
News: Apple's Latest Patent Proposes Augmented Reality Navigation for Cars via Mobile Device
With Google taking on the sidewalks with augmented reality walking navigation for Google Maps, Apple has its sights set on the road.


With Google taking on the sidewalks with augmented reality walking navigation for Google Maps, Apple has its sights set on the road.

With Magic Leap One approaching six months since launch, Magic Leap is fully focused on building a content ecosystem and developer community.

Location-based gaming pioneer Niantic has offered a preview of its augmented reality cloud platform that could change the immersive content game yet again.

Our brains do a magnificent amount of work to process visual stimuli, but they aren't difficult to fool. Optical illusions can trick our minds into believing what we're seeing is real, even if it's not—and virtual and mixed reality technologies take advantage of this little loophole in our brain to help us accept the unreal.

Not content with bringing the first untethered mixed reality headset to market, Microsoft wants to expand their Windows Holographic operating system beyond HoloLens into vastly more robust technologies.

Hate slogging through pages and pages of weighty books and lengthy work documents? You may not be able to depend on speed-reading apps, but with the right font, you can increase the number of words you scan each second, speeding up your reading pace exponentially.
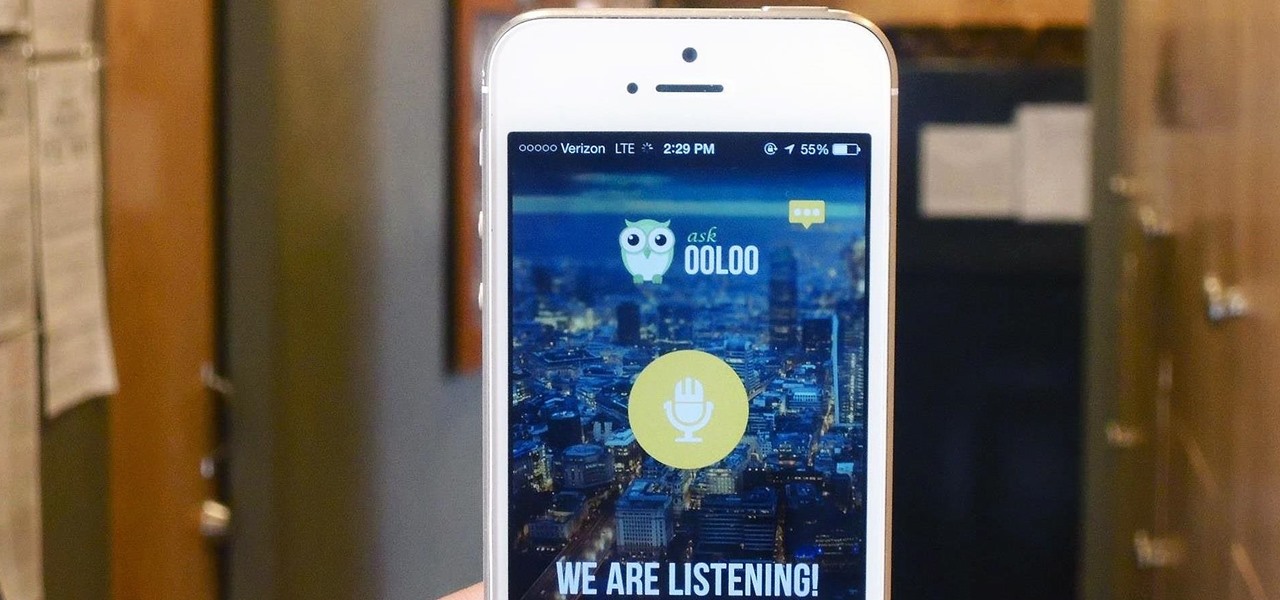
Apple has Siri, Google has its Now service, and Microsoft has Cortana. All of these voice-activated services can bring you information quickly and easily without having to type anything into your smartphone. Speak and within seconds you're provided with either an answer or somewhere you can find it.

Sometimes, you just don't want to hit the Power button to turn your screen off. In the current age of touchscreens, you've got to wonder why we even have physical keys anymore.

Welcome back, my novice hackers! I've written a couple of articles on reconnaissance and its importance, and as I've said before, a good hacker will spend 3 to 4 more times doing reconnaissance than actually exploiting the system. If your recon isn't good, you'll likely fail, or worse—end up serving time and becoming Bubba's wife for a couple years. I can't say it enough—recon is critical.

Who's ready to let future Facebook augmented reality smartglasses read their brain? Well, ready or not, the tech giant is making progress in the area of brain control interfaces (BCI) by funding research.

As Microsoft continues to bask in the glow of its HoloLens 2 unveiling and begins ramping up the hype to launch, Nreal and Vuzix are carving out their own niches in the AR hardware landscape.

