Any developer working with the HoloLens knows that the fight for polygons is a very real conflict. For all of the magic it creates, the HoloLens is a high-powered mobile device that has all the typical processing limitations of a mobile device.

Some of the products I have been looking forward to seeing the most during CES 2017 has been the upcoming Windows Holographic virtual reality headsets. These are VR headset that will run a version of the Windows Holographic platform, which will allow users to have a similar experience as the HoloLens with a mixed reality environment. Of the six headsets that could have possibly made it to CES, five had shown up. Unfortunately, most of them are behind glass.

Well, we have some potentially good news for those wanting to experience Magic Leap. The ultra-secretive company seems to be planning a big year in 2017.

Designing for mixed reality, especially for the HoloLens, can present unique challenges. Dong Yoon Park, a Principal UX Designer at Microsoft with a passion for typography, recently gave a talk to the Windows Holographic Users Group Redmond (WinHUGR) about the pitfalls he ran into trying to convert what started out as a 2D iOS app 5 years ago to the newer 3D Holographic frontier with Unity.

In the world of analog synthesizers, hitting a key, twisting a knob, or sliding a fader makes a beautiful musical (or not so musical) sound and can be an amazing and downright satisfying experience. Now it's about to get even more satisfying, if you add Microsoft's HoloLens into the mix as a means to twist those knobs virtually instead.
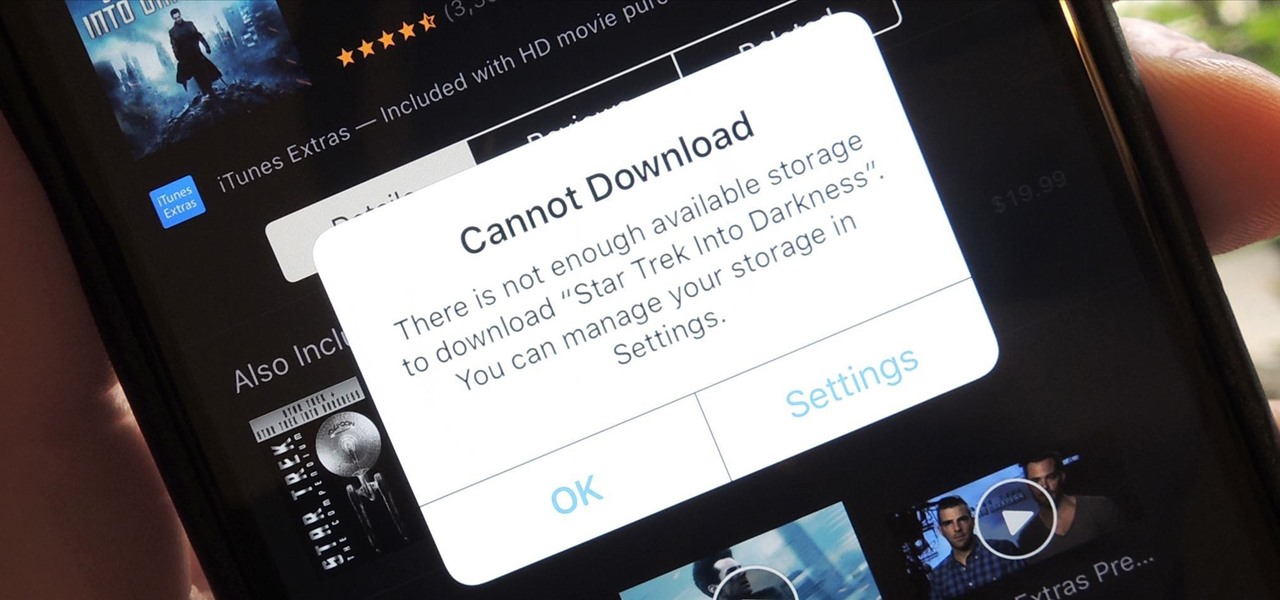
Clearing storage space is a constant concern for people with iPhones, especially since they don't come with expandable storage, limit the amount of free iCloud storage, and still, unfathomably, produce units with only 16 GB of space. Thankfully, Reddit user eavesdroppingyou shared this quick and easy tip you can use to wipe unnecessary files from your phone and potentially free up gigabytes worth of storage.

This is my first tutorial on this website. So, if you think anything to be wrong, just place it in the comments.

It's already that time of year again—LG has unveiled its latest high-end smartphone, dubbed the G4. In past iterations, LG released its flagship devices in the fall. But slowly over the course of the past 2 years, the release schedule has been bumped up to be more in line with HTC and Samsung's springtime releases, and further away from the sales-sucking iPhone event each fall.

