From time immemorial, human beings seem to be at odds with one another. When these differences become so heated and unresolvable, it eventually erodes into physical violence. This violence has manifested into some of the most horrific exercises in human history, things which every school child is aware of and none of which we have to recount here. Although humans have been cruel and violent for a very long time, the 20th century may have epitomized that behavior. With two World Wars and many,...

Welcome back, my greenhorn hackers! In previous Wi-Fi hacking tutorials, I have shown you ways to create an Evil Twin, to DoS a wireless AP, and to crack WEP and WPA2 passwords, but in this tutorial, I will show you something a little bit different.

Welcome back, my tenderfoot hackers! As you know, DNS, or Domain Name System, is critical to the operation of the Internet. It provides us with the ability to type in domain names such as www.wonderhowto.com rather than the IP address. This simple service saves us from having to memorize thousands of our favorite website IP addresses. Instead, we simply type in a domain name to retrieve the website.

Depending on who you ask, internet connectivity should be a basic human right. With Google recently embarking on a project to provide internet capabilities to remote corners of the world using balloons and satellites while Facebook attempts to do the same with unmanned drones, the concept of free web access is steadily gaining steam.
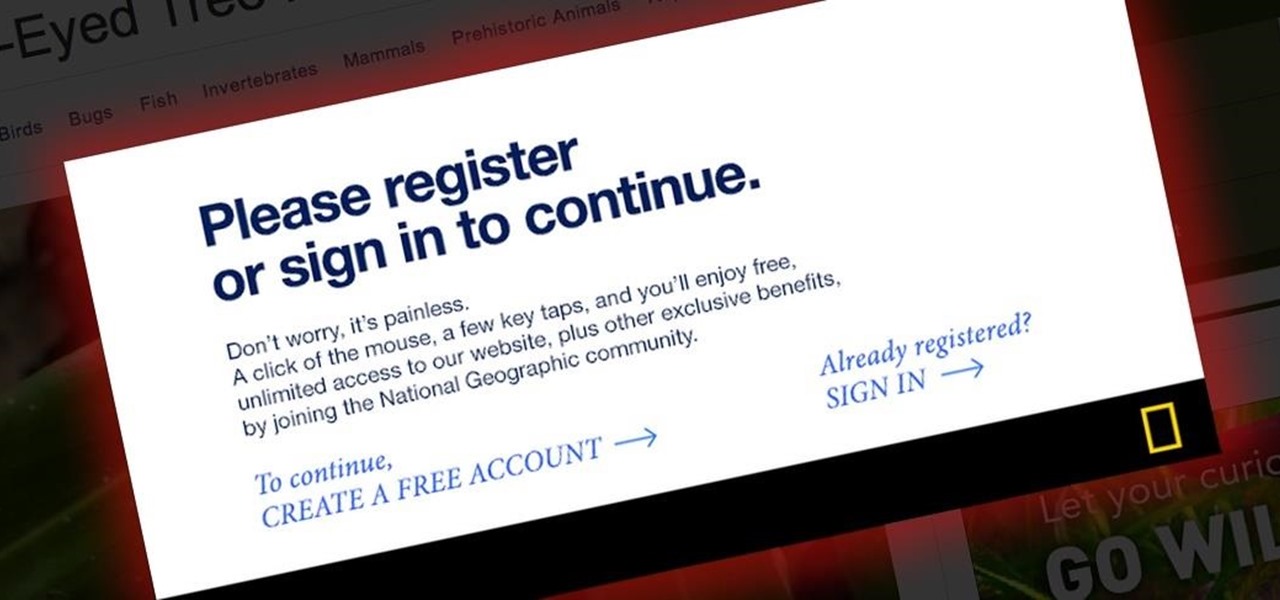
Last night, I was reading a riveting National Geographic article on the green-eyed tree frog, until I was quickly interrupted by an annoying popup asking me to "create a free account" or "sign in." Really, I'd like to do neither. I just want to read about tree frogs.
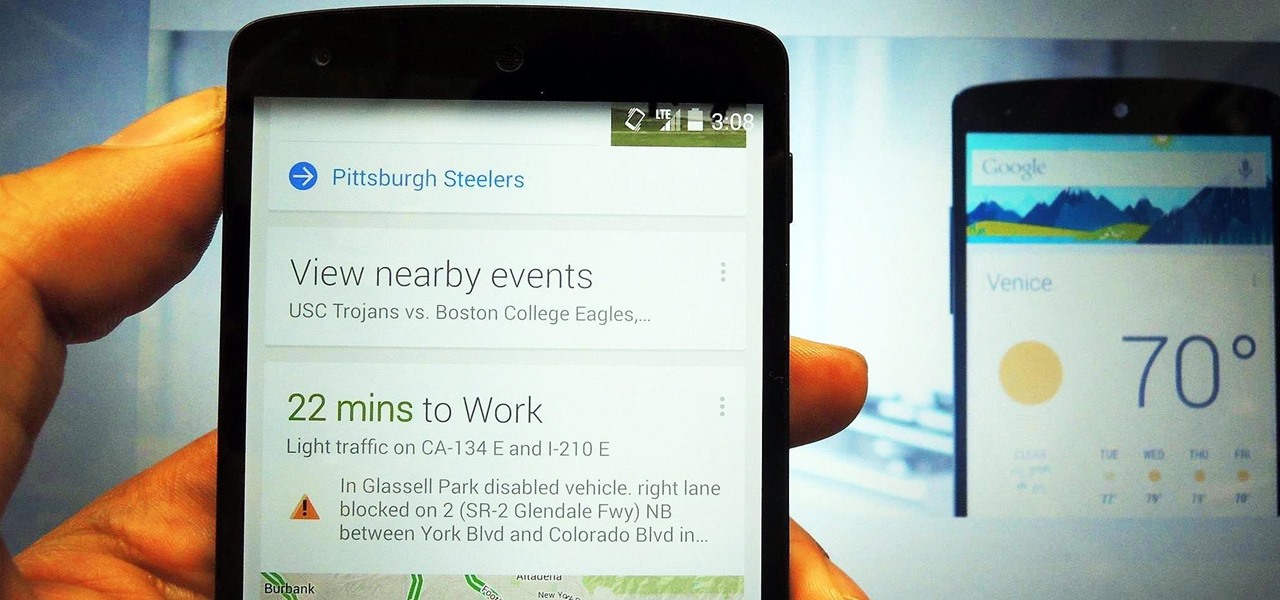
The launch of Android 4.1 Jelly Bean was also the launch of Google Now, a service that was supposed to one-up Siri, the resident personal assistant for iOS devices. Google Now offered enticing features, but its launch went unnoticed by a great many Android users.

