Global design and technology services company Tata Elxsi says it has licensed its advanced autonomous vehicle middleware platform "AUTONOMAI" to a "leading automotive OEM."
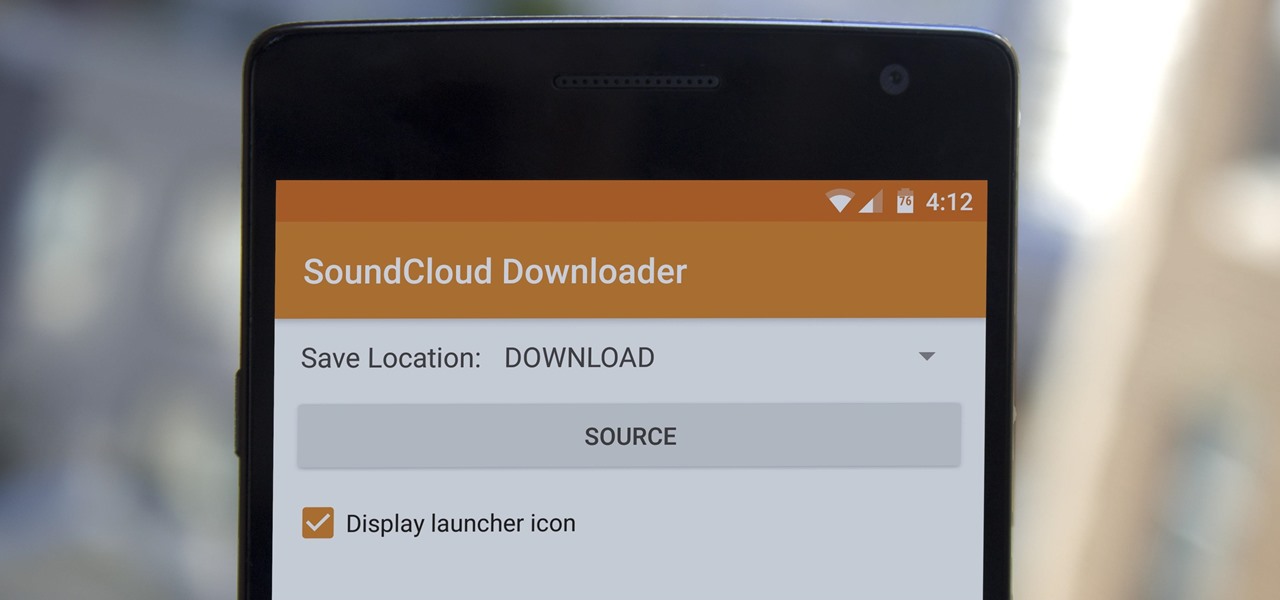
SoundCloud is one of the most popular music streaming services for good reason. You can upload your own music, listen to remixes from your favorite DJ, check out the latest releases from mainstream artists, and even discover new artists. But while you've always been able to listen to most songs for free, you couldn't download MP3s in the official app without paying for SoundCloud Pro — until now, that is.
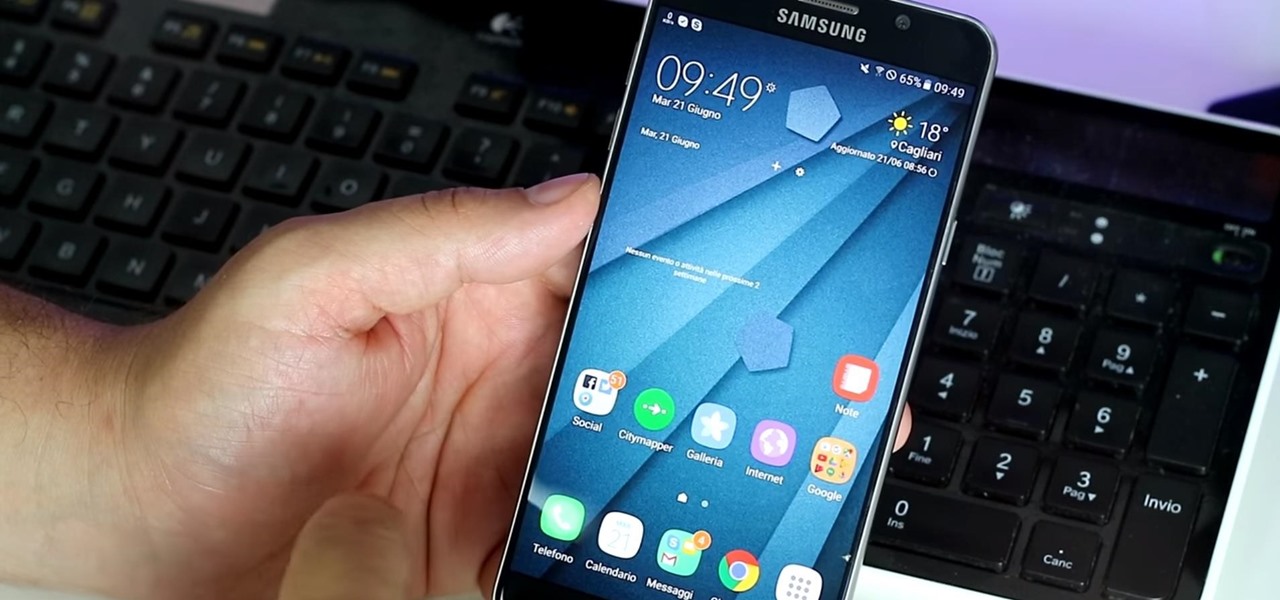
