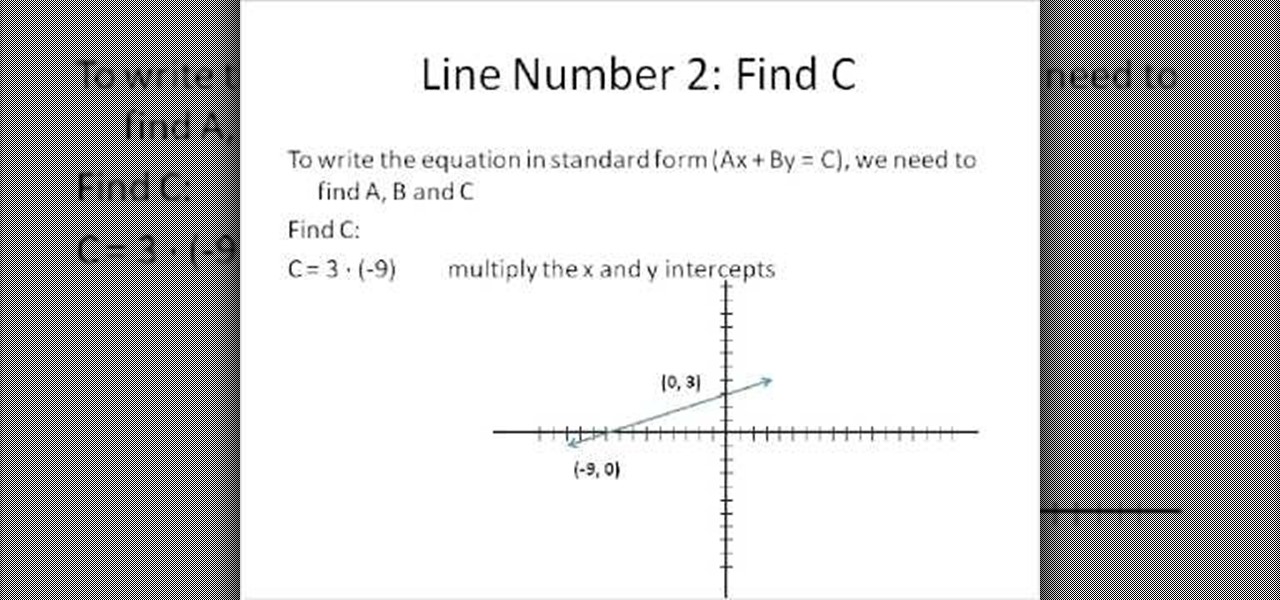
Looking for a primer on how to solve a standard-form linear equation in algebra? Learn how with this free video lesson, which offers examples of how to use the x and y intercepts of a line to write the equation of the line in standard form. From Ramanujan to calculus co-creator Gottfried Leibniz, many of the world's best and brightest mathematical minds have belonged to autodidacts. And, thanks to the Internet, it's easier than ever to follow in their footsteps (or just finish your homework o...

