This week, developer Niantic began rolling out a new feature called AR Mapping to Pokémon GO that has bigger implications on the realism of augmented reality in mobile gaming and beyond.

Apple just pushed out iOS 14 to everyone on Sept. 16, but you may not want to jump right into updating your iPhone. If you have Automatic Updates turned on, you may want to turn it off real quick before it tries to download and install iOS 14 before you're ready.

Alongside the launch of Android 11, Google has gifted Pixel users with several exclusive features, including App Suggestions on the home screen. Another exclusive feature involves Live View, the augmented reality walking navigation feature in Google Maps and one of the more useful implementations of AR for the average consumer.

You may be familiar with image-based or audio-based steganography, the art of hiding messages or code inside of pictures, but that's not the only way to conceal secret communications. With zero-width characters, we can use text-based steganography to stash hidden information inside of plain text, and we can even figure out who's leaking documents online.

Whether you miss the good old days of Telnet or you want to know what hacking was like when security was nothing but an afterthought, Telehack is the game for you. The text-based hacking game is a simulation of a stylized combination of ARPANET and Usenet, circa 1985 to 1990, with a full multi-user universe and player interactions, including 26,600 hosts.

If you made a resolution for 2020 to get healthier, it's essential to concentrate on your mental health just as much as you do on physical fitness. Running and exercising is great, but a sound mind is integral to a healthy and balanced life, and you can improve your emotional and physiological well-being with your smartphone.

Every summer for the last 26 years, hoards of hackers have descended on the Las Vegas Strip for DEFCON, the biggest hacker conference in the US. There's a wealth of talks every season (DEFCON 27 has at least 95 scheduled), and there have been some essential topics to learn from in past discussions. We've dug through the last ten years and found the 15 most popular talks you should watch.

It's common for IoT devices like Wi-Fi security cameras to host a website for controlling or configuring the camera that uses HTTP instead of the more secure HTTPS. This means anyone with the network password can see traffic to and from the camera, allowing a hacker to intercept security camera footage if anyone is watching the camera's HTTP viewing page.

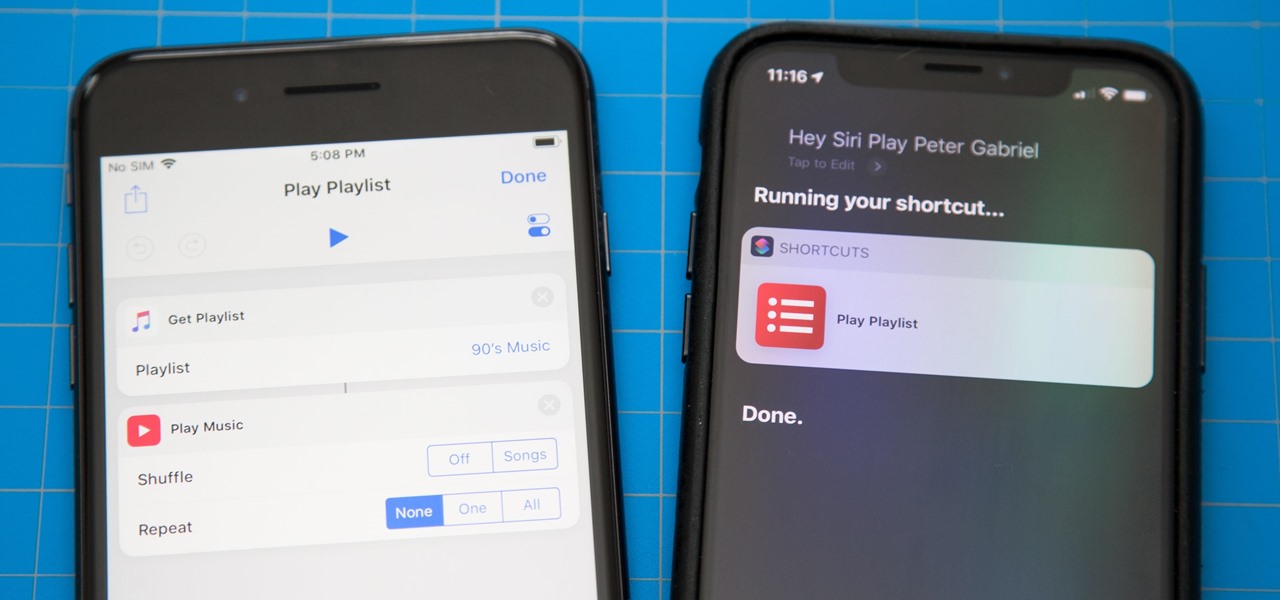
One of the most exciting additions to iOS 12 for iPhones is called Shortcuts, a tool integrated with Siri to help you get things done faster. While there are a few recommended shortcuts available to you in Siri's settings in iOS 12, the Shortcuts app brings the functionality of Workflow to Siri so you can build your own custom actions or select from the gallery of available shortcuts.

