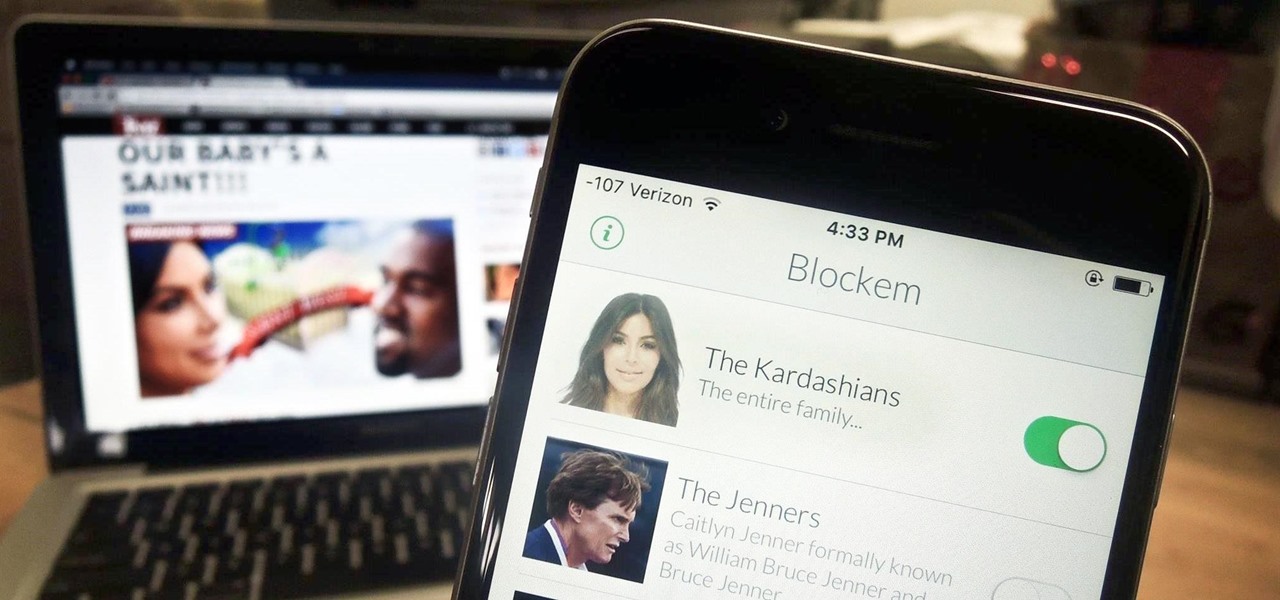
Kim Kardashian and Kanye West have fittingly named their second child "Saint," but I'm sure you don't care about that—and neither do I. Unfortunately, regardless of our pop culture interests, we're forced to know these types of stupid facts because the internet is so densely populated with Kardashian-related content that it's impossible to avoid. It's enough to make you puke.

Many websites are crowded with ads, pictures, and other irrelevant content that make it harder than necessary to read a simple article on your iPhone. In many cases, you have to zoom in just to get a better view of the text you're attempting to read—unless the webpage blocks zooming.

When I started to go to this site I found it fascinating and found myself coming here all day I have used a lot of the info I have gotten from here in my professional career and on my own. I currently am the VP of RND for a small IT company. I have been pushing toward Penetration Testing as a service for our clients and future clients. For the past 10 years here it has been a very long uphill battle and have hit a lot of road blocks. So I decided to work on this on my own of course as soon as...

Hello, my web huggers! In today's tutorial we will learn how to use the Google Hacking Database (GHDB) developed by Exploit Database, to find vulnerable web servers and "juicy" information.

This tutorial is for those who've purchased an account with Private Internet Access to hide your VPN and would like to set it up in Kali. Please note, you can chose to run your PIA service from your Windows computer without configuring it in linux as long as you'll be using a NAT connection. Using a NAT connection will allow your Windows machine and Kali Virtual Machine to use the same IP address, hence if your IP is hidden on one, it will be hidden on the other.

When I tried to set up an eviltwin for a MitM-constelation in kali 2.0, I couldn't provide internet to the victim. The origin was the brctl bridging. I have read many tutorials but all of them where explained in backtrack and older versions of kali. So i was searching for a solution without using brctl and this solution will be explained now. This will just work on unencrypted wireless-environments.

