
News: HIV Co-Opts the Body's First Line of Defense—Using It as a Shuttle to Take Over
A new study just out reveals that HIV takes hold in the human body with the help of cells that usually work to heal, not kill.


A new study just out reveals that HIV takes hold in the human body with the help of cells that usually work to heal, not kill.

Responding to the emergence of Zika in the US, researchers investigated what type of repellent works best to reduce your odds of a mosquito bite from Aedes aegypti, the mosquito species that spreads the Zika virus.

Sometimes you need a password to gain access to an older running Windows system. Maybe it's a machine in your basement you forgot about or a locked machine that belonged to a disgruntled employee. Maybe you just want to try out your pentesting skills.

After California college student Luis Ortiz blacked out and was taken to the hospital in 2015, doctors were startled to discover the reason his brain was swelling—a one-centimeter long, wriggling tapeworm living within a ventricle in the middle of his brain.

Cholera may be rare in the US, but cases of the disease have increased worldwide since 2005, particularly in Africa, southeast Asia, and Haiti. An estimated 3 to 5 million people are infected, and more than 100,000 die from the disease globally each year, mostly from dehydration.
Starting in October, many Nexus 6P users have been experiencing a bug that causes their phone to completely shut down, even though there was 20% or more battery life remaining. At first, it was thought to be a direct result of the recent Android Nougat update, but a combination of factors indicate that this isn't necessarily the case—or, at least, it's not the only problem.

When the HoloStudy Demo app for HoloLens came out in September, it was a pretty impressive start to what could be a very valuable science tool for education. Now, Moscow-based HoloGroup, makers of HoloStudy, started an Indiegogo campaign to improve their modular teaching app.
When Google released the first Developer Preview build of Android 7.0 Nougat, users were happy to see that a new "Night Mode" was included among the changes. The feature would cancel out any blue light emitted from your screen to help you get to sleep a bit earlier, quite similar to f.lux for desktop computers, or Apple's Night Shift for iPhones. It could be set to turn on automatically based on time of day, or you could manually enable Night Mode with a Quick Settings toggle.

If you could save the world by eating a burger, would you? Two companies, Beyond Meat and Impossible Foods, are on a mission to redefine veggie burgers and eliminate all of the downsides of animal farming on our planet. With over five years of research and product testing, they've finally figured out how to make a plant-based burger look, feel, and taste just like real meat.

To become a tried-and-true Pokémon master in Pokémon GO, there's an incredibly important decision that needs your attention: Team Instinct, Team Mystic, or Team Valor?
If you want free Poké Balls and eggs when playing Pokémon GO, you can find them at PokéStops in variation locations around your city, which are marked with towering blue icons on your map. Once you're at Level 5, they'll also grant you Potions and Revives to help you in your battles against other trainers, so they're definitely something you should be visiting whenever you can.

Android's stock battery menu is pretty decent. You can see which apps have been using the most power, and you can tell when your CPU was awake or asleep, among other things. But a lot of times, battery-sucking services will get lumped under the generic "Android System" header, and even though you can see when your CPU was awake, you can't exactly see why.

Hello ladies and gentlemen, welcome back to the Part 2 of our UDP & Wireshark adventure as I promised. Last time we discussed about what DNS is and how it uses UDP as its transport protocol but we left some unexplained parts behind and I'm about to investigate those with you. I would advice you to go back to Part 1 so you can have a clear understanding in case you don't feel comfortable with the topic. So our computer made its request to the DNS server and asked "Hey, I want to find out what ...
Mostly all hackers like to have a laugh. We like to have fun! We like to troll. And maybe, even cause some havoc once in a while. But, while we do this, we must always stay in the line of the law.

The telecommunications industry has come a long way since Ma Bell opened the first telephone exchange in the late 1800s. With the advent of fiber optics and wireless broadband technology, we no longer have a need for a dedicated phone connection, as today's data networks can carry much more than a simple voice conversation.