Hacking Wi-Fi is a lot easier than most people think, but the ways of doing so are clustered around a few common techniques most hackers use. With a few simple actions, the average user can go a long way toward defending against the five most common methods of Wi-Fi hacking, which include password cracking, social engineering, WPS attacks, remote access, and rogue access points.

There has been significant debate over law enforcement's right to access our digital devices in recent years. New tools from Grayshift and Cellebrite are popping up faster than ever to help government agencies, as well as traditional hackers, break into iPhones. If you're concerned, you can take steps right now to beef up your passcode and prevent outsiders from gaining access to your device.

TouchWiz might not be the Android skin of choice for hardcore aficionados, but the Galaxy's OS still has a ton of great features up its sleeve that help provide one of the most enjoyable smartphone experiences out there. Many of these are relatively hidden and overlooked features that you may not be aware of.

The public leaks of NSA tools and information have led to the release of previously secret zero-day exploits such as EternalBlue, which was used in the notorious WannaCry ransomware attack. Despite multiple patches being released, many users have failed to update their systems, so many devices are still vulnerable to these now-public attacks.

An attacker with shell access to a Linux server can manipulate, or perhaps even ruin, anything they have access to. While many more subtle attacks could provide significant value to a hacker, most attacks also leave traces. These traces, of course, can also be manipulated and avoided through methods such as shell scripting.

Black Mirror, Netflix's technology-horror anthology, never fails to provide thought-provoking entertainment centered around emerging and futuristic technologies, and the third season's second episode, "Playtest," delves deep into the worlds of mixed, augmented, and virtual reality. While designed to leave you haunted by the end, offering a more "evil" narrative than we'll likely see in our actual future, the episode explores possibilities that aren't as far off as one might think.

Despite the security concerns that have plagued Facebook for years, most people are sticking around and new members keep on joining. This has led Facebook to break records numbers with over 1.94 billion monthly active users, as of March 2017 — and around 1.28 billion daily active users.

As I said in this earlier post, there's no easy way to explain or define the Steampunk aesthetic. There are a large number of Steampunk tropes or "cues", as I call them, that bring to mind the feeling of Steampunk. These cues combine to push past the "not-Steampunk" threshold into firmly "Steampunk" territory.

Say whatever you want, but Steampunk is primarily a maker culture. Consider that Steampunk has existed since the 1960s and yet more or less languished in obscurity until approximately 2005, which is when it made the leap to costuming. That costuming was what provided the leap to the tangible, despite the fact that Steampunk art had also existed for years.

Brands are increasingly adopting augmented reality to promote their products and services, and they have multiple paths for bringing AR experience to their audiences.

Sure, Microsoft has mostly marketed its HoloLens headsets towards enterprises and developers, but we learned this week that, like every other tech giant, the company is working on a consumer-grade AR wearable. Speaking of consumer smartglasses, Apple made another strategic investment this week that has implications for Apple's AR future.

Apple has a sterling reputation when it comes to managing its supply chain; it's where CEO Tim Cook proved his mettle to succeed Steve Jobs. Now, the company has made a strategic investment with a supplier that will be crucial to its future plans for AR wearables.

A lot of digital ink has been spilled heaping scorn on Magic Leap. Much of that media schadenfreude was due to what some believed were unmet promises versus some of the early hype around the product. Others just seemed to be rubbed the wrong way by the startup's Apple-esque secrecy and penchant for attempting to coin new terms and frameworks for things that were, mostly, already in play.

There are a lot of cool shortcuts you could run on your iPhone, but in iOS 13 and iOS 14, you'll likely see a notification any time you try to run an automation. Shortcuts should feel seamless when their actions are performed, and getting a banner alert each time one initializes takes away the seamlessness of it all. But there is a way to block them.

When you think about it, isn't life just one big open-world RPG just begging to be conquered? We all have a set number of specific tasks or chores we must complete every single day like clockwork. Sometimes, these items on our to-do list can become tedious and cause us to lose motivation. What if you could take those tasks and turn them into something awesome instead? Now you can.

The $35 Raspberry Pi is an amazingly useful single-board computer (SBC) with a good balance of price, performance, and connectivity options. But for some projects, it just isn't enough. Whether you need more computing power, a smaller size, or better machine-learning capabilities, there are other options available.

