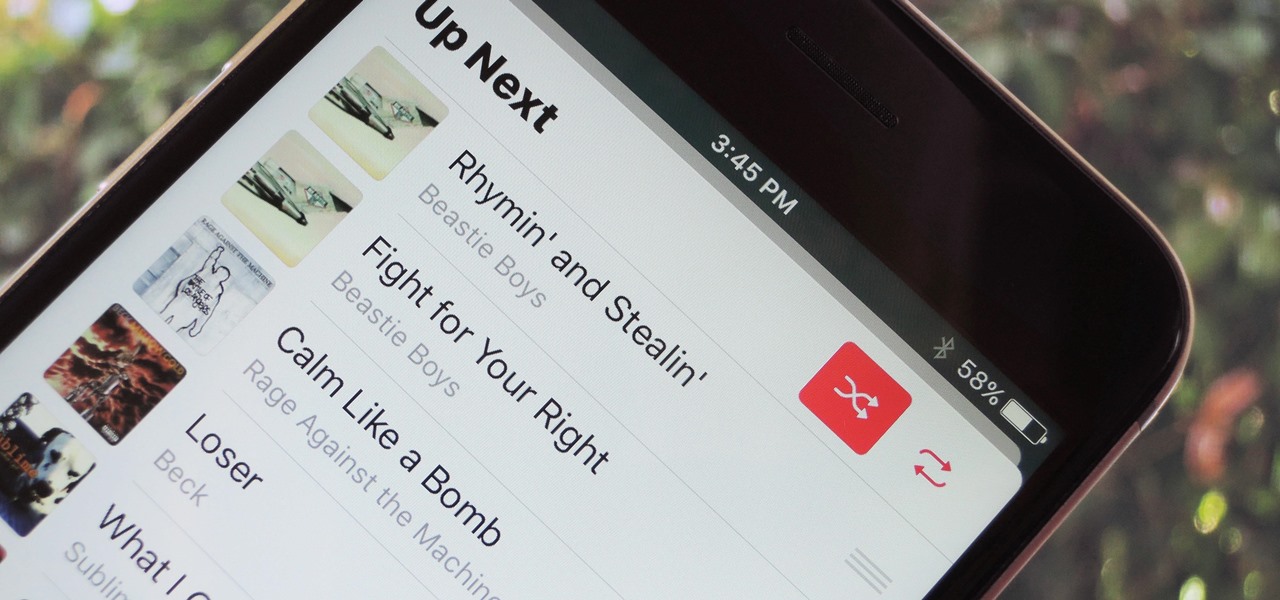
With each update, Apple Music continues to become a bigger part of iOS. It's gotten to the point where you have to fend off multiple requests to subscribe to the streaming music service before you can listen to your own songs on an iPad or iPhone, but as it stands in iOS 10, maintaining your own MP3 library is still possible. Just barely.

Remember that feeling when you first took your smartphone out of the box, powered it on, then proceeded to futz around with it for the rest of the day non-stop? If you've owned your device for more than a year, chances are, that scenario is a distant memory by this point.

I am officially breaking up with my daily breakfast of avocado toast and embarking on a promising new relationship with savory oatmeal. Yes, you read that right—savory oatmeal.

Welcome back, my rookie hackers! The Golden Fleece of hackers is to develop a zero-day exploit, an exploit that has not been seen by antivirus (AV) software or and intrusion detection system (IDS). A zero-day exploit is capable of skating right past these defenses as they do not contain a signature or another way of detecting them.

This is the easiest cookie batch you'll ever bake, I promise. And no, take-and-bake cookie dough doesn't count. With this recipe, it'll take you less than 20 minutes to go from your sad, cookie-less life to cookies in your absolute favorite flavor... of cake.

The Google Now on Tap feature puts the power of Google Search inside each and every application on your Marshmallow-powered device, allowing you to retrieve contextual results based on the content on your screen.

Android Beam is one of those features that makes you look at technology in awe, wondering how exactly something like that works.

welcome back my masters , teachers and classmates , in this second part of this 0-day series we will learn the basic of fuzzing, and i bought some gift for nullbyte(a 0 day vuln that will be released today exclusively on null-byte) .

Arcade games have always been more about chance than skill (at least when I play them). Whether you're at a children's party at a Chuck E. Cheese's or drinking it up with your pals at a barcade like Dave & Buster's, you'll find similar games that hold the golden ticket to fun and cheap prizes that no one needs—boy, do you want them.

Whether it's the start, middle, or end of summer, it's prime-time grilling season. If you find yourself without a grill, however, it may seem as if half your summer plans of swimming by the pool while stuffing hot dogs in your face could be ruined.

Ah, bello risotto. There are few comfort foods in the world that provide the same savory creaminess. Yet for all its simplicity, risotto has gotten a bad rap as a difficult dish to cook. In actuality, nothing is further from the truth.

