The crime procedural show is the perhaps the most direct path to the average TV viewer's heart. Could the same hold true for augmented reality games?

It turns out that coming up groundbreaking technology and raising billions may actually be the easy part for Magic Leap, as a new report has revealed yet another legal entanglement at the Florida-based company.

The National Transportation Safety Board (NTSB) said it is still investigating the circumstances of a fatal Tesla crash last year to determine if the car or Tesla's Autopilot driverless system was at fault, but revealed more details about the circumstances of the crash.

Uber CEO and co-founder Travis Kalanick is taking an indefinite leave of absence from the company, as Uber's recent upheaval has far overshadowed any developments in its driverless initiative during the past few days.

Okay, I have a confession to make. I'm not a real New Yorker. I'm from the land of southern hospitality and steaks bigger than your newborn: Texas. I don't know how to hail a taxi yet, and I still smile at strangers on the street. I'm slowly learning how to fit in, but one thing I still haven't mastered is the New York City subway system. Every day, I struggle to determine where to find my train and how to stand on it without falling over. Fortunately, Google Maps appears to be making some of...

Welcome back my precious hackerians. Today i would like to promote an OS which i have been using for the past couple months. I'm not talking about Backtrack 5 or Kali Linux. Something even more promising:

At the recent DefCon conference in Las Vegas, researchers opened many of the top commercially available gun safes with simple tools like a straw or a paper clip, and in one case, just by shaking it a bit. The investigation began after the researchers, Toby Bluzmanis, Marc Tobias and Matt Fiddler, learned that certain Stack-On safes, issued to some law enforcement officials to secure their firearms at home, could be opened simply by jiggling the doorknob.

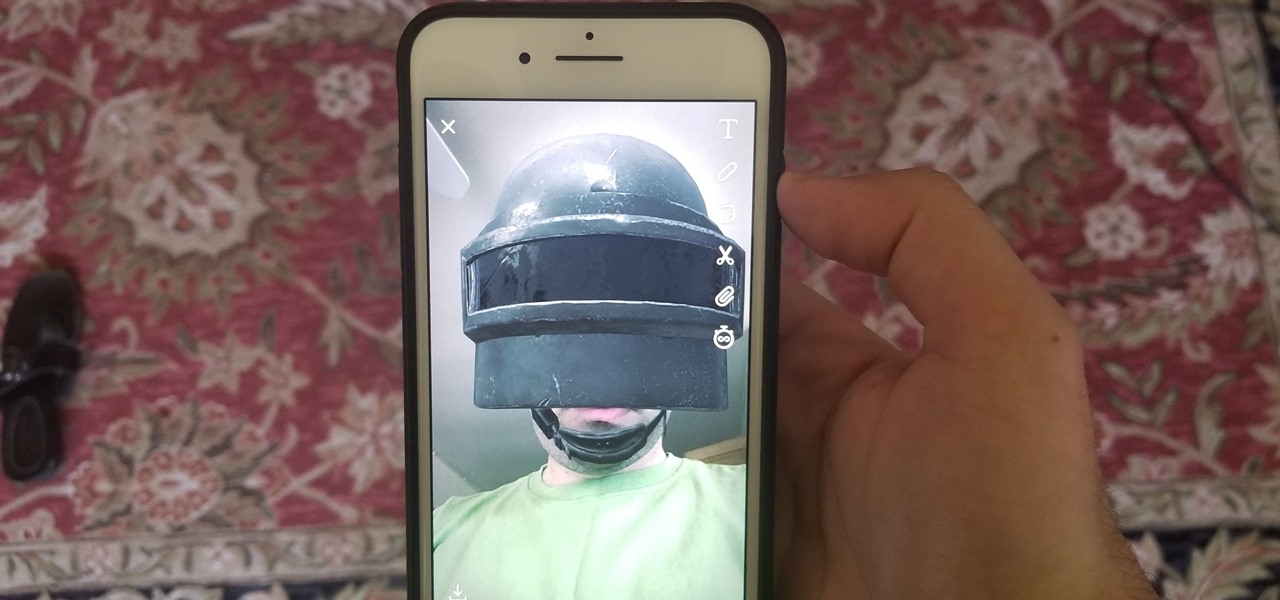
Spring is finally here (in earnest now), and a new batch of great augmented reality Snapchat lenses have come along with it. New life has been breathed into meme culture with the spring lineup of TV shows, Mark Zuckerberg's ongoing investigation, and college kids with too much time on their hands.

A new study shows the Zika virus is present in saliva — but it may not be enough to make you sick. The Centers for Disease Control and Prevention notes there is "no evidence that Zika can be transmitted through saliva during deep kissing." Given the results of research published in the journal, Nature Communications," the agency may need to revise its guidance.

Uber's driverless cabs began picking people up in Arizona in February, after its attempt at a pilot test in San Francisco. Now, one of these cars has been in an accident, and that's just the tip of the iceberg.

Do you have a file (or many files) that, in the wrong hands, may cause you trouble? Don't worry about it, because I'll show you how to wipe it (or them) from your computer in order to leave no trace behind.