It looks as though Samsung will continue to tone down the look of TouchWiz, according to a leaked look at the newest "Grace" user interface for the upcoming Galaxy Note 7. HDblog, who acquired the leaked UI, shows off the beta version of the new skin in their video below.
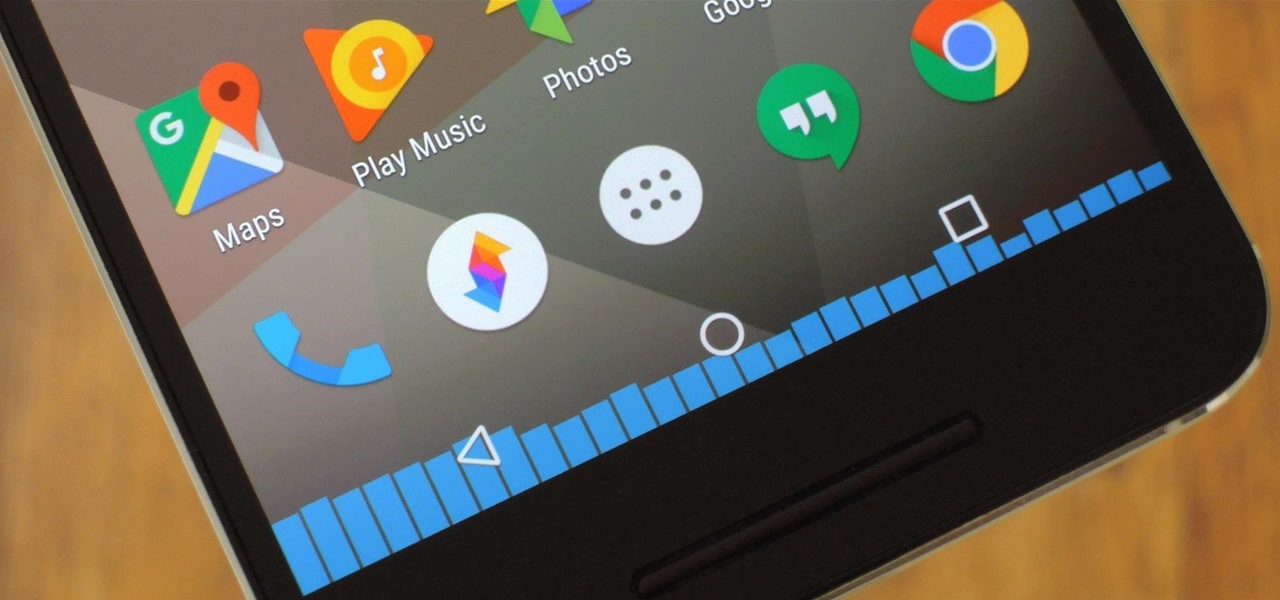
CyanogenMod, the popular custom ROM available for many Android devices, has a nice little feature that displays a music visualizer beneath your on-screen navigation keys while you're listening to your favorite songs. It's a subtle touch, but it makes for a more immersive experience when you're jamming out while using your phone or tablet.

