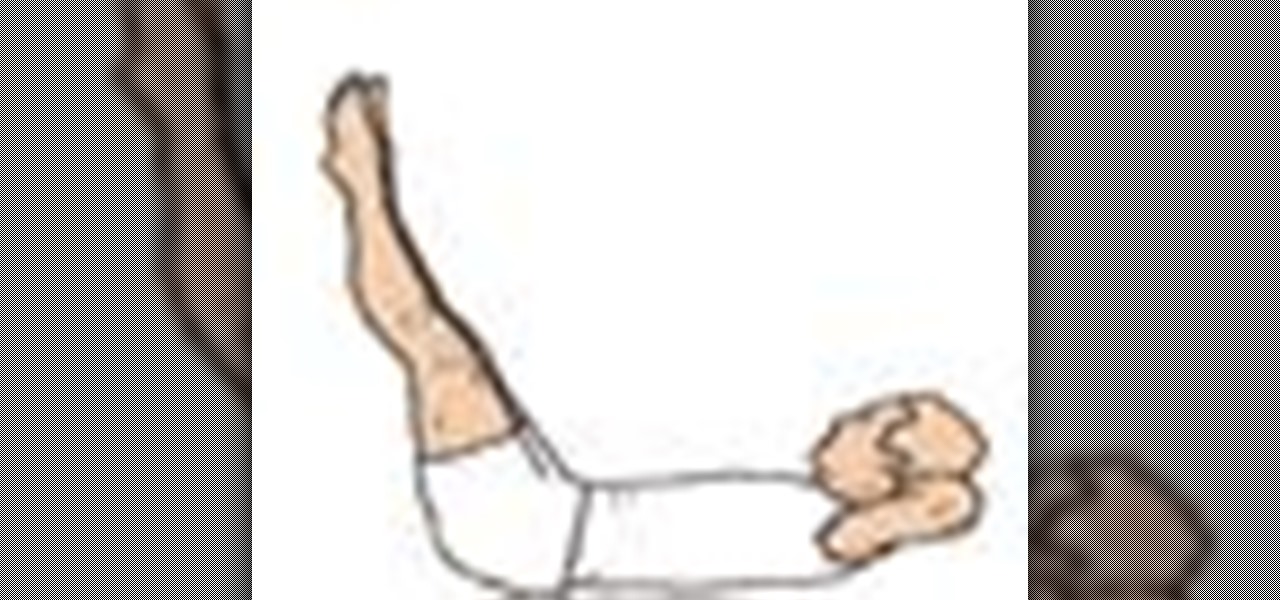
Search "Pilates animation" on Wonderhowto for other more videos by this user. If you are looking a for a quick pilates reference, take a look at this pilates animation. This a quick & easy, clearly explained diagram of the pilates mat exercise: Classical Pilates for Beginners:

Search "Pilates animation" on Wonderhowto for other more videos by this user. If you are looking a for a quick pilates reference, take a look at this pilates animation. This a quick & easy, clearly explained diagram of the pilates mat exercise: Classical Pilates for Beginners:

Search "Pilates animation" on Wonderhowto for other more videos by this user. If you are looking a for a quick pilates reference, take a look at this pilates animation. This a quick & easy, clearly explained diagram of the pilates mat exercise: Classical Pilates for Beginners:

Search "Pilates animation" on Wonderhowto for other more videos by this user. If you are looking a for a quick pilates reference, take a look at this pilates animation. This a quick & easy, clearly explained diagram of the pilates mat exercise: Classical Pilates for Beginners:

Search "Pilates animation" on Wonderhowto for other more videos by this user. If you are looking a for a quick pilates reference, take a look at this pilates animation. This a quick & easy, clearly explained diagram of the pilates mat exercise: Classical Pilates for Beginners:

There’s a lot going on in your head when creating a comic book and it doesn’t stop after it’s done. There are other things that you have to do once your comic book goes online. You have to market it, introduce it to the right market, and find a way how to get it published.

