After finding and monitoring nearby wireless access points and devices connected to them, hackers can use this information to bypass some types of security, like the kind used for Wi-Fi hotspots in coffee shops, hotels, and in flights high above the ground. By swapping their MAC address for that of someone already connected, a hacker can bypass the MAC filter and connect freely.

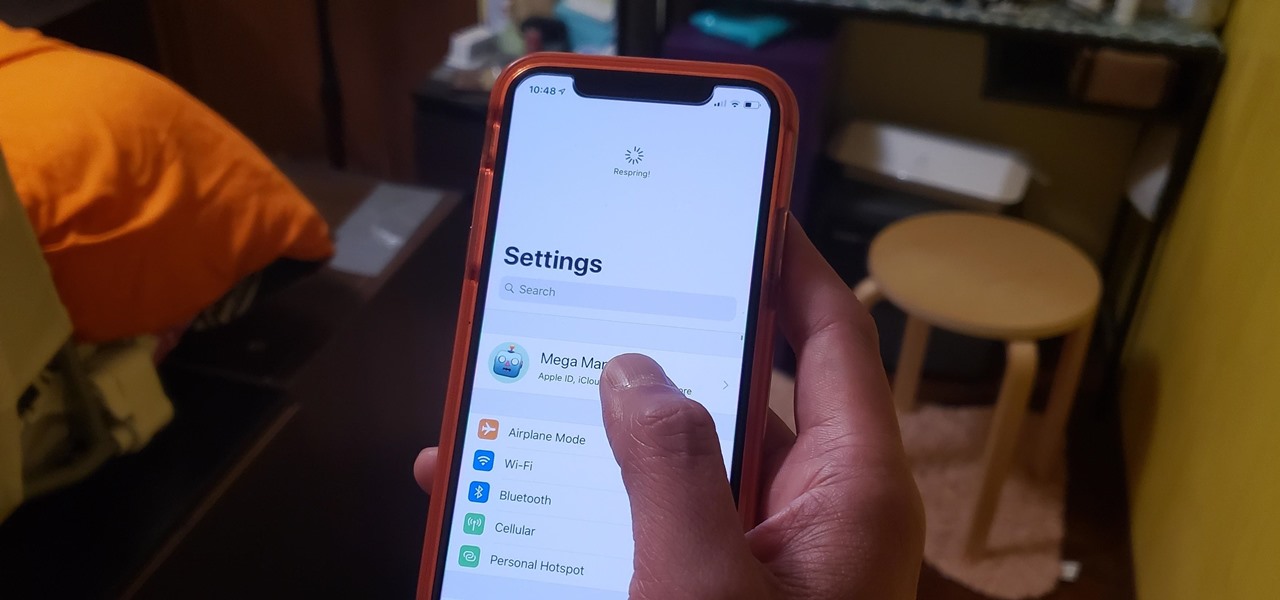
After recently being in the news for collecting PII (personally identifiable information) for analytics and after-sales support, OnePlus has another security problem. An individual going by the name Elliot Alderson discovered an app in OnePlus devices that can enable root access with one command.

Samsung's latest flagship devices—the Galaxy S7 and S7 edge—both sport an interesting new feature called Always On Display, or simply AOD. When enabled, this feature keeps the clock, date, and other bits of information visible at all times—even when the screen is off.

There are few things more annoying in life than getting interrupted—especially when you're in a groove, jamming out to your favorite song. If we can all agree on that sentiment, then why is it that our phones mute the music we're listening to for a few seconds whenever a notification comes in?

Ideas can be a fleeting thought, just like a shooting star that appears and disappears within a brief moment. So when you're inspired and have an awesome idea, it's important to jot it down as soon as possible, otherwise it may vanish from your memory for good.

In case you didn't know, Android has an awesome hidden settings menu called "Developer options" that contains a lot of advanced and unique features. If you've ever come across this menu before, chances are you just dipped in for a minute so that you could enable USB debugging and use ADB features.

With our internet-connected devices growing in number by the year, it would be nice if they could somehow all be interconnected. This is becoming commonplace for our tablets, smartphones, and laptops, but our media streaming boxes still seem to be isolated in their own little worlds.