Welcome back, my rookie hackers! The Golden Fleece of hackers is to develop a zero-day exploit, an exploit that has not been seen by antivirus (AV) software or and intrusion detection system (IDS). A zero-day exploit is capable of skating right past these defenses as they do not contain a signature or another way of detecting them.

Sony's Xperia smartphones are some of the most beautiful Android devices out there—but unfortunately, they're rarely promoted in the U.S. and are seldom available through major carriers (aside from the new Xperia Z5 devices), so not many Americans are aware of how awesome these devices really are.

When they were purchased by Google back in 2011, Motorola underwent a sweeping change in software philosophy. All throughout the UI on their flagship devices, edgy design patterns were replaced by clean, minimalist interfaces akin to vanilla Android. This philosophy has continued on as Motorola's signature, even though they have since been sold to Lenovo.

The stock Camera and Photos apps are great for taking basic pictures and doing some quick edits, but if you're serious about making your iPhone photos the best they can be, you can't stop there.

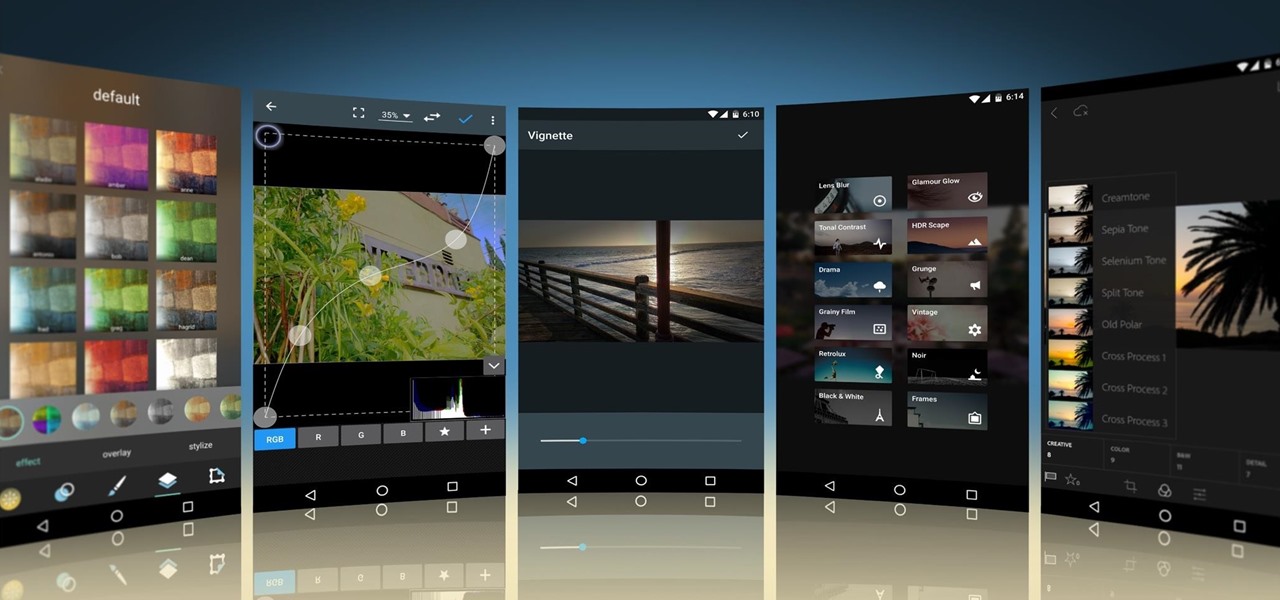
Smartphone cameras are so good nowadays that there's almost no reason to own a point and shoot. Once the megapixel spec race was finally settled (hint: more isn't always better), manufacturers started focusing on the quality of their camera sensors, which has led to a huge jump in color accuracy, dynamic range, and image clarity.

Greetings all. I'm back with another informational review of the diversity of utilities for use in the sphere of hacking at your disposal. Today we are going to cover the insides of CUPP (Common User Passwords Profiler) in its entirety. The tool is very basic in nature, as there is little to no configuration needed to get cracking (worst pun ever). So let's get started, shall we?

