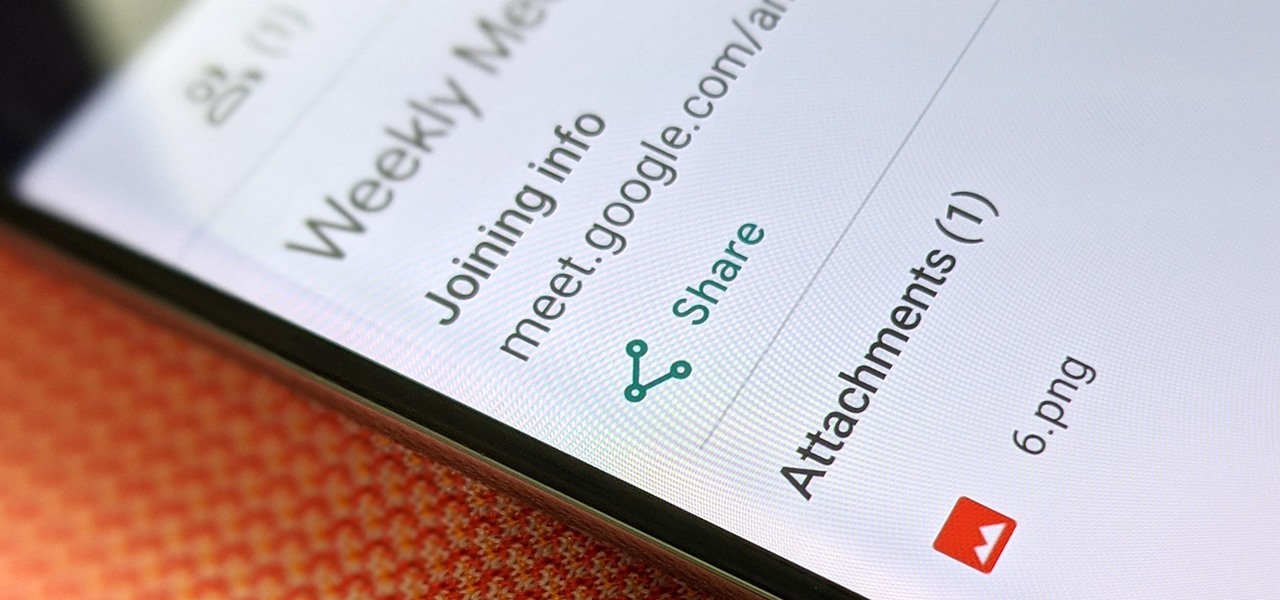
Google Meet might not have virtual backgrounds like Zoom, but it hits all of the other basics, from hosting many multiples of video participants to sharing your screen, that you'd expect from a robust video conferencing platform.

Attacks against databases have become one of the most popular and lucrative activities for hackers recently. New data breaches seem to be popping up every week, but even with all of that attention, databases continue to be a prime target. All of these attacks have to start somewhere, and we'll be exploring a variety of methods to gather information on PostgreSQL databases with Metasploit.