Windows Movie Maker is the PC's answer to iMovie. It is a user friendly, relatively easy way to create and edit movies.
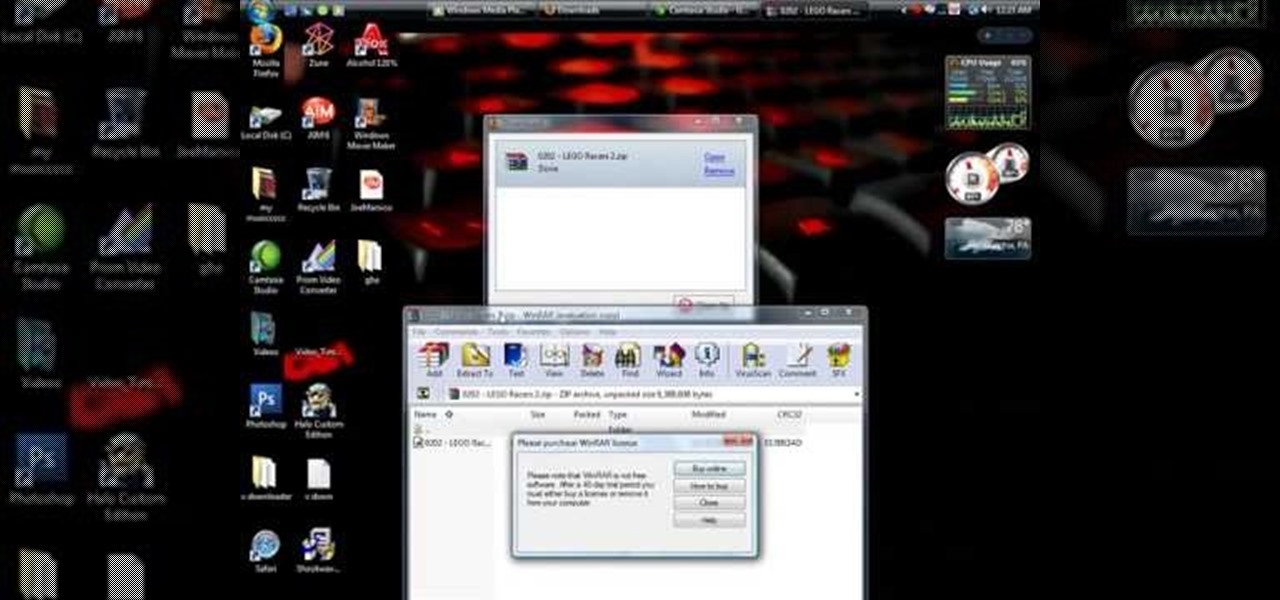
This video tutorial from shrederjoe shows how to easily extract .rar file's content using WinRar application.

In this Home & Garden video tutorial you will learn how to make an accurate boomerang. Material required are 4-6mm thick ply wood or hard board or paper-mache, saw and some spray paint. Search for and download boomerang plans from the internet. The boomerang has three protrusions or handles equally spaced with each protrusion being 14cm long and the diameter of the circle at their ends being 4.5cm. Trace the plan on the plywood and cut it out with a ‘U’ shaped saw. Next draw out the line for ...

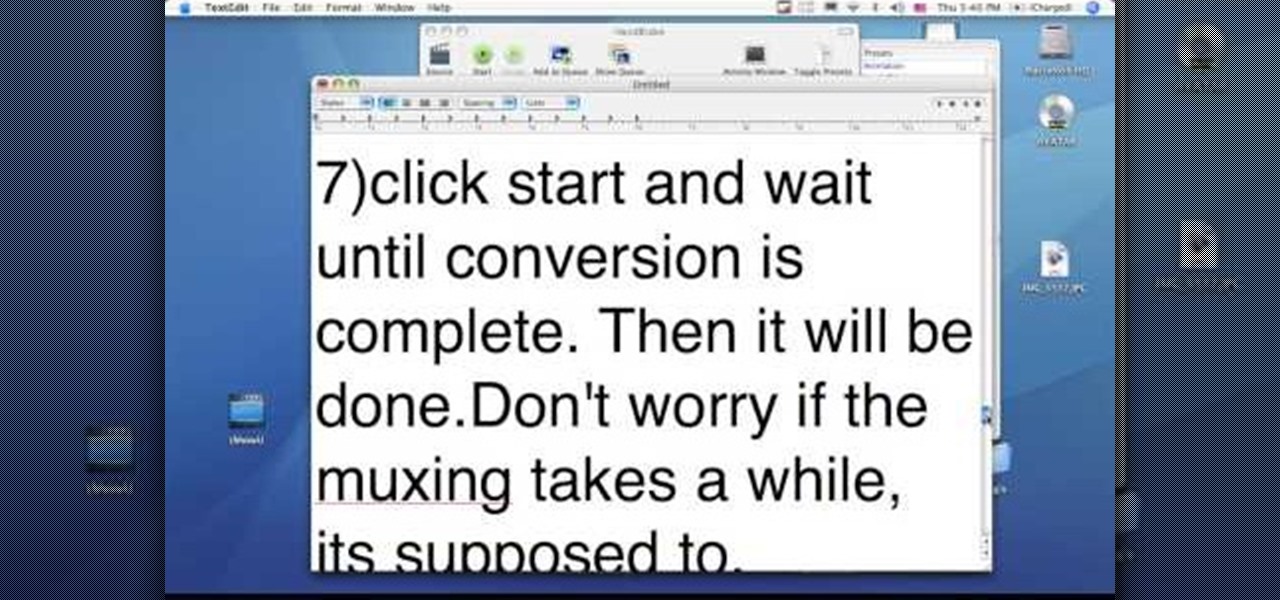
In this video tutorial, viewers learn how to convert .docx file format to a .doc file. Begin by downloading and saving the file to your desktop. Then open your internet browser and go to this link: Zamzar/]. In Step 1, click on Browse and locate the file that you want to convert. In Step 2, select .doc as the format that you want to convert the file to. In Step 3, type in your email address. In Step 4, click on Convert and wait for it to upload. Now open your email to find the sent converted ...

