If you've already gotten your hands on Sony's Internet TV Blu-ray Disc Player, powered by Google TV, then you know how powerful this thing is. But if you're thinking of getting one soon, this video series will help you learn what you'll be getting yourself into.
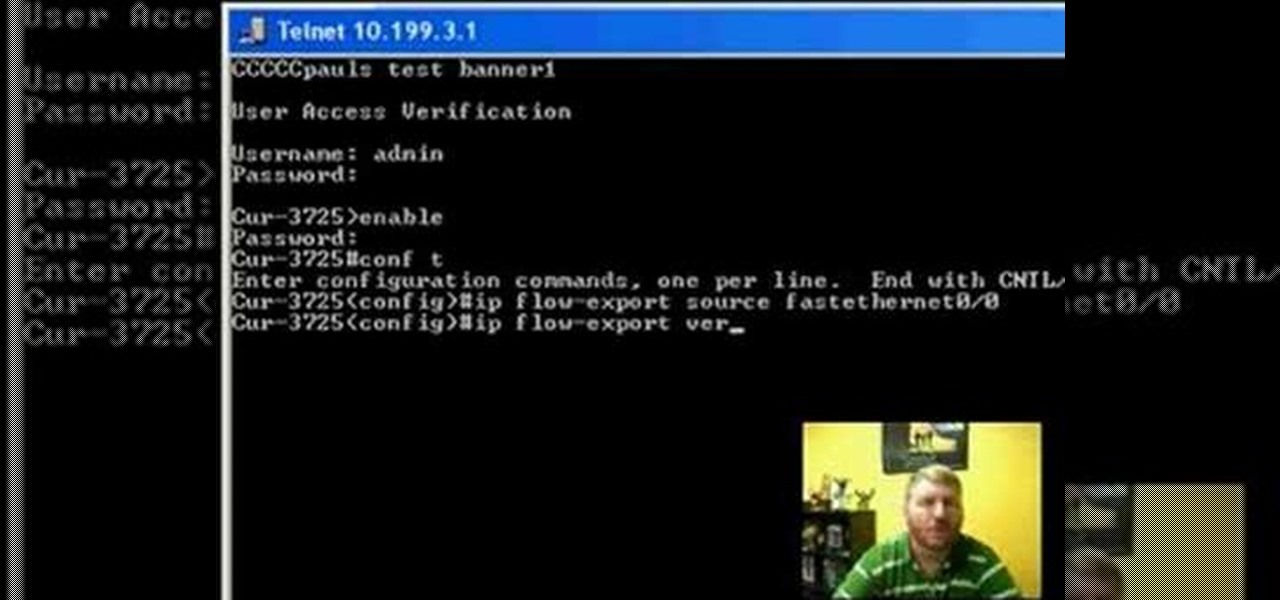
Netflow technology allows you to monitor web traffic to your website - find out who comes to your site, where they're coming from and where they go afterwards. You can configure a Cisco router manually to monitor netflow going through the router.

There are many different applications and games on the Nintendo 3DS that can take advantage of an active internet connection over Wi-Fi such as Netflix or the eStore. Unfortunately, since the 3DS is a mobile device, you won't always have access to the internet. If you have a mobile hotspot on a smartphone or tablet, you can share the internet connection over wireless with the gaming handheld.