These days, using the power button to lock your Android seems a little old-fashioned. Thanks to third-party apps and mods, you could seamlessly lock your device using a double-tap, a swipe, and even gravity, or you could just throw it in your pocket, all of which help prevent additional wear and tear on your power button. Now, we've got another method for you—just shake.

Chromecasts can make for some fun nights. Whether you're setting up a collaborative YouTube watch list, letting everyone add to a giant party playlist, or playing games like Cardcast and Big Web Quiz, Google's streaming media stick is a hit by all accounts.

Samsung catches a lot of flak for all of the "bloatware" it preinstalls on its Galaxy line of devices. Many users complain that "TouchWiz," Samsung's custom Android skin, causes lag with its overabundance of features. But some of these features can actually be pretty handy, like Multi-Window Mode or Milk Music.

Ubuntu isn't just a cool sounding name, but pegs itself as the world's favorite free operating system. It gained its popularity for being lightweight, fast, and visually appealing, and now that great look and speed can be placed right on the lock screen of your Samsung Galaxy S3.

International, T-Mobile, and Verizon customers all share something in common—their carriers provide unlocked Wi-Fi tethering for free. Of course, you still pay for the data used, but they don't charge you extra simply for using your Samsung Galaxy S4 as a wireless hotspot.

Latest video files come in different formats. Some of the programs and devices are compatible with only a few formats and this requires you to convert files between different formats frequently. Lot of streaming files on the internet are in FLV or MPEG format and to use them on your portable devices you may need to convert them into MP3. To do this you will be needing a application called VLC media player. VLC is the most powerful open source medial player which almost supports all of the vid...

This video will show you how to tether your Samsung Messager 2, (the MetroPCS phone) to your PC to use as a modem for internet access. This will allow you to use your cell phone as your internet connection point, meaning you'll connect to the net for the cost of your cell phone's data plan. You will need your Samsung USB cable, a PC with Windows 2000 or higher, all current drivers for your phone and PC, and you will also need to head here to get the Samsung PC Studio program. This is part 1 o...

Need a hand figuring out how the FaceTime video phone call application works? This home-computing how-to from the folks at MacMost will help sort you out. To learn more, and to get started making video calls to iPhones and other FaceTime-enabled iOS devices from your Mac, watch this video guide.

In this clip, learn how to use PDA Net to tether your rooted Droid 3G smartphone to a WiFi network. By tethering your device, you will be able to use it as a portable, wireless modem for anything from other phones to computers to hand held gaming systems. Anything that is WiFi enabled can be tethered to your mobile network with this hack.

If you have a new Land Rover and a Bluetooth enabled cell phone, you can pair them together for simpler in-car calling. This method of calling is safer and easier than holding a handheld or fumbling with a headset. Follow along with this video and connect your mobile device to the car for use anytime.

