Over the past week, we are seeing more companies capitalizing on services leveraging augmented reality. One company secured funding to expand their service, while two other companies grow its own services through acquisition.

Whether you're looking to add a substantial coding foundation to your hacking skill set or want to get a job in programming and development, knowing one or two programming languages just isn't going to cut it.

Some investors play the short game, placing their bets on industries that show the quickest return on their investment, and, in the augmented reality space, that means the enterprise sector.

As it prepares to ship its first product by the end of the summer, Magic Leap has managed to impress yet another high-profile investor in telecommunications giant AT&T.

Enterprise augmented reality software provider Upskill has raised $17.2 million in its latest round of funding, led by new investors Cisco and Accenture.

Bluetooth Low Energy (BLE) is the de facto wireless protocol choice by many wearables developers, and much of the emerging internet of things (IoT) market. Thanks to it's near ubiquity in modern smartphones, tablets, and computers, BLE represents a large and frequently insecure attack surface. This surface can now be mapped with the use of Blue Hydra.

The common thread between this week's Brief Reality stories is that augmented reality is beginning to prove its worth as a technology that improves workflows and processes. From customer service to healthcare to manufacturing, augmented reality is helping companies improve productivity.

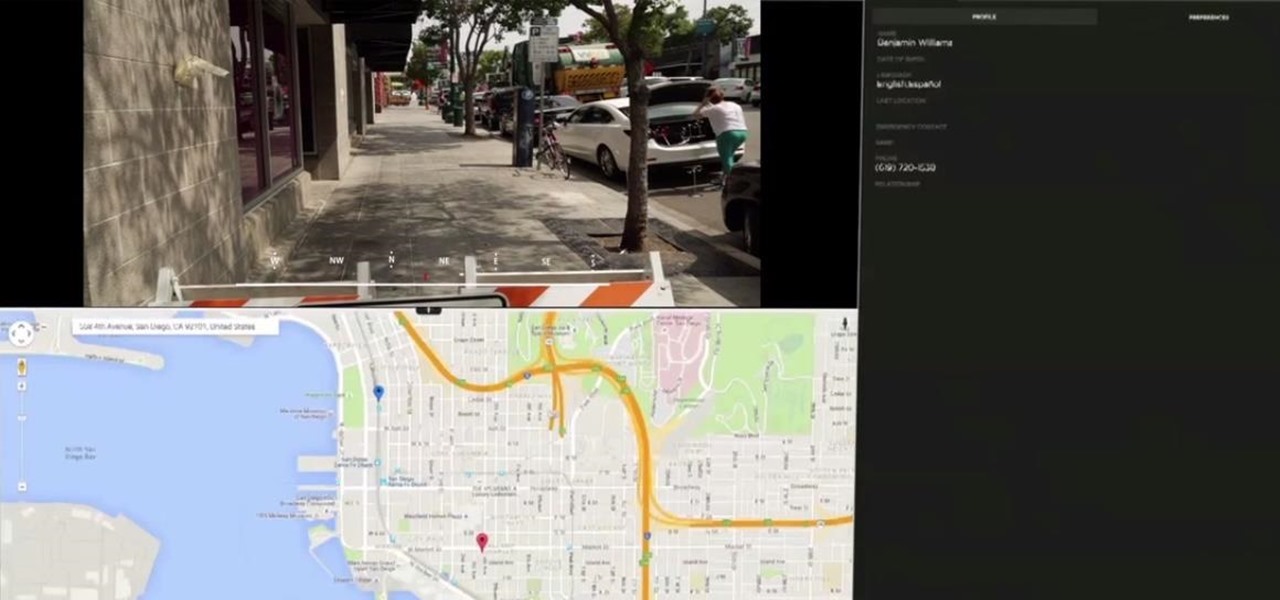
Augmented and mixed reality developer Arvizio is working on a suite of software solutions for enterprises that will extend HoloLens capabilities as a full-fledged collaboration and conferencing tool. The company will demonstrate its Mixed Reality Studio suite to attendees at the Augmented World Expo, which begins later this month in Santa Clara, California.