Welcome back, my greenhorn hackers! As hackers, we often take for granted that nearly all of our hacking tools and operating system are free and open source. I think it's important to examine a bit of background on how we arrived at this intriguing juncture in the history of computer software. After all, we pay for nearly all of our other software (Microsoft, Adobe, etc.) and nearly everything else we use in life, so how is it that Linux and all our hacking tools are free?

Welcome back, my aspiring hackers! As I mentioned in earlier posts, the best hackers (or at least those not behind bars) have a keen understanding of digital forensics. If I am tasked to intrude upon an enemy's file server to retrieve war plans, such as in this tutorial, it is essential to my country's (and my own) well-being that it not be traced back to me. Understanding digital forensics helps us to leave without a trace and never have a trail back to us or our employer.

If you took a big step back and really looked at the world, you'd see how downright silly our nations look when they put up fences to separate themselves from one another. Creatures big and small roam free while respecting each other's space, but humans create borders and physical barriers to delineate their cultures.

The other day I was perusing my Instagram when I came upon a curious hashtag... #OnePotPasta. Intrigued, I investigated further and discovered a whole world that was previously unbeknownst to me.

While most of us don't think twice about dragging a pattern or using Touch ID to open our phones, or entering a password in for our email and bank accounts, these features are there to protect some of our most private information. Only problem is, they don't do a good job of it.

Welcome back, my budding hackers! People often ask me, "Why are you training hackers? Isn't that illegal?" Although I usually give them a short version of this post, there are MANY reasons why YOU should be studying hacking.

It has been a long while since I last came here to write an article. Graduate school keeps you busy. After I looked over what I had written previously, I decided that I should introduce another fun topic from cryptography. In this case, steganography.

Ever since the much-lauded effects of the Mediterranean diet became widely known, people have been buying olive oil by the gallon. A diet that prevents heart disease, is based on fresh, seasonal foods, and includes a tasty as hell fat like olive oil? Duh—that's a no-brainer.

Welcome back, my hacker apprentices! I recently began a new series on digital forensics to show aspiring hackers what the forensic investigator can do and see while investigating a cyber attack. This is the second installment in that series and will focus upon network forensics. In other words, what can a network forensic investigator learn about the attacker during an investigation and how.

Anyone that has ever watched a member of the opposite sex play a video game knows that the other gender does it wrong.

Like a computer, your brain can store and process large amounts of information. It can remember names, solve math problems, and save tips that you might need at a later time.

"You can never know too much" is a saying you hear all the time. Funny thing is, I have no idea where it originated, and neither do most of the people who continually say it. Nevertheless, it's a statement that very few would argue with.

Thrift stores! As a Steampunk, they can be your best friend, but it's easy to make a tragic mistake. This hands-on guide will help you navigate the murky waters of successful thrifting in order to find the hidden gems that will make your Steampunk outfit complete!

Steampunk is a tremendously interesting phenomenon because of its reliance on science fiction, and fiction in general. Steampunk can arguably be broken down into two categories: the fiction, and the aesthetic. Sometimes these categories cross over, but they're often more distinct than most people suspect; that said, the aesthetic is firmly based in works of fiction.

A few days ago, Russian hacker Alexy Borodin found a way to get free in-app purchases on an iPhone or iPad. In-app purchases include things like items and power-ups for iOS games, as well as subscriptions and "premium" memberships for certain apps.

The DROID 2 from Motorola came out last August, but it's just now exploding— literally. The 33 News reported yesterday that a Motorola DROID 2 smartphone exploded in the hands of Aron Embry from Cedar Hills, Texas. He was making a phone call outside his home when he heard a POP sound— blood was dripping down his face and the glass was broken around the phone's speaker— his DROID 2 cell phone actually exploded against his ear. He ended up getting 4 stitches and a CAT scan, but thankfully, he d...

