Mobile gamers who grew up on J.K. Rowling's fantasy epic have yet another reason to rejoice, as Jam City's Harry Potter: Hogwart Mystery is slated to touch down on both iOS and Android on April 25. But if you can't bear the wait, there's a little hack you can do to give the game a try right now.

While the mainstream consumer market waits for cool augmented glasses to arrive from Magic Leap, or maybe even Snap Inc. (Spectacles 2.0??), AR headset maker DAQRI and its business customers are finding new, money-saving and time-saving use cases for the technology today.

Following up on a preview of the deal we reported during last week's CES, Dell has officially announced the details around its role as the first company to resell the Meta 2 augmented reality headset.

Augmented reality headset maker DAQRI today named chief product officer Roy Ashok as the company's new chief executive officer to accelerate the company's growth.

While many have their own strong opinions on Apple and their products, few have complaints about the way they embrace accessibility. Apple typically finds ways to make products functional to all customers, regardless of their situation. This philosophy can be seen in Apple's partnership with Cochlear, as the two develop a new cochlear implant sound processor for iPhone.

My message to Russian hackers is this: LEAVE BRITNEY ALONE! Russian hacking collective Turla has been targeting governments and military operations in the United States, Europe, Asia, and the Middle East for the past decade. Now, it appears that the group is targeting everyday citizens — specifically Britney Spears fans.

When will the drama end? The lawsuit between Waymo and Uber is back in the news with no signs of stopping. Today the court denied yet another request from Uber to shield itself with the fifth amendemnent, securing a small victory for Waymo.

Google's Pixel smartphone is striking up some heated competition between phone makers HTC, LG, TCL, and Coolpad, as the Pixel 3 gets ready to release in 2018. Yep, you heard that right—not the Pixel, not the Pixel 2, but the Pixel 3—which shows that Google is really committed to the future of its new flagship line.

We've all walked into a restaurant with the best of intentions only to order something absurd, like a cheese-injected burger topped with bacon on a brioche bun. It's delicious for the few minutes it takes to eat the thing, and then you're left with a bellyful of regret and an inability to directly look at the numbers on your scale. Turns out that getting yourself to make healthy choices isn't as hard as one might think.

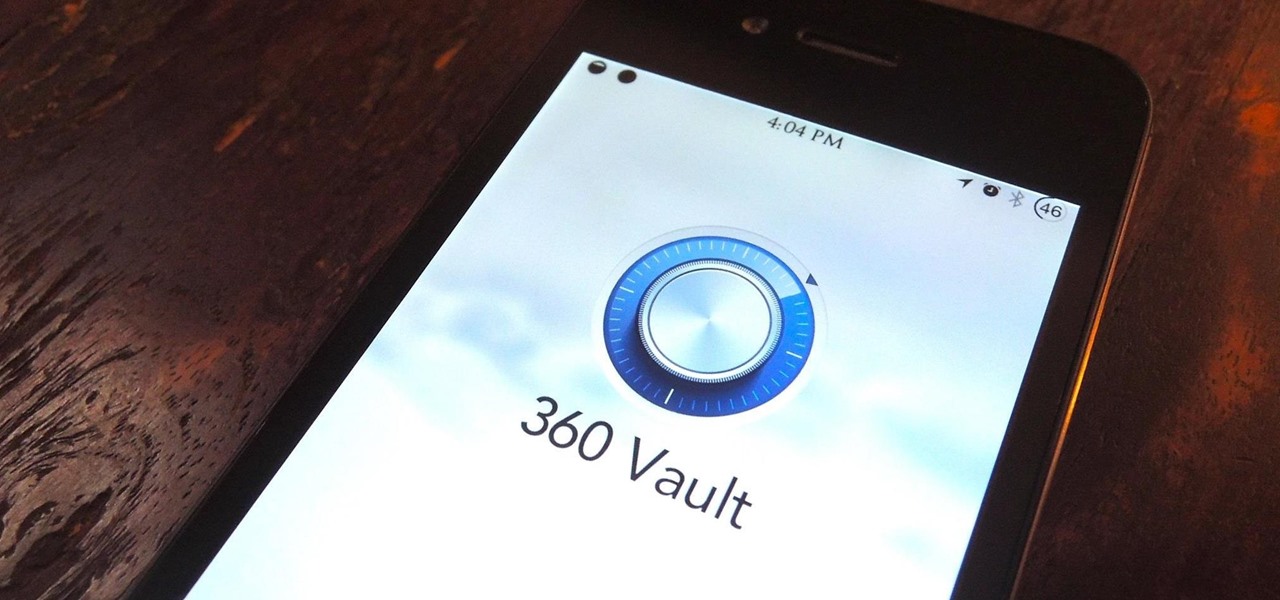
Let's be honest for a second; we all have sensitive material on our phones that we wouldn't want anyone else to ever see. Maybe it's to protect ourselves or someone else, or maybe it's none of your business why I don't want you to see pictures of my bachelor party. Regardless, sometimes we need to keep things hidden and safe.

