This video is a tutorial on how to ride a bike in traffic. The first rule is to obey the law. You would need to follow the laws of traffic as though you were driving a car. If there is a bike lane, use it. It is not a good idea to use the sidewalk as that is reserved for walkers and runners. Ride predictably by signaling your turns. The video tells the viewer which side of the road to ride on, and also provides tips. He also discusses how to ride with another cyclist. This is a very informati...

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to set up SSH tunneling to securely transmit HTTP traffic.

If you're looking to increase the ranking of your website in Google, and so increase your traffic, you'd do well to at least a rudimentary understanding of what Google looks at when considering the relevance of a web page to a given query. This SEO tutorial offers a cursory explanation of how the Google search robot sees, or spiders, your website. Drive more traffic your website with this SEO how-to.

With the rise of website encryption (TLS), sniffing passwords from network activity has become difficult. However, it's still possible to quietly exfiltrate a target's network traffic in real time to extract passwords and sensitive information. Pertaining to macOS, there are two methods for retrieving traffic from a backdoored Mac.
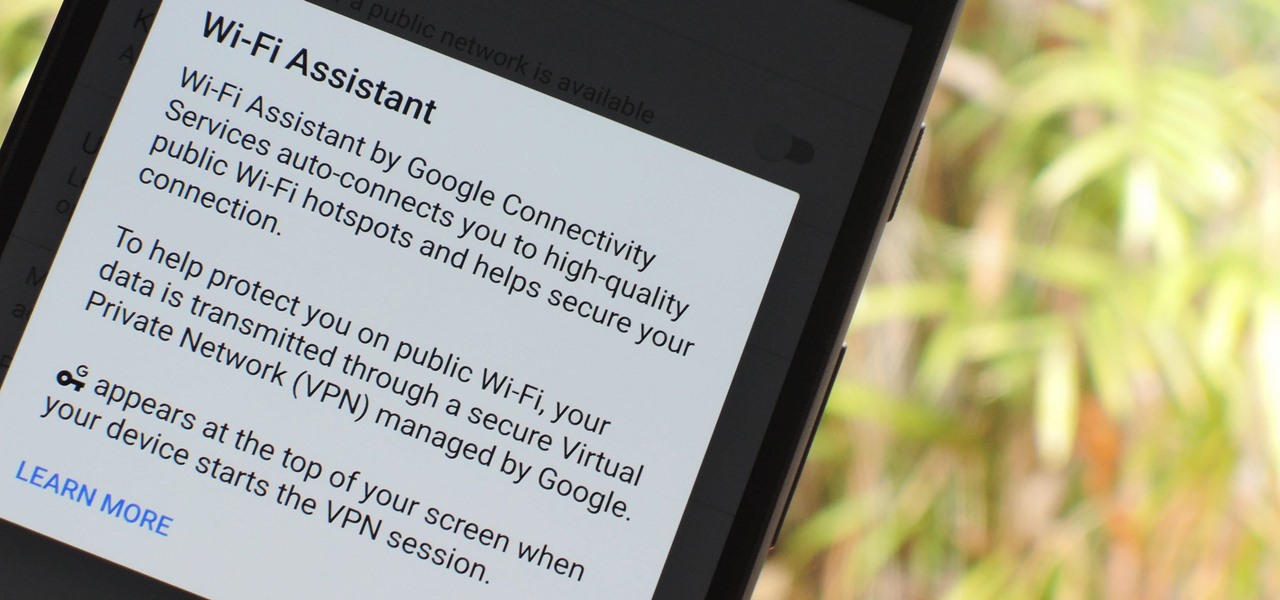
The Pixel and Pixel XL come with an awesome data-saving feature called Wi-Fi Assistant that automatically connects to open internet hotspots, then creates a secure VPN on your device to keep your data safe.

A VPN service is almost an essential these days. Good ones can block ads, prevent tracking cookies, encrypt your internet traffic for better security, and even spoof your device's location to bypass geo-restrictions — all things you should be concerned about in the age of NSA snooping and Facebook data mining.

Flickr is the most known and dependable photo sharing website to date, so if you haven't made an account yet, you better now, if you want to share your precious photos with family, friends, and even the whole world! Flickr allows you to store digital photographs online and share them with other people.