This how-to is aimed at the uncynical, bright-eyed outsider who wants to become a television producer…the talented person who believes he or she has the ‘it’ to crack Hollywood. The ‘Sammy’ who just arrived in 90210.
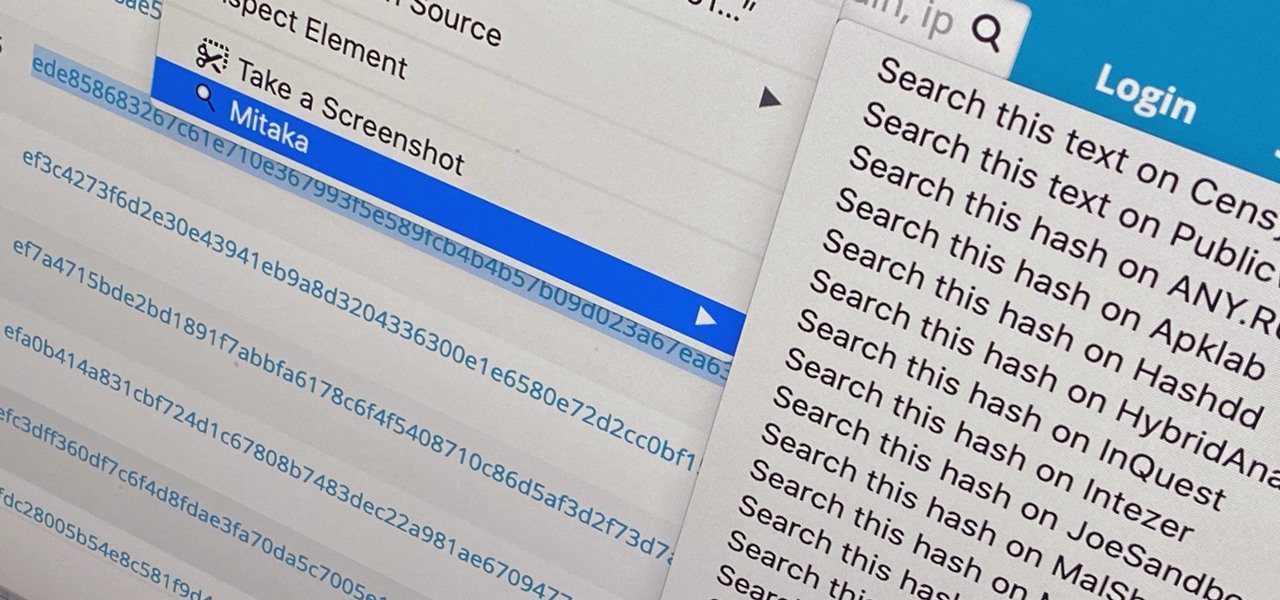
Web browser extensions are one of the simplest ways to get starting using open-source intelligence tools because they're cross-platform. So anyone using Chrome on Linux, macOS, and Windows can use them all the same. The same goes for Firefox. One desktop browser add-on, in particular, makes OSINT as easy as right-clicking to search for hashes, email addresses, and URLs.

Grab your PSP and get ready to ROCK Metal Gear Solid: Peace Walker! This video walkthrough guide will take you through every mission, from the main ones to the secondary ones. Follow along and learn the tips and tricks to the gameplay so you can beat the game yourself! Peace Walker is the fifth installment in the Metal Gear series.

Oh yeah, this is a big topic, at-least for me. All the frequent flyers will/should be interested in this topic. I'm sure all of you have heard at-least something about the TSA, and most of it should have been bad. Complaints, lawsuits and general disgust surround this organization. Is there a reason, or are the 'extremist liberals' at it again? Let's find out!

Grand Theft Auto 3 was the biggest video game of the last decade, by far, introducing open-world adventure games to consoles, a genre that now rivals shooters and sports games for market dominance. A huge map, decentralized narrative, and myriad of interlocking quests and objectives that happen in a flexible order all became hallmarks of the "new" genre, along with the ability to shape the morality and reputation of your character. And most importantly, all of the quests and stories are compl...