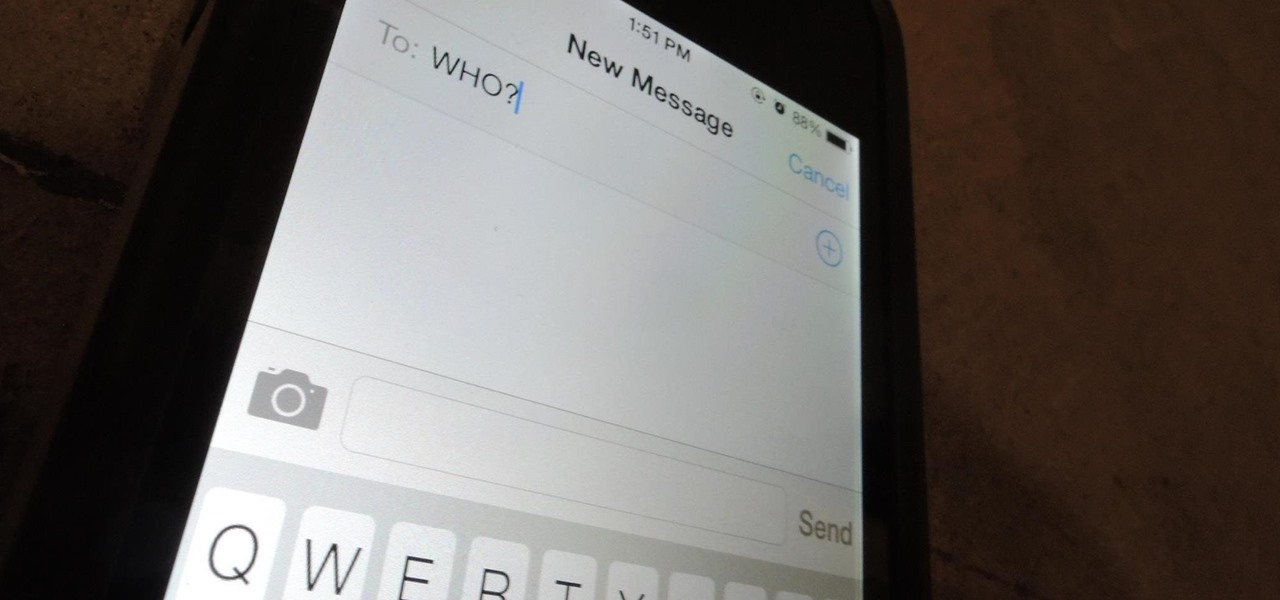
If you're a ladies man like me then this next tip could save you from sorely embarrassing yourself. Here's the problem: You think you are texting Kelly M from New Year's when you're actually texting Kelly F from that one bar. Needless to say this could cause a problem with your relationships.

Communication is the key to any healthy relationship, and when I say any, I mean human and non-human. Previously, one of the biggest culprits for not understanding what you meant was Siri, but now it looks like it has some competition with the new Kinect system, which can control practically everything on your Xbox One—if it can understand you.

