
In this series of videos, our expert explains all things motors. If you are a beginner looking to get involved in this sport, watch these informative videos. You will learn how to keep your control while riding the bikes through mud, sand and jumps. Our expert explains the basics, such as changing a tire on the track, suspension set ups and setting yourself up for a jump. If you are already an experienced rider, get tips on jumps and stunts like wheelies from our expert motors rider. Learn ho...

Though jewelry making can be meticulous and dependent on dexterity, using the right wire makes the whole process easier and faster. Wire necklaces and bracelets are simple when using the soft flexible wire, or soft flex. This demonstration video will help walk you through the process of this threading with soft flex.
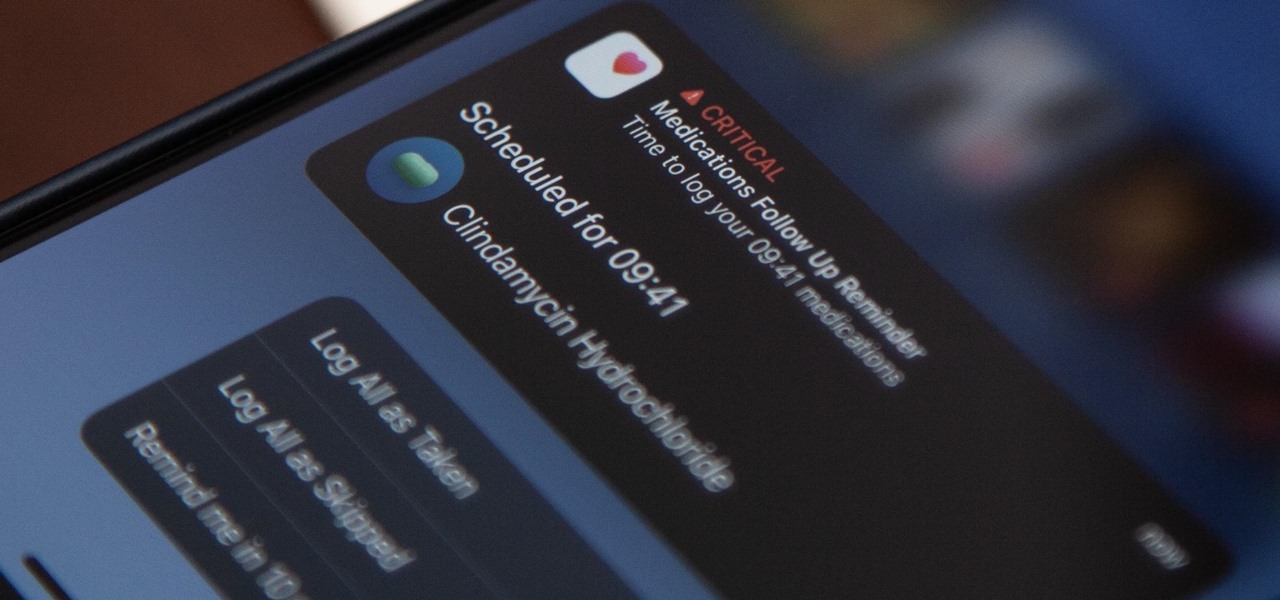
Since iOS 16, you've been able to add and track medication in the Health app, learn about potential drug interactions, and receive dose reminders. With iOS 17, Apple improves that last aspect with even more notification options to ensure you take your medicine on time and never miss a dose.

Android has a new security feature that every Android smartphone user needs to start using — even you. It won't change how you use your phone, but it will make life harder for nearby thieves.

Apple's iOS 14.5 is the biggest update since iOS 14.0 came out, with over 50 confirmed features and more being discovered every day. There are new emoji, support for AirTags, more privacy controls, and exciting upgrades to Siri, Maps, Reminders, Podcasts, Music, and even Shortcuts. So it wouldn't surprise us if you want to get this on your iPhone ASAP.

This week, developer Niantic began rolling out a new feature called AR Mapping to Pokémon GO that has bigger implications on the realism of augmented reality in mobile gaming and beyond.

Whether you miss the good old days of Telnet or you want to know what hacking was like when security was nothing but an afterthought, Telehack is the game for you. The text-based hacking game is a simulation of a stylized combination of ARPANET and Usenet, circa 1985 to 1990, with a full multi-user universe and player interactions, including 26,600 hosts.

There once was a time in the Android rooting scene where we couldn't rely on using a custom recovery for all of our modding needs. Manual file flashing was very popular in the early days of Android before custom recoveries started taking over. With the rise of TWRP, it seemed like there was almost no need for manual file flashers; however, they appear to be making a welcomed return in a big way.

Influencers of augmented reality demonstrate expertise in their fields and outline a strong vision for the future that they evangelize to others. They help define the direction of the industry and identify others who foster and create innovation in the field.

Have you noticed the many utility ARKit apps on the App Store that allow you to measure the sizes of horizontal planes in the world? Guess what? After this tutorial, you'll be able to do this yourself!

Smartphones are still "phones," which means communicating with others is usually a primary use. Ranging from a simple "hi" to a more personal conversation and even sharing passwords, our messages should remain private so that only the intended recipient sees their content. While many apps tout end-to-end encryption, not all apps prioritize security and privacy.

One feature in iOS you're likely underutilizing is 3D Touch, a highly useful, unique tool for iPhones ever since it first appeared on the iPhone 6S. Apple's pressure-sensitive interactivity gives iOS an extra layer of functionality, which can be clearly seen across the entirety of your device. From the lock screen to the home screen to the apps in between, there are plenty of ways to use 3D Touch.

There has been significant debate over law enforcement's right to access our digital devices in recent years. New tools from Grayshift and Cellebrite are popping up faster than ever to help government agencies, as well as traditional hackers, break into iPhones. If you're concerned, you can take steps right now to beef up your passcode and prevent outsiders from gaining access to your device.

