Hello ladies and gentlemen, welcome back to the Part 2 of our UDP & Wireshark adventure as I promised. Last time we discussed about what DNS is and how it uses UDP as its transport protocol but we left some unexplained parts behind and I'm about to investigate those with you. I would advice you to go back to Part 1 so you can have a clear understanding in case you don't feel comfortable with the topic. So our computer made its request to the DNS server and asked "Hey, I want to find out what ...
Mostly all hackers like to have a laugh. We like to have fun! We like to troll. And maybe, even cause some havoc once in a while. But, while we do this, we must always stay in the line of the law.

Welcome back, my aspiring hackers! As I mentioned in earlier posts, the best hackers (or at least those not behind bars) have a keen understanding of digital forensics. If I am tasked to intrude upon an enemy's file server to retrieve war plans, such as in this tutorial, it is essential to my country's (and my own) well-being that it not be traced back to me. Understanding digital forensics helps us to leave without a trace and never have a trail back to us or our employer.

The other day I was perusing my Instagram when I came upon a curious hashtag... #OnePotPasta. Intrigued, I investigated further and discovered a whole world that was previously unbeknownst to me.

It has been a long while since I last came here to write an article. Graduate school keeps you busy. After I looked over what I had written previously, I decided that I should introduce another fun topic from cryptography. In this case, steganography.

Welcome back, my hacker apprentices! I recently began a new series on digital forensics to show aspiring hackers what the forensic investigator can do and see while investigating a cyber attack. This is the second installment in that series and will focus upon network forensics. In other words, what can a network forensic investigator learn about the attacker during an investigation and how.

Anyone that has ever watched a member of the opposite sex play a video game knows that the other gender does it wrong.

Like a computer, your brain can store and process large amounts of information. It can remember names, solve math problems, and save tips that you might need at a later time.

A few days ago, Russian hacker Alexy Borodin found a way to get free in-app purchases on an iPhone or iPad. In-app purchases include things like items and power-ups for iOS games, as well as subscriptions and "premium" memberships for certain apps.

In this online video you'll get tips for recognizing signs of drug & alcohol addiction from a former addict. John DePalma explains how drugs can affect the brain and the long-term affects of addiction on the body. He explains the symptoms of several types of drug use, from alcohol and marijuana, to harder drugs like cocaine, crystal meth and heroin, and warns of the dangers of abusing prescription drugs like pain killers and anti-anxiety drugs as well. He then explains how to approach an addi...

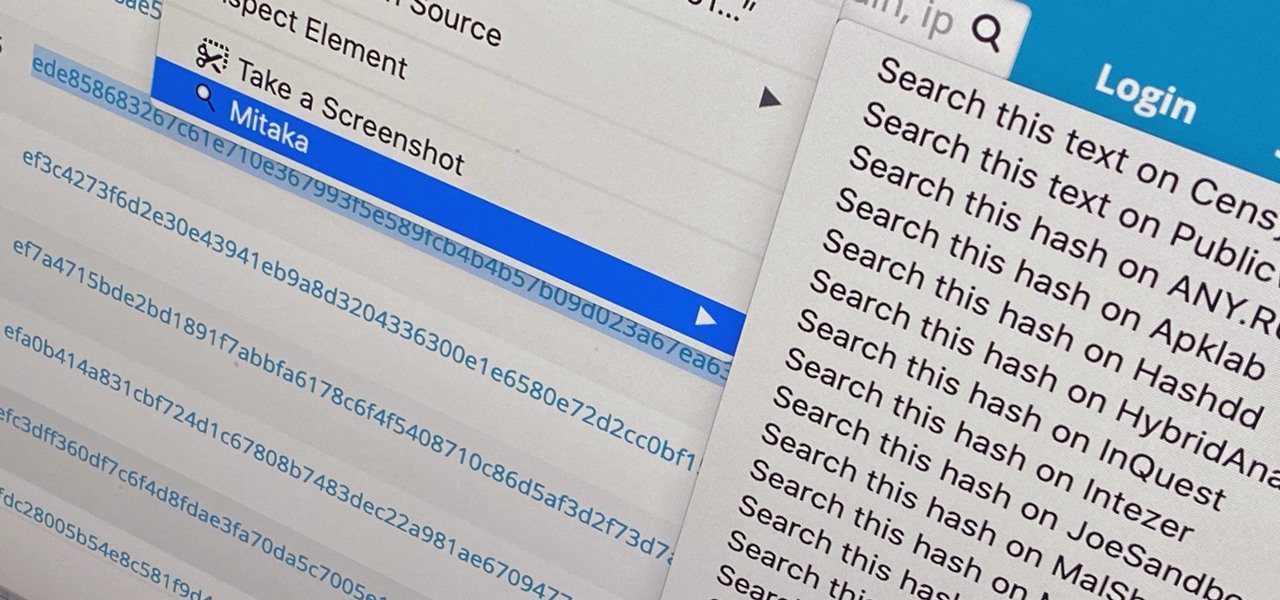
Web browser extensions are one of the simplest ways to get starting using open-source intelligence tools because they're cross-platform. So anyone using Chrome on Linux, macOS, and Windows can use them all the same. The same goes for Firefox. One desktop browser add-on, in particular, makes OSINT as easy as right-clicking to search for hashes, email addresses, and URLs.

Grab your PSP and get ready to ROCK Metal Gear Solid: Peace Walker! This video walkthrough guide will take you through every mission, from the main ones to the secondary ones. Follow along and learn the tips and tricks to the gameplay so you can beat the game yourself! Peace Walker is the fifth installment in the Metal Gear series.

