As mobile devices become more and more popular, service providers have unfortunately resorted to capping data. What this means is that, depending on the plan you have with your ISP, you could have limits placed on how much data you can use for a set period of time. Once you've hit the limit, your ISP could drastically slow down or throttle your internet speed or charge you outrageous overage fees.

I saw a video that Kurz Gesagt made about the Fermi Paradox, and I liked how the video was made, so I looked up what else they had, and came across this:

It's been a while when the major web browsers first introduced HTTP Strict Transport Security, which made it more difficult to carry Man In The Middle (MITM) attacks (except IE, as always, which will support HSTS since Windows 10, surprised?).
This tutorial video will show you how to download any video from internet where download link may not be absent. We are showing the technique for chrome browser. You have to install an add-on to download any video. This add-on has a Firefox version also. See the video and Employ the technique in your browser.

Now most of the free email providers allow upto 25 MB of file attachment. But we need more. This video will help you how to send or transfer big files upto 2GB over internet without any cost. Watch the video and follow all the steps to do it yourself.
This video will show you how to control and limit data usage in your windows 8 phone. You may want to restrict your data usage and want to set limits for apps also. If you set your usage limit internet will stop automatically after reaching the limit.

This video will help you how to set browser home page. Video: .

How to Make Round Braid with EIGHT strands. It's easy to make and suitable for kids and beginners projects. This plait can be used for making nice bracelet or shoelaces may also be useful for hairdo. I couldn't find a Video tutorial that was like this in the internet, so this is a exclusive/first one. Hope that you enjoy.

Need to clear you cache? This guide details how on any web browser (Chrome, Internet Explorer, Firefox, Opera, Safari, Internet, and Dolphin) for any platform (Windows, Mac OS X, iOS, and Android). What Is the Cache Exactly?

BitTorrent—corporations hate it with a passion, but the people love it. The notorious file-sharing protocol was responsible for 36.8% of all upstream Internet traffic last year, as well as 10.3% of all traffic.

People are always looking for ways to save money, and for the most part, saving money and cheating the system are synonymous when it comes to things like free internet access. Practically every new gadget is capable of connecting to the web, which means more and more people are looking for ways around those hefty internet bills.

This video and overally the whole channel behind it, is owned by the most famous cwalker around the internet. Most of his recent videos have upped contrast/brightness which gives the light and very likeable feel. I'm sure you will love him!

This video includes instructions on how to get your PlayStation Portable (PSP) onto the BGSU wireless network.

In 1998, a Beechcraft Baron was following a Boeing 757, with approximately 3 to 5 miles separation. Air Traffic Control warned the Baron pilot three times with the phrase the phrase pilots hear on a regular basis: "Caution. Wake Turbulence".