Scanners are much too cumbersome to fit in a pocket, but with the use of just one application, you can replace all that bulky hardware with your Android smartphone and take it with you wherever you go. All you need to do is find the scanning app that fulfills your needs. Here are our five favorites that are good for business pros and average joes alike.

In modern versions of Windows, Microsoft made quite a few changes to Windows Explorer, the first of which is a new name—File Explorer. Another huge change that most will notice is that File Explorer now has a new look sporting the Ribbon interface.

Why did I write this when they're tons of scanning tools available.

Do you remember the last time we used BeEF? Well, now we get to use it again, but this time with MITMf! We are going to auto-inject the hooking script into every webpage the victim visits!

When you see a color depicted on your computer, smartphone, or tablet, odds are it was processed as a hex triplet before it was rendered. Most modern websites and operating systems use a hexadecimal coding system to signify certain colors, and these are represented as 6 letters and numbers.

A new API in Android Lollipop allows apps to color the status bar to match their overall theme. Google billed this as a more immersive user experience that allows app developers to extend their color branding even further. It certainly seems like a win-win on the surface, but unfortunately, not many apps are using this feature yet.

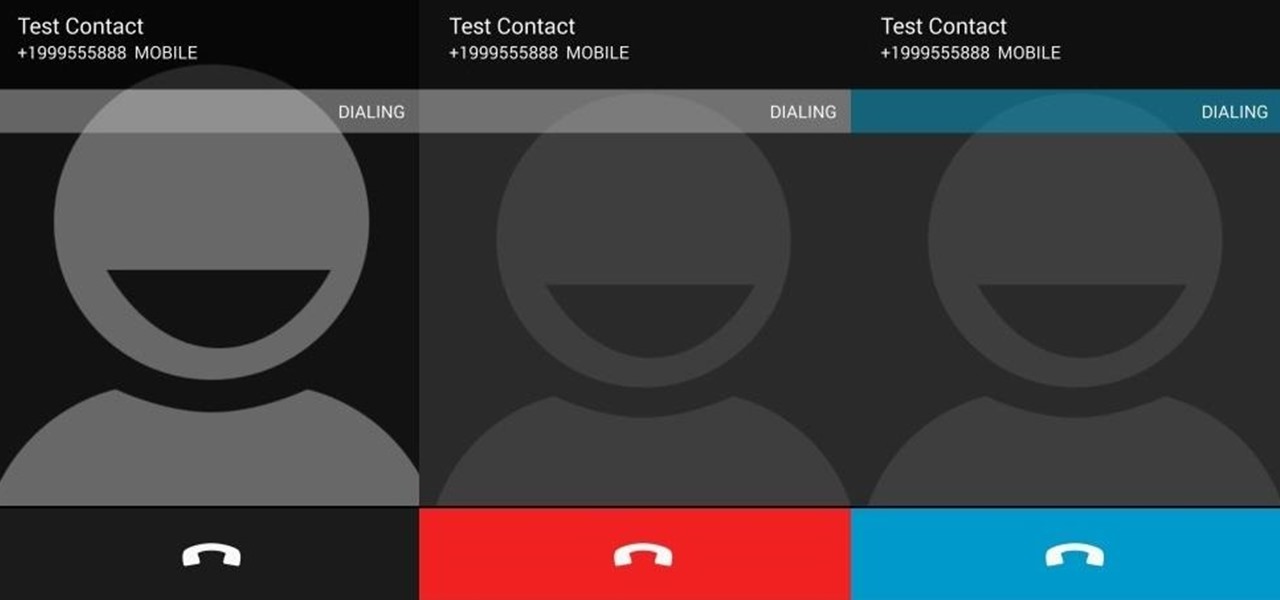
With Android 5.0, Google introduced a new "Heads Up" notification system for incoming calls and messages. While the new incoming call interface seems to be a rousing success, the rest of the Heads Up system has been met with much less enthusiasm from users.

Android Debug Bridge, or ADB for short, is a very powerful utility that can remotely execute commands on your Android device. This remote terminal interface, however, is not very "remote" at all. You have to be tied down to your computer to use it, since a USB cable is normally required.

There's no such thing as a perfect Android keyboard. Some, like Swype, have gesture typing down to a science, but lack in predictive technology. SwiftKey, on the other hand, boasts awesome next-word prediction, but less than stellar gesture typing. Many others are optimized for multiple languages, space saving, or emojis, but none are without their flaws.