I've never been much of a runner. I've tried running alone, with a partner, on busy sidewalks, and back country roads, but I just never got it. There are a few other forms of exercise I genuinely enjoy, but have yet to experience that "natural high" that avid runners are always talking about.
In any project management career, there is no such thing as a person who knows everything for each project. Many times, those who got too much confident with their jobs fail because they were not able to make things clear before and during the project implementation.

Is there something missing from your dance relationship? This four part how to video teaches you how to communicate with your dance partner. Use these secret tips from Naomi Uyama and Andy Reid, and become a better dance partner.

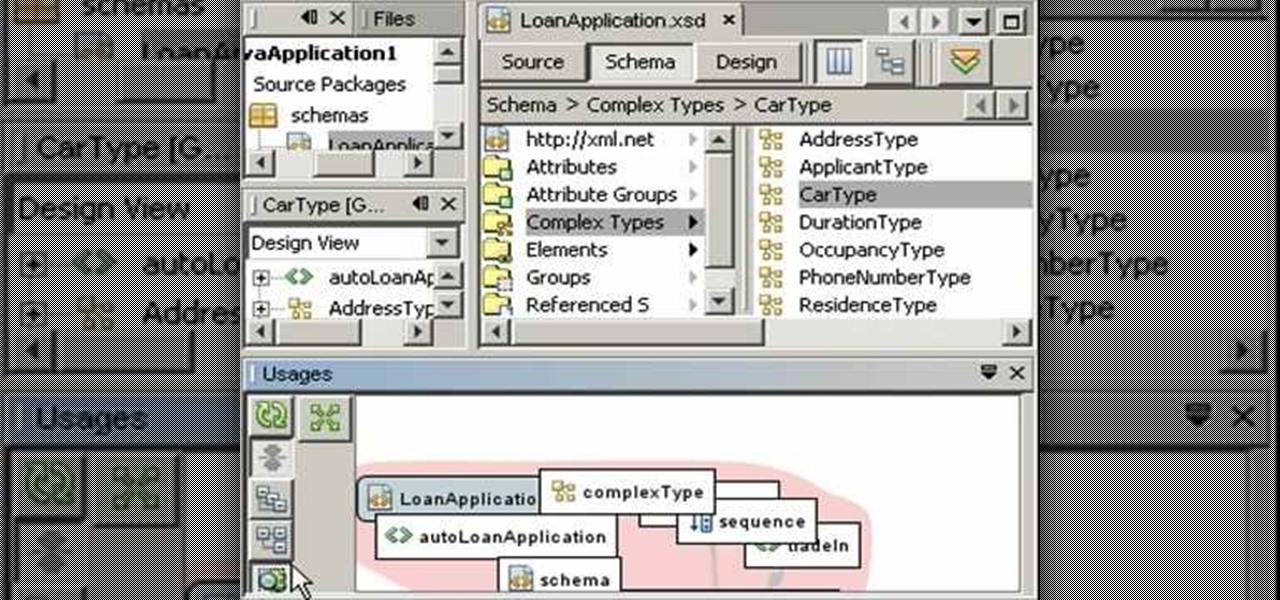
Watch this video tutorial to learn how to use the XML schema tools, which enable you to create, visualize, and edit XML schema in NetBeans 6.0. With these tools, you can visualize relationships between schema elements and use queries to find usages. You will also learn how you can easily create XML schemas by example. You will see how to navigate large schemas in the Design View, and you will learn how to visualize and edit multiple file schemas.

Spider-Man hits the iPhone, iPod Touch & iPad! In Ultimate Spider-Man: Total Mayhem, you take control of Spidey, slinging webs and fighting crime. No longer do you have to stick to comic books, you can enjoy Spider-Man right from your Apple mobile device.

The rock drum beat is an intricate drum pattern that incorporates the hi-hat, snare and bass drum. Learn some tips for playing various patterns of the rock drum beat from an experienced drumming instructor in this free music lesson video series.

How do you raise a smart child? This video answers that question. If you want your child to be as smart as Albert Einstein when he grows up, then you have to start with the basics. Hugging and playing with your child is important. So are talking, listening, and reading to your child. Once you lay down the foundation for a great relationship, it will naturally pave the way for the smart kid you always knew you had to emerge. This video shows you what you need to get the foundation in place.