Soda bread, corned beef and cabbage, and colcannon are all great dishes to serve up on St. Patrick's Day, but desserts really let your inner leprechaun come out to play. Not only can you have fun incorporating all kinds of tasty Irish liquors into baked goods, you get to dye things green.

Welcome back, my fledgling hackers! With this first article, I am initiating a new series intended to convey to my readers the skills necessary to develop your own exploits.

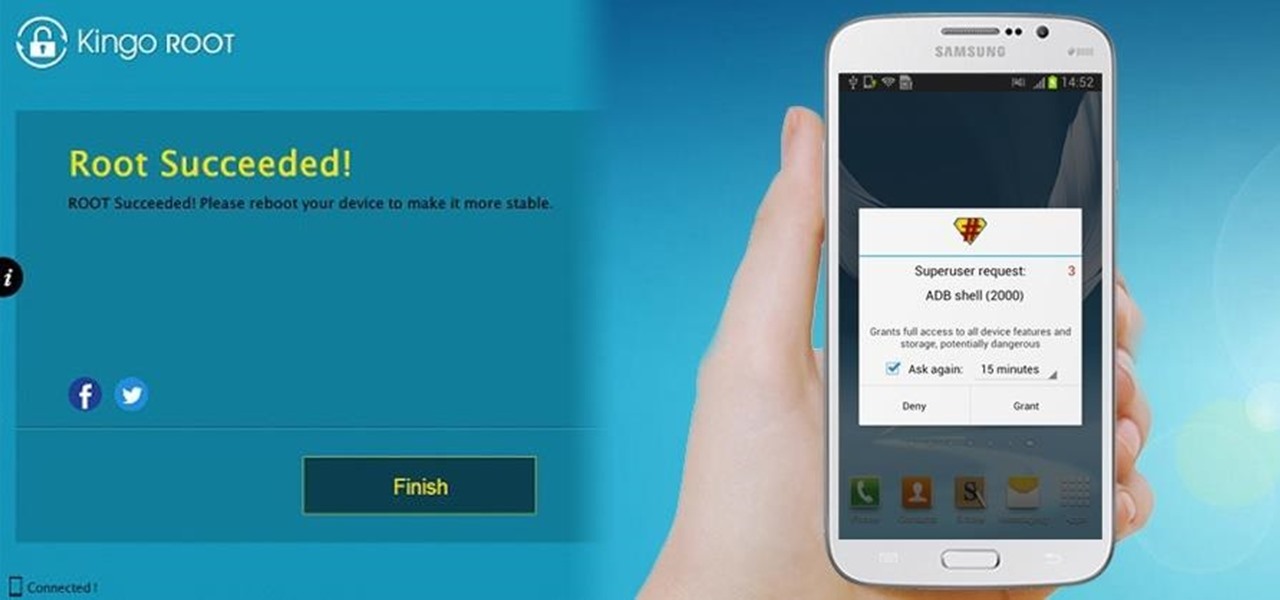
To Android users, especially advanced ones, rooting their phones or tablets is becoming a necessity. Rooting Android could be complicated, if you do it all by yourself, even with a step-by-step tutorial. However, what Kingo Android Root offers you is a true one-click experience when rooting your Android.

iTunes 12 was released alongside Yosemite this year, but it didn't pack quite the punch that the operating system did. Instead, iTunes received a minor facelift, with few new features and somehow lacking the intuitive feel of its predecessor. If you're not thrilled with iTunes 12, we've got a few tips to help you feel like you've got iTunes 11 back on your computer!

The other day I was perusing my Instagram when I came upon a curious hashtag... #OnePotPasta. Intrigued, I investigated further and discovered a whole world that was previously unbeknownst to me.

It's never too early to start planning for the best holiday of the year, right? We've already shown you how to make chillingly creepy cocktails, shrunken heads out of apples and potatoes, and a slew of DIY costumes, whether you want to go as Groot or an emoji. Now it's time to think about the most important part of any good Halloween party: the food. If you need inspiration for some spookily tasty Halloween hors d'oeuvres, just read on.

Listen, I'm not disparaging using really good knives—they can literally change your life, or at the very least, the way you work in the kitchen. However, there are many cutting and slicing tasks where you're better off using a sturdy pair of kitchen shears rather than a chef's or even a paring knife.

"Tempering chocolate" is one of those intimidating-sounding kitchen tasks that keeps novice cooks away from some really fun stuff like making candy, chocolate-dipped biscotti, and fruit.

Journals are a great source of hilarity and embarrassment, detailing everything from your elementary school crushes to those super awkward middle school dances. While rereading your old hand-scrawled entries might make you cringe, that old journaling habit could benefit you as an adult.

