In this video tutorial, viewers learn how to clear their cache in Internet Explorer. Begin by opening the web browser. Then click on Tools from the top menu and select Internet Options. In the General tab under Browsing History, click on Delete. When the Delete Browsing History window opens, click on Delete Cookies and click OK. To automatically clear cookies, click on Settings under Browsing History and check Every time I visit the web page. Then finish by clicking OK. This video will benefi...

Learn a little bit about technology with help from EMBARQ. Watch this how-to video tutorial on installing your EMBARQ 660 Modem. This will cover exactly how to install your EMBARQ Modem for EMBARQ High Speed Internet service. This is the complete process step-by-step from box to connected online.

Learn a little bit about technology with help from EMBARQ. Watch this how-to video tutorial on installing DSL 2Wire Gateway filters on home phones. Make sure to repeat the install process for the Gateway filters for each telephone in your house that uses the same phone number as your High-Speed Internet.

Wireless can be a pain sometimes with video games on the Internet, with disconnections and signal losses, but why not revert back to a wired connection? This video will explain how to connect your Nintendo Wii to a wired network using Actiontec Powerline Networking technology. This will enable your Nintendo Wii to connect to the Internet to download games, console updates, and other information.

Have you always wanted to make a prank call but never had the guts to do it? Well, now you can because there's the Internet. In order to make a cool prank call without getting caught, first you have to choose a voice. The best one to choose is Arnold Schwarzenegger. To get his voice, go to Google and search for Arnold soundboard.

This tutorial illustrates how a wireless pinhole spy video camera can jam wireless internet or WiFi signals.

A basic introduction to Registry Editing. Learn how to hack Internet Explorer's text.

Did you know that you can improve the Wi-Fi in your home without the stress of changing providers or using a costly professional? The answer lies in a simple app you can use yourself at home, and right now, the NetSpot Home Wi-Fi Analyzer With Lifetime Upgrades is on sale for just $39.99. That's 41% off the regular price of $68.

For all the benefits 5G brings to cellular data, it isn't without weaknesses, the biggest being privacy. Yes, the latest standard comes with breakneck downloads speeds up to 4.3 Gbps, but at what cost? Like with all things on the internet, 5G devices open opportunities for both good and bad actors.

Data is king. Nearly every carrier and MVNO offers unlimited talk and text with their cellular plans. Where they differ is the amount of data available, so that's the part that can save or cost you the most money.

So far, iOS 13.4 hasn't been a disappointment. From new Memoji stickers, a refreshed Mail toolbar, and even the beginnings of controlling your car with your iPhone, Apple's latest iOS update is looking like a good one. That's why we're excited that Apple just released the third 13.4 developer beta today, one week after the release of the second one.

Nearly every connection to the internet is dependent on the Domain Name System. DNS, as it's more commonly called, translates domain names like gadgethacks.com into IP addresses, which is what network devices use to route data. The problem with DNS servers is that they don't have your privacy in mind.

When researching a person using open source intelligence, the goal is to find clues that tie information about a target into a bigger picture. Screen names are perfect for this because they are unique and link data together, as people often reuse them in accounts across the internet. With Sherlock, we can instantly hunt down social media accounts created with a unique screen name on many online platforms simultaneously.

Firewall solutions for macOS aren't impervious to attacks. By taking advantage of web browser dependencies already whitelisted by the firewall, an attacker can exfiltrate data or remotely control a MacBook, iMac, Mac mini, or another computer running macOS (previously known as Mac OS X).

If you find yourself with a roommate hogging limited data bandwidth with video games or discover a neighbor has invited themselves into your Wi-Fi network, you can easily take back control of your internet access. Evil Limiter does this by letting you control the bit rate of any device on the same network as you, allowing you to slow or even stop data transfer speeds for them completely.

Silence spreads over these mountains like nothing I've ever felt. If I didn't have Moby blasting in my earphones, there'd probably be no other sounds around. Well, except for someone, Phil probably, murmuring in a nearby tent just low enough to make his words indiscernible.

If you use the internet regularly, it's nearly impossible to avoid memes. They are the epitome of internet culture, demonstrating how jokes can spread and change like wildfire. While there are many different types, the most common ones you'll come across are images and GIFs with humorous text accompanying them, and we've found the best iOS apps to help you create your own.

While Wi-Fi networks can be set up by smart IT people, that doesn't mean the users of the system are similarly tech-savvy. We'll demonstrate how an evil twin attack can steal Wi-Fi passwords by kicking a user off their trusted network while creating a nearly identical fake one. This forces the victim to connect to the fake network and supply the Wi-Fi password to regain internet access.

Most of us have never put much thought into this, but the question needs to be asked — what exactly happens to all of our online accounts when we die? No, the internet won't just know and delete accounts for you, so you need to plan for life's one guarantee. Because without a plan, things become a lot harder to sort out.

While there aren't as many ways to customize your iPhone like there is on Android, there are still a lot of apps out there that can help streamline and enhance your experience beyond Apple's own default options — and we've hand-picked over 100 essentials.