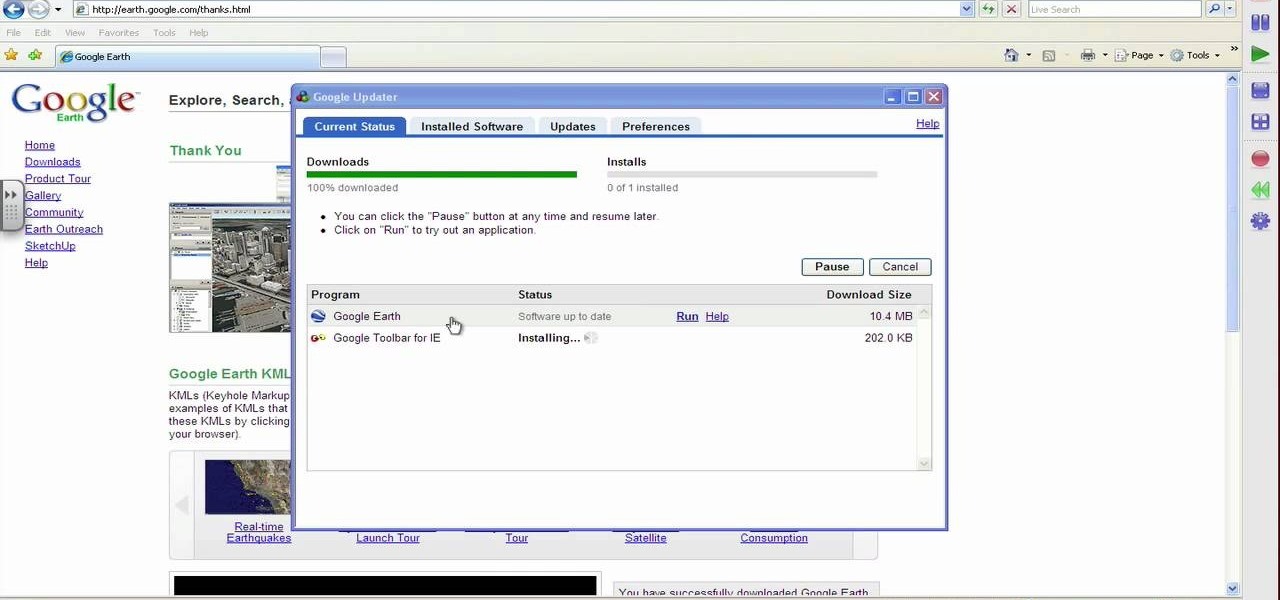
This video shows PC users how to download Google Earth. To do this, first open up an internet browser (Internet Explorer, Mozilla Firefox, etc.). Go to the Google homepage and type 'Google Earth' into the search box. Press enter. Click on the link at the top of the list, which should be named 'Google Earth 5.0'. Click on the blue bar that says 'Download Google Earth 5.0' on it. A page will load with the terms and conditions of using Google Earth. Read them, then click 'Agree and Download'. A ...

Catching sight of a hummingbird floating from flower to flower is one of those rare gifts from nature. In this quick and easy guide, use a little bit of science and learn how to make a hummingbird feeder that will attract all the birds in the yard.

For those of us living in any of the 49 states other than New York on Thanksgiving Day, checking out the famous Macy's Thanksgiving Day parade at New York is more a dream than reality. While the parade airs every Thanksgiving on television, it's also possible to catch the festivities online.

In this video you are shown how to use proxies and why they are important. Proxies are useful because they shield you and make you anonymous over the internet, it also prevents websites from logging your IP address. To see how important it is to prevent this go to whatismyip.com. It will show you your IP, click on it and go to 'look up'. It will show you all the personal information that can determined from your IP address. The easiest way to proxy are VPN's, which stands for virtual private ...

In this video the instructor shows how to check if your computer has a home group setup or setup one if required. Home group is Microsoft's new way of making networking easier with computers. They allow you to share documents, pictures, videos and all kinds of media between computers that are a part of a home group. Go to the start menu and go to Control Panel. In the Control Panel select the Network and Internet link. Now in the Network and Internet window select the Home group. In this page...

This is a Restaurant City 3 in 1 Hack (Working From 12th May 2009).

Safe motorcycle riding requires knowledge and skill. Testing two-wheel vehicle operators is the best measurement of the skills necessary to operate safely in traffic because people often overestimate their own abilities.

Driving around and notice an accident the road keeping you from getting where you need to go? Well, you're in need of a GPS navigation system. Check out this video tutorial on how to Use media functions on a TomTom Go 930 Traffic navigator device. You'll see how to use the GPS system in details and see all of the key features of the Go 930 TomTom, like playing music, listening to audiobooks, and watching videos.

Driving around and notice an accident the road keeping you from getting where you need to go? Well, you're in need of a GPS navigation system. Check out this video tutorial on how to use the TomTom Go 930 Traffic GPS navigator device. You'll see how to use the GPS system in details and see all of the key features of the Go 930 TomTom.

The ability to browse the web in coffee shops, libraries, airports, and practically anywhere else you can imagine is more than convenient, but convenience has risks. Using public Wi-Fi allows others to spy on you easily. Even your own internet service provider can see every website you've ever visited. Don't fall into the trap of protecting your identity, data, and devices after it's too late.