Selling stuff at the local flea market sounds easy enough, but it isn't anything like having a yard sale. There's a lot more to it that just getting rid of your junk, and the biggest things are being licensed and having a sales tax number. Flea market vendor may not be your first career choice but, like many, you may find it’s a lucrative full-time job or a profitable and fun sideline.
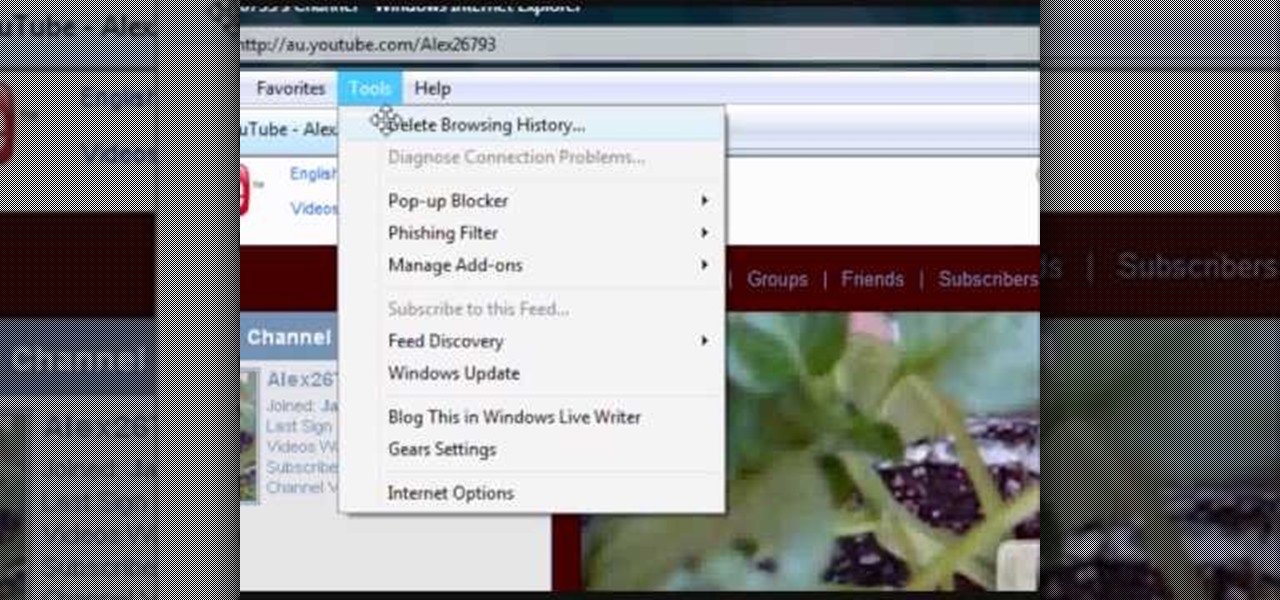
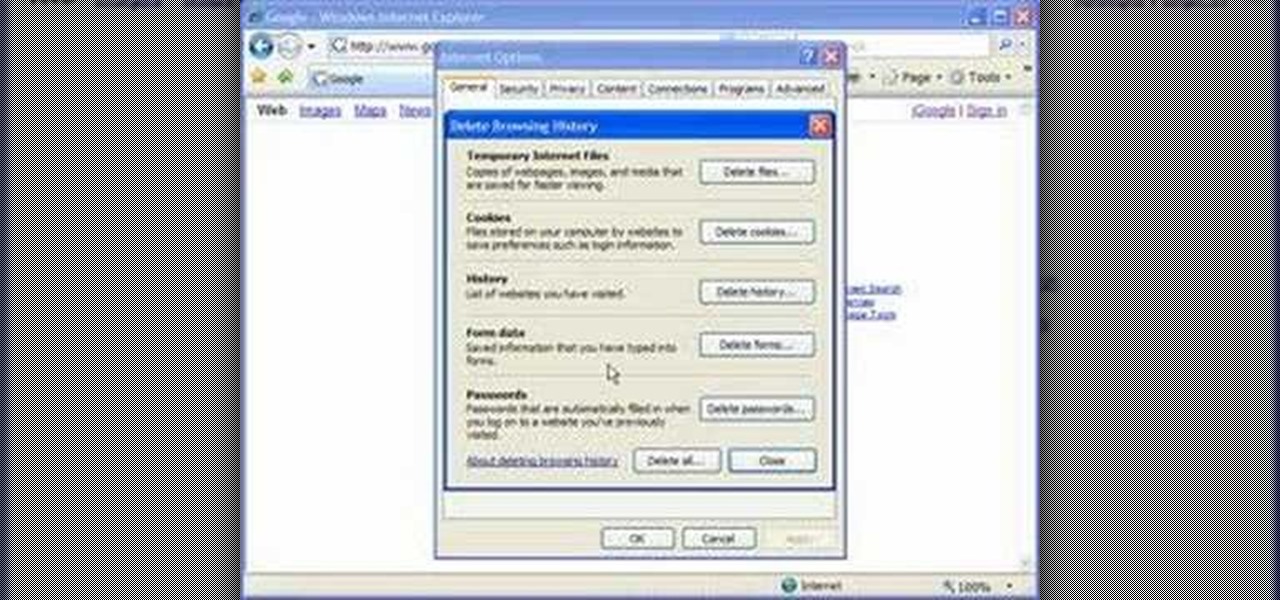
If your computer or web browser is running slowly, a good place to start clearing space is in your Temporary Internet Files. Temporary Internet files, as well as cookies, are collected every time you visit a site online. These files make it easier for your PC to remember your browsing history, and your log in information for various websites. However, sometimes all of these little files can add up into one big clog on your machine. If your computer isn't running up to par, follow along with t...
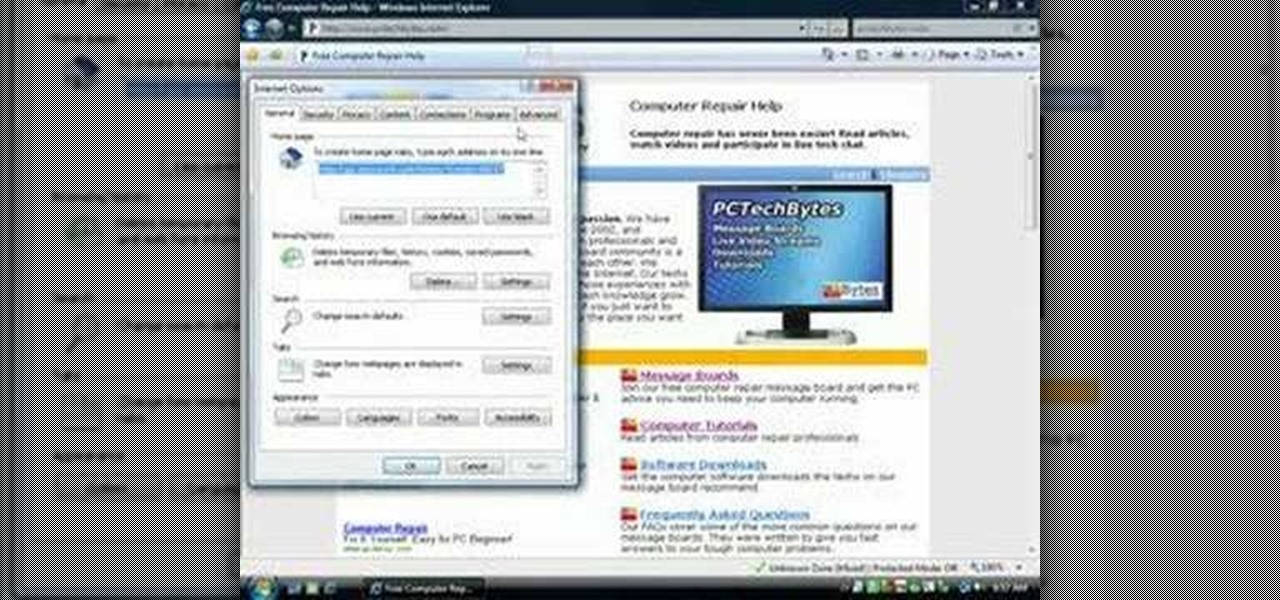
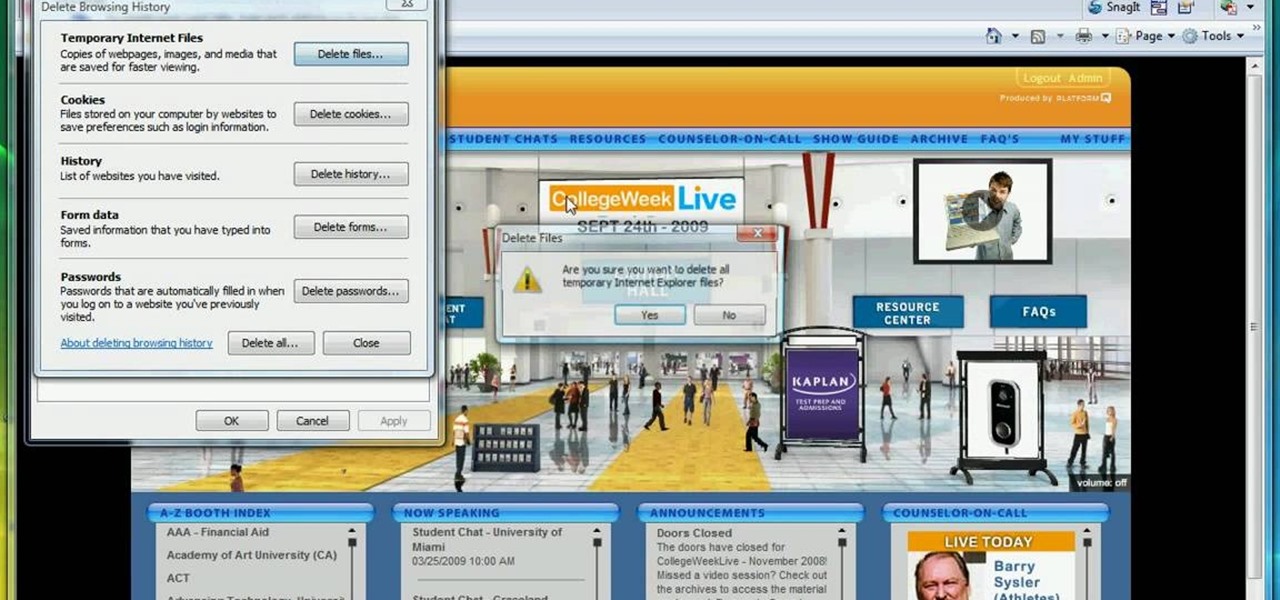
In this video, we learn how to remove our browsing history on Internet Explorer. First, click on "tools", then click on "delete browsing history". If you want to delete all of your browsing history, then click on that option. Most people are content with only deleting temporary internet files as well as browsing history. Getting rid of these will speed up your internet a bit. Another way is to go into "internet options", click under the "general" tab and choose which files you'd like to delet...