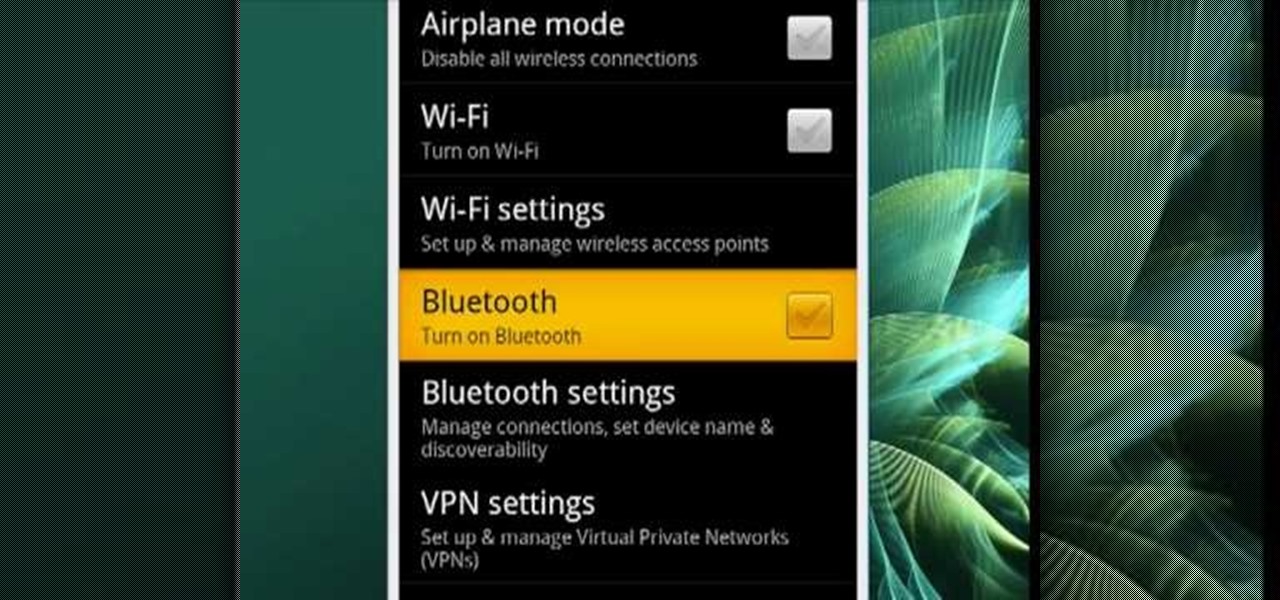
Enable Bluetooth on your Android smartphone. One of the salient advantages of a Google Android smartphone over, say, an Apple iPhone, is the inherent extendibility of the open-source Android mobile OS. There are a seemingly infinite number of settings to tweak and advanced features to discover and use. This free video tutorial will show you how to turn on Bluetooth on your Android device.

A below elbow arm amputee demonstrates the device he uses in the gym. He shows you how to use a prosthetic for working out at the gym when you've suffer a limb amputation. This video is very helpful in describing utilities available for enabling individuals with amputations to workout or get around and function in a gymnasium setting. This is a video that addresses adaptive equipment for handicapped or disabled people.

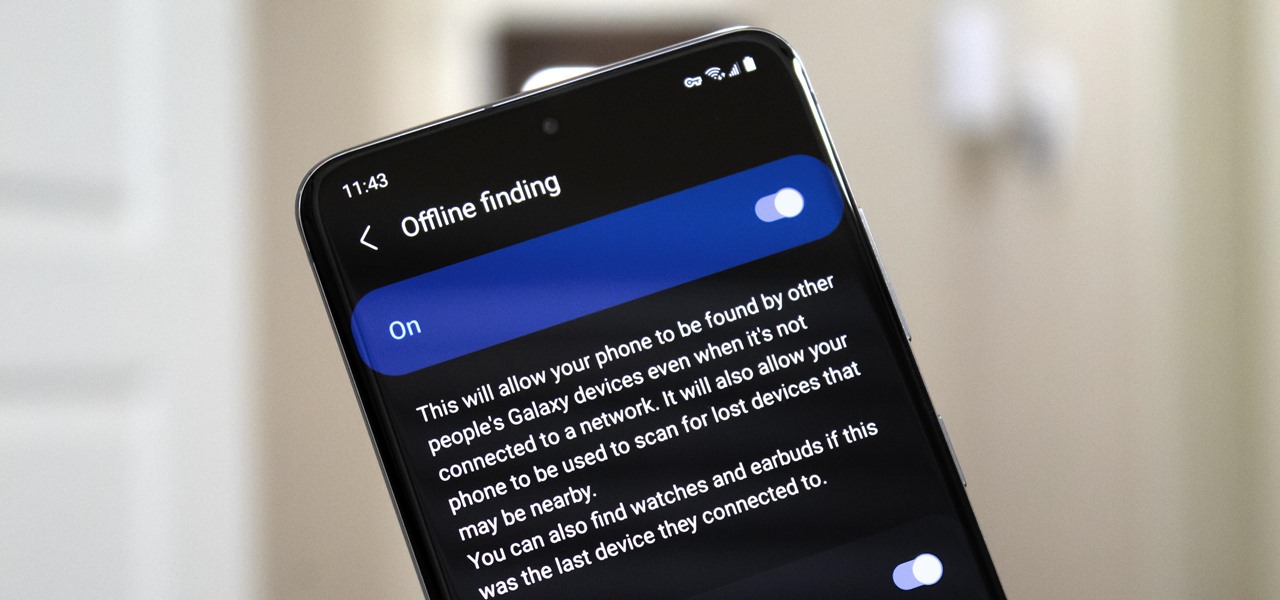
Nowadays, even the dumbest thieves know that the first thing you should do after you steal a phone is turn on airplane mode. Not only does this make it harder for police to track the phone through cell tower triangulation, but it also disables security features the person you stole it from may have implemented — for instance, Samsung's Find My Mobile service.