The relationship between developers and publishers in the video game industry has always been awkward. Many great game developers such as Bizzare Creations, Clover Studio, and Bullfrog Productions have been disbanded due to corporate shenanigans involving their publishers and owners. The indie game movement has risen largely as a response to this.

The widely used expression "free as a bird" intimates an enviable existence: delicate, yet mighty wings transporting to destinations no human could so breezily venture. But despite their fanciful, superhero ability, in truth, the avian race leads one of the most difficult existences in the animal kingdom. Yes, birds have existed for eons—they likely evolved from small dinosaurs of the Jurassic period—but for these creatures, life can be ruthless.

China is a hot mess of traffic and is stereotyped for spawning some of the craziest drivers in the world. The traffic jams are known to be so bad, drivers have been gridlocked for 9 straight days.
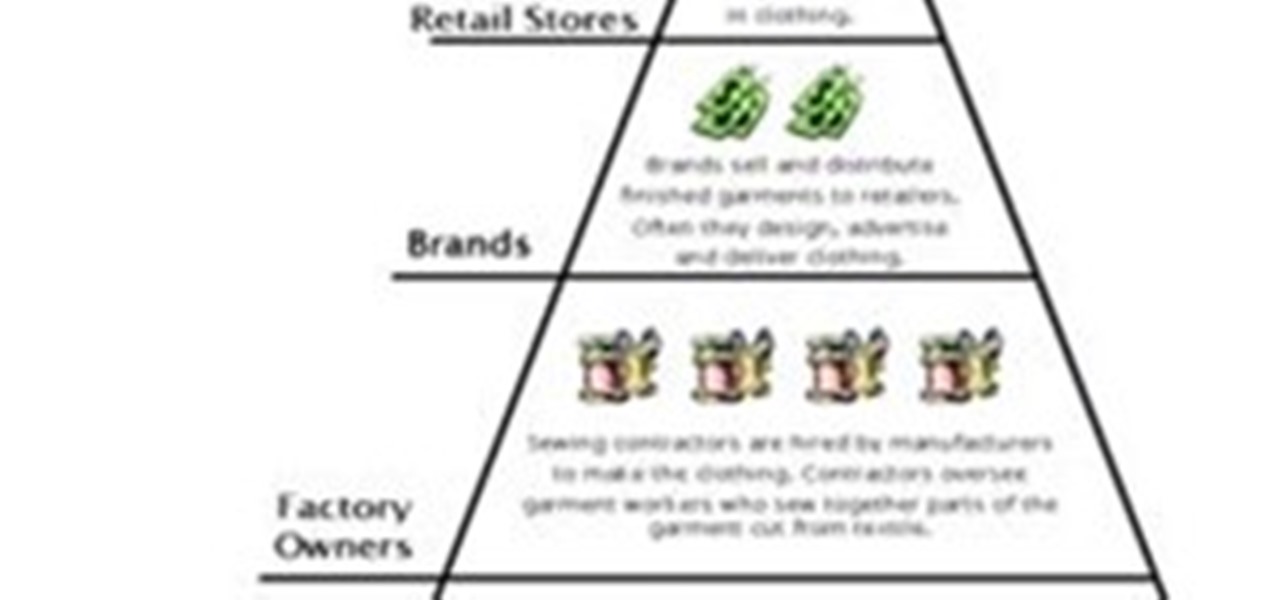
The United States is a hierarchical country where the weak ones are at the bottom and the powerful ones are at the top. Garment workers are at the bottom of the list although they are the most important. Without them there would be no fashion industry. They sew and cut the garments that people buy, the raiment that models wear on the runways. After the garments are sewn, factory owners send the garments to contractors to get make the clothing. Contractors make sure the garment workers sew the...