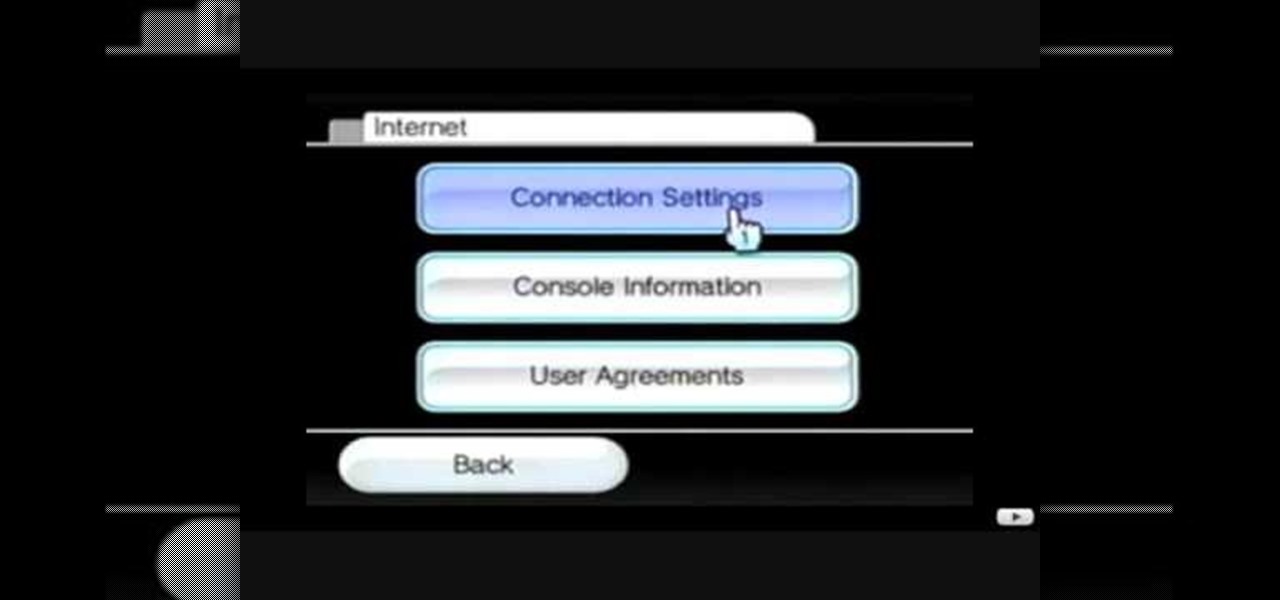
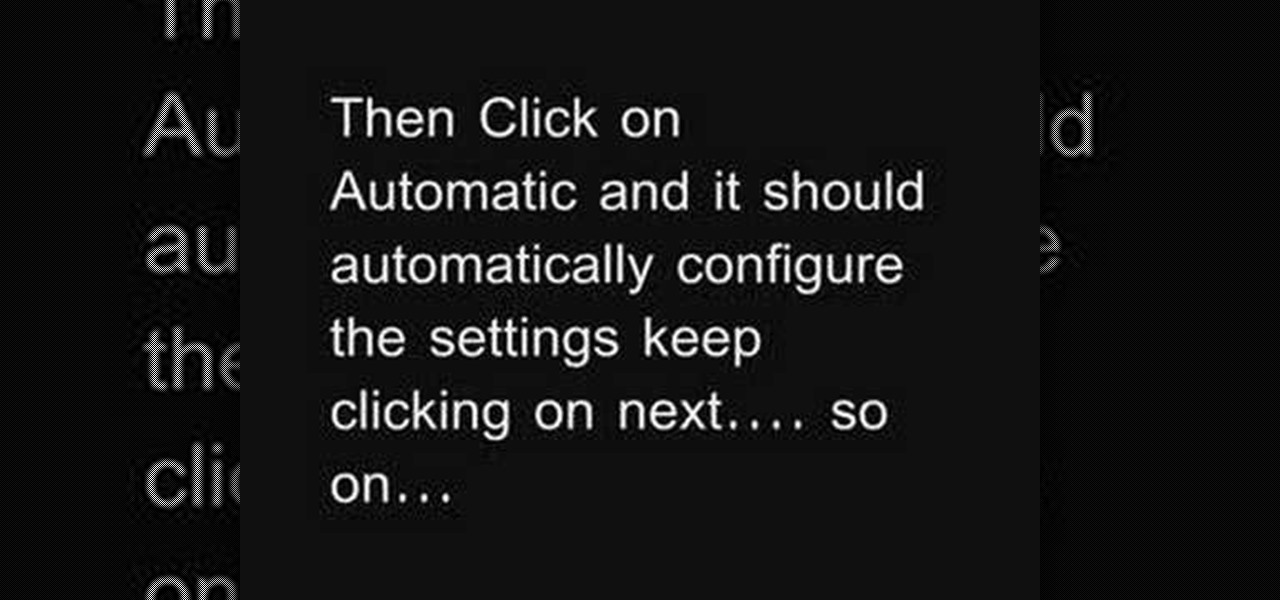
This video tutorial shows how to connect to the Internet using the Wii video game system. The advantage of connecting to the Internet with your gaming system is to play games, such as Animal Crossing or Call of Duty, with other players. You can also get the Internet Channel which allows you to watch YouTube videos and do other tasks you would normally do on the internet. You will need a wireless router to do this. On the Wii home menu, click on Options, Wii Settings, and scroll once to the ri...

