
News: What You Need to Know About ZTE's Ongoing Battle with the US Government
| Update: ZTE's issues with the US government have finally been resolved. Check out the details below.


| Update: ZTE's issues with the US government have finally been resolved. Check out the details below.

While everyone was marveling at the latest drama over at Magic Leap involving employees last week, a major rumor listed in one of the reports, related to the company's flagship device, was mostly overlooked.

No matter your reasons, you might need a second phone number that's a little more disposable than your primary number — a "burner" number, so to speak. If you create this burner number using Google Voice, you'll get new functionality like call forwarding and voicemail transcripts, and best of all, it's completely free.

We can add one more health effect of our gut bacteria to the growing list. Researchers from the UK have just reported that the gut microbiota plays a role, both directly and indirectly, on the toxicity and efficacy of chemotherapy. Their findings are published online in the journal Nature Reviews Gastroenterology & Hepatology.

For some, drinking raw milk is a way to get back to nature, improve family nutrition, and hedge against asthma and allergies. However, according to public health authorities, drinking raw or unpasteurized milk is a big mistake—even fatal. So what's the story?

Jostled in the airport, someone is coughing in line. The air looks empty but it is loaded with microbes that make their way into your body. You get sick. You give it to your family, and that's pretty much it. But what if you were so contagious that you spread it to your entire community and beyond?

It feels like someone reached into your chest and squeezed. Your head throbs in unison with your heartbeat. Clammy dread coats your body in sweat. Whether you call 911 or someone does it for you, the ER is your next stop.

When Kaci Hickox, a Doctors Without Borders nurse, returned to New Jersey from working with Ebola patients in West Africa in 2014, she was surprised by her reception. Instead of a quiet return to her home in Maine after four weeks on the front line of Ebola treatment, she was quarantined by the State of New Jersey in Newark. She later filed a lawsuit in U.S. District Court for violation of her civil rights, false imprisonment, and invasion of privacy.

We're nearly done getting our Mac set up for hacking. If you haven't checked out previous tutorials, I'd recommend you do so first before diving right into this one.

Greetings my fellow aspiring hackers,

Throwing a party means making sure everyone has fun, but that pursuit can quickly get out-of-hand. Before you know it, you're once laid back get-together has received so many RSVPs that it becomes obvious you're throwing the party of the century. With an over-abundance of beer and an inflated guest list, your newly-formed epic reputation must live up to the hype.

White or light-colored dinnerware is a classic: it looks crisp, clean, and elegant. The only problem is that after you've used it for a few years, the surfaces bear a lot of grey scuff marks from forks, spoons, and knives being dragged across the surface.

TouchDevelop is a browser-based programming tool that allows anyone to build your own Windows 8 apps directly from any touchscreen device, including iPad, iPhone, Windows Phone, Android, PC and Macs. Once the script is created and the app proves to work, it can be placed in the Windows Store for free or purchase.

Despite the unfortunate social media-driven association of Corona beer with the virus behind a global pandemic, beverage maker Constellation Brands has pushed its marketing forward like a lime through the mouth of a beer bottle.

Does TikTok scare you? Trust me, I get it. It's a strange, unfamiliar place to those of us not accustomed to its ways, populated by teenagers and college students with their own subcultures, memes, and humor. But here's the thing: TikTok has something for everyone, you included.

Giving up your Wi-Fi password can be giving up more control than you think. Because of the way Chromecast and other IoT devices communicate, anyone on the same Wi-Fi network as your device can often make it do whatever they want. With a script called "Cast All the Things," we can hijack a Chromecast to play nearly any kind of media with a single command in terminal.

Leaked databases get passed around the internet and no one seems to notice. We've become desensitized to the data breaches that occur on a daily basis because it happens so frequently. Join me as I illustrate why reusing passwords across multiple websites is a truly awful practice — and compromise hundreds of social media accounts in the process.

PUBG is currently taking the mobile world by storm, and it's easy to see why. The game has breathed much-needed life to the multiplayer shooting genre, primarily by adding an element of sheer terror as you scavenge for weapons in a hostile environment. With new players continually joining in on the fun, many players are looking for ways to gain an edge.

