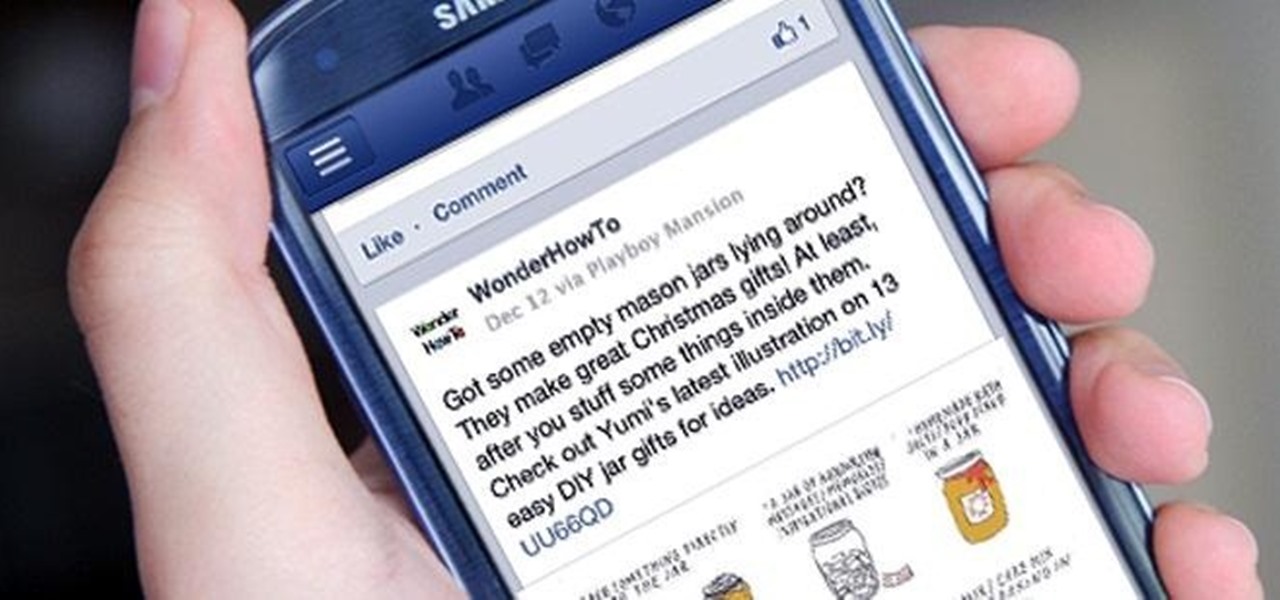
Depending on what mobile device you own, you'll see something that says "via device name" next to the date of your post on Facebook. If you're device is not recognized, you'll simply see a "via Mobile" note, which is what happens when I post from my phone. If you allowed your iPhone to be called iPhone when you logged into the app, it'll show up as a recognized device on Facebook, and will post "via iPhone." Same thing goes if you have a Samsung Galaxy S3 or Nexus 7 or iPad. It could also jus...

Make a bionic hearing spy device by hacking a megaphone! Kipkay brings you this hack video on how to use a megaphone to spy on people. You can pull in conversations up to 100 feet away! Check out Kipkay hiding in a tree, spying on people. It also works through walls. That's how to make a bionic hearing spy device!
If you've taken the time to jailbreak your iOS device, be it an iPod touch, iPhone, or iPad, you can display the iOS screen using your computer so that you can see the device's screen on your monitor or TV. All you need is the ScreenSplitr app to take advantage of this option.