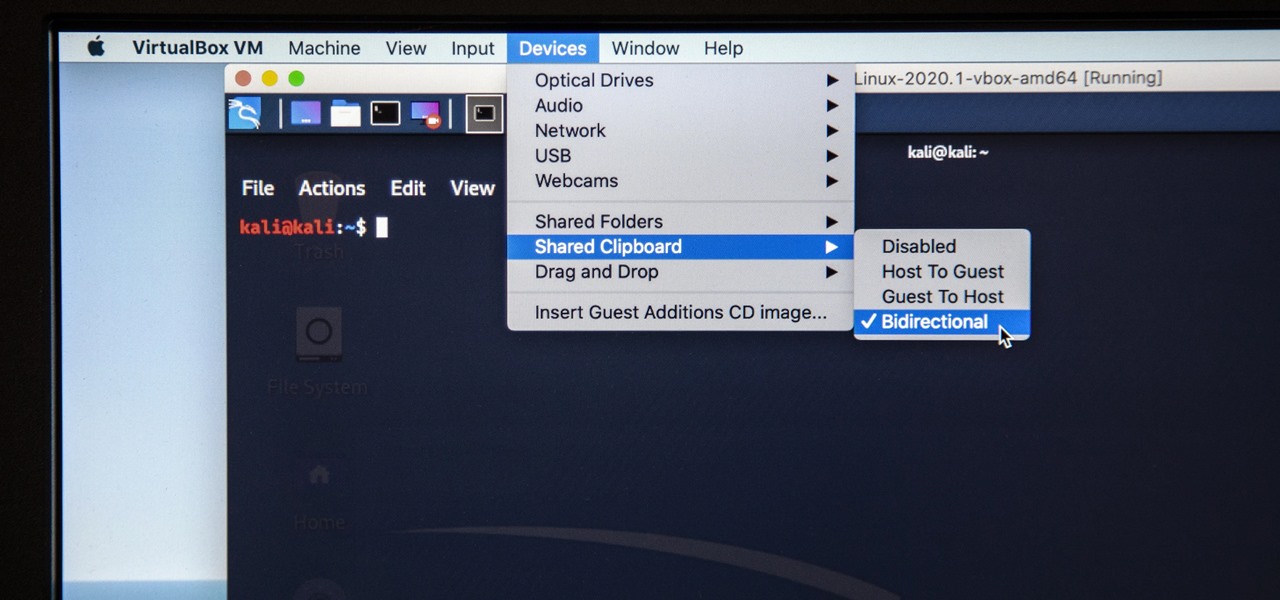
Last week, I updated VirtualBox on my computer since I had skipped a few versions, then I could no longer copy text or paste text from my Kali virtual machine to my host OS and vice versa. Installing the Guest Additions didn't seem to do anything, and the bidirectional shared clipboard was enabled, but there was one thing that did work for me that may help you out too if you experience the issue.

Data is king. Nearly every carrier and MVNO offers unlimited talk and text with their cellular plans. Where they differ is the amount of data available, so that's the part that can save or cost you the most money.

With all this time spent stuck at home because of the COVID-19 pandemic, HQ Trivia would be a prime way to beat the boredom. Unfortunately, HQ went belly up in February, just before everyone had stay-at-home orders. While HQ has teased a potential comeback, there are other trivia games out there that are live right now. One of those brings the spirit of HQ Trivia back to our phones.

It's OK to want an extended break when you're working or learning from home. Maybe you want to play a video game, spend more time with your family, hang out with your dog, or FaceTime with friends. But how can you do that when you're supposed to be in a Zoom video conference or class? Thanks to one Zoom feature on your iPhone, it may be easier than you think.

Facebook has announced the cancelation of its annual F8 developer conference, citing concerns around the developing coronavirus health crisis.

So far, iOS 13.4 hasn't been a disappointment. From new Memoji stickers, a refreshed Mail toolbar, and even the beginnings of controlling your car with your iPhone, Apple's latest iOS update is looking like a good one. That's why we're excited that Apple just released the third 13.4 developer beta today, one week after the release of the second one.

Nearly every connection to the internet is dependent on the Domain Name System. DNS, as it's more commonly called, translates domain names like gadgethacks.com into IP addresses, which is what network devices use to route data. The problem with DNS servers is that they don't have your privacy in mind.