The LG V30 has solid battery life. With its QHD P-OLED screen and 4 GB RAM, it's able to maintain all-day performance with average use. Heavier users might find that its 3,300 mAh battery isn't quite enough for a full day of work, though, but with a few software tweaks, you can squeeze out even more battery life.

Nvidia's decades-long development of graphics processor units (GPU) for PCs has given it a major leg up in the driverless space.

Greetings aspiring hackers. I have observed an increasing number of questions, both here on Null-Byte and on other forums, regarding the decision of which USB wireless network adapter to pick from when performing Wi-Fi hacks. So in today's guide I will be tackling this dilemma. First I will explain the ideal requirements, then I will cover chipsets, and lastly I will talk about examples of wireless cards and my personal recommendations. Without further ado, let's cut to the chase.

The paper towel is a wondrous invention. It allows cooks to wipe up really gross stuff without having to constantly do laundry and drain fried foods so they're crunchy and crispy instead of oily and heavy. But did you know that your humble paper towel has several other uses besides the obvious ones? Read on to find out these essential hacks.

It has been a long while since I last came here to write an article. Graduate school keeps you busy. After I looked over what I had written previously, I decided that I should introduce another fun topic from cryptography. In this case, steganography.

Whether you miss the good old days of Telnet or you want to know what hacking was like when security was nothing but an afterthought, Telehack is the game for you. The text-based hacking game is a simulation of a stylized combination of ARPANET and Usenet, circa 1985 to 1990, with a full multi-user universe and player interactions, including 26,600 hosts.

If you made a resolution for 2020 to get healthier, it's essential to concentrate on your mental health just as much as you do on physical fitness. Running and exercising is great, but a sound mind is integral to a healthy and balanced life, and you can improve your emotional and physiological well-being with your smartphone.

Fireworks are the best part about the Fourth of July and other celebrations, but they can easily cause accidental injuries. It's both safer and more fun to set them off remotely, so we'll hack some standard fireworks with nichrome wire, a relay, and an Arduino to ignite remotely over Wi-Fi using any smartphone or computer.

People say that money makes the world go 'round. And it's no different in the world of augmented reality.

Samsung has finally rolled out the Android Oreo update for the Galaxy S8 and S8+. If you're just now getting the update, you'll be happy to know that your Galaxy just got upgraded with plenty of cool new features. Like previous updates, Samsung has improved upon its software by including a new look and new functionality.

Equifax reported on Sept. 7 that it discovered a breach on July 29 which affects roughly half of Americans, many of whom don't realize they have dealings with the company. Hackers got away with social security numbers, addresses, and driver's license numbers, foreshadowing a "nuclear explosion of identity theft." Let's explore what really happened and what you and those around you can do to protect yourselves.