SSH is a powerful tool with more uses than simply logging into a server. This protocol, which stands for Secure Shell, provides X11 forwarding, port forwarding, secure file transfer, and more. Using SSH port forwarding on a compromised host with access to a restricted network can allow an attacker to access hosts within the restricted network or pivot into the network.

A man-in-the-middle attack places you between your target and the internet, pretending to be a Wi-Fi network while secretly inspecting every packet that flows through the connection. The WiFi-Pumpkin is a rogue AP framework to easily create these fake networks, all while forwarding legitimate traffic to and from the unsuspecting target.

Welcome back, my greenhorn hackers! In previous Wi-Fi hacking tutorials, I have shown you ways to create an Evil Twin, to DoS a wireless AP, and to crack WEP and WPA2 passwords, but in this tutorial, I will show you something a little bit different.

Welcome back, my hacker apprentices! Several of you have written asking me how you can check on whether your boyfriend, girlfriend, or spouse is cheating on you, so I dedicate this tutorial to all of you with doubts about the fidelity of your spouse, girlfriend, or boyfriend.

Welcome back, my fledgling hackers! Awhile back, I demonstrated one of my favorite little tools, netcat, which enables us to create a connection between any two machines and transfer files or spawn a command shell for "owning" the system. Despite the beauty and elegance of this little tool, it has one major drawback—the transfers between the computers can be detected by security devices such as firewalls and an intrusion detection system (IDS).

Welcome back, my hacker novitiates! Many of you have probably heard of a man-in-the-middle attack and wondered how difficult an attack like that would be. For those of you who've never heard of one, it's simply where we, the hacker, place ourselves between the victim and the server and send and receive all the communication between the two.

Welcome back, my hacker apprentices! In recent weeks, the revelation that the NSA has been spying on all of us has many people up in arms. I guess I take it all in stride as I just assume that the NSA is spying on all of us—all of the time. Don't get me wrong, I don't condone it, but I know the NSA.

Right out of the box, iPhone is incredibly easy to use. If you want to get the most out of every feature, you’ve come to the right place. This video tutorial straight from Apple will teach you how to use GPS maps and the compass on the Apple iPhone 3G. The iPhone redefines what a mobile phone can do.

Accidents are the worst. They're costly, time consuming and an all around pain in the butt. Rear-end collisions are among the most common types of accidents on the road. Take these simple precautions to avoid a rear-end collision.

This video tutorial is about using Google Maps and the features in it. Google Maps help us to find the geography and even the traffic situations of a city. Google maps also provide a street view option that helps us to see how a place actually looks like from the ground. Neither of these views are real time. But now, Google Maps has added in a new option, which is the webcam. Just click on the more option in between traffic and map option. In the list that appears, just tick the webcam option...

Hak5 is at it again, with a plethora of somewhat accessible solutions to your technological problems. If you've ever needed to get through your school's firewall, or secure traffic tunneling, or try out applications in a fast, efficient manner? This video has it all and more.