The public leaks of NSA tools and information have led to the release of previously secret zero-day exploits such as EternalBlue, which was used in the notorious WannaCry ransomware attack. Despite multiple patches being released, many users have failed to update their systems, so many devices are still vulnerable to these now-public attacks.

The Watch Dogs video game series came out in 2014, enamoring audiences with the idea of a seemingly magical smartphone that could change traffic signals, hack web cameras, and even remotely control forklifts. This may sound like science fiction, but The Sonic uses a customized flavor of Kali Linux to allow you to unleash the power of Kali from any smartphone — all without the need to create a hotspot to control it.

The dark web is an intimidating place for a newbie hacker, but it's a powerful tool once you've learned to navigate it safely. To help you out with that, this guide will cover some need-to-know information for traversing the dark corners of the internet while keeping your identity and data safe. (Hint: Using Tor is not enough.)

If imitation truly is the sincerest form of flattery, then Snapchat must be blushing profusely as Instagram continues to shamelessly copy its features and dig into its wallet. Instagram has also managed to copy some of the security aspects — or lack thereof — of one of Snapchat's hottest characteristics.

"It just ticked me off," he said. In March 2011, Neil Singh paid $50 to back the Hanfree iPad stand on Kickstarter. The project was funded at $35,000, but production stalled, and the delivery estimates kept getting pushed back.

Welcome back, my fledgling hackers! Hacking has a long and storied history in the U.S. and around the world. It did not begin yesterday, or even at the advent of the 21st century, but rather dates back at least 40 years. Of course, once the internet migrated to commercial use in the 1990s, hacking went into hyperdrive.

Google has a lesser-known Android app called Device Assist that might just be one of the most useful programs the company has ever published. It offers interactive guides and general tech support for Android, plus it can diagnose your device and help you fix any issues it finds.

So, you want to perform an exploit on a victim, but you're not on the same network as their machine. In this tutorial, I'll be showing you how to set up a meterpreter reverse_tcp attack to work over the internet.

In the recent hit movie Furious 7, the storyline revolves around the acquisition of a hacking system known as "God's Eye" that is capable of finding and tracking anyone in real time. Both the U.S. spy agencies and an adversarial spy agency (it's not clear who the adversary is, but the location is "beyond the Caucasus mountains," which could imply Russia?) desperately want their hands on this system.

Welcome back, my greenhorn hackers! Many new hackers come from a Windows background, but seldom, if ever, use its built-in command-line tools. As a hacker, you will often be forced to control the target system using just Windows commands and no GUI.

If you've been using Windows 10 for a while, you already know that Microsoft incorporated lots of new features into it. So you're probably familiar with Cortana (the new voice assistant), the Edge browser (their replacement for Internet Explorer), the newly resurrected Start menu, and all of the other big changes.
Mostly all hackers like to have a laugh. We like to have fun! We like to troll. And maybe, even cause some havoc once in a while. But, while we do this, we must always stay in the line of the law.

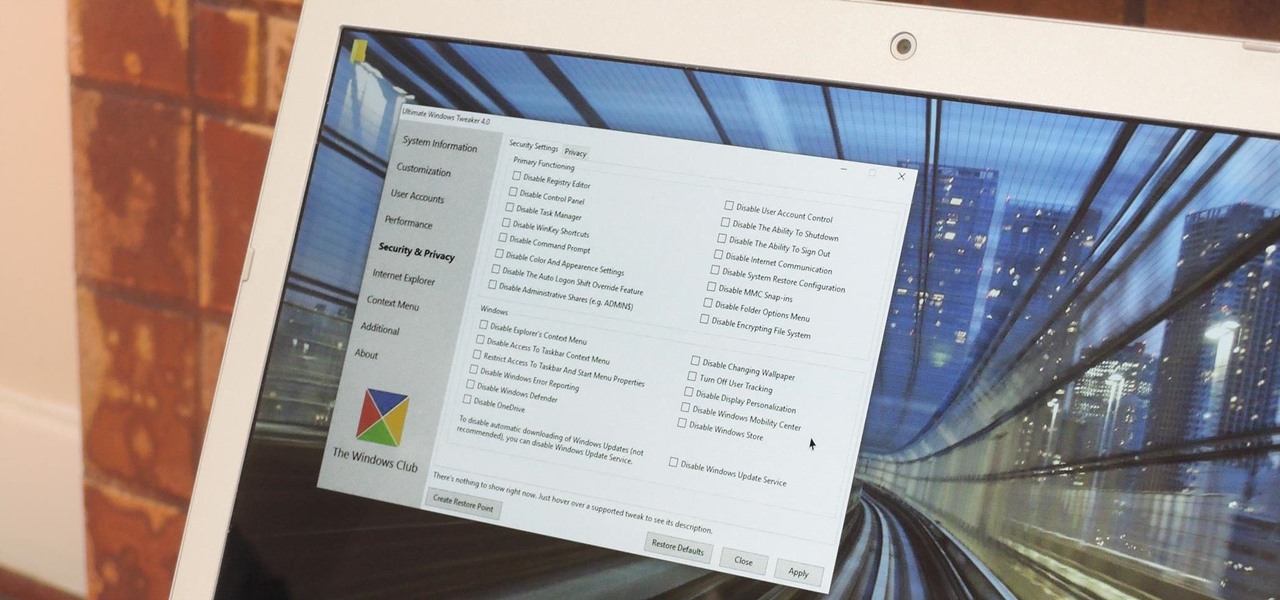
Every time Windows gets a significant update, the vast majority of existing tweaking utilities become obsolete. For every option that you fine-tuned with one of these tools on Windows 7 or 8, there's a change in the registry or system settings that cause your tweaks to now point to a dead end. This was definitely the case with Windows 10, since there were so many sweeping changes that very few existing options carried over.