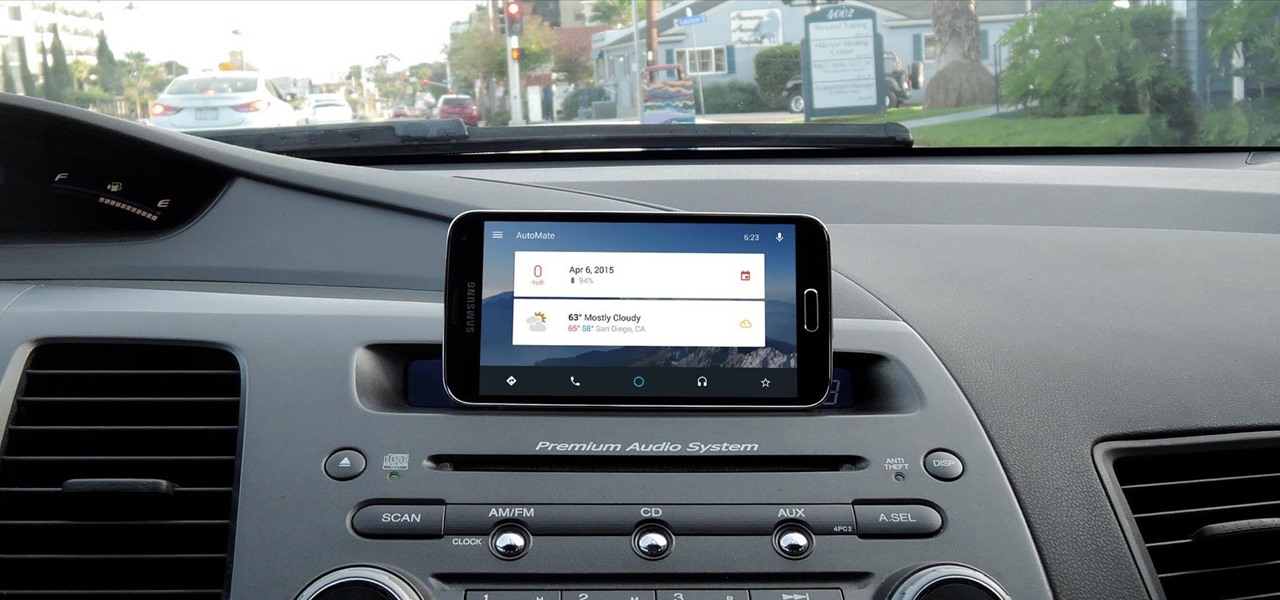
Auto manufacturers are slowly starting to debut models with Google's new Android Auto software baked into the dashboard console. Starting with the 2016 model year, we should see vehicles from Honda, Ford, Chevrolet, and many others sporting the new software.

Beginning with KitKat, I've been used to customizing every aspect of my Android phone, but with the release of Lollipop, there is quite a bit of catching up that developers need to do. Most customization features, like quick settings rearrangement and theme support have already been ported over, but any type of lock screen customization has been noticeably absent.

As far as wallets go, mine is as full as they come; think something like George Castanza's overstuffed wallet on Seinfeld. I've got receipts, pictures, and tickets jammed inside, but what takes up the bulk of the space are all of the cards—credit, debit, gift, rewards, customer loyalty... I've got pretty much any card you can think of squeezed in. While it is a strain on my rear end, there's nothing I can do besides keep some of the cards elsewhere. However, looking for them when I need them ...

Coffee is a topic that everyone has a strong opinion about, especially when it comes to brewing the perfect cup. Even if you buy the best beans and grind them yourself, chances are you're skipping one necessary step to make sure your coffee tastes the best it can: cleaning your coffeemaker the right way.

Samsung unveiled their new flagship device, the Galaxy S4, at a live event in New York City today. Here's a quick rundown of the specs and all of the new features that you can expect when you finally get your hands on one (whenever that will be). The GS4's Specs

Apple has begun selling their new iPad mini at stores around the world starting today. The mini, a smaller and cheaper alternative to the larger iPad, has a starting price of $329 and is expected to sell around 1 to 1.5 million units in the first weekend, far below the 3 million iPad 3s sold last March (who all probably want their money back). Something that's sure to be brought up in the following days, as with most new devices, is the battery life. As we previously provided you tips on savi...

Accidents will happen. This brief how-to will guide you through the process of disassembling your HP iPAQ hw6500, hw6510 (hw6510a, hw6510b, hw6510c, hw6510d, hw6510g), hw6515 (hw6515a, hw6515b, hw6515c, hw6515d, hw6515f), rw6815, rw6818, rw6828, hw6900, hw6910, hw6915, hw6920, hw6925, hw6940, hw6945, hw6950, hw6955 or hw6965 series pocket PC quickly and efficiently without damaging any of the components, the first necessary step of any successful repair. This tutorial will also be of use to t...

Fans of "The Hitchhiker's Guide to the Galaxy" will remember the Babel fish, the universal translator you put in your ear so you can understand every language you hear. While Apple has its Translate app, there's another iPhone feature reminiscent of the Babel fish, but it lets you convert measurements, times, and other units without having to leave the app you're currently using.

Everyone has used a ruler at some point in their life, whether for art sizing, blueprint plans, or sizing up your widescreen television on your living room wall. But there's a lot of little ticks on the ruler that you may not be aware of. Your ruler shouldn’t be used only to draw a straight line. Make sense of all those little lines and take advantage of its intended use.