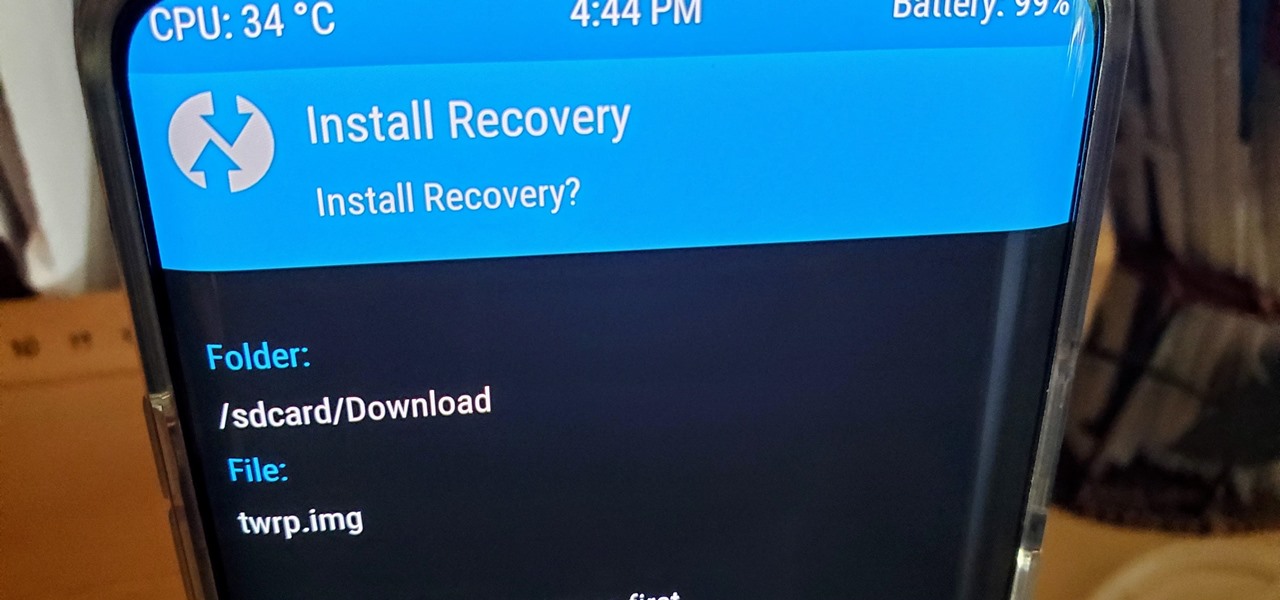
When it comes to modding your Android device, you'll want to be familiar with the TWRP name and what it stands for. It's a tool that you'll be using to make NANDroid backups or to install just about any mod file you can think of — the number of uses is quite awesome. You'll mostly be after Magisk for root access and potentially a custom kernel as well.

While keeping your iPhone out of the bedroom might help to avoid unnecessary distractions before bedtime, it could be better served right by your side to help diagnose sleeping issues you may be experiencing each night.

Give an 18-month-old a shoe, check back 10 minutes later, and it's a very big maybe he will have it on his foot. But give him your smartphone, and in a mere five minutes, he can take 100 pictures of the carpet, send weird messages, and delete essential apps. Imagine what your child could do if they were able to harness this technical aptitude and put it to good use — and they can, with learning apps.

In just a few months, Binance has experienced explosive growth, overtaking its rivals to rank among the top three cryptocurrency exchanges in the world by trading volume. Without a doubt, Binance is now among the best sites for trading alt-coins like Ripple (XRP), Stellar (XLM), and NEM (XEM) to name a few.

Coinbase is the primary go-to for many users when it comes to investing in Bitcoin (BTC), Ethereum (ETH), Litecoin (LTC), Ripple (XRP), and more, due to its user-friendly interface. But before you join them, know that the ease of use comes with a price. Coinbase charges fees for each transaction, and your bank might even add charges on top of that. Plus, there is some fine print to be aware of.

On July 20, 1969, humans set foot on the moon for the first time. But some say our microbes beat us there. With the Space Age came new questions about microscopic invaders from outer space and concern about where we are leaving our microbial footprints. The questions are even more relevant today.

Step 1: What Exploit Development Is and Why Should I Be Interested on About This Topic

If you buy an Android phone from any of the big US carriers, it will come with several extra apps in addition to any apps the manufacturer preinstalled. It's all in the name of profit, of course. Some of these apps are from companies that paid the carriers to distribute their software, and some are from the carriers themselves, usually aimed at upselling you or perhaps collecting a little data.