Learn how to connect to the internet using your PS3 using an Ethernet cable. What you will need: 1. An internet modem or hub. 2. The details required to connect to the internet (password etc.). 3. A PS3 and an actual internet connection e. g. BT or AOL. Once you have those just follow these steps: 1. Take your Ethernet cable and plug it into the back of the PS3 into the socket labeled Ethernet. 2. Plug the other end into your internet modem. 3. Turn on your ps3 and go to "network settings" un...

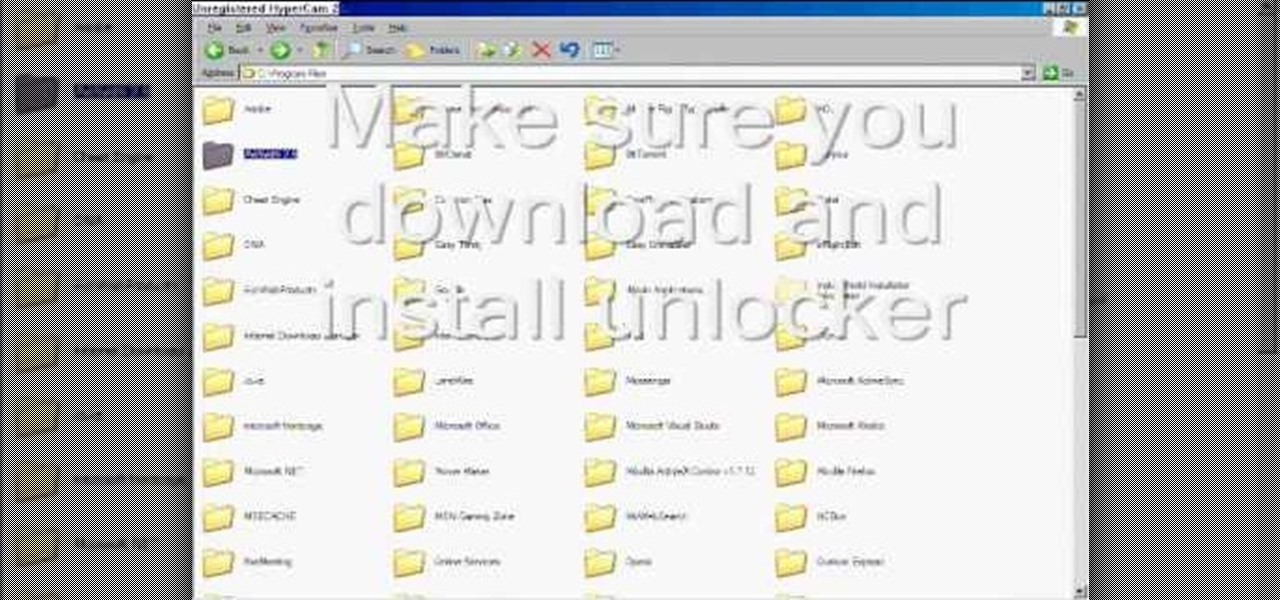
To delete Internet Explorer 7 or 8 from you computer, search for "unlocker" in the Google search engine. Click on the first search result to go to the unlocker site. Click download to access the unlocker application. Click the save me option when prompted. Next, find the downloaded files and install the unlocker application on your computer. Go to the local disk C, open the program files and find Internet Explorer. Right click on Internet Explorer and then click on the unlocker. Select the ap...

