
How To: Navigate with a compass
Learning how to read a compass might just save your life one day! Know how to use a compass and you'll never get lost in the wild. Follow these simple steps & you'll learn this valuable skill.


Learning how to read a compass might just save your life one day! Know how to use a compass and you'll never get lost in the wild. Follow these simple steps & you'll learn this valuable skill.

Looking to get an FHA loan? The Federal Housing Administration, FHA for short, provides mortgage insurance on loans made by FHA-approved lenders throughout the U.S. Here's how to get your FHA-insured loan. Learn how to get one with help from this video.
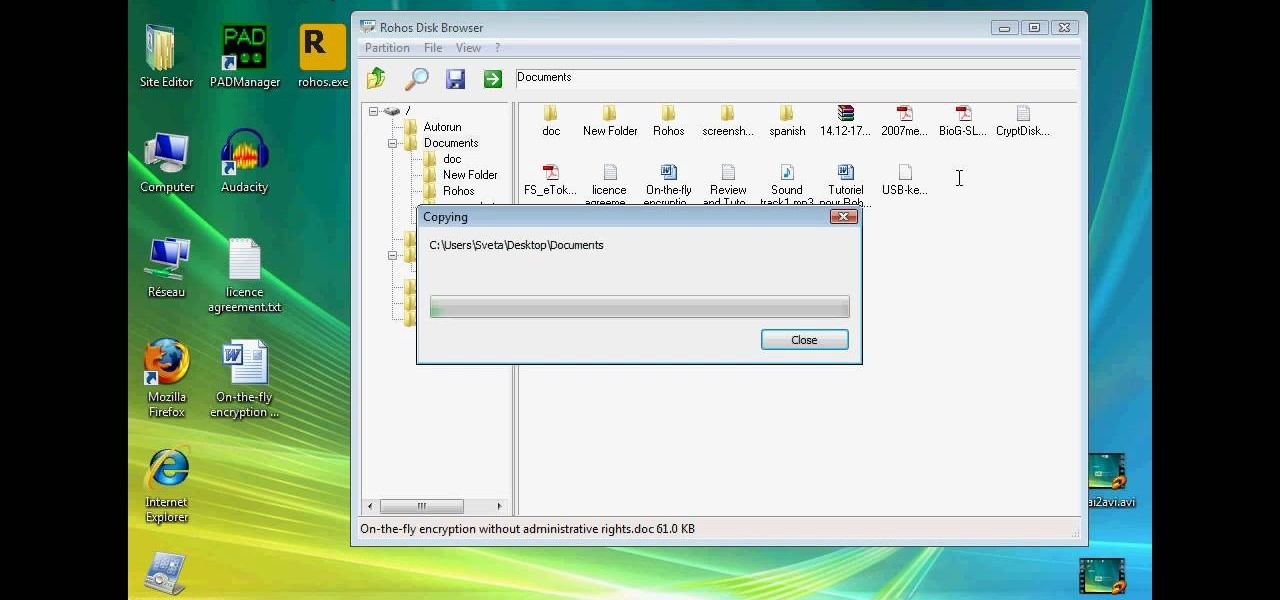
This technical video will show you all about the Rohos Mini Drive. See how you may work with an encrypted partition on a PC without admin rights using this free portable encryption solution. It securely protects your portable data