This video illustrates the method to Set up a Remote Desktop connection on a Windows PC. This process is composed of the following steps: Step 1Install "TeamViwer" software on the PC's which would be involved in this process.Step 2Create a connection between the computer you want to access remotely and the one which would be used to gain remote access. To create a connection , you need to connect them through Wi-Fi, LAN or through the internet.Step 3Open the TeamViewer software from the compu...

Disk space is a valuable commodity on your PC, and if you're running low, it's time to sell some of that unneeded property! This video shows you the steps to freeing up space on the hard drive of your Windows XP or Vista computer. There are many areas in Windows from which you can delete temporary files and hence, decrease your overall disk usage.

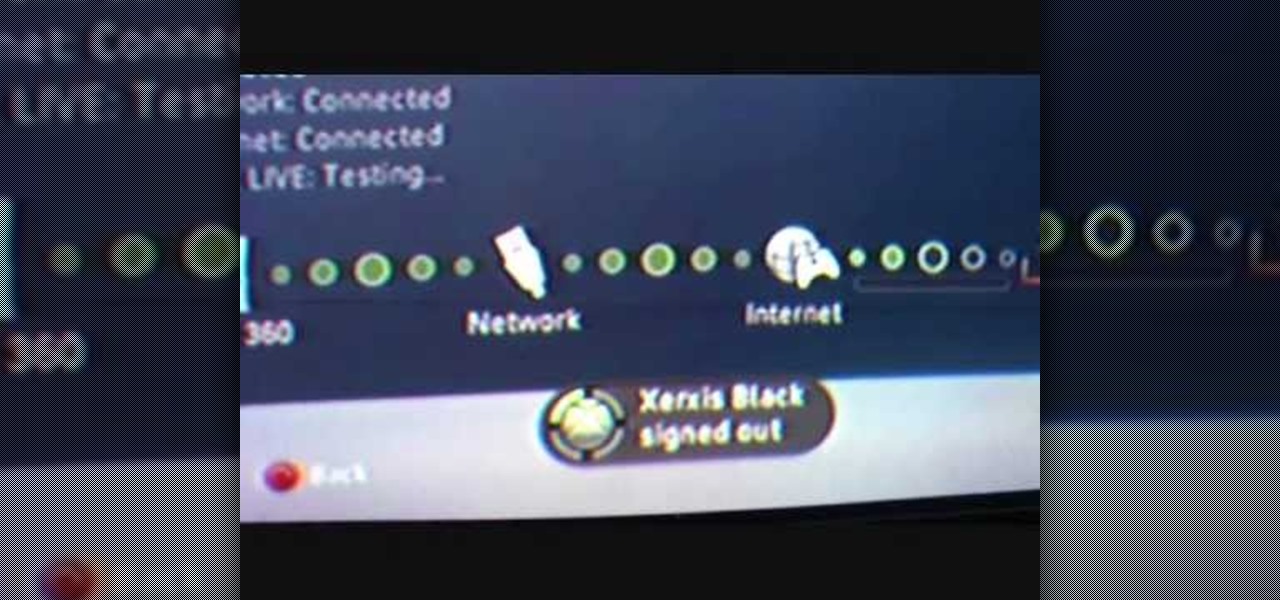
In this video tutorial, viewers learn how to share a wireless connection with a Xbox360. Begin by click on the Start menu and select Control Panel. Click on Network and Sharing Center. Under Tasks, click on Manage Network connections and disable the wireless connection. Right-click on it and select Properties. Go to the Sharing tab and check both boxes. Now enable the wireless connection and then go on your router website to find out the primary and secondary DNS. Now input both DNS numbers a...