One of the main goals of Google Wifi (and Nest Wifi after it) is to make managing your internet connections as simple as possible. A great example of this is how easy it is to prioritize one device and allot it more bandwidth when your network is bogged down with other traffic.

One of Android's biggest strengths relative to iOS is how simple it is to sideload apps that aren't on the official app store. Rather than having to sign IPA files or tell your phone you trust a developer every two weeks, you can just enable a setting and be done with it.

Restarting your iPhone can cure software glitches, but it should only be done as a last resort if your device has a semi-tethered jailbreak, because it will disable any tweaks you've applied. Luckily, your jailbroken iPhone has a faster alternative to rebooting to help you troubleshoot and make changes on the fly.

Security-minded users can reduce the risk of phishing by enabling Advanced Protection on important Google accounts, requiring a U2F security token to log in. Using these keys isn't intuitive on most popular smartphone platforms, and you can find yourself locked out if you don't plan ahead. You'll need to learn and practice using U2F keys on your device before enabling this layer of security.

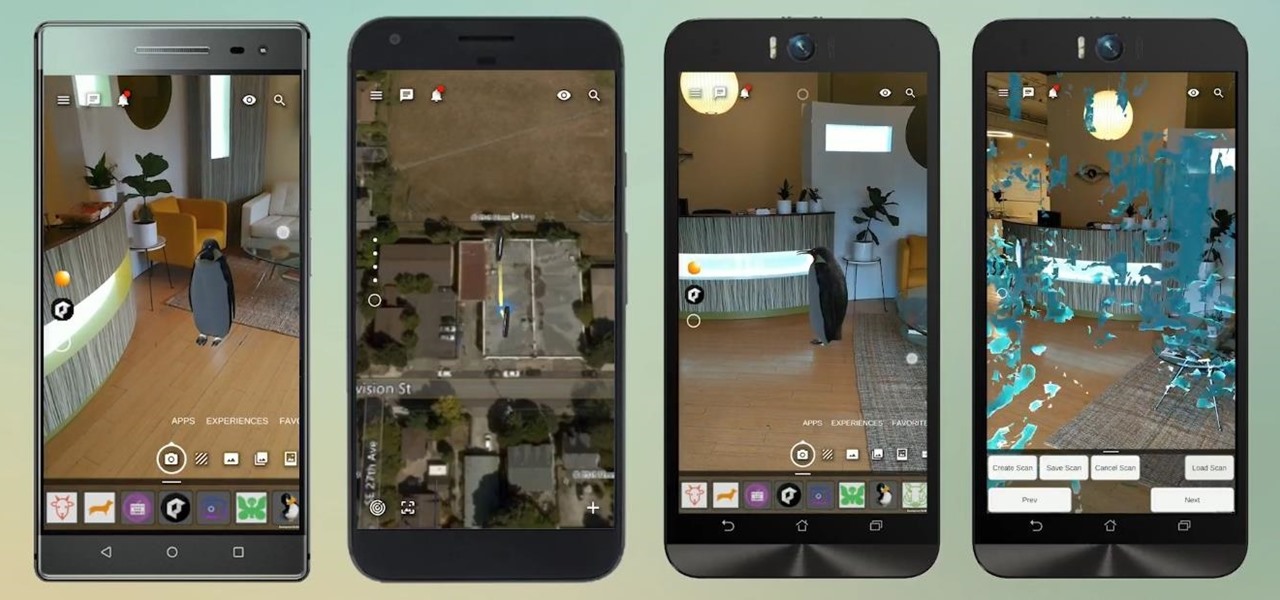
Unsurprisingly, Google wants to be the caretaker for augmented reality on the web, and its latest move in this endeavor is a 3D model viewer prototype called Article that's designed to work across all web browsers.