on any USB device. Portable utility Rohos Disk Browser gives you opportunity to work with your sensitive data on a USB drive in the usual way on any PC (even at an internet cafe, where you don’t have admin rights).
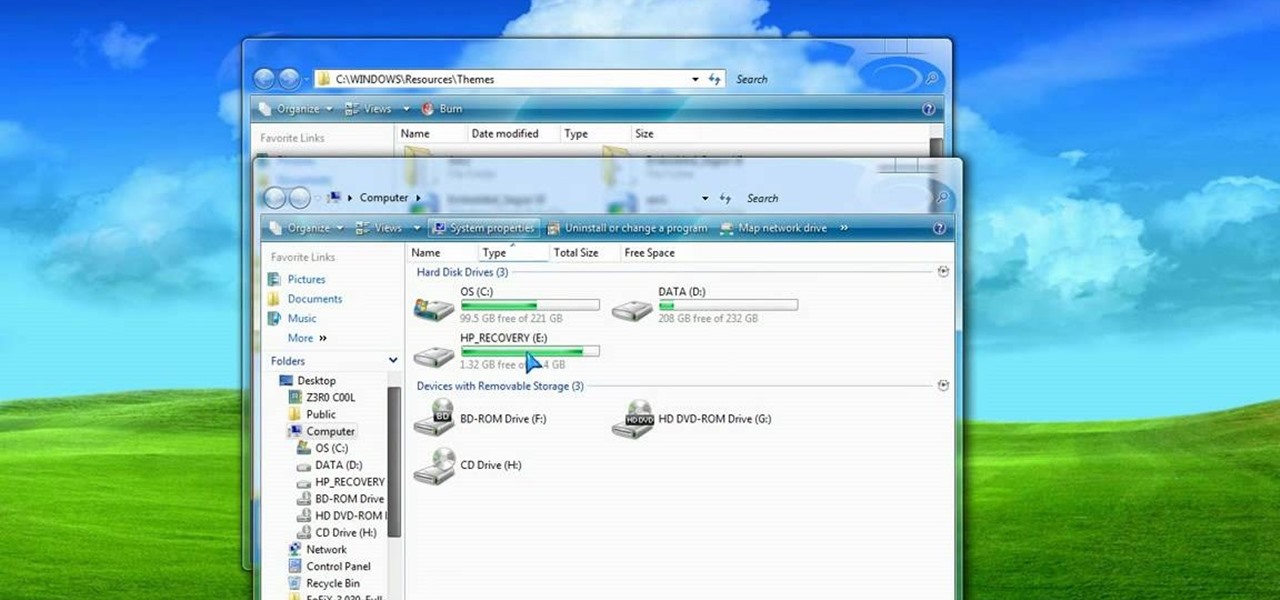
This video tutorial shows you how to make your Vista look like Mac Os X To make Windows Vista look like a Mac Os X using Vista Glazz Application:
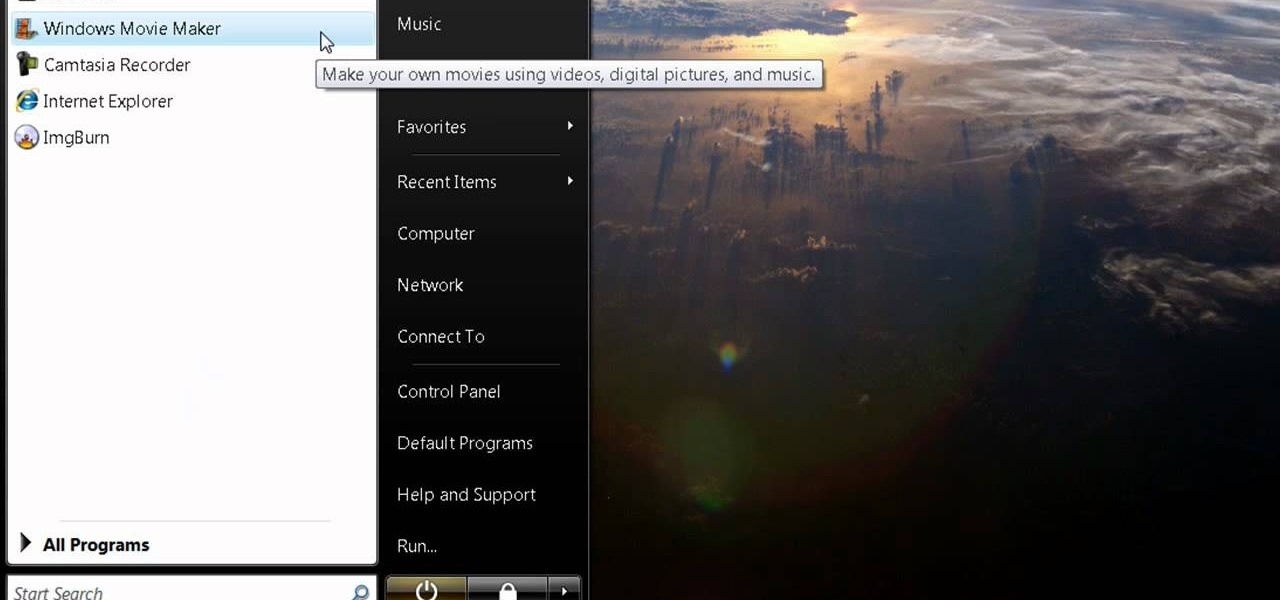
The first thing you have to do make a movie is to click on Start and go to windows Movie Maker. And then click on Import media to edit the video which you want. And then drag the selected video to Time line at the bottom. If you want to make your movie for less than a five seconds or so click on the Trim and drag it to your left hand side. When your done with that click on file menu and click on publish movie. You can name your file and can also choose the destination you want and then click ...