First you need the pre-downloaded game you want to burn. It will be in a ".XBE" file.You must have "Quix" downloaded off the internet. If you do a search for it via Google it will come up and you need to go through the download process.This will change it into a "ISO" that you can burn.Then go to Google and you need to find an "ISO" that fits your computer.Then you must run the "ISO" file through the "Quix" system that you downloaded. Now insert your Blank disc and burn the "ISO" onto the dis...

This video tutorial from dproxisback presents how to download and install Handbrake DVD ripping tool.To avoid installation problems, carefully choose application version for each type of computer and operating system.Open your internet browser and visit http://handbrake.fr/?article=download web page.Choose correct version for your type of operating system (MacOS, Linux, Windows).Download and install the application. Run Handbrake once it's installed.Click File-Select Source. Browse for your f...

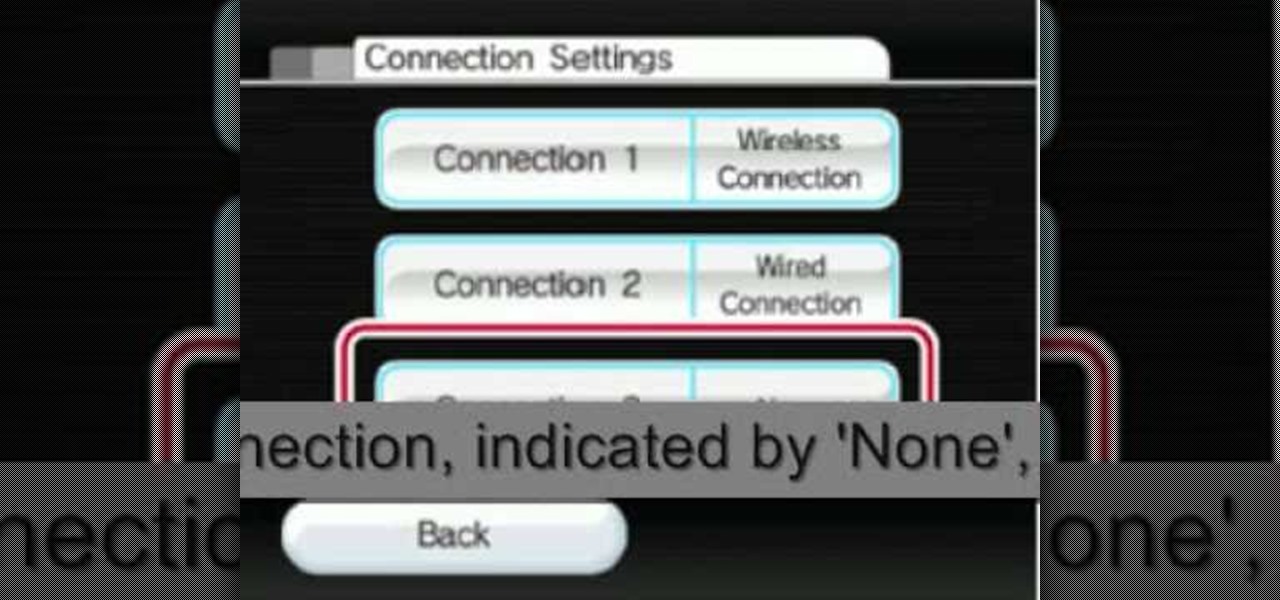
The video shows you how to connect the Nintendo Wii to an available wireless network. First, you have to turn the Wii on. When the menu screen appears, you then click on the "Wii button" in the bottom-left corner. Next, go to "Wii Settings". On the following screen, you have to use the blue arrow on the right to go to the second page of options and select "Internet". Go to "Connection Settings" and click on an "Open Connection". From here, go to "Select Wireless Connection" and then "Search f...

First, on your computer access your command prompt and type in ipconfig. Find the line called default gateway and write it down for later. Type your default gateway into your internet address bar and it will bring up your router setup page. Find your upnp and enable it, this will open your NAT. Start your XBox 360 and go to system settings on your XBox dashboard, go down to network settings and test your connection. Next go to IP settings then manual then IP settings. You want to change your ...