Google+ doesn't have quite the user base of Facebook or Twitter, but for Android enthusiasts, it's definitely the place to be. All of the major developers—such as Chainfire and Koush—make their social media home on Google+, and the Android app sports one of the nicest interfaces of any comparable platform, chock-full of Google's Material Design.

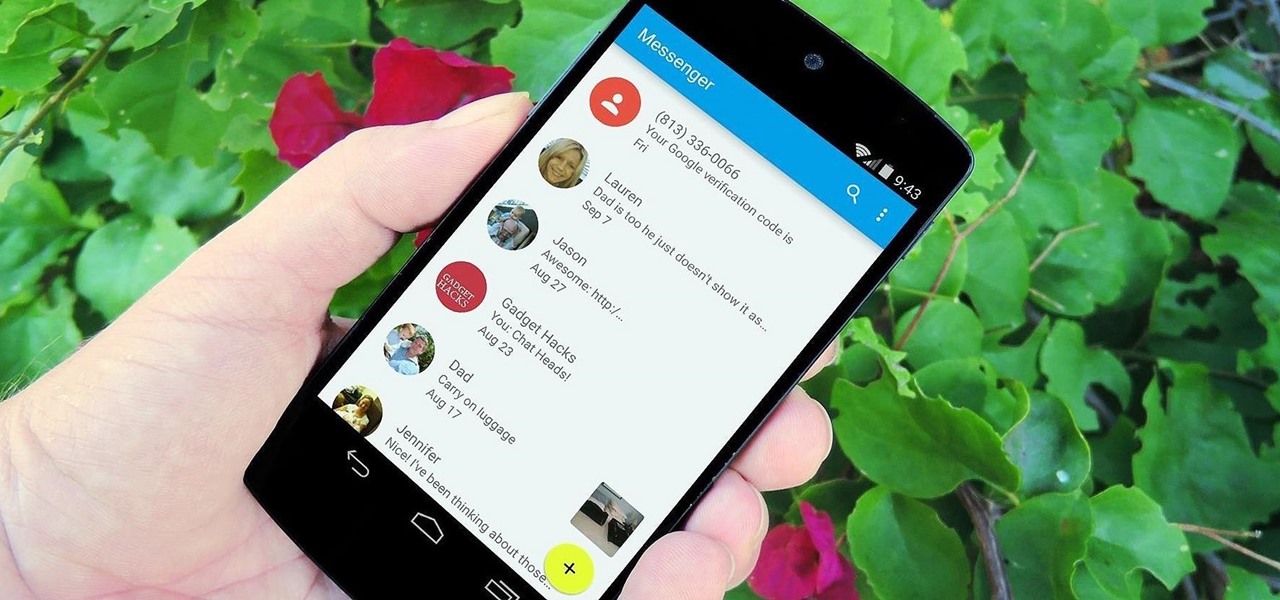
With all of the cool new animations and features in the upcoming Android 5.0 Lollipop release, some pretty awesome system apps may have been overlooked amidst the fanfare. Most noticeably, a new Messenger app was added to the OS, containing many touches of Material Design.

Welcome to the first chapter of Excel is Simple, a place where we will burst all myths around excel and try to make it simpler and fun to use.

When it comes to passwords, the longer and more complex they are, the better the security. Even professional hackers say so. But if you've ever tried to type in such a password, you've surely noticed that it can be a bit of a pain. Mistype one character, and you're probably going to have to clear the field and start all over again.

Now that all variants of the Galaxy S5 have finally been rooted, we can start exploring all of the tweaks and hacks that Superuser privileges open up to us.

When theming Android, it's the little touches that complete the look, making your device yours. If you're rooted, you probably know by now that there's virtually nothing you can't change the look of on Android.

The fact that we own a Nexus means we get to experience the Android interface exactly as Google intended it. But that doesn't mean we can't make a UI tweak here and there, does it?

A boring work meeting. A conversation with someone you don't like. A date that's going horribly. A run-in with an aggressive and intimidating stranger. These are all situations where you want to flee—and fast.

When it comes to smartphones, we can sometimes get a little carried away with the "smart" aspect of it all. Things like apps, games, and softMods take center stage, and we can almost forget that the device also functions as a phone.

