Reconnaissance is the phase of an attack where a red team or hacker designs a strategy based on the information they can learn about the target, as well as what the available attack surface looks like. These scans can take time to discover relationships, but Raccoon OSINT scanner coordinates multiple automated scans to produce invasively detailed reports on a target with a single command.

MacOS isn't known as an ideal operating system for hacking without customization, but it includes native tools that allow easy control of the Wi-Fi radio for packet sniffing. Changing channels, scanning for access points, and even capturing packets all can be done from the command line. We'll use aliasing to set some simple commands for easy native packet capture on a macOS system.

There's a feature in the Gboard keyboard that enables people who cannot talk, type, or swipe normally to still have a way to communicate in the digital age on their smartphones. While it's mainly an accessibility feature for those who actually need it, it's a good way for anyone to learn or brush up on their Morse code skills — and it works on both Android and iOS.

Connecting to your headless Raspberry Pi on the go typically requires a network connection or carrying around bulky peripheral hardware like a screen and keyboard. With the help of an old-school connecting standard, though, you can log into your Pi from any computer using a simple cable. If you don't have a power source, you can also power your Linux distro over the cable at the same time.

The pictures we upload online are something we tend to think of as self-expression, but these very images can carry code to steal our passwords and data. Profile pictures, avatars, and image galleries are used all over the internet. While all images carry digital picture data — and many also carry metadata regarding camera or photo edits — it's far less expected that an image might actually be hiding malicious code.

In my previous article, we learned how to generate a vulnerable virtual machine using SecGen to safely and legally practice hacking. In this tutorial, we will put it all together, and learn how to actually hack our practice VM. This will provide some insight into the methodology behind an actual attack and demonstrate the proper way to practice on a VM.

Hello partners, first of all I would like to thank all those who have sent me positive feedback about my posts, to say that I'm always willing to learn and teach. I'm also open to answer the appropriate questions.

Hello my anxious hackers, the week has started and here we begin a new series that I think will help many here and not only, for those that have the opportunity to follow our tutorials but they are not yet part of the community.

There are more actions available for the Action button, but only a handful of iPhone models have that button. However, there is another button with new features you can use, and you can access all the fresh features on any iPhone model that can run iOS 18.

Apple claims that the iPhone 14 Pro and 14 Pro Max have the highest peak brightness of any smartphone, but is that really true?

While Apple has been rather secretive about its work on AR wearables (despite the abundance of leaks revealing details about their unannounced devices), Facebook has been rather chatty about its plans for smartglasses.

With the Wigle WiFi app running on an Android phone, a hacker can discover and map any nearby network, including those created by printers and other insecure devices. The default tools to analyze the resulting data can fall short of what a hacker needs, but by importing wardriving data into Jupyter Notebook, we can map all Wi-Fi devices we encounter and slice through the data with ease.

It only takes a few commands to manipulate a MacBook's secure HTTPS traffic and pluck login passwords out of the encrypted data. Let's take Facebook and Gmail hacking to the next level by intercepting Safari and Google Chrome web traffic in real time.

Coinhive, a JavaScript cryptocurrency miner, was reportedly discovered on the BlackBerry Mobile website. It was placed there by hackers who exploited a vulnerability in the site's e-commerce software that allowed them to anonymously mine cryptocurrency every time the website was viewed. There's no doubt Coinhive, an innovative mining method, is being abused and exploited by hackers in the wild.

Format strings are a handy way for programmers to whip up a string from several variables. They are designed to save the programmer time and allow their code to look much cleaner. Unbeknownst to some programmers, format strings can also be used by an attacker to compromise their entire program. In this guide, we are going to look at just how we can use a format string to exploit a running program.

Black Mirror, Netflix's technology-horror anthology, never fails to provide thought-provoking entertainment centered around emerging and futuristic technologies, and the third season's second episode, "Playtest," delves deep into the worlds of mixed, augmented, and virtual reality. While designed to leave you haunted by the end, offering a more "evil" narrative than we'll likely see in our actual future, the episode explores possibilities that aren't as far off as one might think.