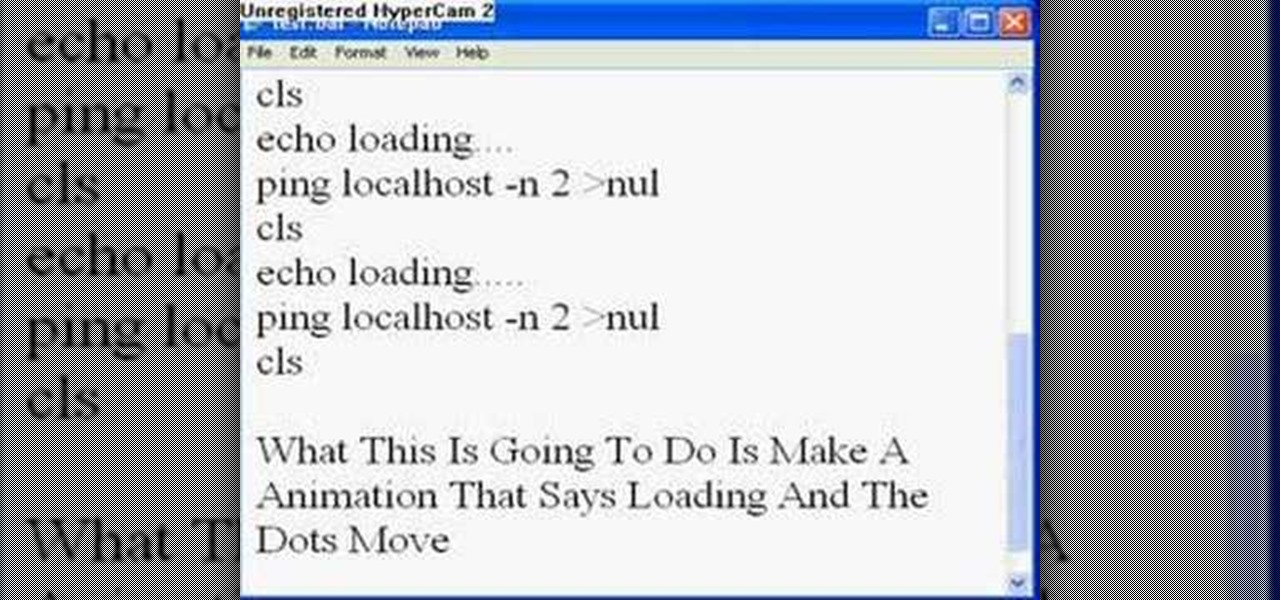
CtrlFormula teaches you how to make an animation with a batch file. Before you begin you must know that sending batch files over the internet is risky, so keep that in mind. You create a new .txt file and type in: @echo off. Hit Enter twice and type in: echo loading. Then hit Enter once and type: ping localhost -n 2 >null. Hit Enter once and type in: cls. Copy and paste this structure three times. For each loading you see you have to add another dot at the end, so the animation will slowly go...

You start the game from the Kongregate website and then run Cheat Engine. Look for your browser in the Process list. It could be Firefox, Chrome or Internet Explorer. Set the value type to Array of bytes. Then check the Hex box above and use the values from the description to apply the effects there, like no mp drain, chain doesn't end on hit and unlimited chain time. After you've searched for the value, click New scan and then add it from the left to the bottom by double clicking it. To acti...