Google's new Pixel and Pixel XL flagships are some very powerful smartphones, but as with any high-tech gadget, they're only as capable as the user allows them to be. So if you're a proud new Pixel owner, it's time to bone up on a few new features to help get the most out of your device.

Much like the Chromecast, Android TV devices such as the Nexus Player and Nvidia Shield TV have always had those beautiful background images as their default screensaver. However, unlike the Chromecast, these "Backdrop" images, as they're called, weren't always customizable on Android TV.

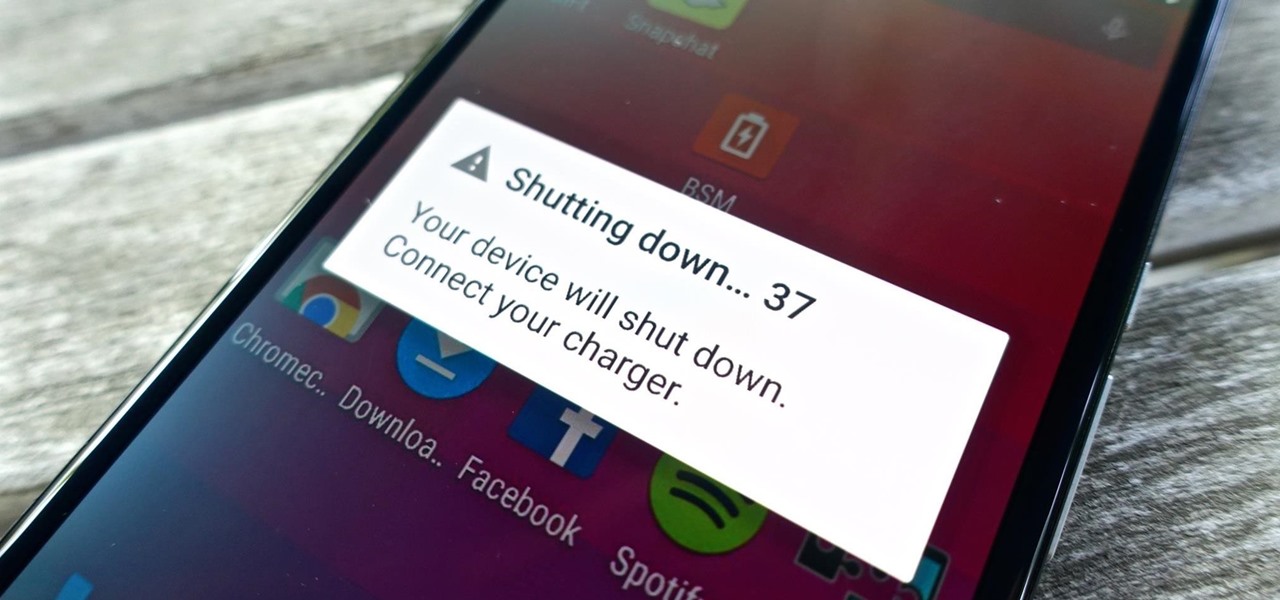
Even if my phone has only 1% of battery life left, I'll keep using it until I can get to a power source somewhere. Most times I never make it to a charger, and my device eventually powers down on its own.

The Nexus 6 came with a hidden kernel module that allowed for double-tap-to-wake functionality, essentially letting you turn your screen on just by tapping it. A simple root app allowed us to activate this feature, which meant we were always two quick taps away from waking our device.