Welcome back, my novice hackers! Previously in my "Spy on Anyone" series, we used our hacking skills to turn a target's computer system into a bug to record conversations and found and downloaded confidential documents on someone's computer. In this tutorial, I will show you how to spy on somebody's Internet traffic.

Weeks before the music video for Nicki Minaj's Sir Mix-a-Lot-sampled single “Anaconda” dropped, an internet frenzy was sparked thanks to the help of an extremely racy cover image, several promo pictures with her "dancing" with label-mate Drake, and a teaser clip that showed Nicki twerking that hypnotizing booty.

Welcome back, my greenhorn hackers! In previous Wi-Fi hacking tutorials, I have shown you ways to create an Evil Twin, to DoS a wireless AP, and to crack WEP and WPA2 passwords, but in this tutorial, I will show you something a little bit different.

Welcome back, my tenderfoot hackers! As you know, DNS, or Domain Name System, is critical to the operation of the Internet. It provides us with the ability to type in domain names such as www.wonderhowto.com rather than the IP address. This simple service saves us from having to memorize thousands of our favorite website IP addresses. Instead, we simply type in a domain name to retrieve the website.

Anytime you surf the web on your iPad or iPhone, Safari saves which webpages you visit, the information you enter into them, and other types of data. This not only make your internet experience quicker, but it'll also keep track of everything you're doing.

Canvas fingerprinting is the web's trickiest privacy threat, but it's not impossible to stop. With all the media attention it's gotten lately, it's time we lay out exactly how to detect and prevent this invasive tracking technique.

Unless you've been living under a rock with no internet connection, it's safe to say that you've heard of the Heartbleed flaw that allows practically anyone with the right knowledge to steal your personal information, such as passwords, credit card numbers, and e-mail addresses using OpenSSL.

Welcome back, my greenhorn hackers! Although we have focused primarily on technical hacks here, social engineering can sometimes be especially effective. This one requires a bit of technical skill, but not too much. In addition, it's limited by how specific a target you can choose—but it will work.

With the development kit fully open, the functionality of our Chromecasts seem to expand with each passing day. From a portable gaming system to your own personalized news station, our little gadgets have a lot going for them.

Thanks to the popularity of casual gaming on smartphones, handheld gaming consoles like Sony's PlayStation Vita have been on the decline. But if you own a new PlayStation 4, the Vita is a nice thing to have, since you can easily connect it to your PS4 for Remote Play.

If you're like seventy percent of America and find it hard to focus on just one thing at a time, the Xbox One had you in mind. If you ever thought that being able to watch The Walking Dead while playing The Walking Dead video game would be awesome, you're in luck. How about looking up cheat codes on Internet Explorer without ever leaving the game? Easy as pie.

With more people joining the internet scene each day it's important that it's security is.. well it has to be good. Of course everything can be hacked and that's the way hackers work. They know there IS a vulnerability but they don't don't know the rest. in this article i'll try to explain the big difference between HTTP and HTTPS

I read a ton of articles online and I am always looking for a way to make the experience a little better. Reading long articles can be tiresome, and if an article has multiple pages, I will most likely skip it. With the ability to endlessly scroll, no site should have multiple pages. It's just a sneaky way to get more page views, IMHO.

UPS offers a four-step guide to prepare packages for shipping. These instructions include shipping advice on packaging materials and proper labeling that can help items arrive safely and on time. And when you are ready to ship, UPS Internet Shipping guides you through the required address fields. Packaging solutions made easy. That’s logistics.

The internet is a great place to find information for pretty much anything you can think of. So why shouldn't it be a place for official higher learning? I'm not talking about a course in Wikipedia or SparkNotes, but real colleges offering real college courses completely online. And guess what—it's FREE.

For the most part, nobody makes money off of Facebook. Sure, some people make a living by updating pages for businesses and celebrities, but hardly anyone gets a dime from the site itself.

Social media is where we post our thoughts for the world to see, but sometimes a little more exclusivity is needed. And that's where Scrambls comes in.