These days, everything is connected. No, really — we mean everything. Your phone, your smart speaker, and even appliances like stoves and refrigerators can be connected and communicate with one another. Welcome to the Internet of Things, the start of our interconnected future. It's projected by 2027 that there will be more than 41 million internet-connected devices in use around the world.

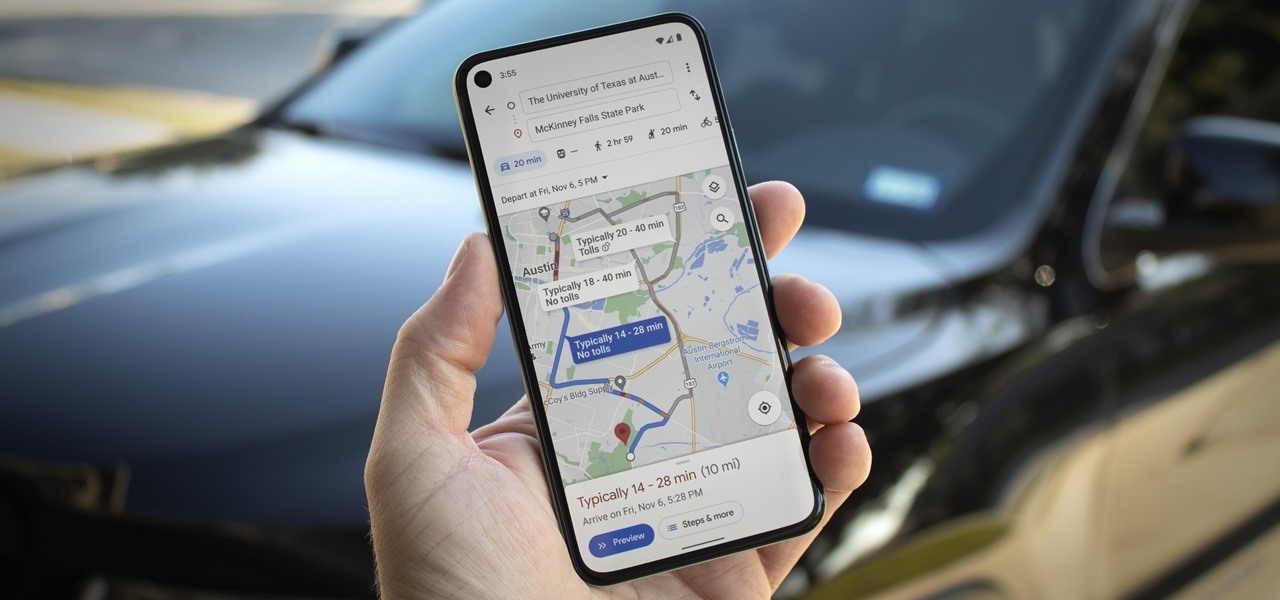
If you're in the market for a new house, how do you know what your commute would be like if current traffic is unseasonably low? Or if you're considering a new job across town and want to weigh the pay raise against the extra time stuck in a gridlock, how do you measure the discrepancy? Google Maps can help.