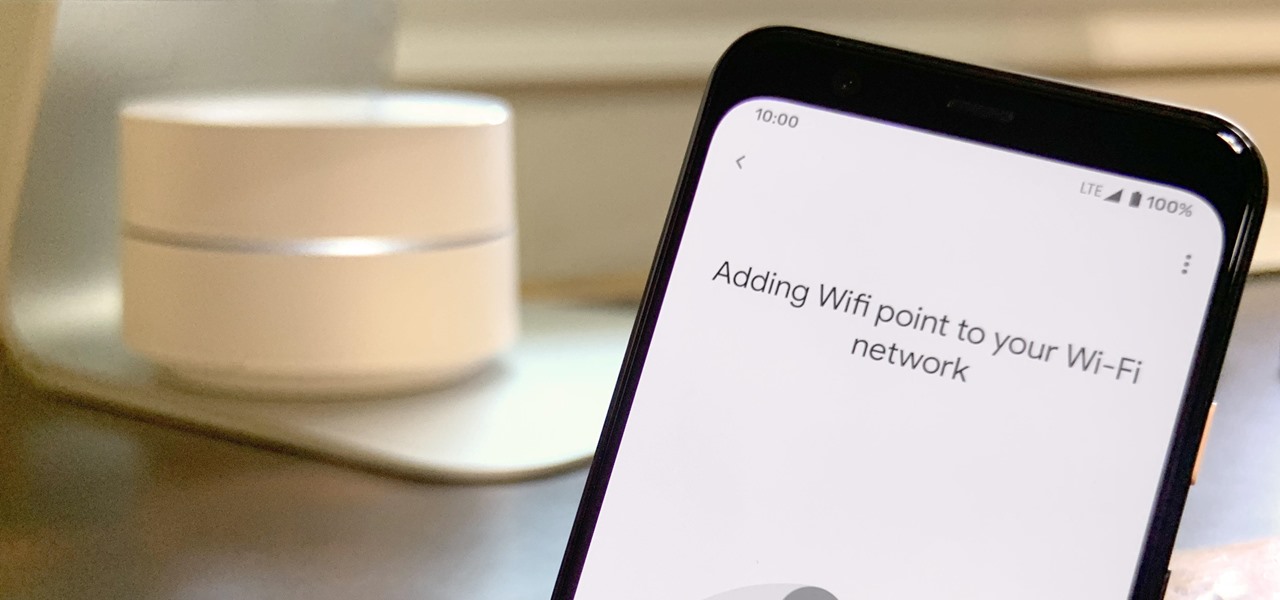
Google is known for merging older products into a new one's ecosystem for ease of use. The transition can take time, and that's the case with the old Google Wifi system now that Nest Wifi is out. Google is working on phasing out the dedicated Google Wifi app in favor of using the Google Home app for all your IoT needs.

After finding and monitoring nearby wireless access points and devices connected to them, hackers can use this information to bypass some types of security, like the kind used for Wi-Fi hotspots in coffee shops, hotels, and in flights high above the ground. By swapping their MAC address for that of someone already connected, a hacker can bypass the MAC filter and connect freely.

Using the CES tech conference in Las Vegas as the launch pad, Dell has announced that it's partnering with Meta Company to offer its augmented reality headsets to business customers.

The Easter Bunny is about to get his first experience with mixed reality. Virtual Reality Los Angeles (VRLA) will host its third annual expo in April, and this year's attendees will get to experience a fun Easter egg hunt sponsored by AfterNow and VRLA, in partnership with mixed reality king, the Microsoft HoloLens.

A relay is an electrical component that works like a light switch, where it's turned on or off with an electrical signal. By connecting a relay to a Wi-Fi connected microcontroller like an ESP8266, you can build a connected switch that can be controlled from the web browser of any device connected to the same Wi-Fi network — all for just a couple of dollars.

Ever wish you could see in the dark? Well, you can't but this how-to will show you a way to build a device to help you out. You will need light polarizors, a flashlight, and a digital camera. Make an infrared night vision device, just follow along with the steps in this video tutorial. Now you can see at night!