So, how does someone keep their hacking life completely secret? What This Is:

In part one of this tutorial we found out that your English teacher is a paedophile, by using a Man in the Middle attack to intercept his internet traffic.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

The results of Microsoft's $480 million contract with the US Army are on display and users continue to test the suped-up version of the HoloLens 2.

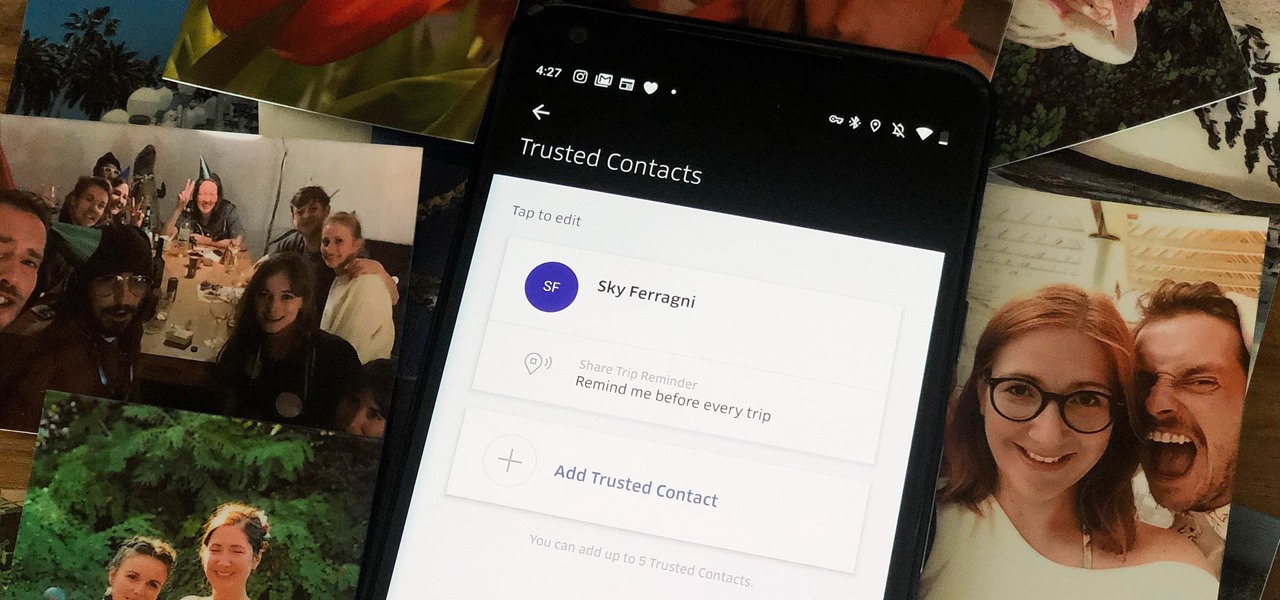
When you're riding in an Uber, on your way to meet family or friends, they may want to know where you are exactly to see how long until your arrival. On the other side of the coin, there may be times when you want to tell family or friends where you and your Uber car are without them asking, like when you're in a dangerous situation. Uber makes this easy, as long as you set it up first.

In recent months, the Magic Leap One has frequently tied promotions to groundbreaking entertainment properties, but the latest may be the startup's biggest coup yet.

Despite its status as a hot commodity amongst emerging technologies, the augmented reality industry is not immune to the ebbs and flows that occur in every industry.

As if the swollen, painful joints of rheumatoid arthritis weren't enough, the disease is the result of our immune system turning against cells of our own body. Ever since this realization, scientists have worked to find the trigger that sets the immune system off. Scientists believe that gut bacteria may have a role in initiating the abnormal immune response. Now, a team of researchers from Boston has figured out how that might occur.

People who have heart disease get shingles more often than others, and the reason has eluded scientists since they first discovered the link. A new study has found a connection, and it lies in a defective white cell with a sweet tooth.

Alzheimer's disease — an irreversible, progressive brain disorder — is the sixth leading cause of death in the US and more than afflicts 5 million Americans. As if those numbers aren't scary enough, the Centers for Disease Control and Prevention expect that number to nearly triple by 2050.

While Lyme disease can be disabling, the wrong treatment for the infection can be fatal.

We fight cancer in a variety of ways, but no matter whether drugs, biologics, or our immune cells are part of the battle, they can do a better job fighting back cancer if we can help them find the tumors.

Yellow fever has emerged again in Brazil, causing death and disease to people unprepared for this mosquito-borne illness.

In the summer of 1976, 4,000 American Legionnaires descended upon the Bellevue-Stratford Hotel in Philadelphia, Pennsylvania, for a four-day convention. Several days later, many of the attendees experienced symptoms of severe pneumonia. By the beginning of August, 22 people had died. The Centers for Disease Control and Prevention (CDC) estimate that about 180 people were sickened and 29 people died before this mysterious outbreak burnt out.

New weapons are needed to combat antibiotic-resistant bacteria. Instead of drugs, scientists have discovered in an animal study that they may be able to harness vampire bacteria to vanquish pneumonia.