Improving interpersonal perception builds communication skills and can provide relationship help. Part 1 of 6 - How to Improve interpersonal perception.

Reconnaissance is the phase of an attack where a red team or hacker designs a strategy based on the information they can learn about the target, as well as what the available attack surface looks like. These scans can take time to discover relationships, but Raccoon OSINT scanner coordinates multiple automated scans to produce invasively detailed reports on a target with a single command.

With any continuously active software, it can start to become fairly complex after a few years of updates. New features and revisions both get layered into a thick mesh of menu systems and controls that even pro users can get bewildered by. If you are new to a certain application after it has been around for many years, it can be downright intimidating to know where to begin.

One of the hardest parts about jewelry making is the knot-tying. It's an intricate process, much like jewelry making in general, which is meticulous and dexterous. Working with leather is also more difficult because of it's thickness and un-malleable contour. This demonstration video will help walk you through the process of tying a knot end with leather.

If you want to shake up your style or pay tribute to the 90s, then bust out that crimping iron. You will bring the party with this fun and funky style that can worn down, up or added to bring a little flare to more traditional styles.

The swing groove drum beat is an intricate drum pattern that combines the hi-hat, snare and kick drum. Learn to play several variations of the swing groove drum pattern by displacing eighth notes with expert tips in this free drumming video series.

The swing drum beat pattern is an intricate jazz rhythm that incorporates the snare, hi-hat and kick drum. Learn to play several variations of the swing drum beat with expert tips in this free drumming video series.

Music theory is a field of study that focuses on the intricate workings and mechanics of music. Learn about guitar music theory and intervals from a professional musician in this free guitar video.

We've gathered some of our favorite pranks with the seasonally appropriate for all you college kids out there. You're more than likely cohabitating with a complete stranger, and what better way to make a good first impression and develop a strong personal relationship than subject them to a hilarious prank?

The realm of science fiction isn't all lasers and cute green toddlers, sometimes alternate science history is sci-fi, too, as exampled by the Apple TV Plus series For All Mankind.

The still-unfolding story of China's Nreal augmented reality startup continues to develop, with each turn uncovering another unexpected wrinkle.

In the late nineteenth century, the advent of the motion picture wowed audiences with a new storytelling medium. Nearly a century and a half later, augmented reality is establishing a new frontier in film.

One of the hallmarks of augmented reality's coming of age is that the technology is starting to find a home in business categories that are less obvious compared to typical AR enterprise use cases.

While Toyota ranks as the leading automotive brand in the world, the company is a follower when it comes to augmented reality.

Smartglasses maker Vuzix has emerged with the first hardware powered by the Snapdragon XR1 chip, roughly nine months after Qualcomm introduced the chipset designed to drive augmented reality wearables at the Augmented World Expo in Santa Clara.

This week, Next Reality released the fifth and final set of profiles on the NR30 leaders in augmented reality, with this chapter focusing on the influencers in the industry.

Automotive augmented reality company WayRay has set its destination for a $1 billion valuation with an estimated time of arrival of 2019, and it has just passed a major milestone towards that goal.

As it prepares to ship its first product by the end of the summer, Magic Leap has managed to impress yet another high-profile investor in telecommunications giant AT&T.

On Tuesday, at the Unite Berlin developers conference, Unity unveiled new tools designed specifically for augmented reality that could literally raise the technology to the next level.

Hackers rely on good data to be able to pull off an attack, and reconnaissance is the stage of the hack in which they must learn as much as they can to devise a plan of action. Technical details are a critical component of this picture, and with OSINT tools like Maltego, a single domain name is everything you need to fingerprint the tech details of an organization from IP address to AS number.

The easiest way around a security policy is to find users who don't follow it. The Have I Been Pwned database identifies accounts with information breached by major third parties like Yahoo and LinkedIn. With Maltego, hackers can locate breached accounts created using company email addresses, potentially giving attackers access to a company account if the employee reuses a compromised password.