Even if your default mobile browser is Google Chrome, you may not want Google to also be your search engine. Maybe you're not impressed with Google's search results all the time, maybe you want a more private search experience, or maybe you just don't want Google's hands over everything in your life. Whatever the case, it's easy to switch from Google to another default search engine.

While you were busy browsing Instagram, composing tweets, or chasing Snapchat updates, an eight-year-old ARKit developer was hard at work on her first step toward taking over the tech world via augmented reality.

With much of the hype centered around its powerful cameras, it's easy to overlook the equally impressive audio capabilities of the Galaxy S9. After all, the S9 and S9+ are the first Samsung flagships to feature AKG-tuned stereo speakers, and that's not even mentioning all the software enhancements that help deliver rich, immersive sound in several different listening situations.

This week's Game Developers Conference came at just the right time for Magic Leap, a company that was riding a wave of bad news from legal troubles and rumors regarding Magic Leap One.

Identifying vulnerable devices and services on a target router can be difficult without leaving logs and other traces of an active attacker on the network. However, there is a way to covertly decrypt and view Wi-Fi activity without ever connecting to the wireless network.

Google just released Android 9.0 Pie, but the Android community is already working its magic. Developer Quinny899 quickly ported the updated Pixel Launcher from the new build, so you can try it out on other phones right now.

With Nokia's relaunch, the iconic company attempted to reimagine the budget phone market. The series of phones they introduced last year challenged the idea that good phones can't be cheap. This year, Nokia introduced the Nokia 7 Plus, a phone which offers perhaps the best balance of specs, software, and price.

In any business, there are a number of questions companies must answer in order to get customers to buy a product or service. The same holds true for companies selling augmented reality headsets.

When it comes to media players, few are more capable than VLC. With its extensive codec support, VLC is able to play almost any video file. Partly due to its open-source nature, features are constantly added. This trend has continued with a new update that added native Chromecast support.

In the not so distant past, you had to actually go meet someone in person to repay money you owed them. Say they covered your half of dinner or picked up movie tickets — they wouldn't get their money back at least until the next time you saw them. Thankfully, Venmo has effectively eliminated this inconvenience.

With the Super Bowl just days away, it seems appropriate to draw parallels between football and the professional sport of technology business, or, more specifically, the augmented reality segment.

Google's Pixel lineup hangs its hat on smooth software and a polished UI. At the core of this experience is the Pixel Launcher, a home screen app that is often imitated, but never perfectly duplicated. That is, until developer AmirZ released the latest version of his Rootless Pixel Launcher port.

Your home has walls for privacy, but Wi-Fi signals passing through them and can be detected up to a mile away with a directional Wi-Fi antenna and a direct line of sight. An amazing amount of information can be learned from this data, including when residents come and go, the manufacturer of all nearby wireless devices, and what on the network is in use at any given time.

It's tough to keep pace with Apple lately. As expected, only one day after the public release of iOS 11.2.5, the company released iOS 11.3 to developers. A day after that, Apple pushed it out to public beta testers, too. With new Animoji, more transparent battery information, Apple Music receiving music videos, and more, this update is the one to watch out for.

Format strings are a handy way for programmers to whip up a string from several variables. They are designed to save the programmer time and allow their code to look much cleaner. Unbeknownst to some programmers, format strings can also be used by an attacker to compromise their entire program. In this guide, we are going to look at just how we can use a format string to exploit a running program.

The Pixel 2's camera is one of the best you'll find on an Android phone. Among its standout features is the incredible Portrait Mode, which Google accomplished with some impressive software processing. Thanks to a few clever developers, you can now enjoy the Pixel 2's Portrait Mode on your Galaxy S8 or Galaxy Note 8.

While there aren't as many ways to customize your iPhone like there is on Android, there are still a lot of apps out there that can help streamline and enhance your experience beyond Apple's own default options — and we've hand-picked over 100 essentials.