Dropping out of high school doesn’t have to mean the end of your educational career. You can earn a General Education Development diploma, also known as a GED. In this video, learn about the process needed, step-by-step, to get your GED.

Want to fulfill your dream of becoming an ice cream truck driver? If the idea of rolling around in the sunshine selling ice cream sounds good to you, here's what you need to do.

Looking to create a savings account? Once you see how much you can save when you spend only on needs rather than wants, you may never go back to frivolous shopping. In this video, ways to stop spending so much money are gone over.

Are you a young aspiring actress? A triple threat? Many top singers and entertainers today got their start on the Disney Channel. In this video, learn how to get that audition with the Disney Channel... Who knows, it could be your big break!

Want to win the prize? Knowing a little math is the key to winning this popular contest. In this video, learn how to estimate correctly.

So, you've downloaded Boxee... Experience TV in a brand new way! This video will help you get started.

Looking to move the right way? Owning a piece of property is an important goal for many people. Here’s how to obtain a copy of proof of ownership.

You are never too old to meet a mate! Never! In this video, learn some great tips on how to socialize your life to meet men when over 60.

Fantasize about role playing? One of the most popular venues for role playing medieval fantasy is the board game, Dungeons and Dragons. Get a group of three or four together and have a blast!

With social networking systems, YouTube comments chains, chat rooms, bulletins boards, Twitter updates... It seems as if almost everyone has at one time publicly stated an opinion on the Internet. Nearly half of all prospective employers research job applicants online. Make sure that what you’re posting today doesn’t cost you a dream job tomorrow!

Looking to make a nutritious change in your life? By choosing the right foods in the right amounts, you can reap rewards that will benefit you in all aspects of your life. In this tutorial, learn how to eat healthy and make positive changes in what you consume.

With information, diligence, and determination, hair pulling is a habit that can be broken. You Will Need

If TV cartoons don’t provide enough intellectual stimulation, try these tips to improve your vocabulary and impress your friends, or just yourself.

Before you select a guard dog, find out what qualities to look for and what to avoid. You Will Need

If you want to stop telemarketers from calling, use this guide and try a multi-pronged approach. You Will Need

Labor is probably the most feared of pregnancy’s "unknowns." Here's how to manage it. You Will Need
Got a digital camera, but no idea how to share pictures with friends and family? Try the photo-sharing site Flickr.

While ramen noodles aren't unhealthy per se, they aren't packed full of vitamins either. But if you're a fan of these cheap, tasty noodles, there are ways to make the meal more balanced.
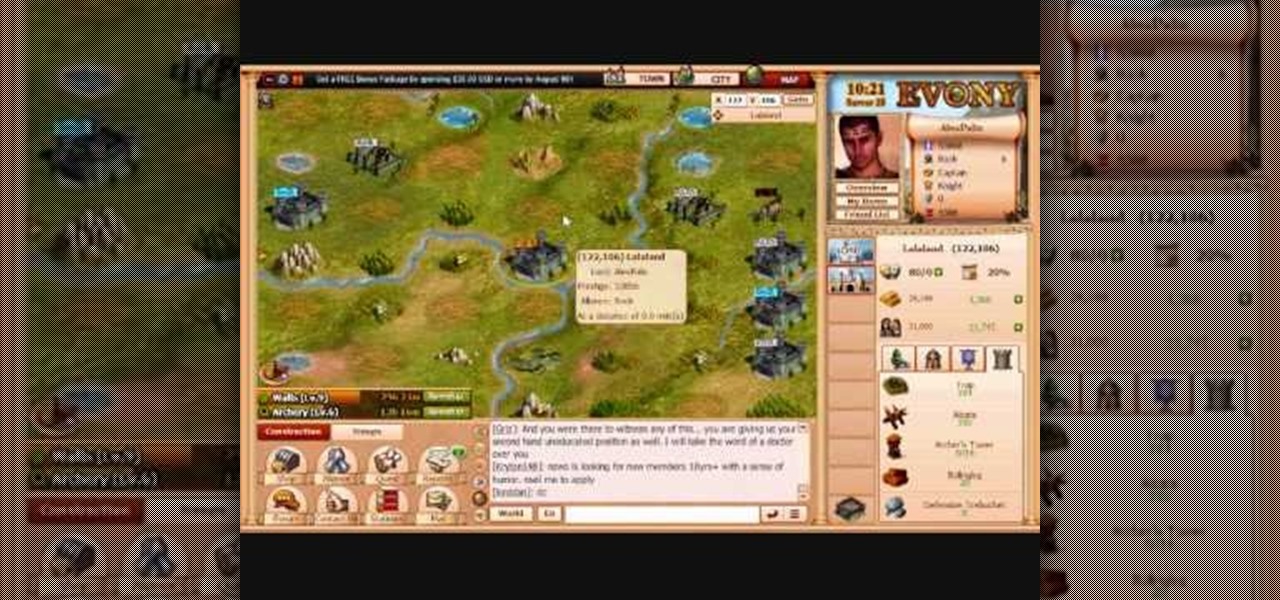
Learn everything you could possibly want to know about the internet, multiplayer game Evony with help from alexstewart2. Watch this video tutorial to learn how to farm rose, lion, cross, and nation medals in Evony.
Don't let fate decide the makeup of your fantasy football team. Participate in a live draft with these tips.
Hack mybrute with this mybrute cheat. MyBrute hacks, cheats, tricks. Watch this video tutorial to learn how to hack MyBrute for more experience and stats (08/01/09).