We've provided Google insiders, Google's community managers, authors, and celebrities for you to add to your circles. This week, we've discovered over 100 brilliant photographers for you to follow.

Are you tired of counting your hair while waiting for your computer or laptop to respond? Then, these easy steps are perfectly fit for you, especially if you're a Windows 7 user.

As many of you know Windows is not the most secure Operating System in the world, but then again no OS is really secure if the user doesn't know how to protect themselves. Later I will show you how to lower the risk even more on your (the user's) end.

Today's digital cameras record not only the images themselves, but also the metadata behind the scenes, like camera settings, location, date, time, etc. But there's a lot more to say about a photograph. What's the subject? Is it night or day? Outside or inside? Person, place or thing?

So you want to learn the basics of the fantastic language Java, but you don't want to search the Inter-webs looking for a great tutorial. Well you came to the right place, now may I present to you JAVA.

In my Wireshark article, we talked a little bit about packet sniffing, but we focused more on the underlying protocols and models. Now, I'd like to dive right back into Wireshark and start stealing packets.

If you live in an urban environment, chances are that you've seen this: It's a program started by the FBI to prevent terrorism and general thievery in peaceful and innocent communities all around America. I myself have seen a lot of these, and my previous apartment community was part of this 'program'.

TOP MOVIES 2011 The Artist (2011)

For any of you not in the loop, last week marked our first ever WTFoto Challenge. The goal was to find the craziest, most absurd stock photo on the web we've never seen before. There were a lot of WTF images submitted to our community corkboard, and now it's time to announce the results of the stock image showdown. Who will win the the honor of Watermark of Weirdness? Drumroll please, imaginary band leader named Tim Drickles...

Google is great. They provide us with tons of free services and open source APIs that we can code fun tools for, one of which I don't think gets enough credit: Google Voice.

Your first, very basic web crawler. Hello again. Today I will show you how to code a web crawler, and only use up 12 lines of code (excluding whitespaces and comments).

This is it! That last basic mission. Last Friday's mission was to accomplish solving HackThisSite, basic mission 11. This final mission in the basic series was made to give us the skills and a place to apply our Apache server knowledge. This will teach us how to traverse through awkward and custom directory structures.

Watch out Instagram, there's a new free, sociable photography filter app that hit the iTunes App Store recently, and it just might be some good competition. It's called PicYou and might sound familiar to some of you photo sharing fiends out there. That's because it's been a successful web-based alternative to Instagram for about six months now.

Skyrim is a time consuming game. I know I'm not alone in saying I constantly find myself looking for more time in the day. There is never enough time to read the books I want to read, or learn what I want to learn, or play the games that I want to play.

The days of entering left, right, left, right, up, down, up, down, a, b to cheat your way through a video game are long gone. With achievements and trophies in existence, game developers have, for the most part, removed cheats from video games.

If you haven't seen one, a comet is one of the most spectacular astronomical objects in the sky, partially because it is so close to Earth. At the closest, it is only 1.3 a.u. (194,477,400 kilometers) away from Earth. Comet C/2009 P1 Garradd was discovered by Gordon J. Garradd on August 13, 2009. It never comes closer to the sun than Mars's orbit. Usually, a comet moves fast, but it has stopped moving so fast recently, making it really easy to observe. It can be observed by a telescope or wit...

Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server. Well this is it folks, the final Pre-Release before Minecraft officially launches! These changes should be the final game changes until it releases in Vegas this Friday. Mojang has made it clear, however, that they will continue making changes to the game while it's released.

Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server. Minecraft Pre-Release 1.9 Version 6 is out! This update includes more bug fixes from Version 5 and Ender Dragons! We'll be reporting more changes as we find them, so stay tuned.