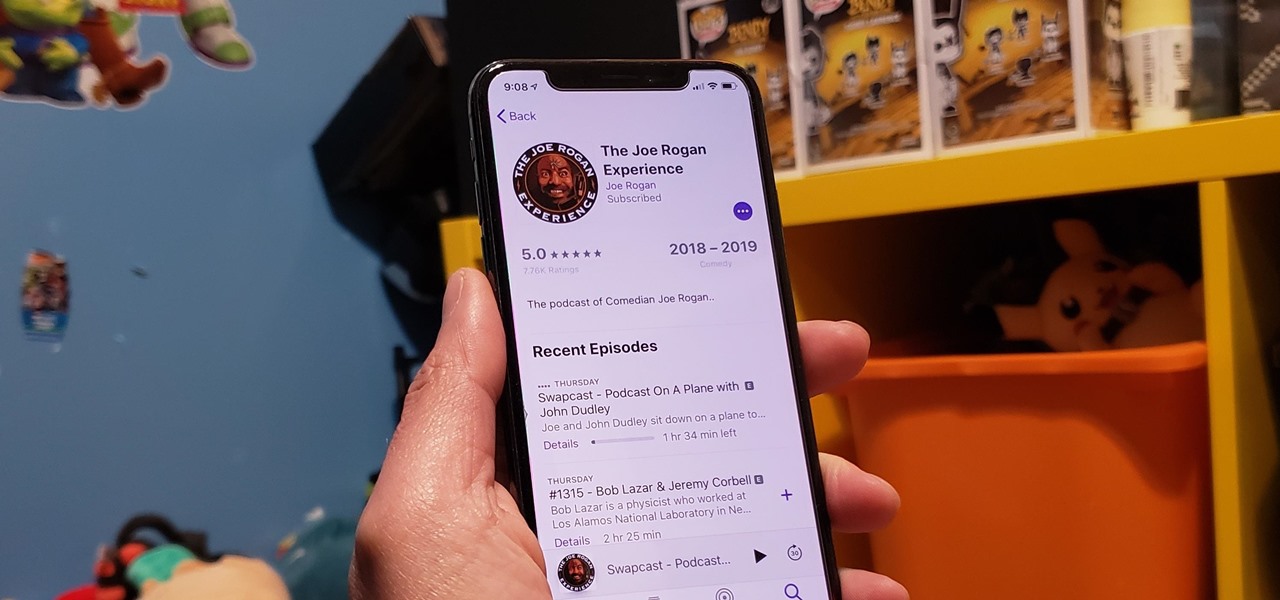
Ratings and reviews apply everywhere, from a restaurant you want to try to a new camera you're thinking of buying and games you might want to play. Podcasts are no different. Reading reviews of shows can help determine which are worth listening to, and your opinion is valuable to other people too. In Apple Podcasts, there are a few different ways to read, rate, and review shows.

When researching a person using open source intelligence, the goal is to find clues that tie information about a target into a bigger picture. Screen names are perfect for this because they are unique and link data together, as people often reuse them in accounts across the internet. With Sherlock, we can instantly hunt down social media accounts created with a unique screen name on many online platforms simultaneously.

Firewall solutions for macOS aren't impervious to attacks. By taking advantage of web browser dependencies already whitelisted by the firewall, an attacker can exfiltrate data or remotely control a MacBook, iMac, Mac mini, or another computer running macOS (previously known as Mac OS X).

If you use the internet regularly, it's nearly impossible to avoid memes. They are the epitome of internet culture, demonstrating how jokes can spread and change like wildfire. While there are many different types, the most common ones you'll come across are images and GIFs with humorous text accompanying them, and we've found the best iOS apps to help you create your own.

If you've grown bored of day-to-day hacking and need a new toy to experiment with, we've compiled a list of gadgets to help you take password cracking and wireless hacking to the next level. If you're not a white hat or pentester yourself but have one to shop for, whether for a birthday, Christmas present, or other gift-giving reason, these also make great gift ideas.