When it comes to washing clothes, the laundry symbols on your tags might as well be hieroglyphics. They're difficult to interpret, easy to forget, and even easier to ignore. But if you don't want to ruin expensive designer clothes, blankets, and other fiber-based materials, you need to figure out the meaning behind those tiny icons. Thankfully, your iPhone can help out.

There have been third-party iOS apps for live conversation translations, and Google Assistant pushed out its own feature for iPhone last year. Still, iOS 14 now has a default translator for real-time multi-language talks in person. So you can finally chat with people who use a different language without missing anything or having to install any complicated apps on your device.

While our time with the Protostar VM from Exploit Exercises was lovely, we must move on to bigger things and harder challenges. Exploit Exercises' Fusion VM offers some more challenging binary exploitation levels for us to tackle. The biggest change is that these levels are all network services, which means we'll write our first remote exploits.

In a new update, the iPhone 16 lineup is finally getting Visual Intelligence, a feature that lets you instantly gather information about anything around you just by snapping a picture.

Withstanding an attack from a motivated hacker is one of the most important responsibilities a system administrator must undertake. This is especially true for websites that may contain sensitive customer information and a high volume of users. So it's important for a sysadmin to take proactive measures to find and fix vulnerabilities in their websites.

Our everyday lives are inundated with displays from smartphones, computers, tablets, TVs, and other devices, so it's important to find ways to limit your screen use wherever possible to improve your overall digital well-being. One simple thing you can do if you have an Apple Watch is make your watch tell you the time so you don't have to look yourself — and this little-known feature is easy to unlock.

An invaluable button on your iPhone can do hundreds, even thousands, of amazing things, but most iPhone users don't even know it exists. You can't push it. You can't click it. You can't press it. But it's the largest button on your iPhone, more powerful than the versatile Side button, and it's hiding in plain sight.

Bash scripting is a convenient way to automate things on any Linux system, and we're going to use it here to automate certain tasks we use all the time.

Apple's iOS 13 has been available for beta testing since June, and the stable release pushed out to everyone on Thursday, Sept. 19. To help you make the most out of iOS 13 for iPhone, we've rounded up everything you'll want to know, whether a colossal feature, small settings change, interface update, or hidden improvement.

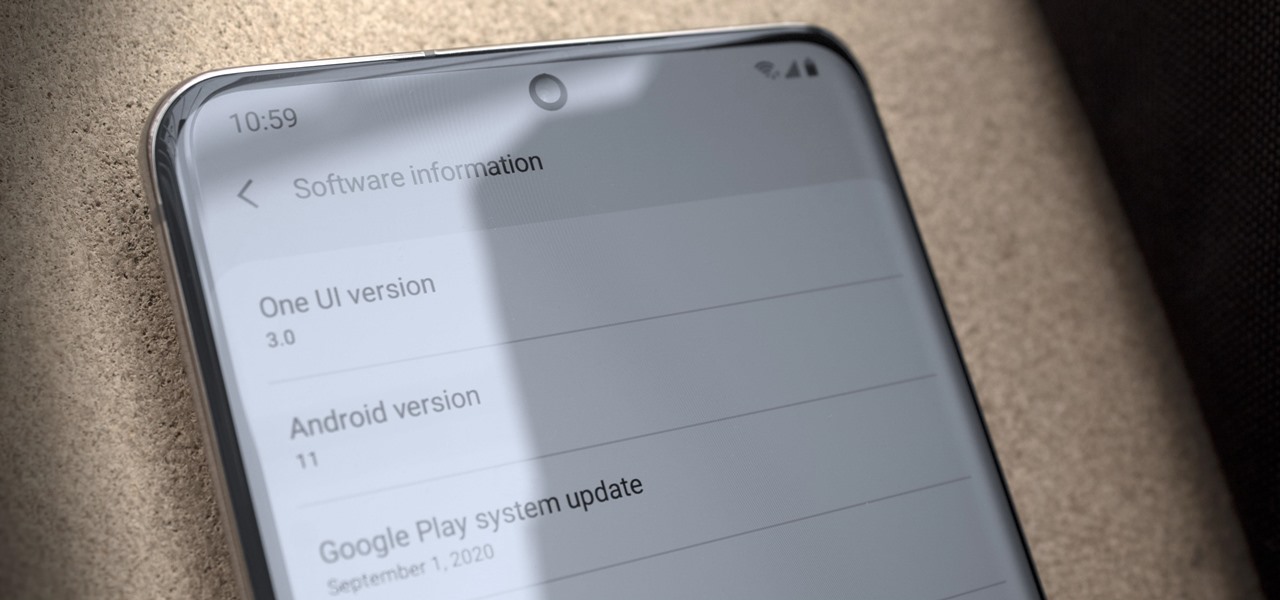
Just days after Google released the official Android 11 update, Samsung already had a pre-beta build of One UI 3.0 available for developers to test their apps on. So this year's main OS upgrade is likely hitting Galaxy phones even earlier than we thought.