The true crime genre has long been popular on television and more recently on podcasts with shows like Serial.

Open-source intelligence researchers and hackers alike love social media for reconnaissance. Websites like Twitter offer vast, searchable databases updated in real time by millions of users, but it can be incredibly time-consuming to sift through manually. Thankfully, tools like Twint can crawl through years of Twitter data to dig up any information with a single terminal command.

With a simple social engineering trick, sudo passwords can be captured in seconds without the target's knowledge. The passwords can then be saved to a file or exfiltrated to another computer on the network.

It's important to know who you're dealing with after hacking your target's MacBook. Getting remote access is simple, but covertly gathering information about the user and their system can be a challenge.

Nmap is possibly the most widely used security scanner of its kind, in part because of its appearances in films such as The Matrix Reloaded and Live Free or Die Hard. Still, most of Nmap's best features are under-appreciated by hackers and pentesters, one of which will improve one's abilities to quickly identify exploits and vulnerabilities when scanning servers.

On June 11, 2016, an Arizona woman died from what appeared to be several infections, including pneumonia. She likely caught at least one of these from her dog.

Regarding foodborne pathogens, eating fish is not as hazardous as it was a few years ago — but if fins are on the menu, it's good to have a heads-up about what's good and what's bad these days.

Just like your gastrointestinal tract, and the soil we walk on — a dust storm has a collection of bacteria, fungi, and viruses all its own called a "dust microbiome."

Most people are familiar with the decline of honeybee colonies around the world. Among other threats, Colony Collapse Disorder (CCD) is eroding the capability of honeybees to maintain their hives and provide their services to human farmers.

Food is both a necessity and a joy. Many people enjoy exploring, cooking, eating, and learning about foods from around the world. But the picture isn't always rosy. A new report from the Centers for Disease Control and Prevention (CDC), highlights the ways and whereabouts of food that make us sick.

Think of the coolest, most unique way to create art that you can. Got it? Now think about creating that art out of living things.

While no longer native to the United States, hospitalization from malaria occurs in this country more than most would believe. Why is that, and what can you do to protect yourself when you travel abroad to regions where malaria is active?

You can get eggs and high-quality compost from backyard chickens—but you can also get Salmonella.

Add antibiotics to the possible list of culprits responsible for honeybee decline around the world. While it may come as a surprise, antibiotics are commonly mixed into feed used by commercial beekeepers to maintain their hives. In a recent study published in PLOS Biology, researchers from the University of Texas at Austin found antibiotics used to treat honeybees may be a contributing factor in individual bee death and colony collapse.

Jostled in the airport, someone is coughing in line. The air looks empty but it is loaded with microbes that make their way into your body. You get sick. You give it to your family, and that's pretty much it. But what if you were so contagious that you spread it to your entire community and beyond?

As researchers learn more and more about our intestinal bacteria—also called the gut microbiome—we're finding out that these microbes aren't just influencing our health and wellness, they're a useful tool for improving it, too.

Hear me out. No, really. Before you sharpen your pitchforks and give me anecdotal evidence of your Chinese restaurant syndrome, I think you need to know a few things about monosodium glutamate. First of all, it's a naturally-occurring chemical compound that can be found in anything from tomatoes to cheese, and is used in all kinds of foods from KFC to breakfast sandwiches. So spare me the comments on MSG and Chinese food—you probably eat MSG on a daily basis without even knowing it. (And also...

Whenever I went to the grocery store on a mission for blueberries, I'd inevitably find myself staring at these weird little tomato-looking berries... and wondering what the hell they really were. Tomatoes? Berries? A weird science experiment? Then, I'd set a pint of blueberries in my cart and carry on, forgetting about them for the time being.

"It just ticked me off," he said. In March 2011, Neil Singh paid $50 to back the Hanfree iPad stand on Kickstarter. The project was funded at $35,000, but production stalled, and the delivery estimates kept getting pushed back.

Welcome back everyone. I apologize for the lack of training articles, but I've been rater busy lately. I've recently picked up a second job and my college courses are now back in session, so I'm a bit strapped for time.

Welcome back, my novice hackers! In this series, we have been exploring how a forensic investigator can find evidence of illegal or illicit activity. Among other things, we have examined the registry and prefetch files for artifacts and have done some rudimentary forensic analysis. For those of you who are seeking career as a forensic investigator or security engineer, this can be invaluable training. For hackers, it might be life-saving.

My first ever post on here was 'Keeping your hacking identity secret' and it did very well, and its not something I see here on null byte. So read along.

To me, the term muffin tin is a lot like Voldemort—it should never be uttered. Not for being evil, however... instead, it's because it's inaccurate.

Welcome back, my hacker apprentices! A you know, Mr. Robot is my favorite TV show this year, and not just for the realistic hacking. Rami Malek, the actor who plays Elliot, is incomparable in his depiction of a young man with social anxiety who is alienated from a superficial, materialistic society and wants to make a better world. I believe we will see a lot more of this actor in coming years.

Welcome back, my rookie hackers!

Biting into a perfectly ripened piece of fruit is enough to convince you to give up baked goods and plant your own garden. The combination of flavor, juice, and sweetness in a ripe mango, apple, plum, or berry is the stuff of life itself.

Welcome back, my fledgling hackers! A short while ago, I did a tutorial on conducting passive OS fingerprinting with p0f. As you remember, p0f is different from other operating system fingerprinting tools as it does not send any packets to the target, instead it simply takes packets off the wire and examines them to determine the operating system that sent them.