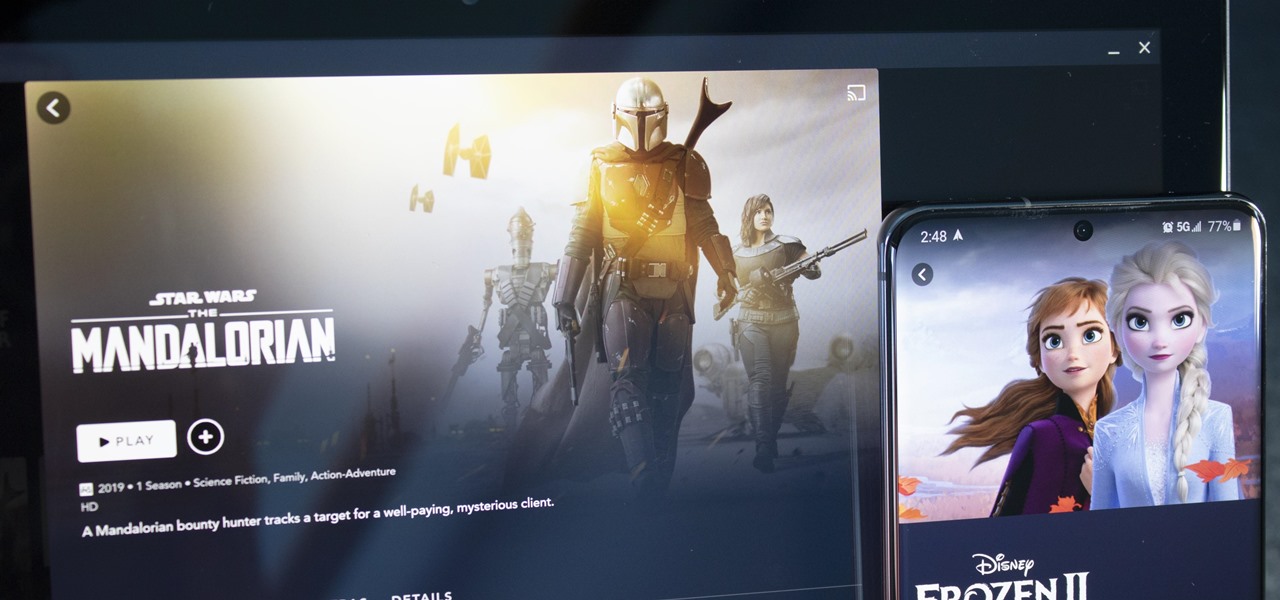
With shows like "The Mandalorian" and movies like "Frozen 2," Disney+ has quickly become a must-have streaming service. However, with Netflix, Amazon Prime Video, and Hulu, adding another subscription-based service can become expensive — but there are ways to trim down the cost.

You're reading this so you're probably already safely huddled up in your house or apartment, watching as the entire planet grapples with the unfolding coronavirus health crisis. But unlike some others, you're lucky enough to already have a couple of weeks of supplies and now it's just about what you can do to entertain yourself and your family as you weather the current situation.

You may not have thought of dorks as powerful, but with the right dorks, you can hack devices just by Googling the password to log in. Because Google is fantastic at indexing everything connected to the internet, it's possible to find files that are exposed accidentally and contain critical information for anyone to see.

If you find yourself with a roommate hogging limited data bandwidth with video games or discover a neighbor has invited themselves into your Wi-Fi network, you can easily take back control of your internet access. Evil Limiter does this by letting you control the bit rate of any device on the same network as you, allowing you to slow or even stop data transfer speeds for them completely.

When joining a new network, computers use the Address Resolution Protocol to discover the MAC address of other devices on the same network. A hacker can take advantage of ARP messages to silently discover the MAC and IP address of network devices or actively scan the network with spoofed ARP requests.

Apple officially released iOS 12 to everyone on Sept. 17, and while the new iPhone XR, XS, and XS Max will come with the software by default, you have a choice on whether or not to update your current iPhone model from iOS 11. There are a lot of tempting features to want to update right away, but there are also some compelling reasons to wait it out and install at a later time.

Reconnaissance is the phase of an attack where a red team or hacker designs a strategy based on the information they can learn about the target, as well as what the available attack surface looks like. These scans can take time to discover relationships, but Raccoon OSINT scanner coordinates multiple automated scans to produce invasively detailed reports on a target with a single command.