It's no secret that devices leak data, but sometimes they do so in ways you may not expect. Your phone, laptop, printer, and IOT devices leak Wi-Fi information that can (and is) used to track you.

MouseJack vulnerabilities were disclosed over three years ago. Some wireless keyboard manufacturers have since issued firmware updates, but millions (if not billions) of keyboards remain unpatched worldwide, either because they can't be updated or because the manufacturer never bothered to issue one.

Smartphones and laptops are constantly sending Wi-Fi radio signals, and many of these signals can be used to track us. In this guide, we'll program a cheap IoT device in Arduino to create hundreds of fake networks with common names; This will cause nearby devices to reveal their real trackable MAC address, and it can even let an attacker take over the phone's data connection with no warning.

So you've got an AppleTV, but you can't watch half the stuff you want because it won't play it. Well, do you have a jailbroken iOS 4.2 device? Sweet! Just follow along with this video, and pretty soon you'll be watching any sort of video you want in no time at all.

Some of us woke up at the KRACK of dawn to begin reading about the latest serious vulnerability that impacts the vast majority of users on Wi-Fi. If you weren't one of those early readers, I'm talking about the Key Reinstallation Attack, which affects nearly all Wi-Fi devices.

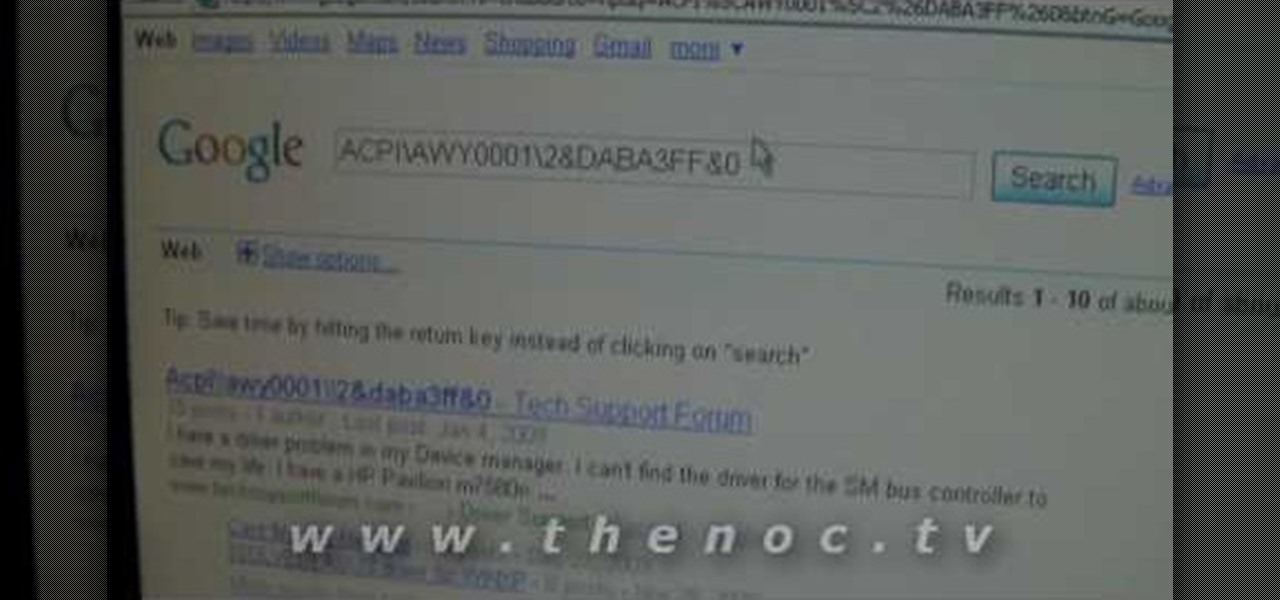
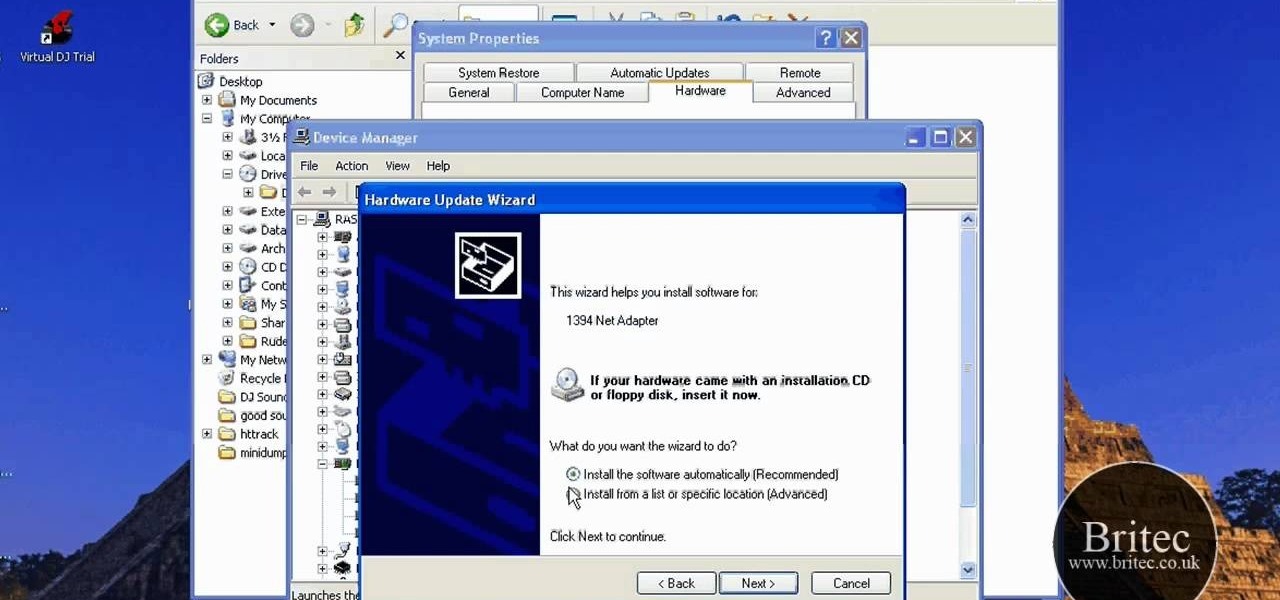