Watch this video tutorial to learn how to play the Google language computer prank on a coworker. Change your colleague's Google settings with this easy prank, and watch their head spin!

Your friends want you to marry them! Before you can officiate their big day, you'll need to jump through some legal hoops. Learn how to officiate at a wedding.

Learn how to write a grant proposal. If your organization has come up with a great idea that needs money to get off the ground, you'll need a great proposal. Here's how to write one.

Go thrifty! Go vintage! Go second hand. With the right approach and an open mind, a trip to your local thrift store can yield some fashionable bargains. Buying used is a smart solution to this economy, and gives you a smart sense of fashion.
Look good for your internet friends. Edit photos on social networking sites such as Facebook and Picasa as well as blogs without having to download them to your computer.

Learn how to use Gmail to its maximum potential; get internet tools and computer networking tips from expert Drew Noah in these free instructional videos.

Reverbnation.com is a revolutionary new website that has been taking the internet promotion idea to the next level with free emailing, widgets and stats. Learn tips on how to use this great site in this free video clip series.

Want to control a friend's cell phone remotely and make "free" calls from it? In this hack how-to video, you'll learn how to hack Bluetooth-enabled cell phones with your Sony Ericsson or Nokia phone and the Super Bluetooth Hack—or "BT Info"—, a free program easily found through Google. Once installed, Super Bluetooth Hack will enable you to control your friends' cell phones remotely.
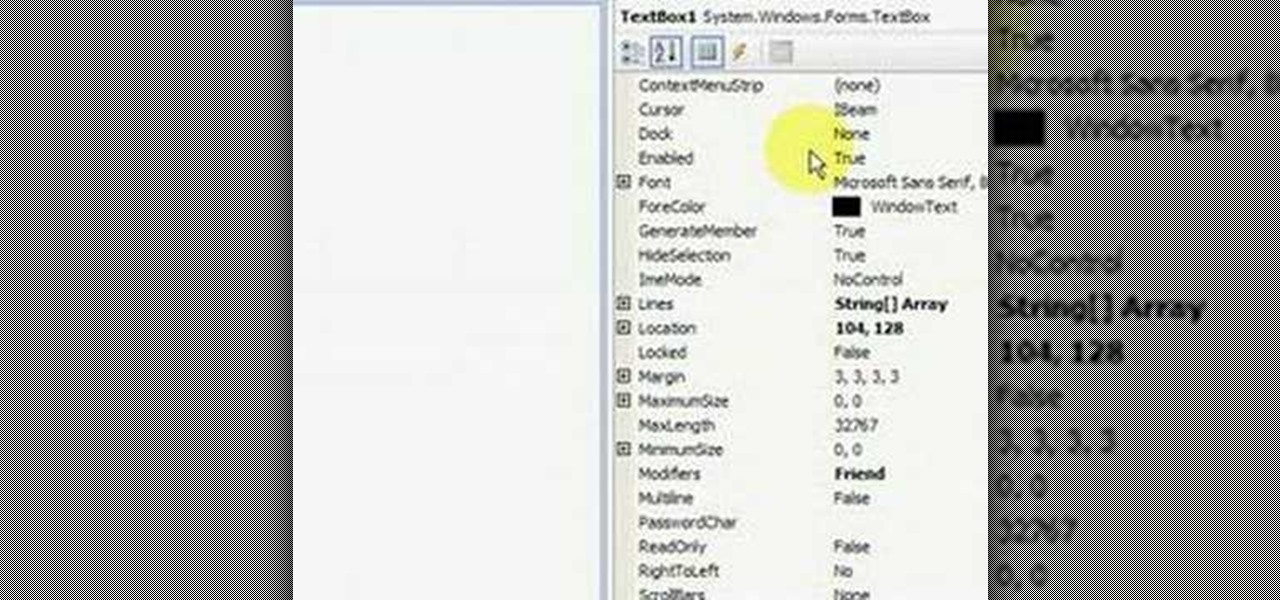
Check out this eight-part VB.Net video tutorial to see how to create a program from the ground up using VB.Net in Microsoft Visual Basic 2008 Express Edition. You'll need Internet access for this task, like most other tasks. Start a new program and get watching. If you're new to VB.Net program development, than this is just the spot.