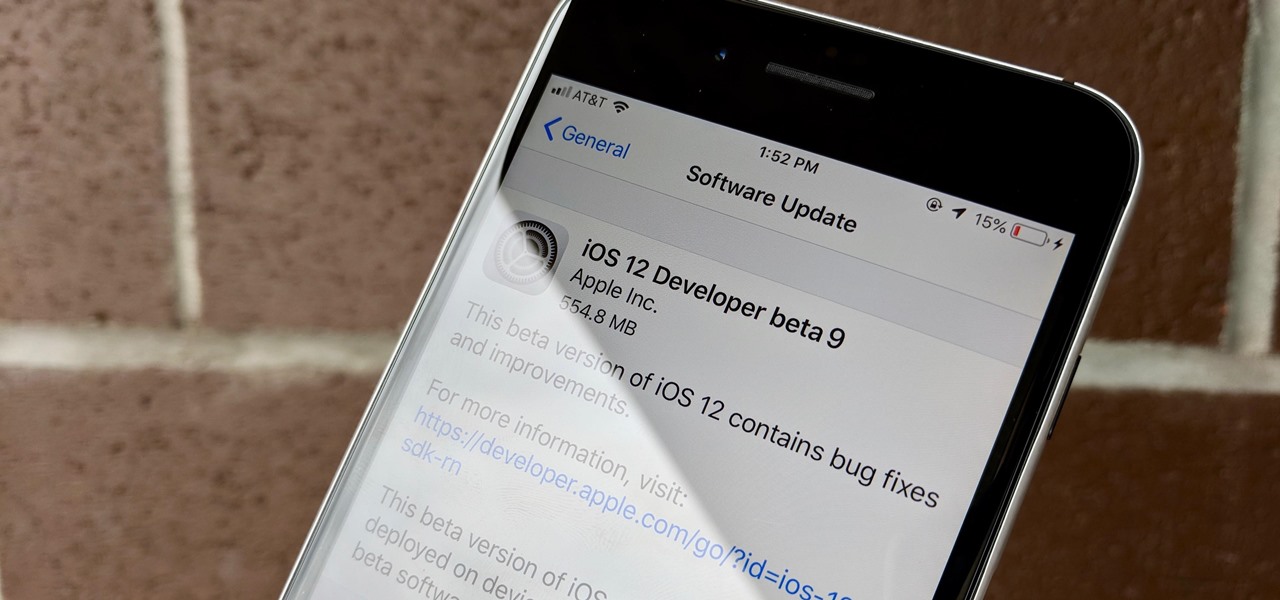
Can't say we didn't see this coming — Apple released iOS 12 public beta 7 on Monday, August 20, the same day it seeded the ninth version of the beta to developers. While the two betas may have different names, public beta 7 and dev beta 9 are virtually identical, so public testers shouldn't feel as though they are missing out.

Apple released iOS 12 beta 9 to developers on Monday, August 20. The company seeded the update just five days after releasing dev beta 8 to testers, itself a quick replacement for the problematic beta 7. This update was followed closely by public beta 7, confirming Apple's new same-day release schedule for both developer and public betas.

The Watch Dogs video game series came out in 2014, enamoring audiences with the idea of a seemingly magical smartphone that could change traffic signals, hack web cameras, and even remotely control forklifts. This may sound like science fiction, but The Sonic uses a customized flavor of Kali Linux to allow you to unleash the power of Kali from any smartphone — all without the need to create a hotspot to control it.

Well, well, well. Uber, we knew you were investing a ton of money into creating self-driving taxis and flying cars, but what we didn't know is that you were already testing out your driverless vehicles on the streets of New York City.

Welcome back, my novice hackers! In this series, we have been exploring how a forensic investigator can find evidence of illegal or illicit activity. Among other things, we have examined the registry and prefetch files for artifacts and have done some rudimentary forensic analysis. For those of you who are seeking career as a forensic investigator or security engineer, this can be invaluable training. For hackers, it might be life-saving.

Welcome back, my greenhorn hackers! Over the years, I have written many articles here on Null Byte chronicling the many the hacks of the NSA, including the recent hack of the Juniper Networks VPN. (By the way, my speculation in that article has proven to be correct. The NSA did embed a backdoor on those devices.)