When I tried to set up an eviltwin for a MitM-constelation in kali 2.0, I couldn't provide internet to the victim. The origin was the brctl bridging. I have read many tutorials but all of them where explained in backtrack and older versions of kali. So i was searching for a solution without using brctl and this solution will be explained now. This will just work on unencrypted wireless-environments.

From time immemorial, human beings seem to be at odds with one another. When these differences become so heated and unresolvable, it eventually erodes into physical violence. This violence has manifested into some of the most horrific exercises in human history, things which every school child is aware of and none of which we have to recount here. Although humans have been cruel and violent for a very long time, the 20th century may have epitomized that behavior. With two World Wars and many,...

If you took a big step back and really looked at the world, you'd see how downright silly our nations look when they put up fences to separate themselves from one another. Creatures big and small roam free while respecting each other's space, but humans create borders and physical barriers to delineate their cultures.

Welcome back, my greenhorn hackers! In previous Wi-Fi hacking tutorials, I have shown you ways to create an Evil Twin, to DoS a wireless AP, and to crack WEP and WPA2 passwords, but in this tutorial, I will show you something a little bit different.

Welcome back, my tenderfoot hackers! As you know, DNS, or Domain Name System, is critical to the operation of the Internet. It provides us with the ability to type in domain names such as www.wonderhowto.com rather than the IP address. This simple service saves us from having to memorize thousands of our favorite website IP addresses. Instead, we simply type in a domain name to retrieve the website.

Depending on who you ask, internet connectivity should be a basic human right. With Google recently embarking on a project to provide internet capabilities to remote corners of the world using balloons and satellites while Facebook attempts to do the same with unmanned drones, the concept of free web access is steadily gaining steam.

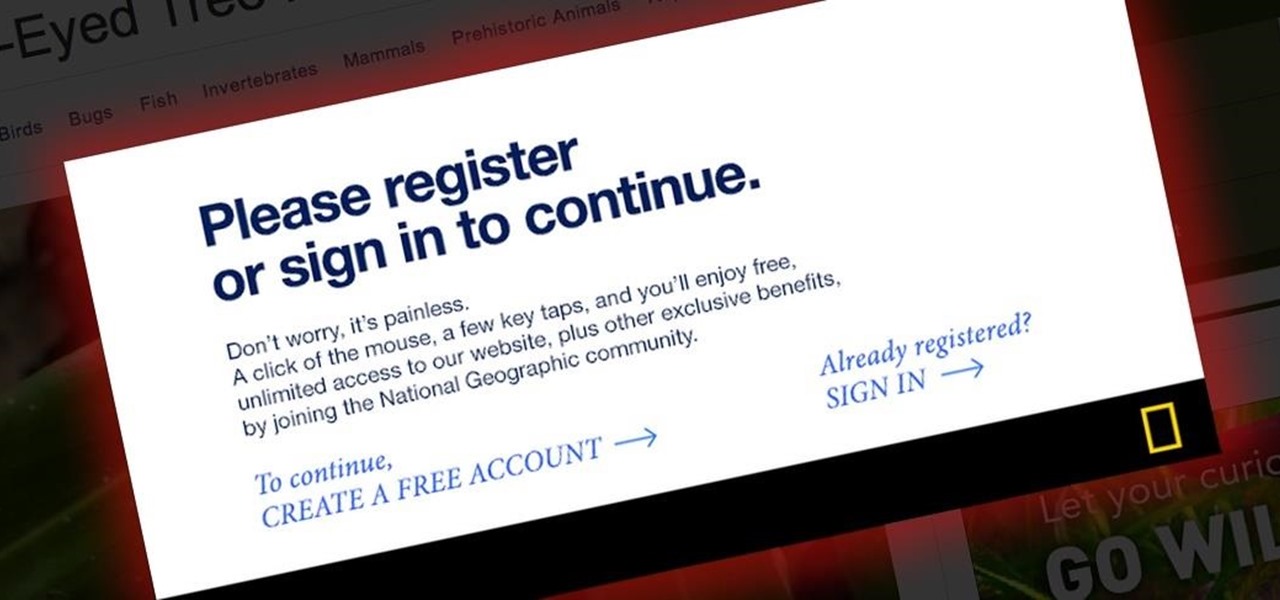
Last night, I was reading a riveting National Geographic article on the green-eyed tree frog, until I was quickly interrupted by an annoying popup asking me to "create a free account" or "sign in." Really, I'd like to do neither. I just want to read about tree frogs.