Having a dust- and water-resistant phone is truly useful, but it comes with a price. In order to achieve this functionality, Samsung had to literally plug up any holes in the Galaxy S5, and this included the charging port.

Have you ever fallen victim to a clever Jedi mind trick? Don't worry. It happens. There are evolutionary reasons as to why our brains sometimes give into the oldest tricks in the book. Fortunately, the more you understand the tricks of a salesman, the easier it is to avoid their gripping psychological influence. Clue #1: Too Much Specificity

Welcome back, my greenhorn hackers! In my continuing effort to demonstrate to you how to hack the ubiquitous Windows 7, we will going after that notoriously vulnerable Adobe Flash that is on nearly every client Windows system (you are not likely to find it on servers).

The Problem If you are working on a car restoration project, then you are going to faced with rust damage. This problem can’t be overlooked, as the entire project depends on repairing and eliminating rust. This would be like laying down new carpet to a house that was flooded, without cleaning the mess and making necessary repairs before laying the carpet down. The problem will still be there and the new carpet will be ruined.

Anyone that has ever watched a member of the opposite sex play a video game knows that the other gender does it wrong.

Currently, the COVID-19 pandemic is showing signs of winding down, nevertheless, Google will still hold its annual I/O developer conference as a virtual affair, with keynotes and sessions available as live streams and on-demand videos starting Tuesday, May 18 and concluding on Thursday, May 20.

HomePod and HomePod mini are excellent smart speakers if you're entrenched in the Apple ecosystem. They even offer ways to protect your sensitive information from friends and visitors who try to ask Siri to spill your secrets. But there's an extra layer of privacy you can put in place to make sure nobody gains access to any important notes, reminders, and calendar events.

TWRP is the premiere custom recovery for Android because of how many devices it supports and how simple it is to use. But installing it in the first place hasn't always been the easiest thing to do — until now. With the help of a Magisk module, you can finally use one Android device to flash TWRP on another.

File permissions can get tricky on Linux and can be a valuable avenue of attack during privilege escalation if things aren't configured correctly. SUID binaries can often be an easy path to root, but sifting through all of the defaults can be a massive waste of time. Luckily, there's a simple script that can sort things out for us.

The response to the COVID-19 pandemic means that social distancing has become the new normal. It also means that more Americans are using video conferencing to connect with colleagues working from home or friends and family in quarantine because of the new coronavirus.

Without admin privileges, installing additional software, or modifying the Windows 10 firewall, an attacker can alter a router and perform a variety of exploits. It's accomplished by forwarding requests from Kali through a backdoored Windows computer to the router gateway with simple SSH tunnels.

One of the most common web application vulnerabilities is LFI, which allows unauthorized access to sensitive files on the server. Such a common weakness is often safeguarded against, and low-hanging fruit can be defended quite easily. But there are always creative ways to get around these defenses, and we'll be looking at two methods to beat the system and successfully pull off LFI.

KeePassX, 1Password, and LastPass are effective against keyloggers, phishing, and database breaches, but passwords managers rely on the operating system's clipboard to securely move credentials from the password vault to the web browser. It's within these few seconds that an attacker can dump the clipboard contents and exfiltrate passwords.

The year in augmented reality 2019 started with the kind of doom and gloom that usually signals the end of something. Driven in large part by the story we broke in January about the fall of Meta, along with similar flameouts by ODG and Blippar, the virtual shrapnel of AR ventures that took a wrong turn has already marred the landscape of 2019.

Just like Instagram, Photoshop Express for Android and iOS has its own set of filters you can quickly apply to any photo. It's simple, fast, and more customizable than using Instagram's pre-made filters. The options in Photoshop Express allow you to edit and change your filters to be exactly to your liking. Then, you can even save those edits as your own custom filters.

Because timing is everything, the latest entry in the location-based augmented reality gaming sweepstakes, Ghostbusters World, has arrived just in time for Halloween.

Web 2.0 technology has provided a convenient way to post videos online, keep up with old friends on social media, and even bank from the comfort of your web browser. But when applications are poorly designed or incorrectly configured, certain flaws can be exploited. One such flaw, known as CSRF, allows an attacker to use a legitimate user's session to execute unauthorized requests to the server.

With the announcement of ARKit 2.0 at WWDC 2018, Apple is bringing some powerful new capabilities to mobile augmented reality apps this fall.

Continuing our series on building a dynamic user interface for the HoloLens, this guide will show how to rotate the objects that we already created and moved and scaled in previous lessons.

Waze is the go-to navigation app for millions of drivers, and it's easy to see why. Benefits such crowd-sourced traffic data, police trap locations, and road work avoidance are just the tip of the iceberg. It can almost be overwhelming, but with these simple tips, you'll master Waze and start navigating like an expert in no time.