This video narrates and explains how to figure out how to install an unknown device using the device manager. The first step is to access the device manager through the control panel/system. Once in device manager you must select the show devices options. Once the device menu is visible you then find the unknown device section and copy the name of the device driver. The next step is to open Google search engine and paste the unknown device ID name. After the search is complete you will see ma...

Whether you're the proud owner of a brand new Apple iPad or are merely considering picking one up, you're sure to appreciate this video tutorial, which presents a complete overview of how to use the mobile device's user interface. For more information, including detailed, step-by-step instructions, watch this iPad user's guide.

Armis Labs has revealed eight vulnerabilities, called "BlueBorne", which put 5.3 billion Android, iOS, Windows, and Linux devices that use Bluetooth at risk. With it, hackers can control devices, access data, and spread malware to other vulnerable devices through networks. In this post, we will learn about the vulnerabilities, then look at how to find devices that have them.

The Droid Bionic was rooted the same day it came out with the one click method used to root the Droid 3. This tutorial will walk you through the process of rooting Motorola's Android device so that you can unlock the full potential of Verizon Wireless's flagship device.

If you haven't bought a new iPhone or iPod Touch since the 3G and 2G models of those respective devices, iOS 4 has probably been a major problem for you. It slows down those devices mightily, but there is a solution. This video will show you how to adjust some basic settings in your phone or MP3 player to make it run the new operating system faster and allow you to keep enjoying you device as you have for years.