The augmented reality industry had enough twists this week to surprise even M. Night Shyamalan.

Having an efficient workflow is an integral part of any craft, but it's especially important when it comes to probing apps for vulnerabilities. While Metasploit is considered the de facto standard when it comes to exploitation, it also contains modules for other activities, such as scanning. Case in point, WMAP, a web application scanner available for use from within the Metasploit framework.

Apparently, it's Google Week for the augmented reality business. Now that ARCore has a firm foothold in the app ecosystem, Google is making a case with educators and marketers that the apps should have a place in schools and campaigns, and the company is also encouraging developers to learn how to build apps using ARCore.

Now that ARCore is out of its developer preview, it's time to get cracking on building augmented reality apps for the supported selection of Android phones available. Since Google's ARCore 1.0 is fairly new, there's not a lot of information out there for developers yet — but we're about to alleviate that.

Another piece of Magic Leap's mysterious story has been uncovered thanks to a new patent application revealed on Thursday, March 15.

Within the coming months, software startup Neurable plans to introduce the next paradigm in virtual and augmented reality: the brain–computer interface (BCI).

LOOOK, a Seattle-based mixed reality and development studio, can now peer into the future with their new geotechnical engineering visualization application for Microsoft HoloLens.

Welcome back, my neophyte hackers! Digital forensics is one of the fields often overlooked by aspiring hackers. In a rush to exploit every and any system they can, they often ignore learning digital forensics—the field that may lead to them being traced.
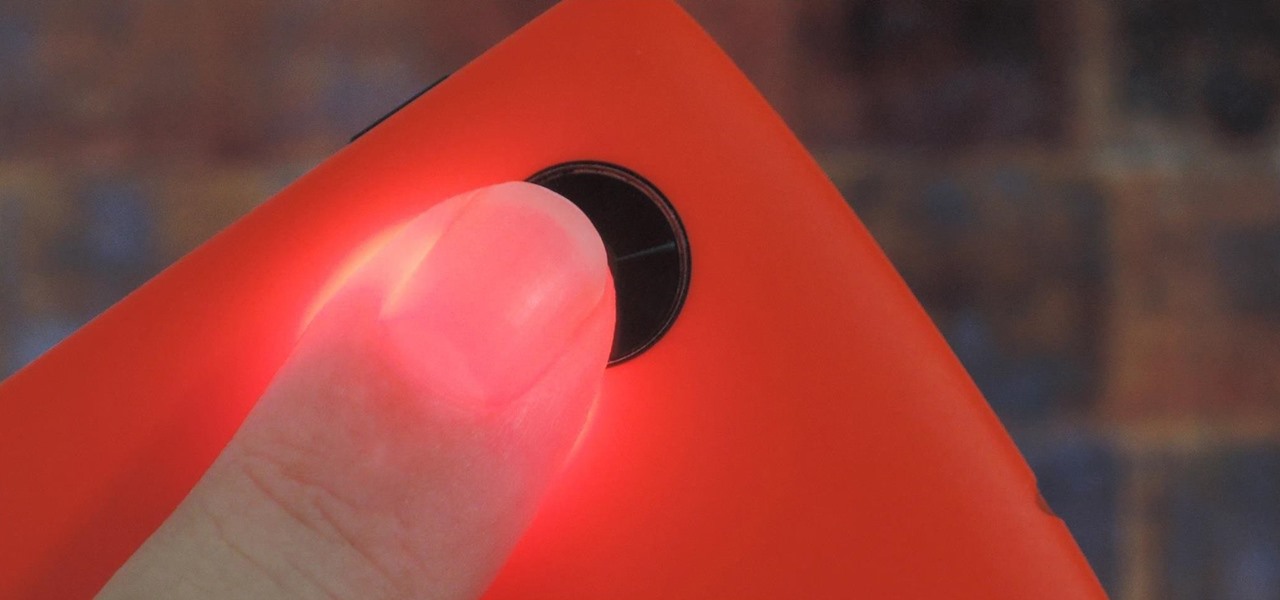
Samsung created quite a buzz when it debuted a built-in heart rate sensor on the Galaxy S5 back in 2014, but amazingly, not many other manufacturers decided to follow suit. It's really a shame, too, since data from a heart rate sensor would go perfectly hand in hand with the increasing fitness- and activity-tracking features that most smartphones sport these days.

Welcome back, my rookie hackers! The more we know about a system or network, the better our chances of owning it and not leaving a trace for investigators to follow. One of the often overlooked sources for information is the Simple Network Management Protocol (SNMP). Many rookie hackers are not even aware of it, but it can prove to be a treasure trove of information, if you understand how it works and how to hack it.
With Apple's Photos app, you no longer need a third-party tool on your iPhone, iPad, or Mac to blur or pixelate faces in your photos, helping you safeguard identities when sharing online.