Even though it seems like forever, the phenomenon of "rickrolling" has only been around since 2007. It was started as an inside joke by a 19-year-old who just wanted to troll his buddies, but ended up becoming one of the Internet's most popular memes with over 66 million views (as of this writing).

Growing up, my family would get together in the living room every Saturday night and gather around my mom's old boombox radio and listen to Disco Saturday Night on 104.3 FM from 6 p.m. to 2 a.m. (the show ended in 2008 after 14 years of consecutive shows). The old ladies in the picture below are the best representation of these nights that I could find. Now, the radio is all but dead (just like the old ladies above) in this world of music streaming services and torrenting. All of our music is...

Steampunk music is an oft-debated genre, full of bands playing all sorts of different sounds. While this can make it difficult to generalize about the genre as a whole, it means that the average person is bound to like at least some Steampunk bands. That's why it's a great idea to support some independent Steampunk bands this holiday season by buying their music for yourself, or sharing it with someone else.

Android devices are known for their USB and Wi-Fi tethering abilities—rooted or unrooted—which comes in handy for those that travel and need internet on their laptops in areas that don't have any Wi-Fi networks available, but have a strong cellular signal.

The big question this week would be the controversial Obamacare mandate. And heres the answer: Yes. Obamacare passes Congress' filters and is now an official OK. Texas college hacks drone in front of DHS — RT.

Alright guys sorry for the delay, lets just get to it: » Pelosi Says Holder Contempt Charge About Suppressing Vote.

You love your bike and it was stolen. Although, this is not a good scenario, you still may be able to retrieve it. Sketch the serial number or means of identification into the bike and then when it is stolen you can really get the word out to all the places that it might turn up.

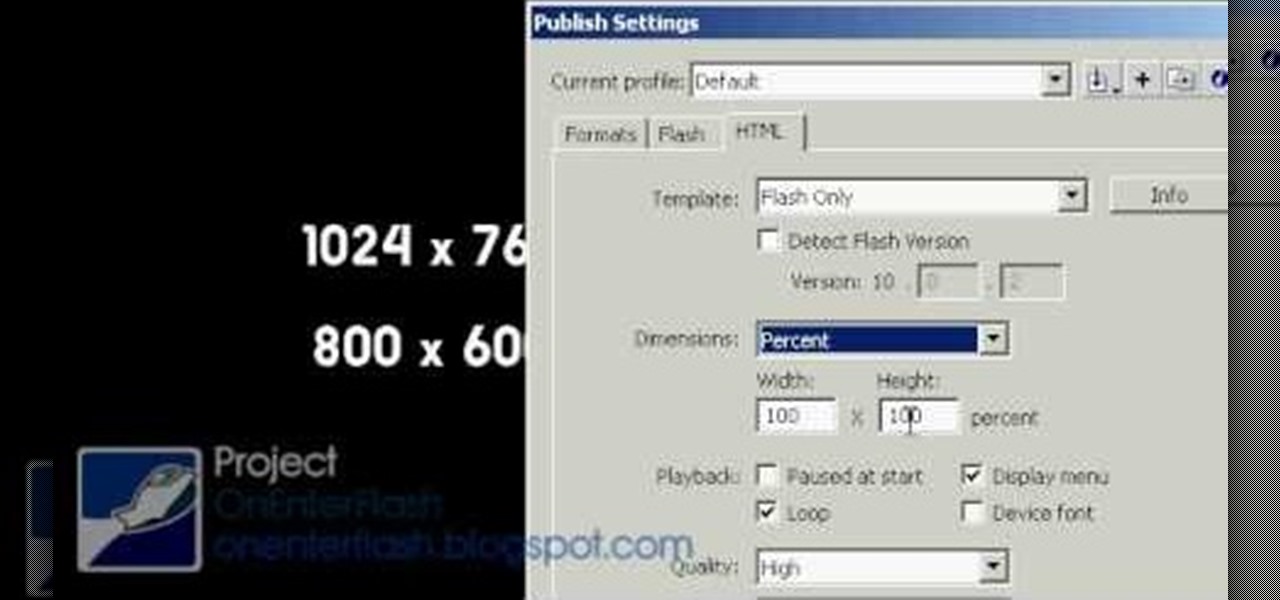
Creating a website from scratch is one of the most productive and most challenging things that you can do on a computer, whether the site promotes your own services and interests or you're being paid to make it for someone else. This nine-part video will walk you through the entire process of making a website using Flash CS4. It is very complete, and if you have the patience to watch all nine parts you should be well on your way to creating a really cool, high-traffic site.