Welcome back, my fledgling hackers! Awhile back, I demonstrated one of my favorite little tools, netcat, which enables us to create a connection between any two machines and transfer files or spawn a command shell for "owning" the system. Despite the beauty and elegance of this little tool, it has one major drawback—the transfers between the computers can be detected by security devices such as firewalls and an intrusion detection system (IDS).

Not having internet sucks! We do a ton online these days, from working, shopping, studying, and collaborating, to watching fail videos and endlessly clicking through memes.

We've all been there. Your phone is on your nightstand, but you're on the couch in the living room browsing the web on your Nexus 7. Then you hear it—a faint sound for a new text message notification from the bedroom.

Do you ever wonder how all these celebrities continue to have their private photos spread all over the internet? While celebrities' phones and computers are forever vulnerable to attacks, the common folk must also be wary. No matter how careful you think you were went you sent those "candid" photos to your ex, with a little effort and access to public information, your pictures can be snagged, too. Here's how.

With the new year right around the corner, it's time to talk about the end of the 19th century, a time which plays an enormous role in Steampunk. If you've done any reading of British books written from about 1890 to 1899, you may have come across the phrase 'fin de siecle' and wondered what it meant. You also may have come across this term in reading about the late Victorian era. No worries, I'll tell you all about it! Image by Giovanni Dicandia

A Look into Internet Marketing including common pitfalls to avoid and how to build a userbase. Part 1 of 2 - How to Get into Internet Marketing.

Bored of sitting on your PC? Need internet on your Nintendo DSI? First check out whether you have WAP/WPA2. You can find out whether you have WAP by going to internet and typing your IP address and going to your wireless settings. If you do have WAP/WPA2 then go to system settings, then to internet. If you have Wi-Fi connector, turn that on. If you have WPA2, then go to advanced settings. This will get your Nintendo DSI get connected to the internet.