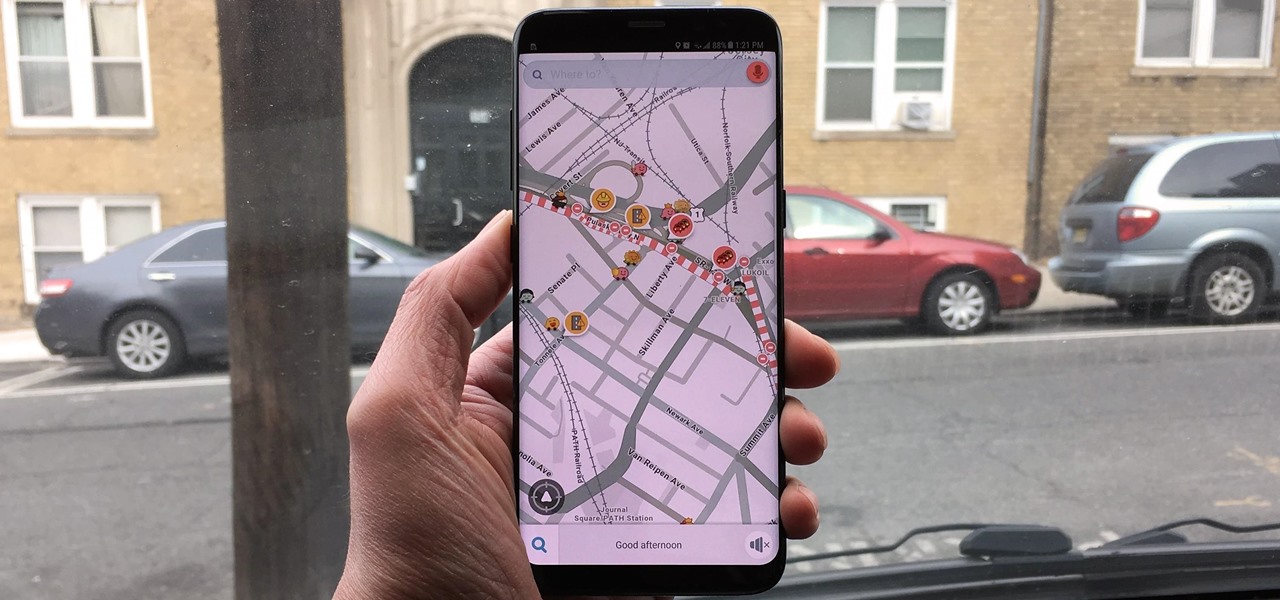
Because it sources a majority of its vital data from actual drivers on the road, Waze is easily one of the best navigation apps to use if you prioritize safety. Benefits such as crowd-sourced traffic data, police trap locations, and road work avoidance, when combined, help you anticipate traffic conditions with unprecedented accuracy and make adjustments accordingly.

In this video, we learn how to use the iPhone map app. First, go to Google Maps and click on the bottom to find your current location. This will show up in a blue button, which you can tap on to find out more information. The map will go in the direction your iPhone is facing and you can zoom in on information about places around you. You can also type in a place you are searching for, and get directions, then save them to your phone if you prefer. The key is the button on the bottom right wh...

This video will show you how to tether your Samsung Messager 2, (the MetroPCS phone) to your PC to use as a modem for internet access. This will allow you to use your cell phone as your internet connection point, meaning you'll connect to the net for the cost of your cell phone's data plan. You will need your Samsung USB cable, a PC with Windows 2000 or higher, all current drivers for your phone and PC, and you will also need to head here to get the Samsung PC Studio program. This is part 1 o...

In this tutorial, we learn how to drive traffic to your website using Twitter. To get started, you will sign up for an account and then go to your profile. Start to follow people and have them follow you back as well. If someone mentions your name then all of their followers will see your name and can click on you to see your profile. If you have something interesting on your profile, then they will want to follow you! It's important to have your main website link on your website and a bio wi...

Want to make an Inverted Traffic Light cocktail like a champion bartender? This clip will show you how it's done. With the proper technique, mixing the perfect drink can be easy. So easy, in fact, that this free video bartenders' guide can present an overview of the process in about a minute's time. For more information, including a full list of ingredients and complete instructions on how to mix this drink yourself, take a look.

Collin teaches us how to race at Laguna Seca raceway in this tutorial. When coming out of the pit lane, wait for the workers to wave you on. Make sure there is not traffic around you because you will be doing over 100mph. Once you are sure there is no traffic, turn in the late turn so don't dual apex it as you are turning. By this time you will turn four and then turn five after this on the right hand side of the track. Next, turn six with a small amount of braking bringing the car out and ru...

Systm is the Do-It-Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. They will help you avoid pitfalls and get your project up and running fast. In this DIY episode, see how to create an Internet enabled claw game.

While modern browsers are robust and provide a lot of functionality, they can be unlocked to do some pretty spectacular things with browser extensions. For hackers and OSINT researchers, these tools can be used to defeat online tracking, log in to SSH devices, and search the internet for clues during an investigation. These are a list of my top ten favorite browser extensions for hackers — and how to use them.

Hacking from a host machine without any form of proxying is reckless for a hacker, and in a penetration test, could lead to an important IP address becoming quickly blacklisted by the target. By routing all traffic over Tor and reducing the threat of malicious entrance and exit nodes with a VPN, we can configure Kali to become thoroughly private and anonymous.

I have came across a lot of members on the forum that didn't have a clear idea of what port forwarding is and what it does. So...Let's get started...