To the displeasure of many loyal Firefox users, Mozilla has been deploying what seems like a new marketing strategy to "catch up" to Google Chrome. I have no idea if this is because the version number is higher than theirs, but it is downright annoying. It's not all complaints, though. Firefox has done an amazing job at completely revamping its source code and redesigning all of its engines, making it a more than worthy competitor to Chrome. However, we are displeased with Firefox because eve...

As we all know, security is a big thing here in Null Byte. We've talked quite a bit about ways to encrypt traffic and become anonymous on the internet, some of which entail using proxies, VPNs, and SSH tunnels. We've also talked about preference using SSL pages in practice for safe logins. These are all great protocols and tools, but aren't without their flaws and inconveniences.

Our mission for this week's Community Byte was to create a Python program to crack web-based passwords, like the ones you would see on an email or router login. I wanted it to be universal in the sense that it could be easily modified and adapted to another website just by changing a few variables. That was a success! Even though people weren't on time to the coding session, everything went well.

Welcome to part two in a series about steganography, the art of hiding things in plain sight. We are practicing steganography because it can be a useful skill if you don't have access to encryption software, or need a quick solution to make sure the sender and recipient are the only ones who are able to read your message.

Cheating. It happens everywhere. From scientists faking human ears on mice, to Hollywood thirty-somethings cheating on their quadragenarian wives, to chess players accusing supercomputers of fraud. There's no game or profession out there that doesn't have a cheater or two, but the bigger nuisance is probably those people who accuse others of cheating.

Giveaway Tuesdays has officially ended! But don't sweat it, WonderHowTo has another World that's taken its place. Every Tuesday, Phone Snap! invites you to show off your cell phone photography skills.

Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server. We're back again for another Pre-release!

Often times when staying at a hotel or anywhere for that matter, you'll whip out your laptop and check the local area for Wi-Fi. I know you've all been in my shoes when you find an unsecured network that appears to be public Wi-Fi belonging to the hotel or airport, and you connect to it. You connect fast and perfectly, only to find that when you open your browser, it says you don't have an account, and are filtered from accessing the web. This is because the owners of the network want to keep...

The internet is a scary place, and if you're like me, you don't want anyone tracking you or learning your search habits. It's a blatant invasion of privacy for companies to do this, but at least we have methods of fighting back—one of which is Tor.

Since its release three years ago, Canon's EOS 5D Mark II has been the most sought out digital SLR for photographers everywhere. But it's also becoming a favorite amongst cinematographers, thanks to its compact size and high-def video recording mode, seeing action in everything from independent features to Hollywood blockbusters and even big network TV shows.

These days, I keep multiple browsers open so I can keep track of all my work and personal items. As a staff member of WonderHowTo, a lot of my work is done through our Google Account, which is separate from my personal Google Account.

There are over 250,000 apps in the Android Market, ranging from free productivity programs to a ridiculous $200 for a vuvuzela horn effect. But chances are you don't have the vuvuzela app on your Android smartphones right now, but you are likely to have one of the ten most popular apps in the Android Market.

+Eric Cattell, the Social Graph Technical Lead of Google+, announced a lot of improvements and added features this morning, most of them having to do with circle management and blocking people.

Public Radio Exchange (PRX) has teamed up with music intelligence company The Echo Nest to bring us music lovers Bandito, an easy way to find out what's going on with our favorite artists. Their new mobile app uses the existing iTunes library on your iPad, iPhone or iPod touch to find your most-played bands and singers, serving up the latest news from around the web on them.

More than a year ago, Twitter rolled out the first phase of its Promoted Tweets ad service, which consisted of selected tweets from advertising partners like Best Buy and Sony Pictures receiving "promoted" exposure in the search results pages on Twitter and in the trends lists. These ads were clearly labeled as such, so it was never any real bother to Twitter users.

Now that you can invite anyone you want to Google+, the floodgates are open. If you've been bummed out about not being able to share the joys of Google+ with your friends and acquaintances, make use of that handy envelope icon the right side of your stream page. Just enter the email addresses of the people you want to invite, and hit the "Invite" button.