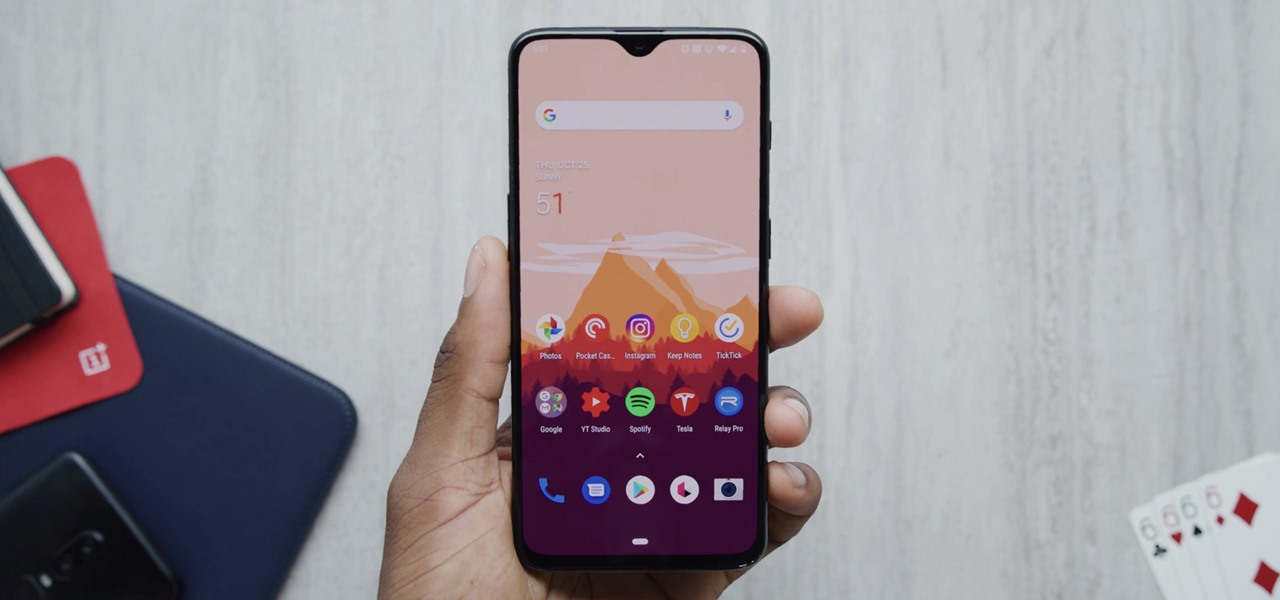
With the same starting price as its predecessor and a nice list of improvements, the OnePlus 6T is a great buy for a number of reasons. But for many Android users, the main selling point for the latest OnePlus flagship is how easy it will be to root and mod the device.

One of the best ways to improve your skills as a hacker is to learn to combine different avenues of attack to achieve success. What if it were possible to get a victim to connect to our machine and execute a chosen payload on our behalf? This is indeed possible with the almighty Metasploit and the aid of a technique known as command injection.

A simple security flaw can allow an attacker to gain a strong foothold with little effort on their part. When a web application permits remotely hosted files to be loaded without any validation, a whole can of worms is opened up, with consequences ranging from simple website defacement to full-on code execution. For this reason, RFI can be a promising path to obtaining a shell.

If you're using a mobile device, it's a pretty safe bet that your apps are sending lots of information back and forth from their servers. To make sure there is no inappropriate data collection going on, it's worth setting up a web proxy to spy on this traffic, so you know exactly which apps are "phoning home" and when.

While Wi-Fi networks can be set up by smart IT people, that doesn't mean the users of the system are similarly tech-savvy. We'll demonstrate how an evil twin attack can steal Wi-Fi passwords by kicking a user off their trusted network while creating a nearly identical fake one. This forces the victim to connect to the fake network and supply the Wi-Fi password to regain internet access.

HBO's Westworld has touched down on iOS as a mobile game, giving players the chance to manage their very own futuristic theme park set in the wild west. Unfortunately, the game is currently only available in select countries as a soft launch until its fully developed. But if you'd like to try out this game right now, there's a simple workaround to get Westworld on your iPhone.

Stop me if you've heard this one before: scan an image with your iPhone's camera and augmented reality content shows up.

Most of us have never put much thought into this, but the question needs to be asked — what exactly happens to all of our online accounts when we die? No, the internet won't just know and delete accounts for you, so you need to plan for life's one guarantee. Because without a plan, things become a lot harder to sort out.

Ports allow network and internet-connected devices to interact using specified channels. While servers with dedicated IP addresses can connect directly to the internet and make ports publicly available, a system behind a router on a local network may not be open to the rest of the web. To overcome the issue, port forwarding can be used to make these devices publicly accessible.

With the addition of the OpenSSH client and server in the Windows 10 Fall Creators Update, you no longer have to rely on third-party programs to open an SSH server and connect to a Windows machine. While still a beta feature, this represents a long-overdue update fulfilling a promise made back in 2015.