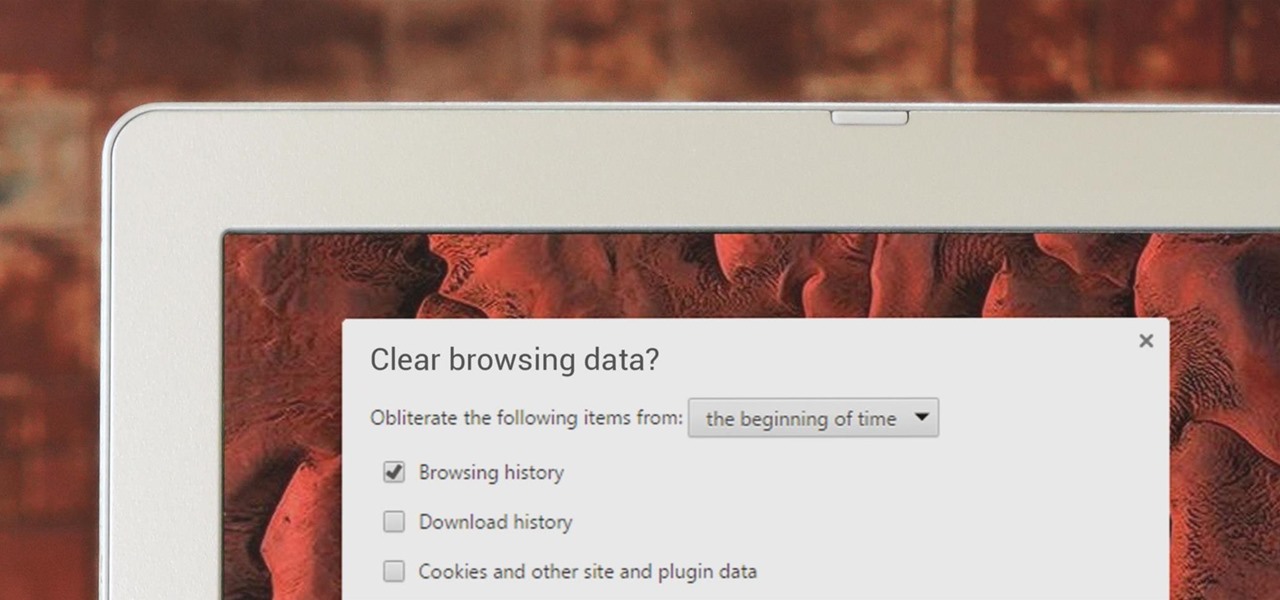
If you've been visiting websites of ill repute, or if you've been Christmas shopping and don't want to spoil the surprise, it would be a disastrous situation if anyone were to come across your browsing history. Visited sites, cookies, and cache can paint a very clear picture of your recent internet activity, and depending on the situation, you may only have a few seconds to delete your history before someone else barges in.

Having the ability to stream music or video from practically any internet-capable device is a thing of wonder—especially at the airport. I don't know how many times Netflix has saved me from watching something like CNN for 5 hours straight at the gate during long layovers. But streaming video sites like Netflix only work in North American and few other regions. So, if you're a U.S. subscriber currently in Australia or France or any other international location, Au Revoir to your streaming cap...

Android has released a new application called ezNetScan, which is a free app that scans the wireless network you're connected to and gives you a full log of all of the devices connected to that network. This isn't new for smartphone users, let alone Android users. Fing has been around for a while and does practically the same thing that exNetScan does. It gathers information such as the IP and MAC addresses, device vendors, and ISP location. But while Fing is a great program, it does lack a f...

This tutorial demonstrates how to use Microsoft Internet Explorer and Mozilla Firefox. Learn more about web browsers in this free instructional video series.

In this Computers and Programming video tutorial you will learn how to delete temporary internet files in Internet Explorer 8. The video is from FreeComputerRepair. Click on Start -> control panel ->network and internet connections -> internet options. Now the internet properties dialog box opens up. Here you go down to browsing history and click ‘Delete’ button. This will open up the Delete Browsing History window. Here you check all the data that you want to delete. If you don’t want to del...