If you were to summarize the path Snap has taken towards augmented reality smartglasses with a meme template, how it started would be the first-generation Spectacles camera glasses and how it's going would be the next-generation Spectacles with AR capabilities.

While the stock market can be unpredictable, it's not a complete enigma. There are patterns to watch for that can make you a successful trader. Fortunately, there is an expert guide to becoming an analyst that's now available to everyone.

With just one line of Ruby code embedded into a fake PDF, a hacker can remotely control any Mac computer from anywhere in the world. Creating the command is the easy part, but getting the target to open the code is where a hacker will need to get creative.

Most users don't realize how much valuable data is in their network traffic. With a few simple tools, an attacker can quickly pick out cookies, passwords, and DNS queries from a macOS device as it covertly streams the victim's network traffic to the attacker's system. Here, we will cover two methods for analyzing packets flowing from a Mac.

Proxies can be quicker to use than a VPN for specific applications, like web browsers or torrent clients. Both services will hide your true IP address, but a VPN is slowed down because it encrypts all data through a VPN network, while a proxy just acts as a middleman for fetching and returning requests from a server on your behalf. When speed is needed, go proxy.

So much information exists online that it's easy to get lost in data while researching. Understanding the bigger picture can take a lot of time and energy, but narrowing the question to one that's easy to answer is the first step of any investigation. That's why analysts use open-source intelligence (OSINT) tools like Maltego — to help refine raw data into a complete understanding of a situation.

If you need a tiny, flexible attack platform for raining down human-interface-device (HID) attacks on unattended computers, the USB Rubber Ducky is the most popular tool for the job. By loading the Ducky with custom firmware, you can design new attacks to be effective against even air-gapped computers without internet access. Today, you'll learn to write a payload to make "involuntary backups" through copying a targeted folder to the Ducky's USB mass storage.

Android has a single text file named build.prop that determines tons of various system-wide settings on your device. You need root access to edit this file, since it's stored on the system partition—but the various lines of codes it contains are actually fairly easy to interpret and modify.

Apple's special September event just wrapped up with the company unveiling several new products, including the iPhone 6S, iPhone 6S Plus, iPad Pro, and the new Apple TV set-top box. In addition to hardware, Apple also discussed a couple of its latest software platforms, iOS 9 and watchOS 2. Check out everything that Apple unveiled below.

Welcome back, my tenderfoot hackers! Well, the first season of Mr. Robot just ended and Elliot and fsociety successfully took down Evil Corp! They have effectively destroyed over 70% of the world's consumer and student debt! Free at last! Free at last! Of course, global financial markets crashed as well, but that's another story.

Though many students spend four years of high school learning a foreign language, most of us probably retained very little. Chalk it up to the carelessness of youth, but chances are you've since been in situations or places that left you wishing you paid more attention in class or had continued practicing long after you graduated.

A friend of mine has a crazy amount of Reddit karma and gold, and yesterday he let me in on his secret. This person, who will remain unnamed for obvious reasons, created a Python script called Reddit Karma Crawler that finds rising posts before they get too popular.

Welcome back, my novice hackers! This next subject might seem a bit obscure, but I promise you, this lesson will benefit you significantly either as a hacker or system admin. This tutorial will cover what is usually referred to as a regular expression, or regex for short.
Featured on MTV's Catfish TV series, in season 7, episode 8, Grabify is a tracking link generator that makes it easy to catch an online catfish in a lie. With the ability to identify the IP address, location, make, and model of any device that opens on a cleverly disguised tracking link, Grabify can even identify information leaked from behind a VPN.

Before attacking any website, a hacker or penetration tester will first compile a list of target surfaces. After they've used some good recon and found the right places to point their scope at, they'll use a web server scanning tool such as Nikto for hunting down vulnerabilities that could be potential attack vectors.

Auditing websites and discovering vulnerabilities can be a challenge. With RapidScan and UserLAnd combined, anyone with an unrooted Android phone can start hacking websites with a few simple commands.

Cracking the password for WPA2 networks has been roughly the same for many years, but a newer attack requires less interaction and info than previous techniques and has the added advantage of being able to target access points with no one connected. The latest attack against the PMKID uses Hashcat to crack WPA passwords and allows hackers to find networks with weak passwords more easily.

Most companies have services like employee login portals, internal-only subdomains, and test servers they would prefer to keep private. Red teams and white hat hackers can find these obscure and often vulnerable services using a tool designed to help protect users from fraudulent certificates.