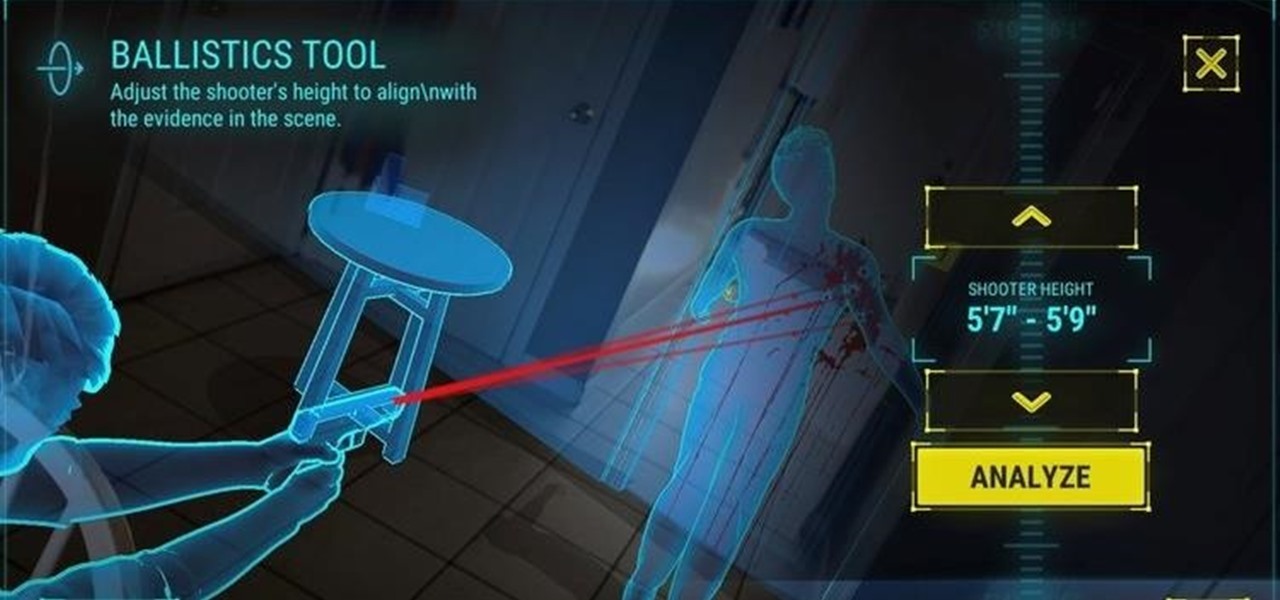
Welcome back, my greenhorn hackers! In many cases when a computer, phone, or mobile device is seized for evidence, the system will have graphic images that might be used as evidence. Obviously, in some cases these graphic images may be the evidence such as in child pornography cases. In other situations, the graphic images may tell us something about where and when the suspect was somewhere specific.

Welcome back, my aspiring hackers! In this series, we continue to examine digital forensics, both to develop your skills as a forensic investigator and to avoid the pitfalls of being tracked by a forensic investigator.
Mostly all hackers like to have a laugh. We like to have fun! We like to troll. And maybe, even cause some havoc once in a while. But, while we do this, we must always stay in the line of the law.

Welcome back, my fledgling hackers! In this series, I am trying to develop your knowledge of digital forensics, which is valuable whether you're choosing a career in it or just want to know how your hacker activity can be traced. Few professional digital forensic investigators have a hacking background, but the best ones do.

Welcome back, my amateur hackers! When you are using and administering Linux, it is important to be conversant in the use of the log files. As you know, log files are the repository for much information about our system, including errors and security alerts.

Welcome back, my greenhorn hackers! In previous Wi-Fi hacking tutorials, I have shown you ways to create an Evil Twin, to DoS a wireless AP, and to crack WEP and WPA2 passwords, but in this tutorial, I will show you something a little bit different.

Welcome back, my hacker apprentices! I recently began a new series on digital forensics to show aspiring hackers what the forensic investigator can do and see while investigating a cyber attack. This is the second installment in that series and will focus upon network forensics. In other words, what can a network forensic investigator learn about the attacker during an investigation and how.

It is well documented that what you say and do online is tracked. Yes, private organizations do their best to protect your data from hackers, but those protections don't extend to themselves, advertisers, and law enforcement.

By far the most significant development for AR in the coming months and years — the development that will drive AR adoption — will be our reliance upon the AR cloud.

If you're ever faced with a situation of handing over your iPhone to law enforcement (or getting it taken forcibly), whether by the police, feds, or court system, there are things you can do to prevent them from getting access to all that potentially self-incriminating data. And it takes less than a second.

In most macOS hacks, a non-root terminal is used to create a backdoor into the device. A lot of damage can be done as a low-privileged user, but it has its limitations. Think twice before granting a file permission to execute — an attacker might be able to convert your harmless scripts into persistent root backdoors.

Windborne microbes shifting in the snows of the great ice sheet of Greenland may be able to neutralize some of the industrial contaminants oozing out of the melting ice.

The best go-to method for reducing your risk of infection is to wash your hands. Next time you reach for the soap, here is some news you can use.

Most carmakers now agree with Waymo that piloting driverless cars is best left to the machine — with no meddling from the human.