Welcome back, my hackers apprentices! To own a network and retrieve the key data, we only need to find ONE weak link in the network. It makes little sense to beat our heads against heavily fortified systems like the file and database server when we can take advantage of the biggest weak link of all—humans.

What is your Samsung Galaxy Note 2 running? More than likely, you're still rocking Jelly Bean 4.1.2, which is already pretty outdated. My grandma uses 4.1.2.

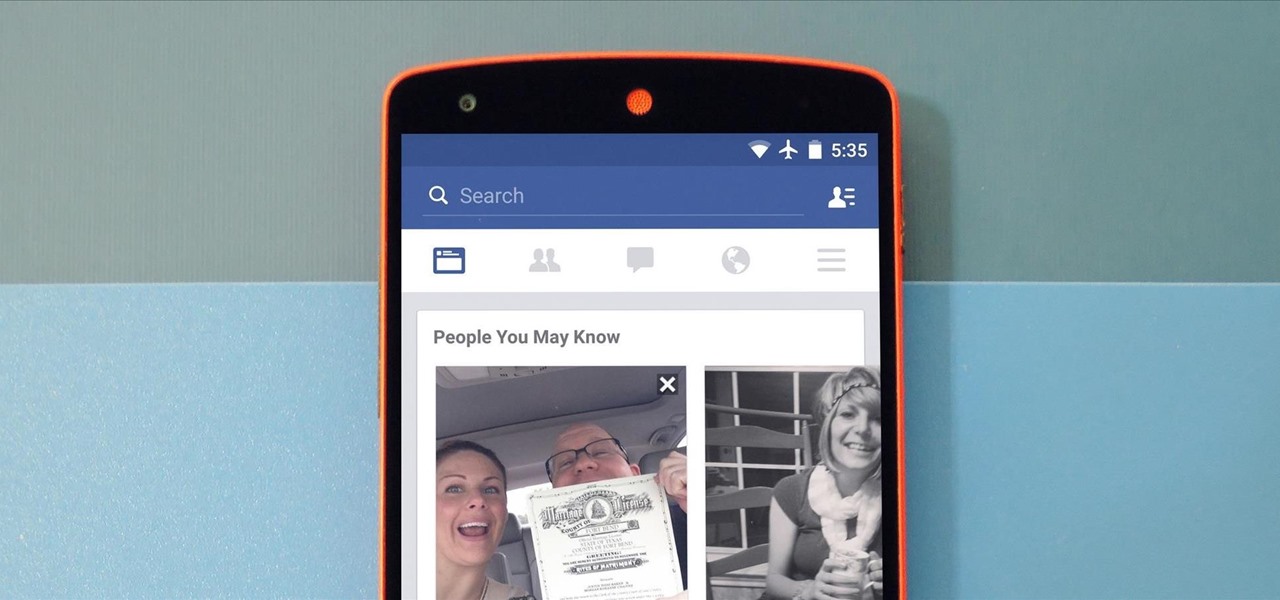
Welcome back, my fellow hackerians! Today we'll be hacking Facebook profiles on your local network. You may think, "How is this useful, nobody but me is using my network." Well, you can use this on other Wi-Fi networks that are available for free (like at Starbucks) and crack their precious Facebook profile!