Waze is the go-to navigation app for millions of drivers, and it's easy to see why. Benefits such crowd-sourced traffic data, police trap locations, and road work avoidance are just the tip of the iceberg. It can almost be overwhelming, but with these simple tips, you'll master Waze and start navigating like an expert in no time.

We all know we shouldn't be using our smartphones while driving. But we also know many people do it anyway. Soon, however, the addicts among us may not have a choice but to kick their habit. A new app announced today by Samsung will block all calls and texts while you drive, stopping those who text and drive right in their tracks.

You may not know what HTTP is exactly, but you definitely know that every single website you visit starts with it. Without the Hypertext Transfer Protocol, there'd be no easy way to view all the text, media, and data that you're able to see online. However, all communication between your browser and a website are unencrypted, which means it can be eavesdropped on.

With iTunes, you can listen to the radio over the internet and hear broadcasts from around the world. Make sure your computer is connected through the internet, then click "Radio" in the source list to see the internet radio stations available through iTunes.

360world, a Hungary-based tech company involved in motion control and augmented reality, released information today about their latest products, the CLAIRITY HoloTower and CLAIRITY SmartBinocular. These tools are designed to bring augmented reality into the hands of air traffic controllers, via Windows Mixed Reality, to greatly improve their workflow over tools already in use.

Good day people, today we will examine some basic, for some people well-known attacks, also we will take a look at some advanced attacks.

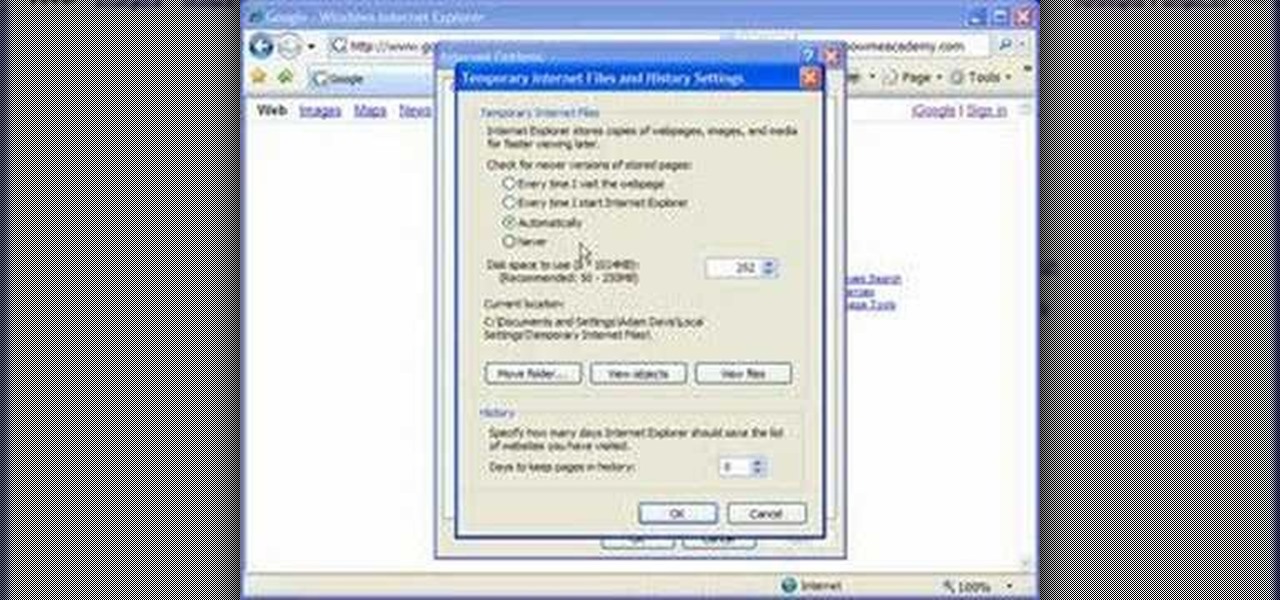
In this video, we learn how to automatically clear browser cache in Internet Explorer. This will help your internet run faster and it will also help protect your computer from your personal information being store. First, open up Internet Explorer, then click on the tools drop down menu and go to internet options. From here, go to temporary internet files and click on the button that says "automatically", then adjust the disk space to use to what you prefer. After you have changed the setting...