While there aren't as many ways to customize your iPhone like there is on Android, there are still a lot of apps out there that can help streamline and enhance your experience beyond Apple's own default options — and we've hand-picked over 100 essentials.

The public leaks of NSA tools and information have led to the release of previously secret zero-day exploits such as EternalBlue, which was used in the notorious WannaCry ransomware attack. Despite multiple patches being released, many users have failed to update their systems, so many devices are still vulnerable to these now-public attacks.

The staff at Next Reality News is legitimately excited about the prospects that Google's ARCore could bring not only to smartphones and tablets running Android, but also to Android-based hardware such as smartglasses.

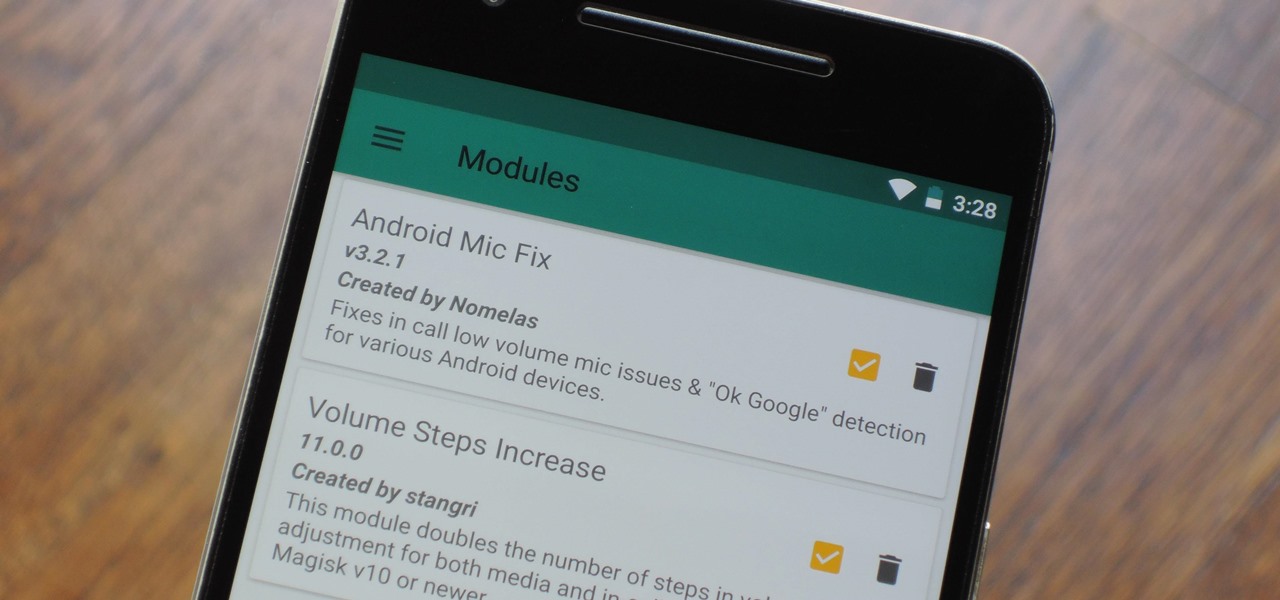
Much like Xposed or Cydia, Magisk has an official repository that makes it easy to download root-level tweaks. These tweaks are called modules, and they can do anything from changing your emojis to installing high-level audio mods. But as it stands, a large number of Magisk modules are not hosted on the official repo just yet, so there are two primary ways to install them.

PowerShell Empire is a post-exploitation framework for computers and servers running Microsoft Windows, Windows Server operating systems, or both. In these tutorials, we will be exploring everything from how to install Powershell Empire to how to snoop around a target's computer without the antivirus software knowing about it. If we are lucky, we might even be able to obtain domain administrator credentials and own the whole network.

The number of households in the US that go hungry because they lack money for food hit a high of almost 15% in 2011. While that number continues to decline, nearly 13% of American households still go hungry.