Learn everything you could possibly want to know about the internet, multiplayer game Evony. Watch this video tutorial to learn how to hack Evony (09/17/09).

Learn everything you could possibly want to know about the internet, multiplayer game Evony. Watch this video tutorial to learn how to get heroes and troops in Evony.

Learn how to recreate "Pedobear" from 4chan as a custom, multilayer Black Ops playercard emblem! This COD Emblem Editor tutorial presents a complete, step-by-step walkthrough of the drawing process.

Have you ever had a cold sore that just won't seem to go away? In this video, we learn how to get rid of your cold sores for good! Since there is no complete cure for cold sores, you must start with prevention. Eat a healthy diet with lots of nutrients, which will restore your immune system to fight against cold sores before you get them. If you end up still getting one, don't bite it or irritate it. You can use natural remedies or over the counter products to help relieve these and get rid o...

In this video we learn how to alter your IP address. To do this, you will need to go to this website: http://shadysurfing.t35.com. After you go here, you will be directed to the site, click on the left hand side toolbar to display your IP address. Then, go to the web based proxy and search for the site you want to visit. From here, the site will pop up under a different IP address. You can use there at school or at work, whenever you don't want the information for where your IP address has be...

In this video, we learn how to remove Security Tool the simple way. Most ways will not remove this from your computer, but this way will. To start, you will need to restart your computer. After this, press ctrl+alt+del the moment Windows shows up. Then, go to the Task Manager and look through the programs that are open. When your security tool opens, press the same buttons to get the mouse free. Then close the security tool from the Task Manager. Now, go to your desktop and press on the icon ...

To watch HD videos in YouTube in your iPhone 3g you must have Cydia and jailbroken iPhone with 3.0.1 IOS.

Much like Mac OS X's Dashboard, which contains Widgets, Windows 7 has developed their own uniqued version, which they call Gadgets. This quick tip video from Microsoft will help you understand where and what Gadgets are, and how to use them to best suit your needs.

In this tutorial, we learn how to remove advertisements from Mozilla Firefox. First, click on "tools", then "add ons". After this, type in "adblockplus" in the search bar. Now, click "add to Firefox", then download and install this add-on. When finished installing, go to the website where you want images blocked. Once on the site, click on the adblock icon and select "open blockable items". Now, right click and click on "block this item", then "add filter". When you click on this, the images ...

In this video tutorial, viewers learn how to disable ads with the Ad Block Plus add-on in Mozilla Firefox. Begin by going to the Firefox add-on site and search for "ad block". Then click on "Add to Firefox" to install it. Once installed, users will be able to block out any advertisements. Users are able to add a filter subscription. To block an image, right-click on the image and select "Ad Block Image". Users are able to customize their ad block filters to only allow certain advertisements. ...

Forex— what is it? Any investor could tell you a complicated description of what Forex is, but the basics of the FX currency markets is— an over-the-counter financial market for trading currencies. The foreign currency exchange market has no central exchanges like the stock market and little regulatory oversight. With this beginner’s guide, learn the trading basics.

Daemon Tools Lite is a program that helps you install a virtual drive, thereby loading an .iso image into the drive to be used at all times with ease. Download DAEMON Tools Lite by searching on the google. After you download, install the program successfully. This may take some time as the virtual drive needs to be installed. Once installed a small icon appears on the bottom right corner of the screen on the task bar. Right click on the icon and go to ‘virtual CD/DVD ROM’. Select a drive ...

In order to jailbreak and unlock an IPhone 3 G with redsnow v 0.8, you will need to use Windows Vista. When it asks if you are sure you want to run this software, then you should click "run".

This video is about how to install new fonts in Windows XP. The first step that you will need to do is open your web browser then search for fonts. If you have found the site, just simply click on it. Then the next step is have a browse and look for the font you like. Once you have found the font that suits you best, just simply click the button "download" then save the file in your computer. Once you have saved the file in your computer, simply right-click the file and click on the "extract ...

If you have thinning or short hair and are looking for a change, you may want to try a wig. There are many types of wigs today, different styles made up of different materials. Watch this video to find out information on buying a wig or hair piece so that you don't wind up looking like you have an animal on your head.

Privacy is important. Whether its a telemarketer or a crazy ex, sometimes you may need to block someone from contacting you. With this tutorial, learn how to get rid of those pesky callers.