In this how-to video, you will learn how to perform basic circuit bending. You will need a screw driver, alligator clips, solder, a soldering iron, wires, a wire stripper, a button or switch, and a drill. Open up the device you want to circuit bend. Once the side of the board with the solder points is exposed, take your alligator clips and find two solder points that make an interesting noise. Be careful of areas where the battery is connected, as you might shock your self or destroy the devi...

Spider-Man hits the iPhone, iPod Touch & iPad! In Ultimate Spider-Man: Total Mayhem, you take control of Spidey, slinging webs and fighting crime. No longer do you have to stick to comic books, you can enjoy Spider-Man right from your Apple mobile device.

USB devices are ubiquitous and cheap nowadays, which means they make great raw materials for hacking and electronics projects. This video will show you how you use a USB host shield to hack USB devices and use them with MIDI controllers, game controllers, and other devices.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to track a USB device.

Microsoft Build 2017, the first of Microsoft's big developer conferences for the year, is just a few weeks away. This very popular conference, which has been going on since 2011, is known to sell out fast. In 2015, it sold out in under an hour, and in 2016, in less than 5 minutes. This year was no different, according to VentureBeat; While not quite as fast as last year with so many rumors of HoloLens on the horizon at the time, this year's Build was sold out in 8 hours. And for this year's B...

These days, if you walk through Best Buy, you will see an entire area designated to smart home technology. Thanks to the interest and growth of the Internet of Things (IoT), this exciting new technology has finally entered the mainstream. Appliances, thermostats, and even the lighting throughout your house can be controlled from your computer or smartphone. You could also use artificial intelligence; Simply tell Amazon's Alexa what you want your house to do, and she will do it.

Hello, Null Byters. I'm Barrow, and I'm excited to introduce myself as the new admin here on Null Byte. Just like previous admins have done before me, I will be writing new guides, updating older guides if they need it, and responding to some of your issues in the forum. Before I get started with any of that, though, I wanted to talk a little bit about myself and the future of Null Byte.

You can easily share and transport your photo and videos on the Canon EOS 7D by using the wireless file transmission option. See exactly how sharing and downloading your files to computers and other devices works in this video. When the digital SLR camera is combined with the WFT-E5A Wireless File Transmitter, transmitting is easy.

This video tutorial from iDeviceTutz shows how to change the SSH root password for iPhone or iPod.When iPhone or iPod is jailbroken it sets its password to default - alpine.Thus your device becomes vulnerable from a network attack that could steal your information or identity. So you need to change your password as soon as possible when your device is jailbroken.For this you'll need Mobile Terminal program on your device and SSH client (Cyberduck or WinSCP) on your computer.First download and...

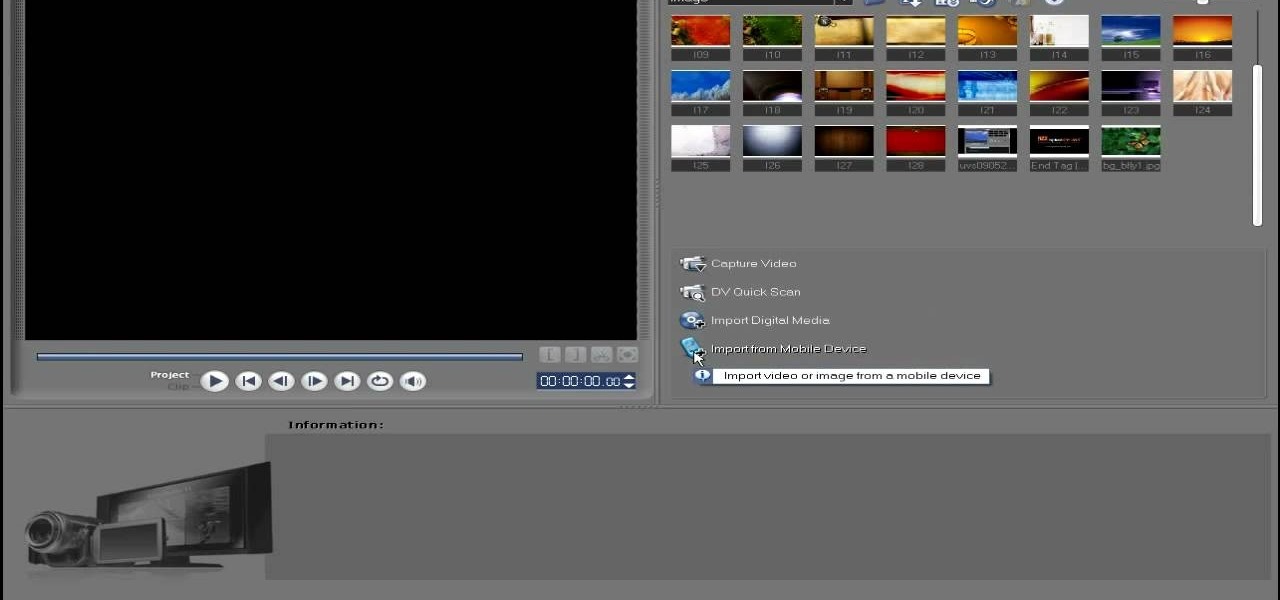
In this video tutorial, viewers learn how to import media from devices in Corel Video Studio. Begin by connecting your mobile device to the computer. It can be any device with a memory card or hard drive. Open the program and click on the Capture tab. Click on the option, Import from Mobile Device and select the device that you want. Select the file(s) that you wish to import and click OK. The program will then import the media to your selection window. This video will benefit those viewers w...