This video is a step by step guide to clear cache for Internet Explorer version 7.0. On your Internet Explorer browser version 7.0, go to tools. Click Internet options. Go to general tab, then click browsing history and hit delete. Window will pop up. Click delete on temporary files and click yes to confirm. Click delete on cookies and click yes to confirm. Click delete on history and click yes to confirm. Click x to close the window and the current Internet Explorer window. Pull up a new Int...

In a previous guide, I demonstrated how to extract images from a security camera over Wi-Fi using Wireshark, provided you know the password. If you don't know the password, you can always get physical with the Hak5 Plunder Bug. Using this small LAN tap, we can intercept traffic like images from a Wi-Fi or IP security camera if we can get physical access to the Ethernet cable carrying the data.

Threats to your privacy and security are everywhere, so protecting your data should be the highest priority for anyone with a smartphone. However, one threat many people overlook is the company who supplies the operating system your Android phone runs — Google.

The dark web is an intimidating place for a newbie hacker, but it's a powerful tool once you've learned to navigate it safely. To help you out with that, this guide will cover some need-to-know information for traversing the dark corners of the internet while keeping your identity and data safe. (Hint: Using Tor is not enough.)

In this day and age, maintaining your privacy is a perpetual battle, and doing so with an internet-connected device like your smartphone is even more of a struggle. Every website you visit, every app you install, every message you send, and every call you make is a potential vulnerability that could expose you to prying eyes.

When I tried to set up an eviltwin for a MitM-constelation in kali 2.0, I couldn't provide internet to the victim. The origin was the brctl bridging. I have read many tutorials but all of them where explained in backtrack and older versions of kali. So i was searching for a solution without using brctl and this solution will be explained now. This will just work on unencrypted wireless-environments.

If you're just starting out with Android—or smartphones in general, for that matter—there are a lot of little things to learn. One of the first terms you'll likely encounter is "Wi-Fi," which is a wireless internet connection served up by a router in your home, office, or local coffee shop. This differs from your smartphone's regular "Mobile Data" connection, which is provided by your cellular carrier and included as part of your monthly bill.

As was mentioned by the great OTW last week, TOR, aka The Onion Router, has had its integrity attacked by the NSA. In an attempt to reduce the anonymity granted by the service, the NSA has opened a great many nodes of their own. The purpose is presumably to trace the origin of a communication by compromising some entrance and exit nodes. Once both are compromised, it is much easier to correlate traffic with a particular individual.

When you are riding with a group or in a trafficked area, communicating with the people around you is essential for keeping all of you safe. This videos will explain the importance of good communication for riders and show some commonly used hand signals that you can use to signal your fellow riders. These will help you avoid obstacles and have the most fun ride you can.

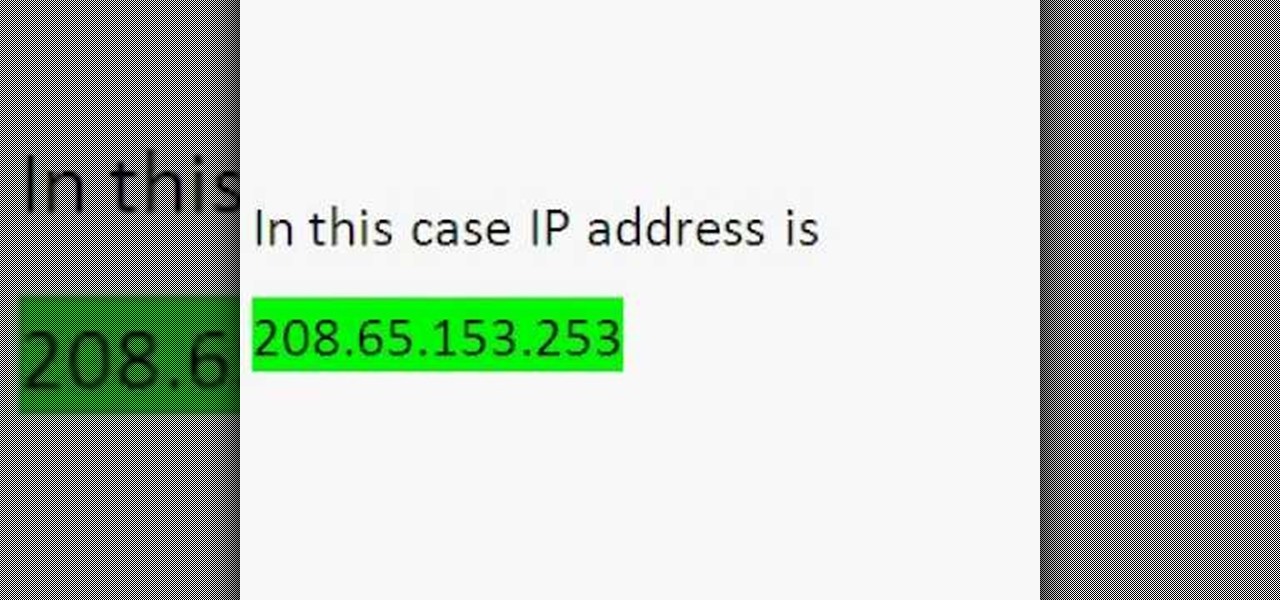
Wondering how to find the Internet Protocol address of a website?

Need internet but don't want to pay? Well, try lusting of those around you by picking up their Wi-Fi signal. Live out in the boondocks? No problem… if you have an old satellite dish laying around.