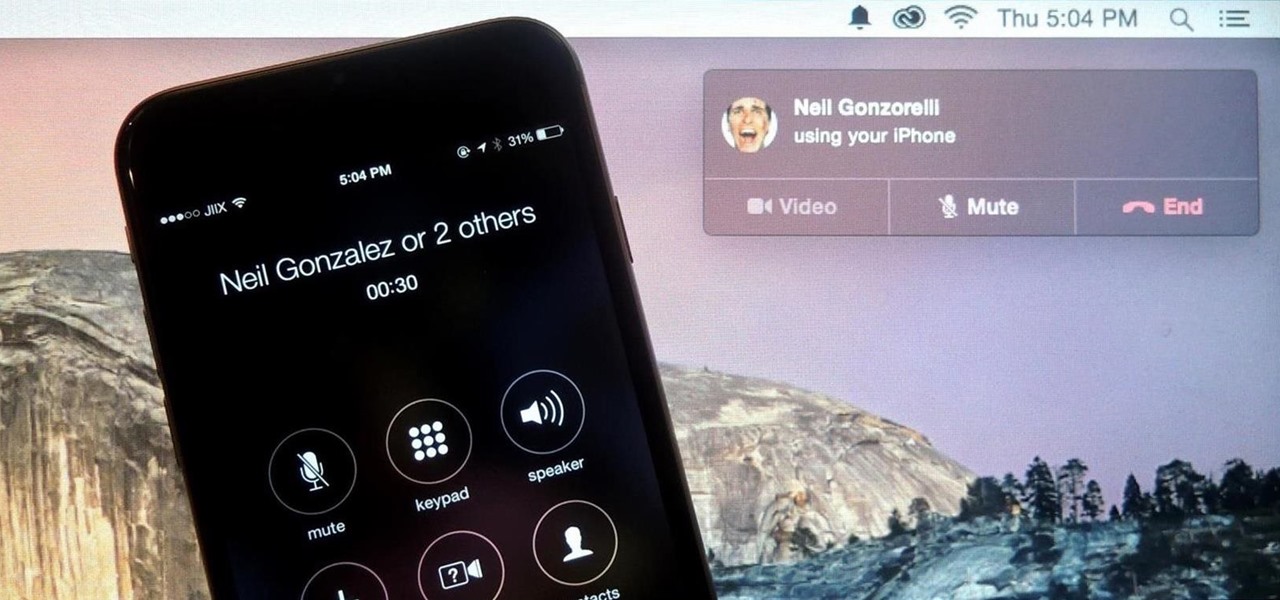
Earlier this year, Apple announced Continuity, a feature for Yosemite and iOS 8 that lets you connect your iOS devices to your Mac in order to access apps, receive phone calls, send text messages, and more while seamlessly switching between the two.

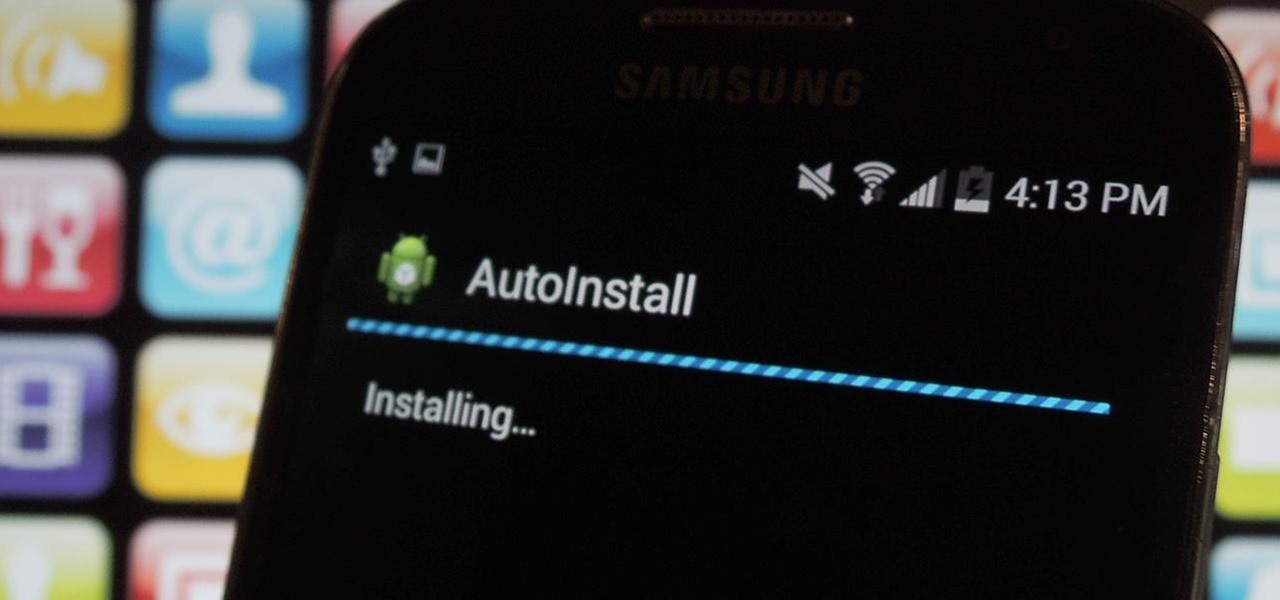
I'm always looking for the best apps and services for my Android, and that means sticking strictly to the Google Play Store is a no-go. If you're like me and tend to install a lot of APKs (application files), you're probably tired of seeing the "Install" confirmation that always pops up.