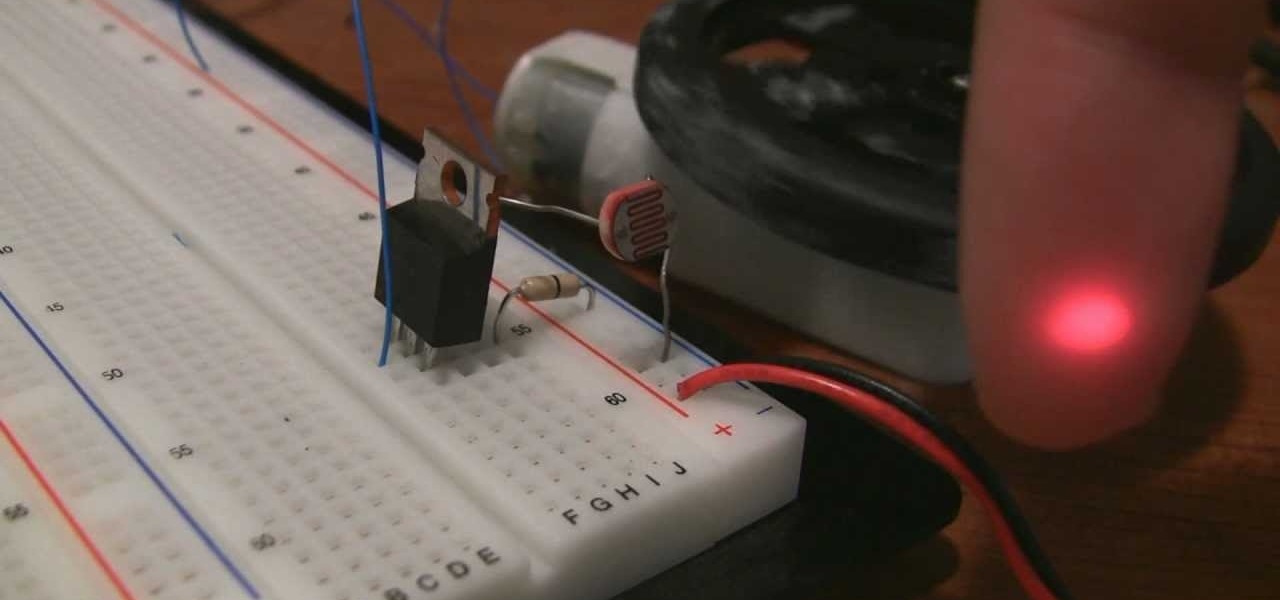
This video, incredibly short for it's massive content, will teach you how to make a laser tripwire that, combined with a photoresistor, can trigger just about any device. You can make traps, alarms, awesome party decorations, and all sorts of other awesome things with this easy-to-make device, provided you have a soldering iron and a local electronics store to buy some parts.