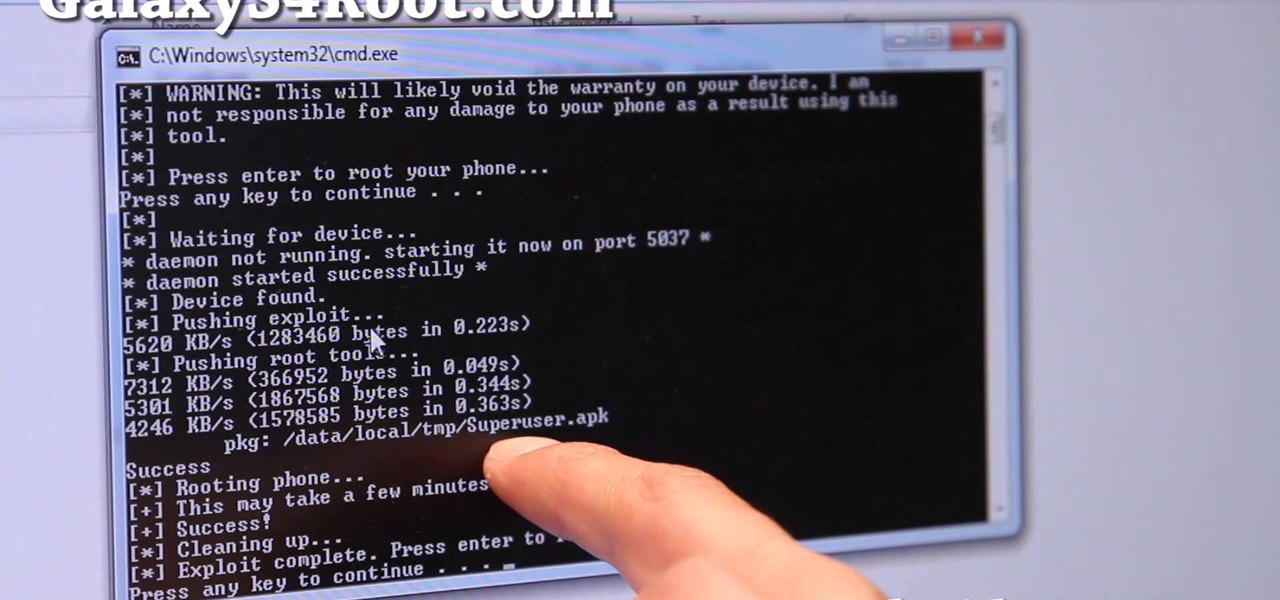
Here's a quick and easy video tutorial on how to root any Qualcomm-based U.S. or Canadian Galaxy S4 Android smartphone.

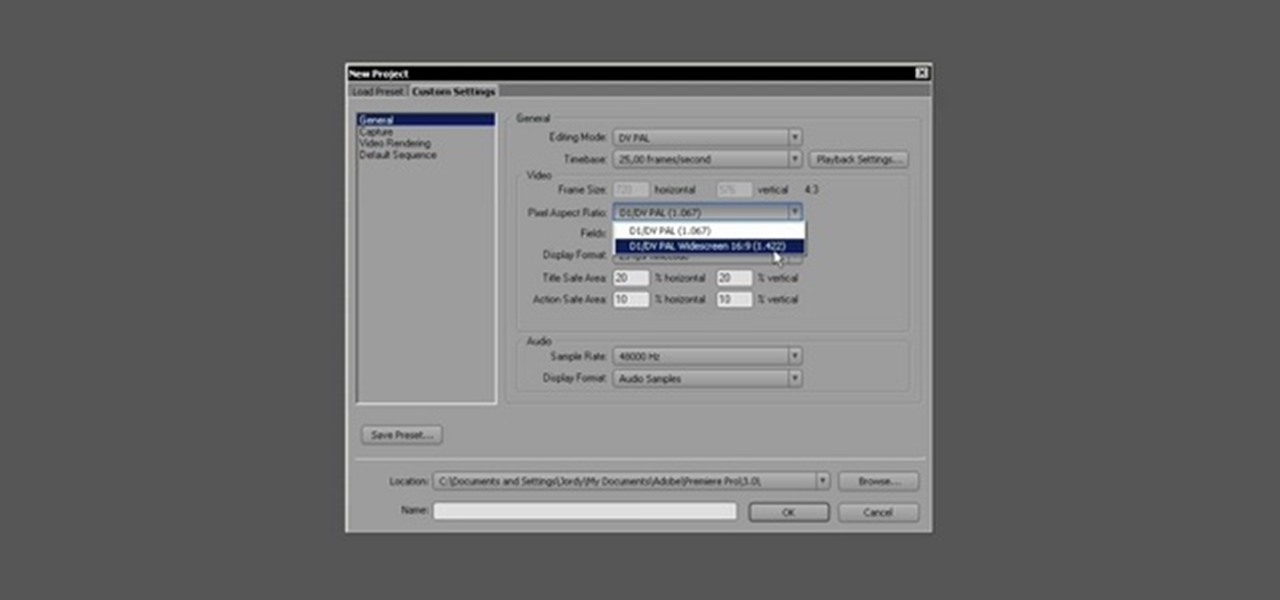
For a new user, Adobe Premier Pro can be overwhelming. There's just so much you can do! So, a little guidance, or shall we say "basic training," is what you'll need to get started editing your own home video or professional film. This five-part series is your basic training, taught by Jordy Vandeput, showing you the basic, need-to-know stuff in Premiere Pro CS3.

