In-N-Out Burgers on the West Coast is famous for their not-so-secret and secret menus, along with their cheap, no-fuss burgers. Pre-internet, you felt like you were actually part of a small, select club when you knew what secret menu items to order.

Welcome back, my budding hackers! Recently, I showed you how you could exploit the widely disseminated OpenSSL vulnerability that has to become known as "Heartbleed". Although the world has known about this vulnerability for over a month now, it will likely take many more months—or even years—for everyone to close this vulnerability.

This time it's serious. Really. The largest web security vulnerability of all time went public on Monday, April 7th, 2014, resulting in widespread panic throughout the Internet as system administrators scrambled to secure their websites from the OpenSSL bug known as Heartbleed.

You've seen the Samsung Fingers and the Emoji Translator, and I know you spent a good part of the day catching Pokémon, but now that April Fool's Day is officially upon us, the flood of gags has reached a tipping point. Here's the best of what we've seen today.

I have Verizon, America's largest 4G LTE network, as my cell service provider, but there are times when I find myself with a pretty shitty signal, rendering my upload and download speeds substantially slower than usual.

There are several ways to get around location restrictions on subscription sites like Netflix and Hulu using apps, extensions and proxies, but they tend to only work on laptops and computers. Users who want to access content from mobile devices and gaming consoles are usually out of luck.

It's officially the holiday season, which means everyone will soon be traveling home to spend time with loved ones. And anyone who has any knowledge whatsoever of computers knows what else that means—family members left and right asking you to fix their various technical woes.

Welcome back, my greenhorn hackers! Continuing with my Wi-Fi hacking series, this article will focus on creating an invisible rogue access point, which is an access point that's not authorized by the information technology staff and may be a significant security vulnerability for any particular firm.

We all know about PRISM. The Surveillance Program allowing the U.S Government to access private user information. Such as, Google Searches, Tweets, Facebook Posts, Private Images, and other private user data. "Hiding" yourself can be very difficult, but it is possible. I'm here to show you How to Become Anonymous & Browse the Internet Safely.

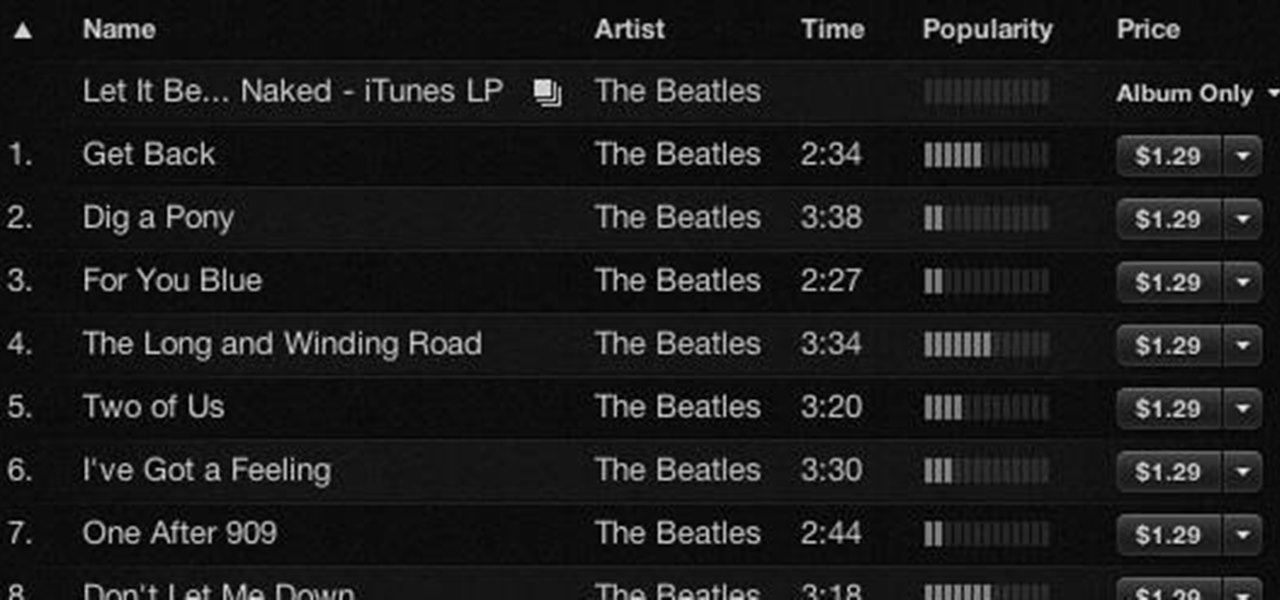
If you weren't aware, all music purchased online through iTunes, Amazon, and other digital audio providers have information embedded that can be used to identify the buyer and transaction of the digital music file. This may seem like something you should be disclosed about in their terms of use, but it's not.