One thing I absolutely cannot stand is lag when I'm gaming. Every time I'm about to beat my killstreak record on Call of Duty, my internet connection drops and I'm a goner. It never fails. This usually happens because someone else on my Wi-Fi is streaming a movie or downloading a huge file.

Created by by XDA developer rovo89, the Xposed Framework allows you to quickly search for, download, and install new modules that allow various forms of customization for your Android device.

The video is about making a ISO file or a disc.To enable this you must have ISO installed on your system.The video begins by opening the Image burn setup wizard file.Once you have opened it , keep clicking next until you are finished with the installation. Then you have to insert a blank CD into the drive. Once you have done that a window will pop open displaying options for the CD.Click on the mode option in the window and select ec mode and then click on the first option displayed which is ...

This is a video that teaches you how to connect a Nintendo DSi to the internet. In order to connect a Nintendo DSi to the internet, you have to do this.

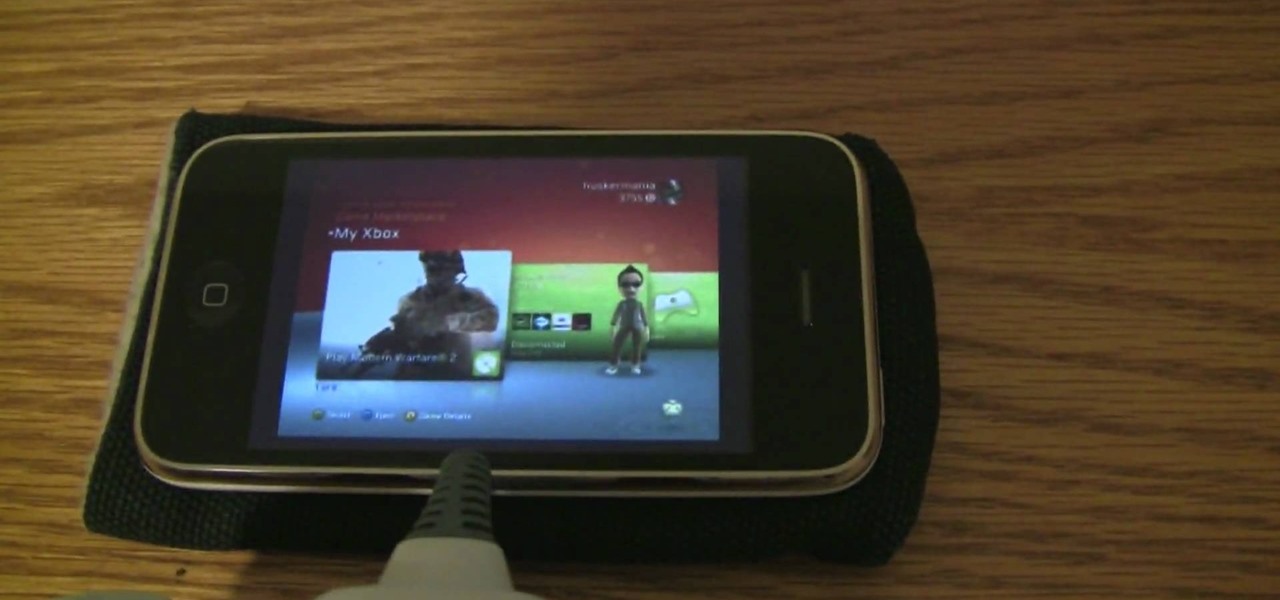
This video will show you how to play on your Xbox 360 using your iPhone 3GS. In order to do that just follow these steps: You will need to get a Slingbox Solo, a composite cable and the Slingbox Player installed on your device. Now you will need to plug in the composite cable into the Slingbox Solo and into the Xbox 360. Connect the Slingbox with the wireless router and with the internet modem. Now configure the network and connect with the iPhone. The last thing to do is to start the Xbox 36...