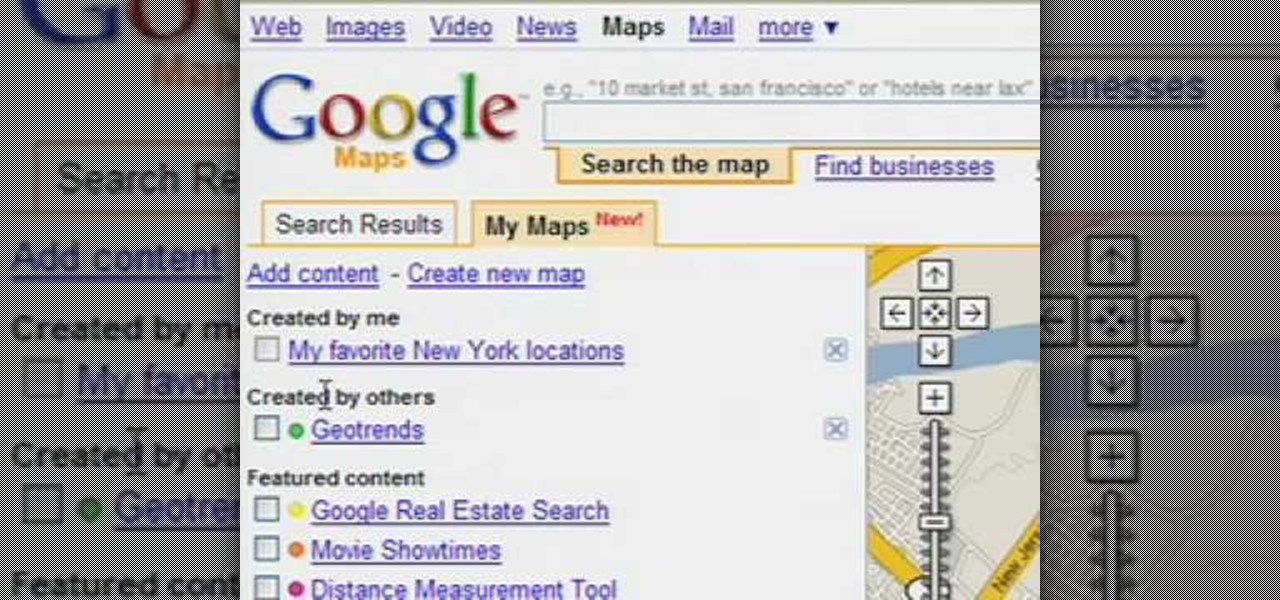
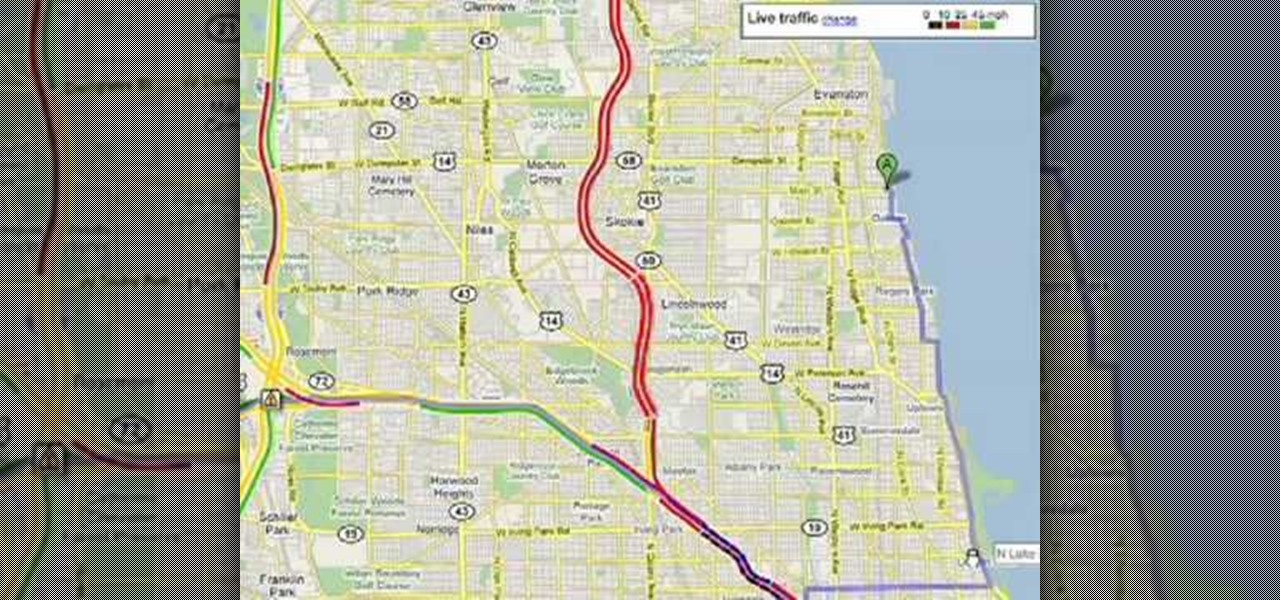
Customize your directions on Google Maps. Drag and drop the default directions to your preferred roads or highways, get walking or public transit directions, route around traffic, or add multiple stops on your way.

Customize your directions on Google Maps. Drag and drop the default directions to your preferred roads or highways, get walking or public transit directions, route around traffic, or add multiple stops on your way. Print directions with Street View, photos included.