There are several different ways to go about stretching your shoes. This method uses water, a ziplock bag, and a freezer. Michelle Phan demonstrates how:

Check out this informative video tutorial from Apple on how to add a blog to your website in iWeb '09.

Check out this informative video tutorial from Apple on how to add a photo album in iWeb '09.

Check out this informative video tutorial from Apple on how to add a movie to your website in iWeb '09.

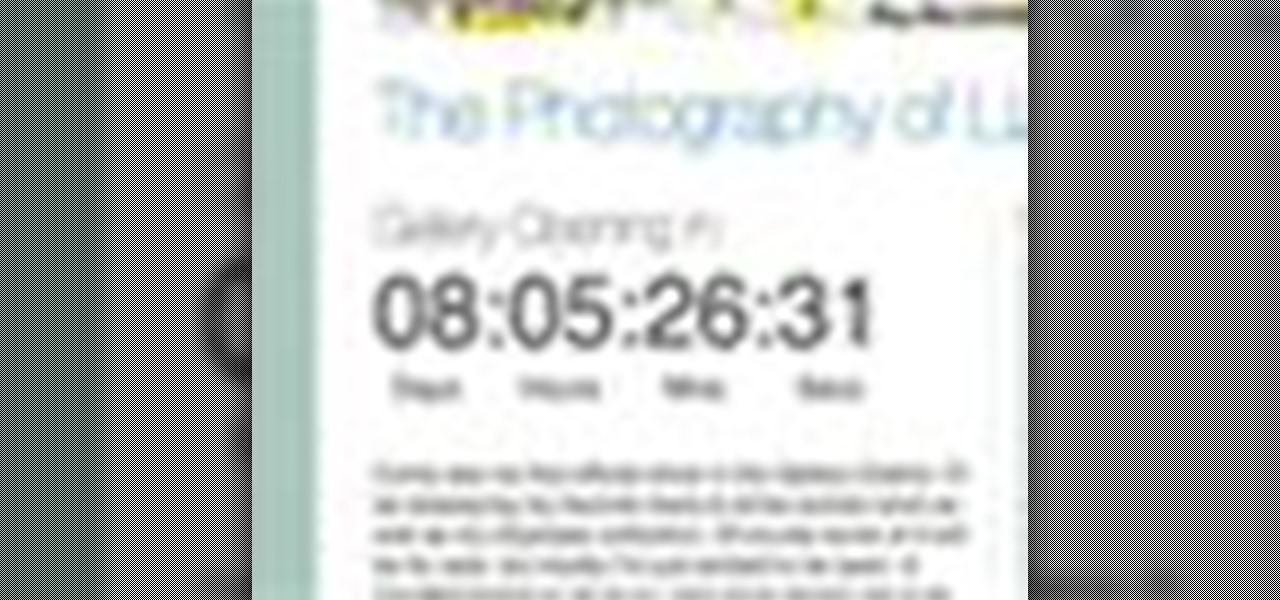
Check out this informative video tutorial from Apple on how to add a countdown clock in iWeb '09.

Grand Illusions is a site for the enquiring mind. This how to video demonstrates how to make Folded Page Art. Your wonderful & charming host represents Grand Illusions, an amazing toy, magic & illusion web shop and gallery.

Give your website a truly professional look by designing your own favicon. Your favicon will appear in the address bar and when your site is bookmared. Using a simple software like MS Paint and following the instructions of this video for editing HTML, you can make your custom favicon appear.

Visit this site and download all of the necessary files, then check out this videos helpful instructions for install the More Creeps and Weirdos mod to Minecraft. Your modded Minecraft world will have more Creeps and Weirdos in it than you'll know what to do with.

Mods can let you change around the way your game looks, and you can download quite a lot of mods for free off Minecraft fan sites. This tutorial shows you where to find the best ones and how to download and install them.