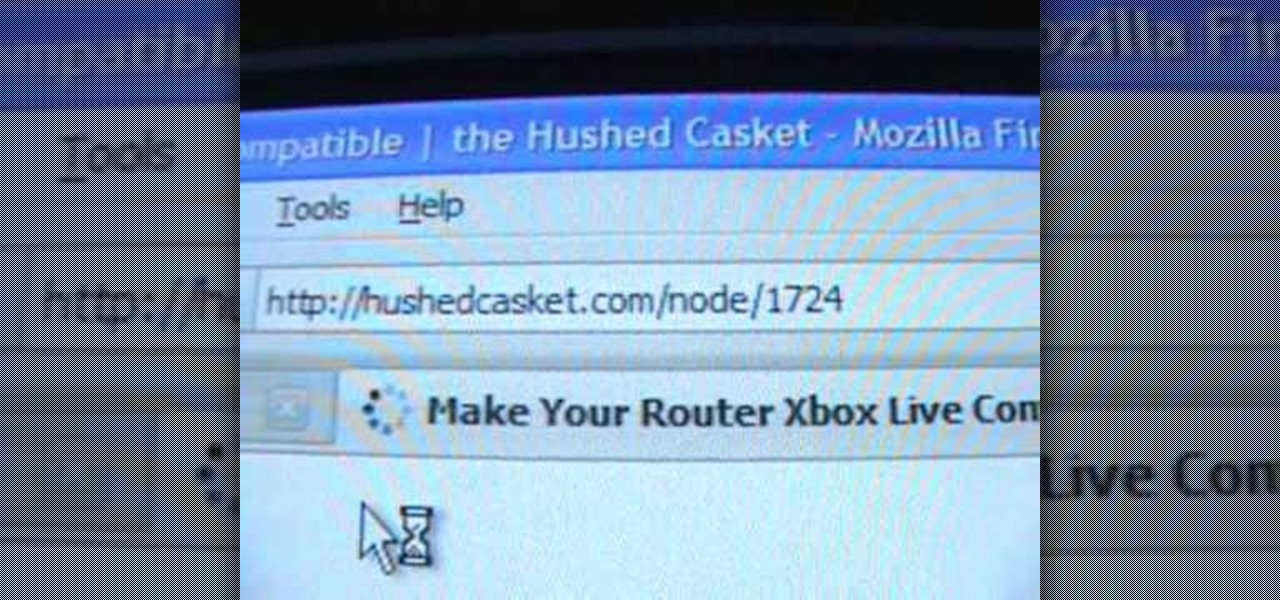
Open your internet browser, type in the address bar 192.168.1.1 and enter your user name and password to access. Look in the right and search for Port Forwarding / Port Triggering. Click on Add Custom Service. Type a name to the service, like XBox Live, now access HushedCasket and scroll down to see the ports you need to open. Go back to the setting and select UDP in Service Type. Put 88 in Starting Port and Ending Port. Go to your XBox and enter in System Settings, go down to Network Setting...

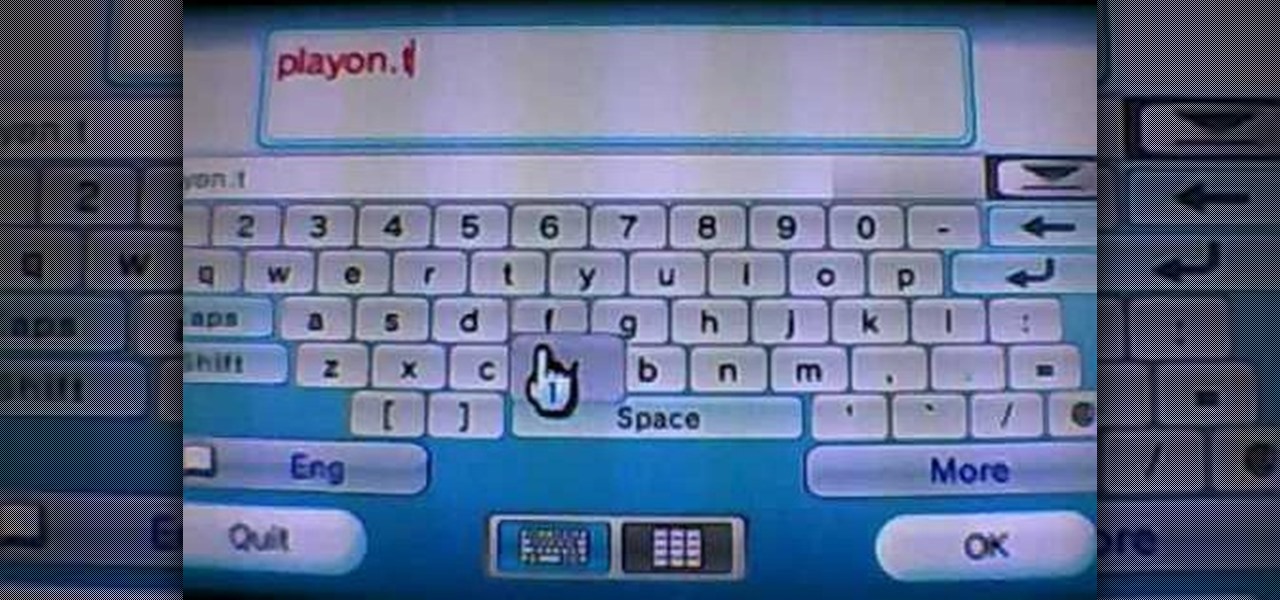
Evan shows viewers how you can use the PlayOn option on your Wii to watch videos on Netflix or Hulu. He starts off by showing how you can set up your wireless network and your connection settings. You will need to do this first if you have never done this before. To get PlayOn you will have to purchase it from the Wii Store using Wii Points. Evan also shows how you can link your internet channel to PlayOn so that you can view videos in just seconds. Watch all his tips and techniques and you c...