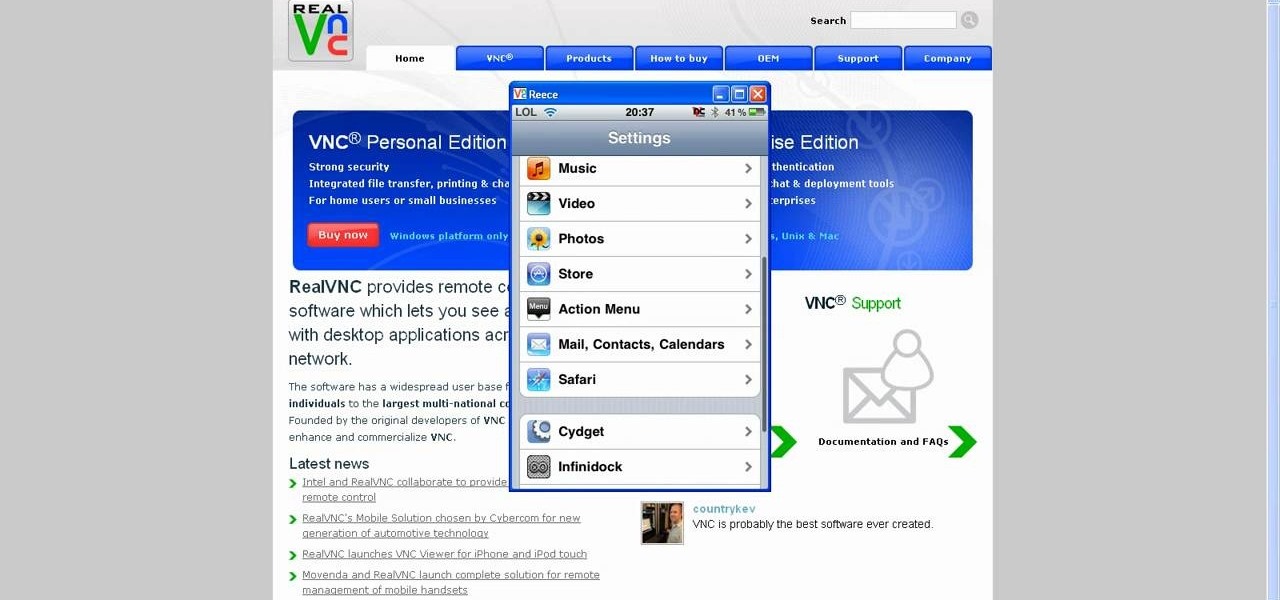
This tutorial will show you how to view your iPod or iPhone screen on your desktop. First of all, you need to have a jailbroken iPod for the applications necessary and secondly you will need Wi-Fi. You will need to download the application RealVNC for your desktop and Cydia for the jailbroken iPod or iPhone. Within Cydia you will search for the program Veency and go to the homepage. From there you will go into settings Veency. Now you have down everything on your iPod or iPhone. Now on your c...

Need to know what kind of oil your car needs? How about your vehicle load capacity? What about the standard maintenance procedures for you specific make and model? All of this and more can be located inside your owner's manual. If you don’t have an owner’s manual for your used car, you may still be able to find one even if your car is an antique.

This video teaches the secrets of downloading and using uTorrent in your computer. First download the software from the link shown in the video and open it. Now to download any file search some popular torrent websites. Make sure you select a torrent file with more SEEDS but less LEECHERS and download it. Now open the downloaded torrent, select the required files if there are many and start downloading. After downloading stop the torrent and use the files.

This is demo showing where to get a cheap origami paper. Origami papers are expensive in terms of shaping. It's very cute and nice. While seeing the holographic picture of the paper we may clarify that. Take a big roll and it is cheap. Take off the protective sheets on the walls. Its cheap and its like 3 -4 $ per piece. Its pretty and wonderful. Also we may get wrapping paper which you can buy. This is cheaper and you can get it home. This is a great paper and you may can fold everything. Whe...

Often artist use, their voice and they are always searching for new and effective methods to improve their singing.