The one thing that separates a script kiddy from a legitimate hacker or security professional is the ability to program. Script kiddies use other people's tools, while hackers and security pros write their own tools. To that end, we're going to see how a stack overflow vulnerability allows us to flood a variable with enough input to overwrite the instruction pointer with our own commands.

Coinbase sets itself apart from other wallet apps by making cryptocurrency transactions incredibly convenient. You can easily withdraw cash from the app and deposit it into your bank account within days — and now, if you want to cut the time from days to mere minutes, Coinbase has you covered as well.

With the big reveal of the Magic Leap One: Creator Edition in December 2017, and now the update on Feb. 13, 2018, we no longer have to speculate as to what the augmented reality headset will look like or when (in general) it will be available.

The Sony Xperia XZ Premium brought 4K HDR to a Sony flagship along with some competitive internals, while the Xz1 brought some powerful specs in a more midrange, traditional form factor. While it only makes sense to be excited about what's coming next, Sony has yet to show us the XZ2. For now, we need to stick to the rumor mill. Thankfully, the rumor mill is a fun place to be.

It's long past time to face the facts: farts are funny. The first fart joke dates back nearly 4,000 years to the ancient Sumerian people. References to flatulence were also found in ancient Greece within the works of Aristophanes. (More like Aristo-fannies, am I right?) A standard in practical jokes, the whoopie cushion debuted way back during the time of the Roman Empire.

Features like themes and a tab queue make Firefox an extremely versatile mobile browser. Mozilla is constantly adding bonus functionality like this to Firefox, but a long-time staple is perhaps the most powerful feature: Extensions. This system gives you the ability to add features without having to upgrade the entire app.

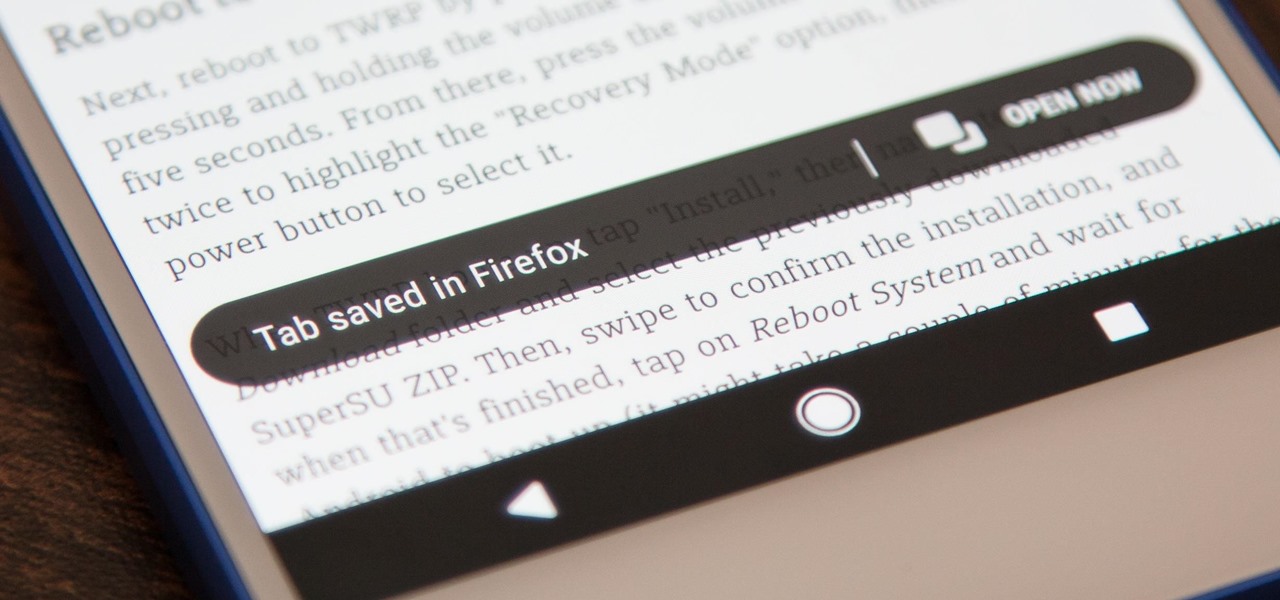
Mozilla baked an easily missed feature into their Firefox Browser for Android called the "tab queue," which you should definitely be using if you find yourself opening links a lot from emails, texts, and other link-heavy apps. With tab queuing enabled, you can save links as new tabs in Firefox without ever leaving the current app you're in.