Peter John explains how to interpret the appearance of a Major Arcana card in a reading using the Rider-Waite Tarot deck. He shows how the High Priestess and Empress cards indicate that a pregnancy might be in the future for your querent.

In this math lesson we will learn how to solve a proportion word problem. Watch the video to learn how to set up a proportion, solve it, and interpret the answer.

Ready to stop going threw life blind? Try to get a glimpse of the future or at least a use these as a reflection of what’s happening in your life with your own tarot cards. Tarot cards can provide endless hours of entertainment.

Joyce Danielson, our professional wardrobe expert tells you how to iron pockets, add pleats as well as iron seams and cuffs. She also explains how to interpret care instructions on the label and how to wash and iron your shorts accordingly. Why look like a slob when you can look like a prep?

In this instructional video series, learn how to read piano sheet music for yourself. Our expert will walk you through a step-by-step tutorial that covers such basics as which notes to play with which hands, what key signatures mean, how to interpret the rhythm of the song, and how to sight read without knowing the song.

Dating a man who wants to keep his freedom? - Why does he say he loves you, then? Dating coach Francisco Bujan tells you how to interpret mix messages from men.

Math class got you down? We all know sixth grade mathematics is where we all start to lose it. We get frustrated with all of those numbers, try to figure it out, but ultimately flunk out or barely pass the class. Maybe the teacher just wasn't good enough to educate us, who knows, but there's no worries anymore.

This tutorial discusses the differences between a straight and a premultiplied Alpha channel in Cinema 4D. Learn how to spot the difference and ensure you interpret your files correctly when setting up your composite. Whether you're new to MAXON's popular 3D modeling application or are just looking to get better acquainted with Cinema 4D and its various features and functions, you're sure to enjoy this free video software tutorial. For more information, and to get started using this trick in ...

Choosing a nanny or au pair for your children is a process that should be organized and performed carefully, to ensure you find someone who can be trusted, will contribute significantly to the development of your child and integrate well into your family.

Learn how to use the history brush to correct your images. You will also briefly learn how to read and interpret your image using Photoshop’s built-in histogram tool. Whether you're new to Adobe's popular image editing application or simply looking to brush up on Photoshop CS4, you're sure to enjoy this free video tutorial. For detailed instructions, and to get started color correcting your own images with the histogram and history brush tools, take a look. Use Photoshop CS4's histogram & his...

This highly educational video geared towards scientists will show you how to generate AC electrokinetic phenomena by microelectrode structures.

Looks good enough to eat. Artist Olle Hemmendorff was asked to interpret the Nike Air Max 90 for an exhibit.

Let's take a look at the softer side of illusions! Check out the images below and see if you can crack what's really behind these photos. This type of optical illusion is usually referred to as an ambiguous image. Your brain tries to make quick sense out of the information coming in, and sometimes an interpretation of one image gets preference over the other.

The day of interactive porn has arrived, all thanks to Steve Jobs. The iPhone 4's new video-call feature, FaceTime, enables users to have live video chat sessions over a Wi-Fi network, via the iPhone's camera and screen. Unsurprisingly, the porn industry was immediately inspired.