This video shows you how to easily remove the tracking Cookies from your web browser. Normally, if you use AVG Free, it will detect the tracking cookies but not delete them. This video will show you how to manually remove that tracking cookies without using any software. The first thing you have to do is click Start menu, then search for Run. In the Run windows, paste the following: C:\Users\YOUR PC NAME\AppData\Roaming\Microsoft\Windows\Cookies , and hit Ok button. Delete all the files that ...

Computer forensics expert Steve Burgess gives a highly informative tutorial on how to recover deleted emails in Outlook and Eudora. The most critical factor affecting the recoverability of deleted web-based emails, according to Steve, is whether the PST file, which stores all the emails, has been compressed after the mail was deleted. If this hasn't been done it is possible to hack into this file and recover the deleted email. Text-based emails, like those one creates on programs like Eudora,...

This how-to video is about how to use command prompt to view the blocked websites at school. This step by step instruction will help one to open the blocked websites at school.

There's 6 small techniques to improving traffic on your website via web optimization. Improving your SEO (Search Engine Optimization) is the key to getting traffic to your site, especially a small business that needs to compete online. Lincoln explains 6 small business marketing strategies for improving your web traffic and small business SEO. Watch both parts of this video series.

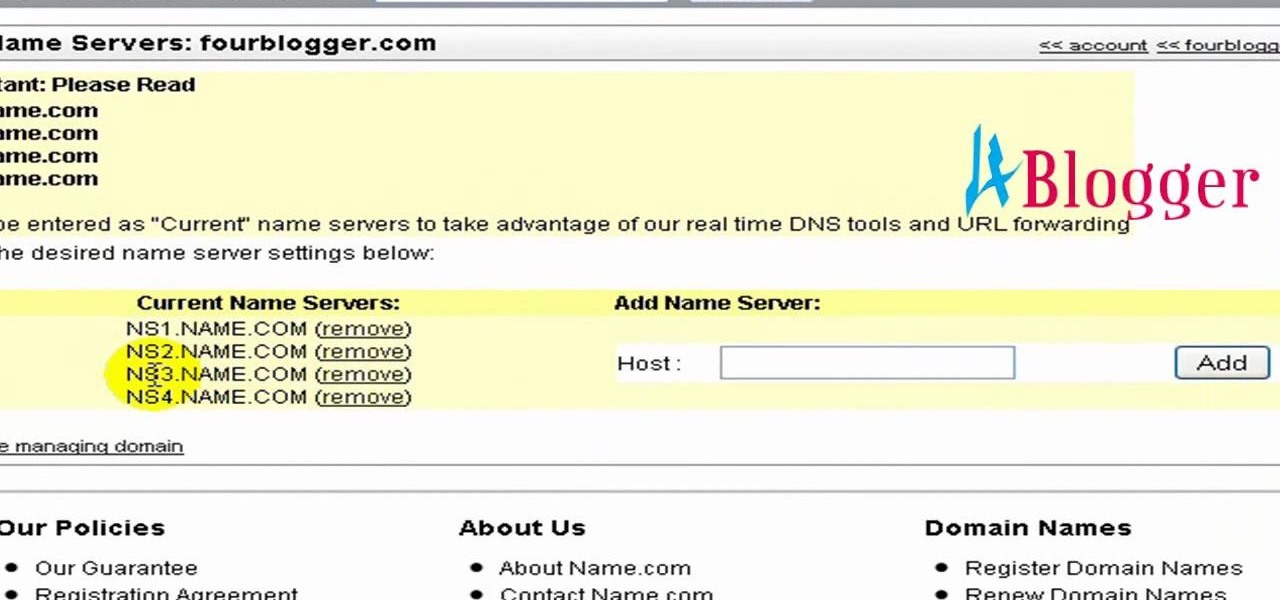
Edit name servers in the domain management area. If you're buying domain and web hosting from a single provider, like Hostgator, then the domain name automatically has a corresponding host.

Change your Snow Leopard dock on Mac OS X with this video tutorial. Go to Leopard Hard drive -> System folder -> Library folder -> CoreServices folder -> Dock App (right click) -> Show package contents -> Contents folder -> Resources folder -> Scroll down until you get to Scurve-1.png, Scruve-m.png, Scurve-sm.png, Scurve-xl.png -> Highlight them all and delete them -> Select the dock you want to change it to -> Paste the files into the place that you deleted the others -> Search for "Terminal...