Here is the answer to the question that a lot of people have asked lately, "How does one install Linux Ubuntu on Windows without causing any modifications in the original boot record of the PC?" Software wiz-kid Matt Hartley walks the viewer through a step-by-step process of installing Ubuntu on a Windows-driven computer. The secret is to download Ubuntu to a CD instead of downloading and installing it directly on the hard drive of one's PC. This also ensures that the Ubuntu is easy to delete...

How to send text messages from your using Trillian, just follow the some few steps. First step is use Internet Explorer download the Trillian.

Learn how to remove viruses with spybot search and destroy. * First you need to download the 'spybot search and destroy' software.

Loose your birth certificate? Or, need to get a copy of someone else's, like your daughter or son? Don't fear. In this how-to video learn the steps needed to be taken in order to obtain an additional or duplicate copy of your birth certificate. Before you get started you will need basic information on the person and Internet or library access. Good luck!

Chumby is the dream toy of hackers and tinkerers everywhere. Made up of a few simple parts, Chumby takes your favorite parts of the Internet and streams it so that you'll always have access to your favorite podcasts, music, photos, games and more. What's great is that you can put together the Chumby yourself. In this video MAKE shows us how to put the Chumby guts kit together. Be sure to make sure you have all the required parts.

Take a look at this video if you've ever been curious on how people send video messages via the iPhone.

Learn everything you could possibly want to know about the internet, multiplayer game Evony. Watch this video tutorial to learn how to get honor medals in Evony. This is just a honor medal guide.

Learn everything you could possibly want to know about the internet, multiplayer game Evony. Watch this video tutorial to learn how to get medals fast on Evony (09/25/09). Swamps are NOT the best place to attack if you want medals. A level 2 would be the best.

Got video files on your computer? Watch them on your big-screen TV – using your Xbox! You Will Need

You have a webcam, right? Nowadays, who doesn't? But just because you all have webcams doesn't mean you're using them the same way. And a great way to take full advantage of your peripheral or built-in webcam is by turning it into a security camera. This video will show you how to turn it into a security cam by accessing the video feed remotely over the internet. And it's a really simple solution—you just need to sign up for a USTREAM account, which allows you to stream webcam footage live!

Wordpress is one of the world's most-loved content management systems (CMS). The user-friendly interface and ease of use have made this open-source system a no-brainer for millions of people. Over one-quarter of the top 10 million websites on the planet use Wordpress.

The Pi-hole project is a popular DNS-level ad blocker, but it can be much more than that. Its DNS-level filtering can also be used as a firewall of sorts to prevent malicious websites from resolving, as well as to keep privacy-killing trackers such as Google Analytics from ever loading in the browser. Let's take a look at setting a Pi-hole up and customizing a blacklist to suit your needs.

Apple's iOS 13 for iPhone includes new features in Safari that make browsing the web a little bit better when compared to iOS 12. Some changes are small while others add functionality that just wasn't there before. Plus, there are more security enhancements.

Phishing is the easiest way to get your password stolen, as it only takes one mistake to log in to the wrong website. A convincing phishing site is key to a successful attempt, and tools to create them have become intuitive and more sophisticated. SocialFish allows a hacker to create a persuasive phishing page for nearly any website, offering a web interface with an Android app for remote control.

When researching a person using open source intelligence, the goal is to find clues that tie information about a target into a bigger picture. Screen names are perfect for this because they are unique and link data together, as people often reuse them in accounts across the internet. With Sherlock, we can instantly hunt down social media accounts created with a unique screen name on many online platforms simultaneously.

Stumbling upon a specifically tailored advertisement on your iPhone can be a bit disconcerting. But that's what happens when you let advertisers track your data. Some of you may appreciate more relevant ads in apps, but the rest of you might consider it a straight-up privacy invasion.