It's always a dilemma when you're organizing your closet and deciding whether you want to keep or throw out a meaningful old t-shirt that you don't wear anymore. Many of our t-shirts have been with us through thick and thin, so preserve their memory (and stop creating more waste) by reusing them.

Most users don't realize how much valuable data is in their network traffic. With a few simple tools, an attacker can quickly pick out cookies, passwords, and DNS queries from a macOS device as it covertly streams the victim's network traffic to the attacker's system. Here, we will cover two methods for analyzing packets flowing from a Mac.

Whether you're white hat, black hat, or some shade in-between, navigating through a network is a core part of hacking. To do that, we need to be able to explore a network to discover the addresses of gateways, interfaces, and other attached devices. When ifconfig just isn't enough, you can steer your way around a network with a convenient tool called Ship, the script for everything IP.

The default tool for payload generation is MSFvenom, a Metasploit standalone payload generator as well as encoder. This tool is an incredibly powerful tool for payload generation, but it can be difficult and requires a bit of reading for newer users.

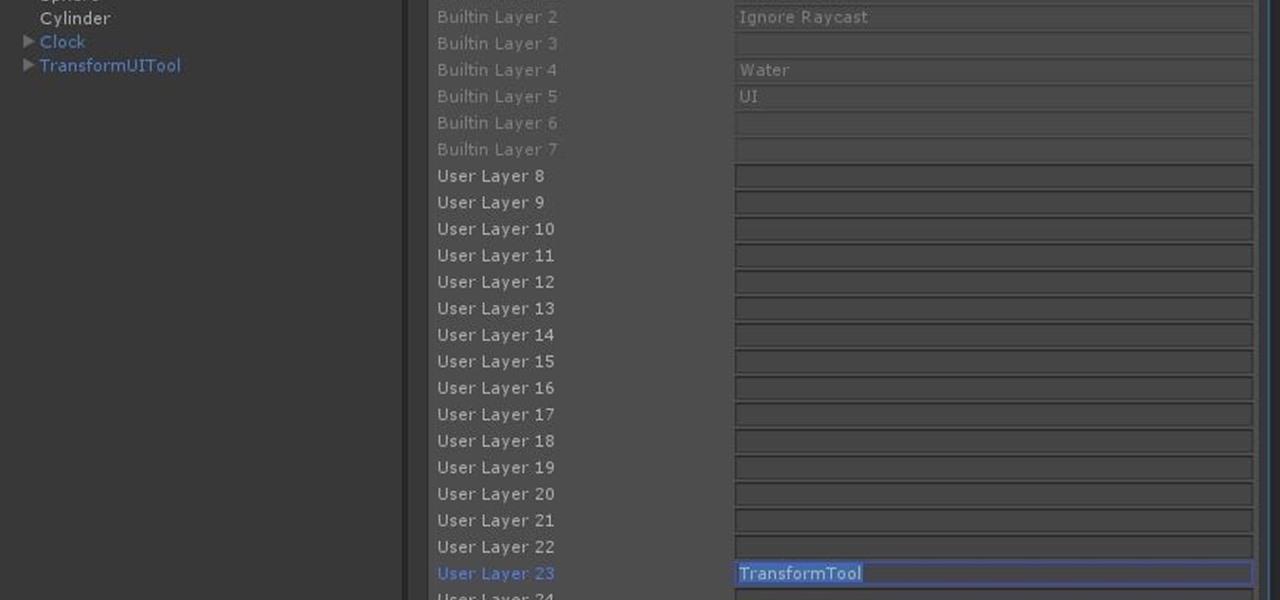
Now that we have unlocked the menu movement — which is working very smoothly — we now have to get to work on the gaze manager, but first, we have to make a course correction.

OpenVAS is a powerful vulnerability assessment tool. Forked from Nessus after Nessus became a proprietary product, OpenVAS stepped in to fill the niche. OpenVAS really shines for information gathering in large networks where manual scanning to establish a foothold can be time-consuming. OpenVAS is also helpful for administrators who need to identify potential security issues on a network.