In these days of mobile technology, losing your iPhone or iPod Touch is almost worse than losing your car keys. It becomes one of the most frantic searches you've ever had to endure. But you can relax now, because you can use Apple's Find My iPhone, iPad or iPod Touch service to locate your lost device.

An accelerometer is capable of detecting how the device is being moved by the user, a feature which can add an extra level of functionality for an application which knows how to take advantage of it. This video explains several different methods for incorporating the presence of an accelerometer into your mobile content.

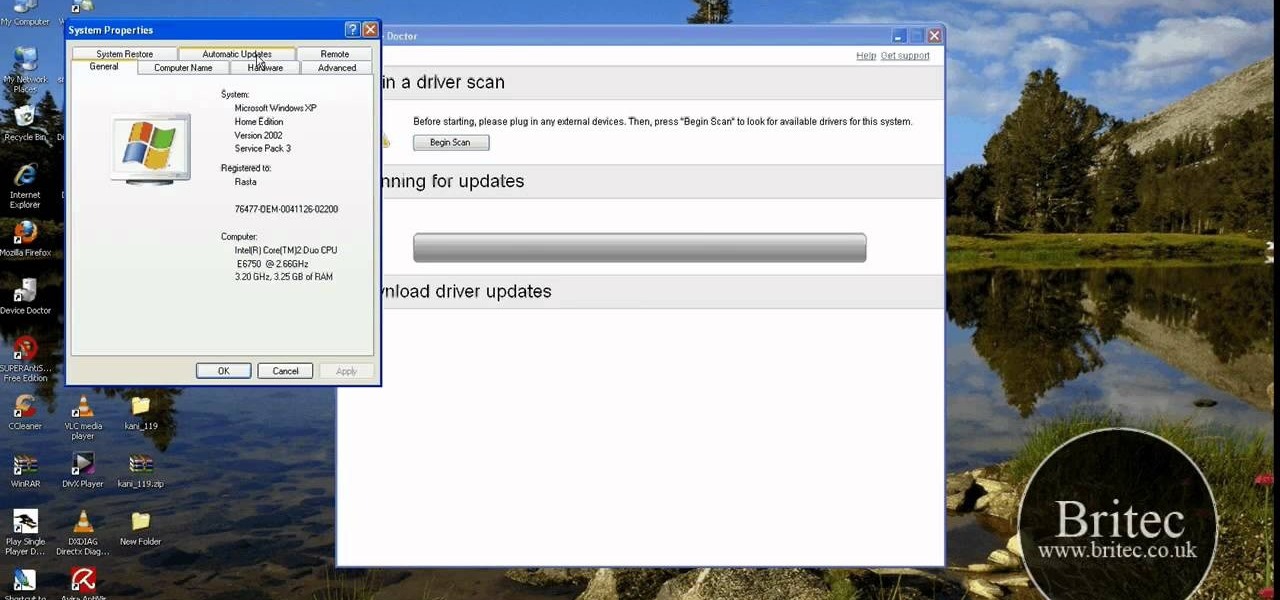
In this clip, you'll learn how to use the free Device Doctor app to update your device drivers. It's easy! So easy, in fact, that this home-computing how-to from the folks at Britec can present a complete overview of the process in just over five minutes. For more information, including step-by-step instructions, take a look.

In this video tutorial, viewers learn how to put their iPod device into recovery mode using Z-Phone. The Z-phone application does not work on 1st generation iPod devices. Begin by unplugging the device from your computer. Then hold down the power and center button until the device\s screen goes completely black. Now hold the center button as you connect the device back to your computer. Finish by following the process in iTunes to restore the device. This video will benefit those viewers who ...

If your Windows PC has been running rather slow lately and you're not sure why - you may have unknown devices taking up space and energy. Check out this tutorial for details on how to detect and disable unknown devices in Windows Device Manager.