The public leaks of NSA tools and information have led to the release of previously secret zero-day exploits such as EternalBlue, which was used in the notorious WannaCry ransomware attack. Despite multiple patches being released, many users have failed to update their systems, so many devices are still vulnerable to these now-public attacks.

As smartphone users, we live in dangerous times. The value of phones continues to rise, making them prime targets for thieves. In 2015, the FCC estimated that one million phones are stolen each year, and with several devices starting to hit the $1,000 mark now, these numbers are sure to rise. But what do you do if you fall victim to phone theft?

Because of the way Google Play works, Android has a "bad app" problem. Google allows any developer to upload an app to the Play Store, regardless of if it works, how it looks, or whether or not it can harm users. Malware scanning happens primarily after apps are uploaded, and though Google has recently taken steps to safeguard users with its Play Protect program, you don't have to depend on them.

If preorder delays are any indication, the iPhone X certainly has some buzz. But does the X have the quality to support that buzz in the long run? After all, a $1,000 (or more) iPhone feels more like an investment than a smartphone purchase. The question on any prospective buyer's mind should be, "Is this thing worth it?"

Armis Labs has revealed eight vulnerabilities, called "BlueBorne", which put 5.3 billion Android, iOS, Windows, and Linux devices that use Bluetooth at risk. With it, hackers can control devices, access data, and spread malware to other vulnerable devices through networks. In this post, we will learn about the vulnerabilities, then look at how to find devices that have them.

After months of leaks and rumors, Google has finally unveiled the Pixel 2 and Pixel 2 XL. If there were such a thing, the Pixel would be the one "true" Android flagship — so even if you don't plan on buying a Pixel 2, you'll want you learn more about this milestone device.

Whisking liquids seems somehow quaint, especially since there are good, cheap devices out there like immersion blenders and hand mixers that can whip cream, turn egg whites into meringue, and mix batters for you.

As a species, our cells are designed to use sugar for energy. Is it any wonder that as humans evolved, we grew to love the taste of sugar?

If you've been to a convention of any sort before, you know that there are good and bad panels, and that their inherent goodness or badness often has little to do with the actual content being discussed. That's because giving a panel is a skill that not everyone has. However, it is a skill that everyone could have! In this article, I'll tell you how to give a good panel on practically any subject. Image by Shannon Cottrell

This video series takes you through the steps involved in installing a kitchen sink. You'll see how to mount the sink, and connect and run all the necessary pipes and plumbing.

Oil painting is an artistic process that involves using pigments bound with a medium of drying oil. Learn to paint the portrait of a young girl from a professional artist in this free painting video.

It's always fun to get an unexpected glimpse of the future, especially when that peek is so close you can actually feel the excitement of the new emerging dynamic.

After facing delays due to the COVID-19 pandemic, the Olympic Games are underway in Tokyo, but a surge in cases worldwide has taken the spectator out of these spectator sports.

On Friday, the Tokyo Olympics finally kicked off after massive delays and complications due to the pandemic.

With fears over the COVID-19 pandemic subsiding, live concerts are returning. And Doritos wants to send music fans to a few of them via an augmented reality promotion.

The debut of the augmented reality version of Snap's Spectacles came with several examples of how the wearable can allow creators to transform the world around them.

Currently, the COVID-19 pandemic is showing signs of winding down, nevertheless, Google will still hold its annual I/O developer conference as a virtual affair, with keynotes and sessions available as live streams and on-demand videos starting Tuesday, May 18 and concluding on Thursday, May 20.

Apple has changed how home screen shortcuts work on iOS, which makes one of the most enjoyable customization features even better than before.

Written language began with one of the most pedestrian tasks imaginable: accounting. The basis of poetry, epic mythologies, and novels initially involved marking down trades between livestock owners and grain suppliers. We rightfully think that literature is essential to the human spirit. But when contemplating how societies operate, spreadsheets are king.

The amount of information we see on a daily basis is overwhelming. Then there's all the data we never even see. If your career depends on making sense of all of this information, you need to understand the programs that do the heavy lifting.

For all the benefits 5G brings to cellular data, it isn't without weaknesses, the biggest being privacy. Yes, the latest standard comes with breakneck downloads speeds up to 4.3 Gbps, but at what cost? Like with all things on the internet, 5G devices open opportunities for both good and bad actors.

Even under normal circumstances, it's almost impossible to speak to a representative for a government agency or company in just one try. Many systems will put you on hold for long periods or ask to call you back when someone is available, but there are still some out there that just give you the busy signal over and over again. In those cases, there's a jailbreak tweak that can help.

TWRP is the premiere custom recovery for Android because of how many devices it supports and how simple it is to use. But installing it in the first place hasn't always been the easiest thing to do — until now. With the help of a Magisk module, you can finally use one Android device to flash TWRP on another.

File permissions can get tricky on Linux and can be a valuable avenue of attack during privilege escalation if things aren't configured correctly. SUID binaries can often be an easy path to root, but sifting through all of the defaults can be a massive waste of time. Luckily, there's a simple script that can sort things out for us.

The response to the COVID-19 pandemic means that social distancing has become the new normal. It also means that more Americans are using video conferencing to connect with colleagues working from home or friends and family in quarantine because of the new coronavirus.

This week, the beginning of an epic legal battle was set to begin between augmented reality players Magic Leap and Nreal, the small China-based startup accused by the former of stealing trade secrets.

One of the most common web application vulnerabilities is LFI, which allows unauthorized access to sensitive files on the server. Such a common weakness is often safeguarded against, and low-hanging fruit can be defended quite easily. But there are always creative ways to get around these defenses, and we'll be looking at two methods to beat the system and successfully pull off LFI.







