Being able to write your own hacking tools is what separates the script kiddies from the legendary hackers. While this can take many forms, one of the most coveted skills in hacking is the ability to dig through the binary files of a program and identify vulnerabilities at the lowest level. This is referred to as binary exploitation, and today we're going to check out a tool known as Protostar.

Thanks to Metaverse, it has never been this easy to create your own AR game.

So after setting everything up, creating the system, working with focus and gaze, creating our bounding box and UI elements, unlocking the menu movement, as well as jumping through hoops refactoring a few parts of the system itself, we have finally made it to the point in our series on dynamic user interfaces for HoloLens where we get some real interaction.

The default tool for payload generation is MSFvenom, a Metasploit standalone payload generator as well as encoder. This tool is an incredibly powerful tool for payload generation, but it can be difficult and requires a bit of reading for newer users.

The Pixel 2 and Pixel 2 XL were built by different manufacturers. This is pretty common knowledge among Android fans at this point — Google's smaller Pixel 2 was built by HTC, while the larger Pixel 2 XL was built by LG. What would the Pixel 2 XL look like if HTC had followed through and delivered on the larger phone for Google? Today we have some answers.

Update 10/14: Developer paphonb has added rootless Google Now integration to the leaked Pixel 2 launcher, so now, anyone running Android Nougat or Oreo can get the full Pixel 2 home screen experience. For those running Lollipop or Marshmallow, we've left the unaltered leaked version linked out below, but we've added a new link for the tweaked version with Google Now integration.

In the case of rotting food, microbes are not our friends. Now, scientists have developed a new food wrap coated with tiny clay tubes packed with an antibacterial essential oil that can extend the shelf life of perishable food, so we can waste less and eat more.

When Disney teased an augmented reality game called Star Wars: Jedi Challenges running on a headset from Lenovo, fans had more questions than Disney had answers. When? How much? Can I be a real Jedi?

Plants all around us capture sunlight every day and convert it to energy, making them a model of solar energy production. And while the energy they make may serve the needs of a plant, the process isn't efficient enough to generate power on a larger scale. So, scientists from the University of California found a way to treat bacteria with chemicals that turned them into photosynthesis machines, capable of generating products we can convert into food, fuels, and plastics.

This morning Google announced ARCore, an SDK for Android devices that will allow augmented reality developers to add new functionality to Android 7.0 and up, all without any special hardware other than the camera of a phone.

Cross-compilation allows you to develop for one platform (like Kali) and compile to run on a different platform (such as Windows). For developers, it means that they can work on their platform of choice and compile their code for their target platform. For hackers, it means we can compile exploit code for Windows from Kali.

This week, two companies looking to capitalize on the growing augmented reality industry, raised funding from starkly different sources.

Developers in the augmented reality space are sitting on the bleeding edge of a hot technology. With the intense interest, especially in the tech circles, there are a large number of people working on potential solutions and uses for the technology. There is also a lot of time, money and effort being put in the tools and infrastructure for the technology. For better of for worse this also means constant changes.

As more companies begin adopting augmented reality in the workplace, providers like Vuzix reap the benefits.

The Audi A8 may be short on the wow factor as the industry's first Level 3 car, but Audi has revealed some interesting details about one stand-out feature underneath the hood: the car's ability to self-pilot itself at stop signs and lights.

Cruise Automation follows Waymo's and Uber's lead with its debut of a beta version of an app-based driverless ride-hailing service for its employees in San Francisco, ahead of a possible launch of a full-fledged commercial offering within four years.