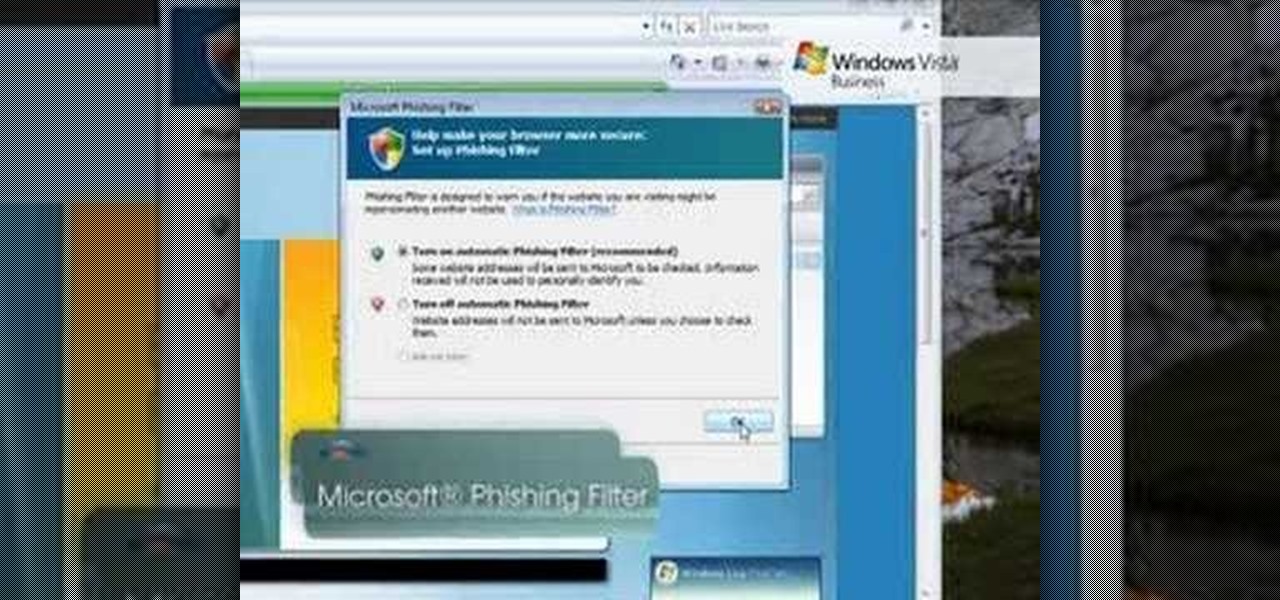
Check out this video tutorial to learn more about the Phishing Filter on Internet Explorer 7. Web browsers such as Microsoft's Internet Explorer 7 have become an important part of the computing experience for business and home users around the world. With the popularity of web browsers for accessing information, running programs, and even accessing corporate resources, the browser has become a target for viruses, malware, and phishing schemes that present real dangers to Internet users. Inter...

Needless to say, we're talking minor traffic violations. If you've just led the cops on a high-speed chase down the freeway, you're on your own.

Play remotely with all your friends, stream videos and music from the Internet or even check your Facebook and email - all with your PSP. The PSP has Internet capability, but not every network will be available to you at all times. Here is how you can hack any wifi connection with your PSP.

The internet has created amazing new standards for how closely information can be followed. If you want a portable analog unit that will monitor one important piece of online info continuously and have some DIY electrical knowhow, watch this video. It will show you how to use an Arduino Ethernet Shield to make an internet meter to monitor email, stocks, and other online info on a simple analog display. You will need to know some PHP to make this work.

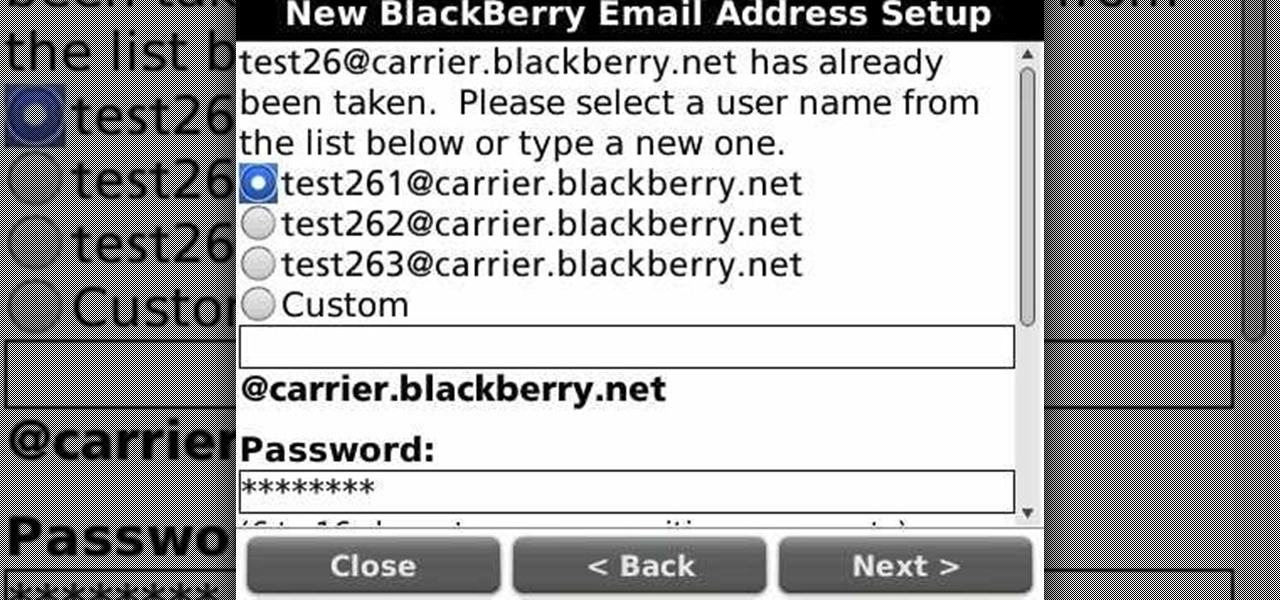
Learn how to create a new BlackBerry Internet service email account on a BlackBerry device running version 5 of the BlackBerry OS. This clip will show you how it's done. Whether you're the proud owner of a BlackBerry smartphone or are merely considering picking one up, you're sure to be well served by this video guide. For detailed information, including step-by-step instructions, take a look.