Are you constantly traveling? Well, as a Hilton HHonors member, you can enjoy special treatment at all of their hotels and resorts. It's free to register, but the difficulty lies in climbing up their membership level. To reach Gold elite status, Hilton HHonors requires that you have a minimum of 20 stays, 40 nights, or 75,000 base points—all in one year. While this may very will be easily attainable for those with jobs that revolve around traveling, it's almost damn near impossible for the re...

The PlayStation 3 is a sweet gaming system, and even though Blu-ray discs didn't really live up to all the hype and there is still no HBO GO app available, I love my PS3. One of the coolest things about it is that you can customize it to look however you want. One of the most common ways to do this is by changing the wallpaper, but most people use their computers to transfer wallpaper images over.

For anyone who uses computers regularly, the screen can become cluttered with different windows, tabs, and applications in no time. One solution to that mess is dual monitors, which allow users to be more organized and divide their work into two halves. The problem is that not everyone is fortunate enough to have access to more than one monitor.

An internet connection has become a basic necessity in our modern lives. Wireless hotspots (commonly known as Wi-Fi) can be found everywhere!

When you're at work or in class, there's nothing more annoying than sites that automatically play media. One minute you're happily distracting yourself, and the next, you're scrambling to hit pause while everyone stares at you. Not to mention now your boss knows you're slacking off.

Learn how to connect a DVD or Blu-Ray player to the Internet. You'll see the simple steps on how to connect a DVD or Blu-Ray Player to the Internet using the powerlines in your home with Powerline Adapters from Actiontec Electronics.

Learn how to connect a DirectTV set-top box or DVR to the Internet. You'll see the simple steps on how to connect a Set Top Box or DVR to the Internet using the power outlets in your home with MegaPlug Powerline Adapters from Actiontec Electronics.

Learn a little bit about technology with help from EMBARQ. Watch this how-to video tutorial on installing your 2Wire Gateway for EMBARQ High-Speed Internet. This will cover exactly how to install your EMBARQ 2Wire Gateway modem for Internet. This is the complete process step-by-step from box to connected online.

You can hack into nearly any Facebook or Flash based game on the Internet - no cheat codes or special strategies needed. All you really need is the free game hack program Cheat Engine, and a compatible browser like Firefox.

When you clean the carpet in your home or apartment, it seems like that dirt just comes right back the next day. It's never really clean. Well, that could be changed with a deeper clean. Deep-cleaning your carpet can offer benefits including getting rid of dust mites and allergens. Not to mention dirt.

In this video tutorial, viewers learn how to record songs on the Internet without a microphone. Begin by putting the sound control icon into the application bar. Then go to Volume Control and click on Properties. Click on Recording and then select all the recording options. Now close the window. Then select the mixage on the volume control, but do not close it. Then open the sound recorder in the Start menu and find the song that you want to record on the Internet. Play the song and click on ...

Delete Your Cookies and Browsing history.

This tutorial video demonstrates how to play GBA emulator on a PC with a friend through the internet. Follow these instructions, and get started! Very easy.

Watch this video to learn the basics of Google Toolbar for Internet Explorer.

This video demonstrates how to use the Internet on your Sony PSP. Get the most out of your Sony PSP.

It takes talent and training to drive a semitrailer. See if you have what it takes to operate one of these rigs on the open road.

With everything the last year has thrown at us, the odds are good that you've had to start working from home, complete with all-new challenges both for you and the technology you use.