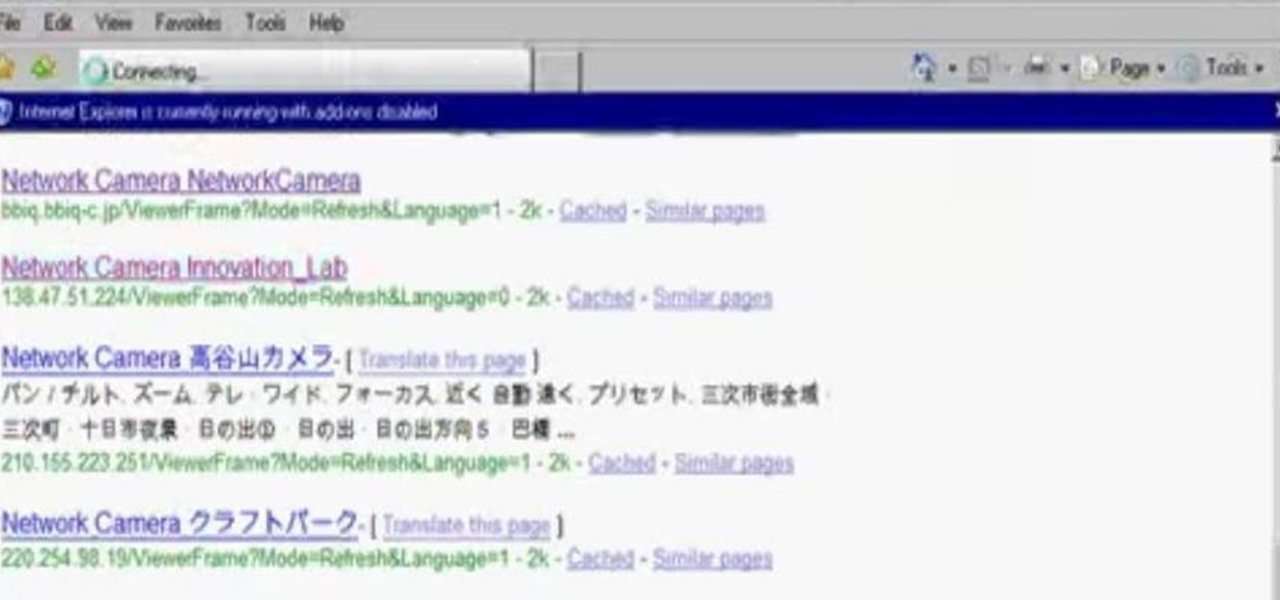
Learn how to hack Google with this amazing video. This video will teach you how to hack Google by using advanced search operators and esoteric search terms to find “hidden” files and mp3s quickly and easily; you'll also learn how to use Google to hack unprotected Internet-controlled devices like webcams and security cameras. For more information on Google hacking, and how to get started using these hacks yourself, take a look at this instructional video!

Imagine a scenario where you're nowhere near your iPhone, but it's on loud, and you really need to silence it. An alarm may be blaring, notifications could be spitting out sounds left and right, and calls may be ringing. Things can get annoying real quick for whoever's around it. Plus, all that attention makes it easy for someone to find and possibly steal your iPhone. Luckily, you can quiet it down.

One of the main reasons Authy was able to top our list of the best two-factor authentications apps was its ability to transfer access to a new device. This feature ensures that whenever you get a new phone, you don't lose all your tokens. However, if the process is done incorrectly, you can leave your account vulnerable.

Another AR cloud candidate has emerged in YOUAR, a startup that has developed a new system that enables persistent augmented reality experiences on iPhones and Android devices.