Now that smartphones have ensured that we're connected to the internet 24/7, online privacy has become more important than ever. With data-mining apps hoping to sell your information for targeted ads, and government agencies only one subpoena away from knowing every detail of your private life, encryption has become our last line of defense.
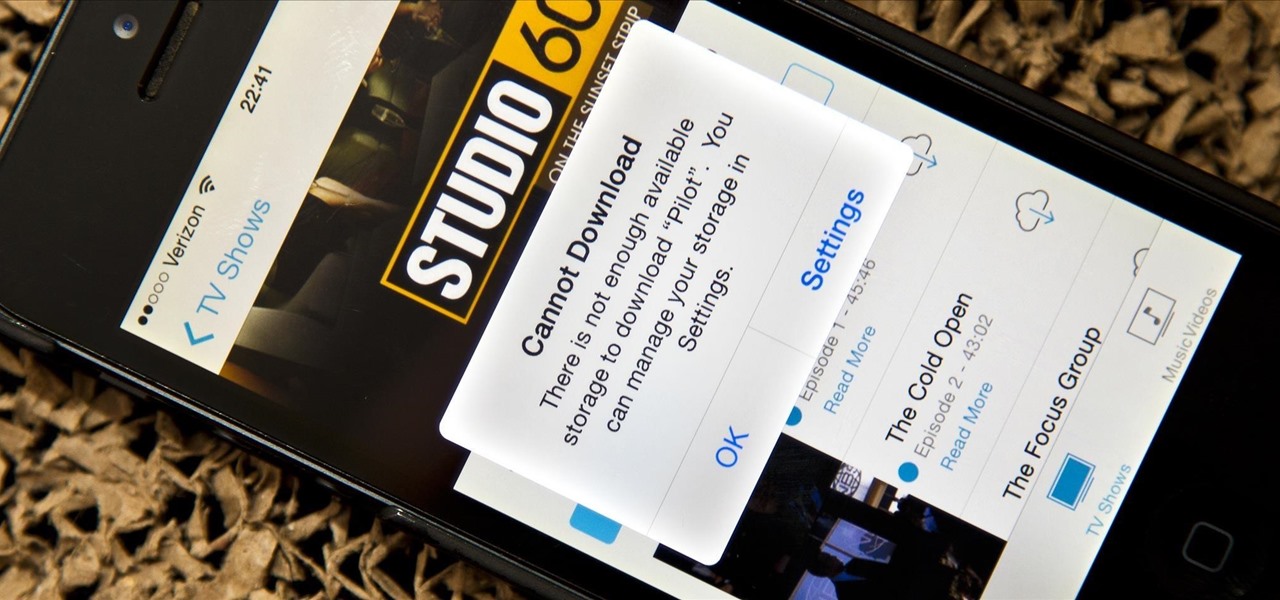
Running out of storage space on your iPhone is annoying, but trying to free some up is downright aggravating. Until they figure out a way to throw a terabyte of flash memory in there, you're going to have to do some spring cleaning every now and then, especially if you're trying to update to iOS 8.

Sure, Microsoft has mostly marketed its HoloLens headsets towards enterprises and developers, but we learned this week that, like every other tech giant, the company is working on a consumer-grade AR wearable. Speaking of consumer smartglasses, Apple made another strategic investment this week that has implications for Apple's AR future.

You don't have to be a frequent flyer to know how indispensable navigation apps have become. Many of us rely on these apps for traveling from state to state and getting around in foreign cities, but even more of us count on these apps to beat rush hour traffic and find the quickest routes to school or work. So naturally, we all have our favorite mapping apps, but which one is truly the best?

When I review apps, I'll oftentimes end up downloading at least one or two "bad" apps that either lied about their functionality or were riddled with ads. These apps, while not as harmful as malware, can still be a major headache. This got me thinking about the other bad apps on the Play Store and how to avoid them.

The gig economy is thriving, and if you aren't already making money with your phone, you could be missing out on easy residual income. Some people just want extra cash, and some even manage to completely ditch the 9–5, enabling them to work at their own pace and set their own hours.

Hello, budding augmented reality developers! My name is Ambuj, and I'll be introducing all of you Next Reality readers to the world ARKit, as I'm developing an ARKit 101 series on using ARKit to create augmented reality apps for iPad and iPhone. My background is in software engineering, and I've been working on iOS apps for the past three years.

Smartphones are still "phones," which means communicating with others is usually a primary use. Ranging from a simple "hi" to a more personal conversation and even sharing passwords, our messages should remain private so that only the intended recipient sees their content. While many apps tout end-to-end encryption, not all apps prioritize security and privacy.

On July 20, 1969, humans set foot on the moon for the first time. But some say our microbes beat us there. With the Space Age came new questions about microscopic invaders from outer space and concern about where we are leaving our microbial footprints. The questions are even more relevant today.

Autism affects 1 in 68 children in the US, and that means it affects at least 1 in every 68 families. More boys than girls are diagnosed as being on the autism spectrum, and it's estimated that almost 60,000 12-year-olds in the US have autism. That is a 37-fold increase from the 1 in 2,500 children diagnosed just 30 years ago.

Apple does not provide a native way to lock apps on your iPhone behind Face ID, Touch ID, or your passcode. For a long time, we've wanted that option for improved privacy and security, but Apple does allow developers to use its authentication protocols. Apps like Messenger, Outlook, and WhatsApp give the option to lock them down, but for the apps that don't, you can force it with a little time and effort.