The internet has been a massive financial windfall for millions of people around the world, and it can be for you as well! There are a lot of ways to make money on your couch by using the internet, and this video will show you five great ways to do it! These include making websites and forums, advertising, and gambling. If you're hard up for cash, give it a whirl!

In this video tutorial, you'll learn how to add WiFi Internet connectivity to a normal Sprint Palm Pixi smartphone with a quick and easy radio board (radioboard) swap. For more information, including detailed, step-by-step instructions on how to add WiFi capabilities to your own Palm Pixi phone, watch this hacker's how to.

Cookies serve their purpose in Internet Explorer 7. They let the browser know which sites you have visited so you don't have to get security prompts every time you back to them. However, they can also slow down your browser, which can be frustrating. This video will show you how to delete cookies in Internet Explorer and browse faster.

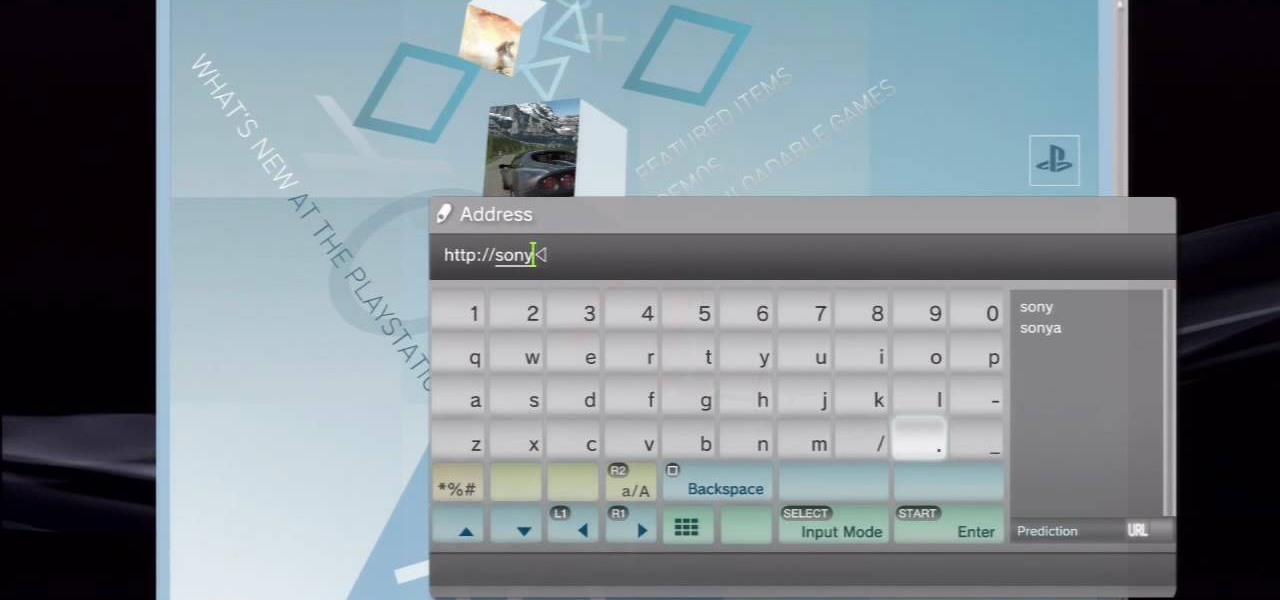
This video tutorial was created by SCEA for Sony PlayStation fans and readers on how to use their PS3. Learn how to surf the web on your PS3. Once you learn the ease of browsing the Internet on your PlayStation 3 with the Internet Browser, you won't be able to stop.

They are after you from all over the globe. Looking for ways to exploit you. Ways to hurt you. Not political terrorists, but rather "info terrorists." Each month thousands of websites get hacked into and have hidden links inserted into the pages by people wanting their spam sites to rank highly in the search engines.

Just because the internet renders you virtually anonymous does not mean social customs should be ignored. Just like in the outside world, there is etiquette that should be obeyed if you want to be treated as a friend rather than an annoyance online. In this how to video, Proper Ollie teaches you how you can have proper internet etiquette in social networking forums.

Have you maybe been eyeballing some things you'd rather other people didn't know about? Clear your Internet history and leave your anxiety behind.

So you want to know what that person who is always on their phone is up to? If you're on the same Wi-Fi network, it's as simple as opening Wireshark and configuring a few settings. We'll use the tool to decrypt WPA2 network traffic so we can spy on which applications a phone is running in real time.

Sniffing packets over a network is an easy way for hackers to gather information on a target without needing to do much work. But doing so can be risky if sniffing packets on an untrusted network because a payload within the packets being captured could be executed on your system. To prevent that, Sniffglue sandboxes packet sniffing to provide an extra layer of security.

It only takes a few commands to manipulate a MacBook's secure HTTPS traffic and pluck login passwords out of the encrypted data. Let's take Facebook and Gmail hacking to the next level by intercepting Safari and Google Chrome web traffic in real time.

If you're using a mobile device, it's a pretty safe bet that your apps are sending lots of information back and forth from their servers. To make sure there is no inappropriate data collection going on, it's worth setting up a web proxy to spy on this traffic, so you know exactly which apps are "phoning home" and when.

Whether due to spotty cellular reception or just data that you want to save, popular navigation apps like Google Maps and Waze offer an offline feature that lets you navigate from one location to another in the absence of internet service. Apple Maps also lets you use its service offline on your iPhone, though the feature is not as straightforward as it is on its competitors.

After numerous scandals like the Equifax data breach and the 2016 US election, cybersecurity has become a significant issue for Americans. Unfortunately, anytime we use our devices, we're open to a cyber attack — especially when we browse the web. However, there are ways that we can make it harder for hackers and data miners.