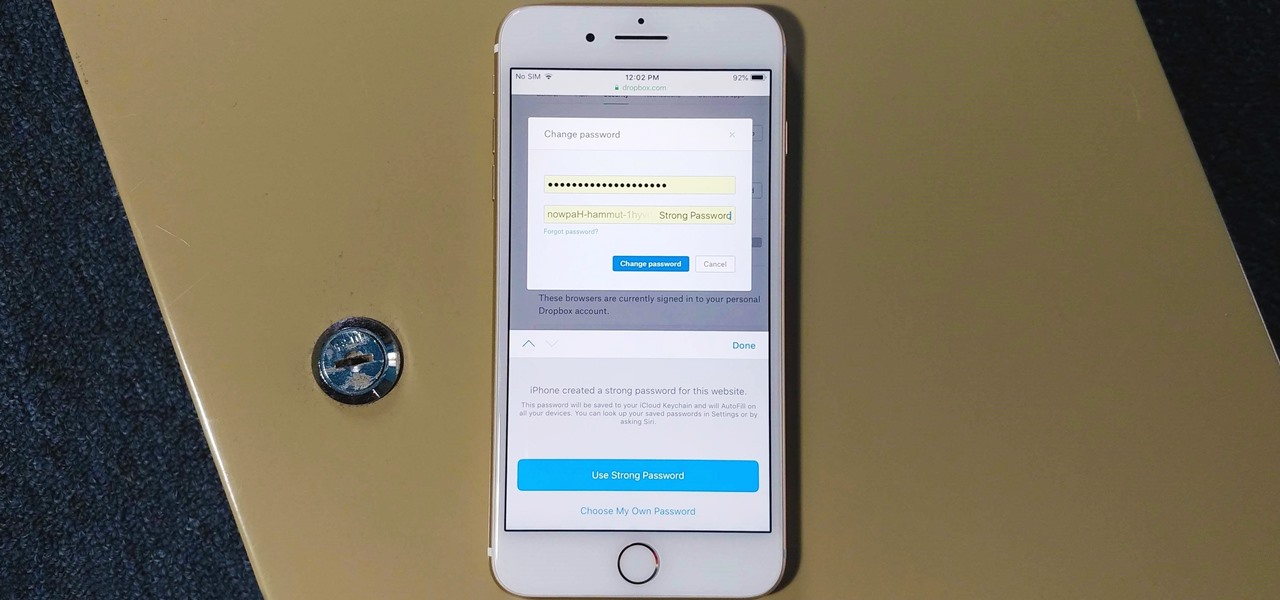
The option to auto-fill passwords on your iPhone has been around a while now, but iOS 12 improves on it by suggesting strong passwords when first creating an account online in Safari or within apps. Apple has also added "password reuse auditing" for your iCloud Keychain, where all your logins are housed, which will find and change your weak passwords to strong ones.

Unlike many browsers, Firefox gives a lot of control to the user. By default, Firefox does a great job of balancing security and performance. However, within the app's settings, you can modify options to shift this balance in one direction or another. For those looking to shift it toward security, here are few suggestions.

While there aren't as many ways to customize your iPhone like there is on Android, there are still a lot of apps out there that can help streamline and enhance your experience beyond Apple's own default options — and we've hand-picked over 100 essentials.

Configuring onion services for the first time can be tricky. A surprising number of system administrators make seemingly trivial mistakes that ultimately lead to catastrophic cases of de-anonymizing supposedly anonymous sites on the dark web. OnionScan is a tool designed to identify common misconfigurations in onion services and aid us in understanding how to fix them.

Any internet user will need to download files eventually, and most simply have faith that what they are downloading is trustworthy. This doesn't give much clarity into the contents of the file, but if the file's author published the original checksum, comparing it to the SHA-256 hash of the downloaded file can ensure nothing was tampered with.

Facebook is testing a new feature in India. One that could help you protect your profile photos from being used on sites without your permission.

Download a popular, legit app from the Google Play Store. Decompile it. Add malicious code. Repackage the app. Distribute the now trojan-ized app through third-party Android app sites. This is how advertising malware Ewind, what Palo Alto Networks calls "adware in applications' clothing," infects Android users.

Android has several features built into the platform that improve user experience but require extra attention to prevent a security breach. By modifying these settings, you can drastically reduce the possibility of someone exploiting your device or intercepting information.