Almost 20% of the US population (about 60 million Americans) live in rural areas where mobile reception is weak or nonexistent. In times of crisis, these Americans can't rely on the internet to communicate with loved ones or receive new information. This is why being able to interact offline is so important.

Giving up your Wi-Fi password can be giving up more control than you think. Because of the way Chromecast and other IoT devices communicate, anyone on the same Wi-Fi network as your device can often make it do whatever they want. With a script called "Cast All the Things," we can hijack a Chromecast to play nearly any kind of media with a single command in terminal.
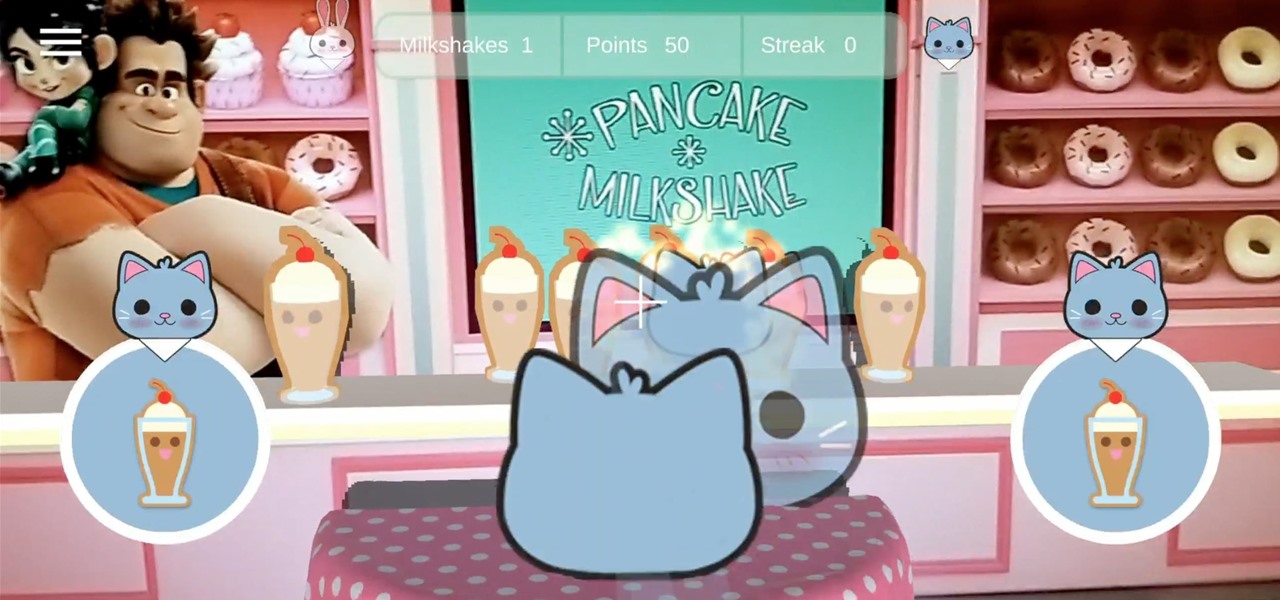
One of the funniest scenes from the teaser trailer for the Wreck-It Ralph sequel is the basis for the new pre-show augmented reality experience via the Noovie ARCade app.

These days, it seems new phones get announced every other week. We've grown accustomed to glossing over the specs, looking at some press renders, then moving on to check out the next phone. If you had done this in September 2008, you might have overlooked what would become one of the most important phones of all time.

Hacking Wi-Fi is a lot easier than most people think, but the ways of doing so are clustered around a few common techniques most hackers use. With a few simple actions, the average user can go a long way toward defending against the five most common methods of Wi-Fi hacking, which include password cracking, social engineering, WPS attacks, remote access, and rogue access points.