Among the various components of the emerging augmented reality space, the most lucrative is the advertising market. The prospect of turning every object, every location, ever signpost in the real world into a discount code or virtual transaction interface is why AR will ultimately be more profitable than VR.

If you just got an iPhone 12, 12 Pro, 12 Pro Max, or 12 mini, and you've never owned an iPhone before, some of the most basic tasks can be baffling. Shutting it down, force-restarting it, quitting apps, and even viewing the percentage of battery remaining sound simple but aren't very intuitive for new iPhone owners. Another big question mark is screenshots, and there are several ways to take them.

The art of fuzzing is a vital skill for any penetration tester or hacker to possess. The faster you fuzz, and the more efficiently you are at doing it, the closer you come to achieving your goal, whether that means finding a valid bug or discovering an initial attack vector. A tool called ffuf comes in handy to help speed things along and fuzz for parameters, directors, and more.

While Apple and Samsung have started integrating depth sensors into the iPad Pro and Galaxy smartphones, more advanced AR experiences are arriving for standard smartphone cameras on Android devices.

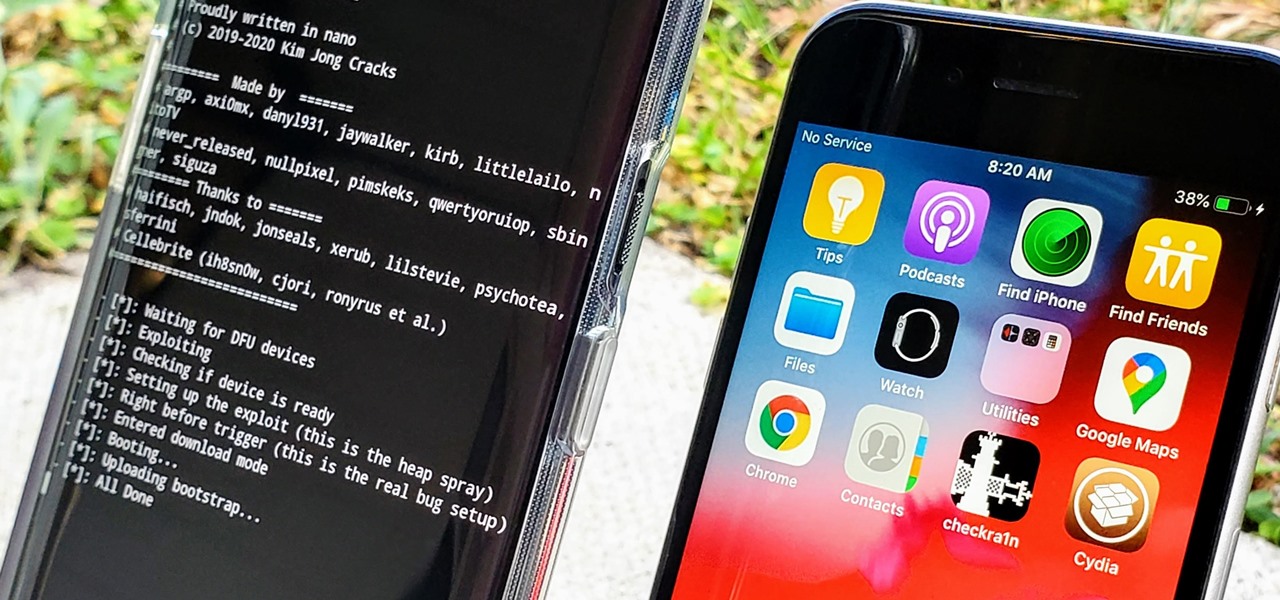
In the iPhone modding scene, the Checkm8 bootrom exploit, by developer axi0mX, led to a powerful jailbreaking tool known as Checkra1n. With it, you can jailbreak a variety of iPhone models without worrying about it getting patched later on. But in the past, it required you to have a macOS computer — but not anymore.

In the first guide, we laid the groundwork for our ultimate goal of uploading and running the unix-privesc-check script on our target. We identified an input field vulnerable to SQL injection and utilized Sqlmap to set up a file stager on the server. Now, we're ready to upload files and execute the script, so we can identify any misconfigurations that could lead to privilege escalation.

Silence spreads over these mountains like nothing I've ever felt. If I didn't have Moby blasting in my earphones, there'd probably be no other sounds around. Well, except for someone, Phil probably, murmuring in a nearby tent just low enough to make his words indiscernible.