A home air conditioner is nearly as vital as the electricity that powers it. Learn how to replace a home air conditioning unit with tips from a professional HVAC technician in this free home improvement video series.

Last year, your iPhone's Weather app received some great features, but things are even better now with the latest iOS 17 version.

In the great smartglasses race, component makers, such as those that supply the crucial waveguide displays that make visualization of virtual content possible, have a vested interest in pushing the industry forward in order to ship units.

It is well documented that what you say and do online is tracked. Yes, private organizations do their best to protect your data from hackers, but those protections don't extend to themselves, advertisers, and law enforcement.

SSH, or the secure shell, is a way of controlling a computer remotely from a command-line interface. While the information exchanged in the SSH session is encrypted, it's easy to spy on an SSH session if you have access to the computer that's being logged in to. Using a tool called SSHPry, we can spy on and inject commands into the SSH sessions of any other user logged in to on the same machine.

Brute-forcing is an easy way of discovering weak login credentials and is often one of the first steps when a hacker finds network services running on a network they gain access to. For beginners and experienced hackers alike, it's useful to have access to the right tools to discover, classify, and then launch customized brute-force attacks against a target. BruteDum does it all from a single framework.

Gathering information on an online target can be a time-consuming activity, especially if you only need specific pieces of information about a target with a lot of subdomains. We can use a web crawler designed for OSINT called Photon to do the heavy lifting, sifting through URLs on our behalf to retrieve information of value to a hacker.

By far the most significant development for AR in the coming months and years — the development that will drive AR adoption — will be our reliance upon the AR cloud.

If you're ever faced with a situation of handing over your iPhone to law enforcement (or getting it taken forcibly), whether by the police, feds, or court system, there are things you can do to prevent them from getting access to all that potentially self-incriminating data. And it takes less than a second.

Many online users worry about their accounts being breached by some master hacker, but the more likely scenario is falling victim to a bot written to use leaked passwords in data breaches from companies like LinkedIn, MySpace, and Tumblr. For instance, a tool called H8mail can search through over 1 billion leaked credentials to discover passwords that might still be in use today.

In most macOS hacks, a non-root terminal is used to create a backdoor into the device. A lot of damage can be done as a low-privileged user, but it has its limitations. Think twice before granting a file permission to execute — an attacker might be able to convert your harmless scripts into persistent root backdoors.

Augmented reality is beginning to leak out into the mainstream world. This is thanks, in part, to ARKit and ARCore. These releases turned the current smartphones owned by millions of Apple and Android users into AR-capable machines. And while there are definitely some awesome use cases for mobile AR, the real future in AR is headworn.

Windborne microbes shifting in the snows of the great ice sheet of Greenland may be able to neutralize some of the industrial contaminants oozing out of the melting ice.

The best go-to method for reducing your risk of infection is to wash your hands. Next time you reach for the soap, here is some news you can use.

Most carmakers now agree with Waymo that piloting driverless cars is best left to the machine — with no meddling from the human.

With new diet and health claims coming at you everyday, it's sometimes hard to know what to believe. Well, here's a bright spot: A pair of studies confirm that whole grains are healthy for you, and for the diversity of microbes living in your gut.

Kuru is called the shaking disease, its name derived from the Fore word for "to shake." Caused by an organism that infects the part of the brain that controls coordination, people afflicted with kuru shake uncontrollably.

Cats give us so much—companionship, loyalty, love... and now the bird flu. Several weeks ago, a veterinarian from the Animal Care Centers of New York City's Manhattan shelter caught H7N2 from a sick cat. According to a press release from the NYC Health Department on December 22, "The illness was mild, short-lived, and has resolved." This isn't the first time cats have passed infections on to humans, but it is the first time they passed on the bird flu—avian flu H7N2, to be exact.

Even when no one is in your kitchen, it is crowded. The refrigerator, sink, and counters are all covered with microbes that are just hanging around. They are inadvertent remnants from the raw chicken you used in that recipe last night, brewing a bacterial cocktail in your Nespresso machine, or just growing their merry little colonies on your leftovers.

I've seen my fair share of heartbreaks when it comes to used phones. As a repair tech, I often had to try and help out customers who bought used handsets which turned out to be useless, either because it was stolen or not working on their carrier's network. More often than not, there was very little I could do. To help you from being stuck in the same situation, here are some tips to prevent you from getting scammed out of your hard earned money when buying a used handset.

Welcome back, my novice hackers! In this series, we have been exploring how a forensic investigator can find evidence of illegal or illicit activity. Among other things, we have examined the registry and prefetch files for artifacts and have done some rudimentary forensic analysis. For those of you who are seeking career as a forensic investigator or security engineer, this can be invaluable training. For hackers, it might be life-saving.

My first ever post on here was 'Keeping your hacking identity secret' and it did very well, and its not something I see here on null byte. So read along.