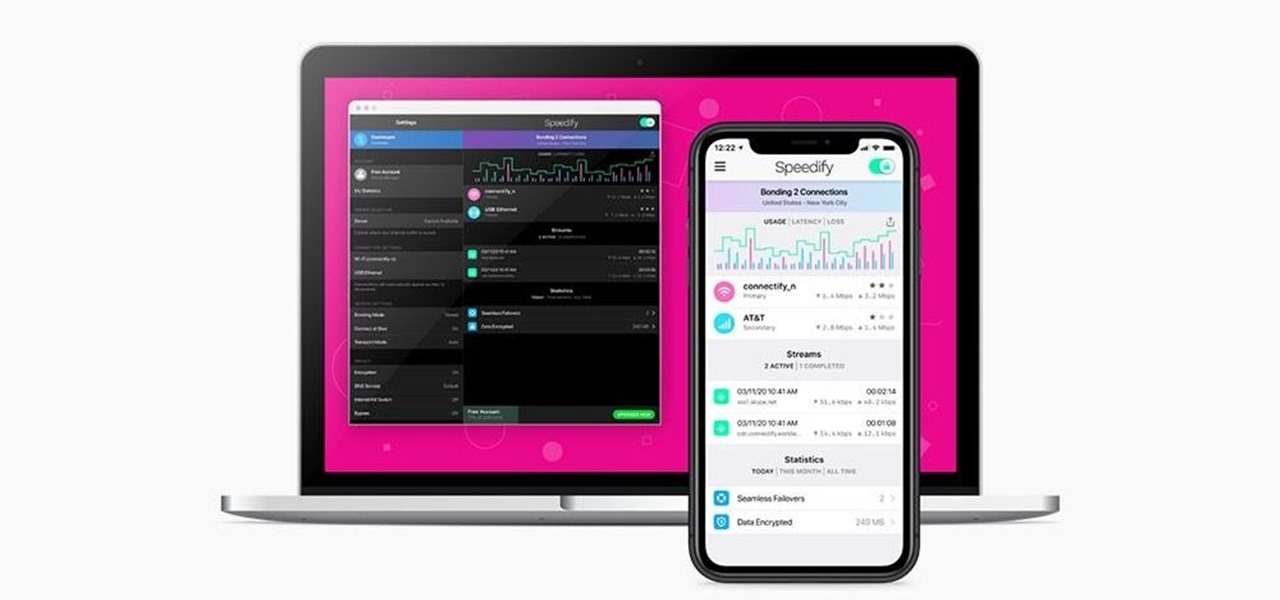
Using a virtual private network (VPN) is one of the safest ways to ensure your identity and data remain secure. Choosing one from the hundreds of services that now exist is another story. How do you tell which VPN truly provides the best protection at a great price?

There are many considerations to make when choosing a web hosting plan. Storage space, performance, security, and reliability all matter. The cheapest option isn't always the best idea.

Ever a hacker can have their own business that goes beyond cashing in on profitable bug bounties. With the right skill set and certifications, an ethical hacker could build a cybersecurity firm, become a penetration testing for hire, or even just consult on preventive measures to defend against black hats. But learning how to start and grow a business is rarely easy.

Long before the HoloLens or the Magic Leap One, a California-based team of independent filmmakers envisioned what the future of augmented reality might look like.

What if you could easily visualize which access point every Wi-Fi device nearby is connected to in a matter of seconds? While programs like Airodump-ng can intercept this wireless information, making it easy for hackers to use and understand is another challenge. Fortunately, a tool called Airgraph-ng can visualize the relationships between Wi-Fi devices from only a few seconds of wireless observation.

If you want to get started sniffing Wi-Fi networks, you usually need to start with a wireless network adapter. But thanks to a Wi-Fi sniffing library written in Arduino and the ultra-cheap ESP8266 chip, you might not need one. For less than $10 in electronics, you can build a tiny Arduino Wi-Fi sniffer that saves Wireshark-compatible PCAP files and fits anywhere.

An augmented reality system developed by Lyft might make it less awkward for drivers to figure out who they are supposed to pick up.

Nmap is more powerful than you know. With a few scripts, we can extend its functionality beyond a simple port scanner and start to identify details about target servers sysadmins don't want us to know.

The HoloLens team is finally beginning to realize that to truly engage the mainstream, augmented reality needs to make its way out of the lab or factory floor and onto the streets.

Accused of violating whistleblower and age discrimination laws by its security director, Magic Leap has taken an internal situation to the US District Court to clear its name of the allegations.

The internet is constantly under siege by bots searching for vulnerabilities to attack and exploit. While conventional wisdom is to prevent these attacks, there are ways to deliberately lure hackers into a trap in order to spy on them, study their behavior, and capture samples of malware. In this tutorial, we'll be creating a Cowrie honeypot, an alluring target to attract and trap hackers.

On Thursday, Snapchat opened up its walled garden of World Lenses to the masses of creators with the launch of Lens Studio.

PowerShell Empire is an amazing framework that is widely used by penetration testers for exploiting Microsoft Windows hosts. In our previous guide, we discussed why and when it's important to use, as well as some general info on listeners, stagers, agents, and modules. Now, we will actually explore setting up listeners and generating a stager.