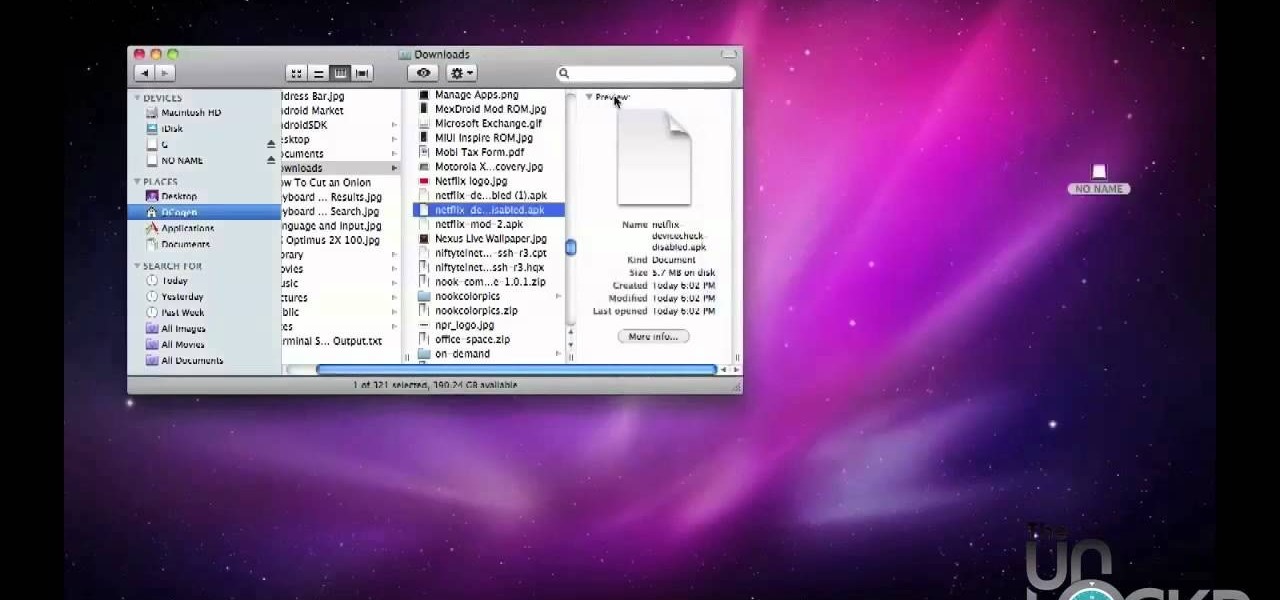
Want to watch Netflix Watch Instantly on your Android device? Watch this video and follow these instructions to learn how to hack any rooted Android device with an APK to work with Netflix. Watch thousands of streaming movies and TV shows with your hacked Android tablet or smartphone.

Watch this video to learn how to get Hulu streaming video on your Nook Color or other Android device. To do this, you'll need to download a modified Adobe Flash player and Dropbox. Turn your Nook Color or Android device into a full service entertainment machine.
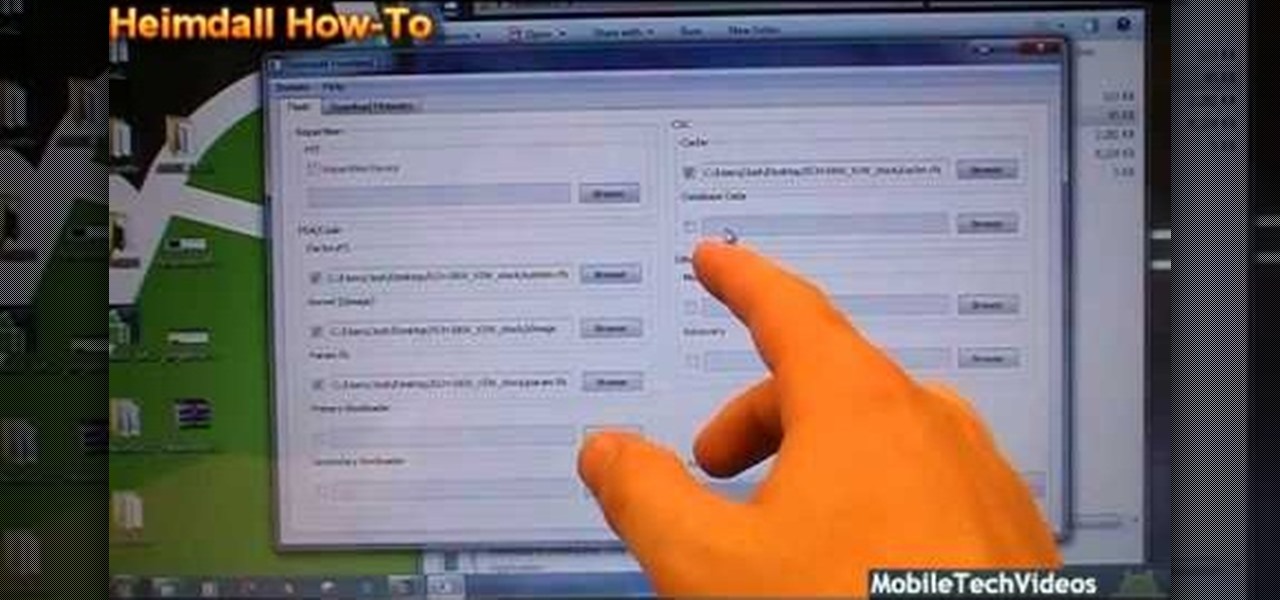
If you are looking for an alternative to Odin, you can try Heimdall, a third party software designed for flashing firmware to Samsung mobile devices, including smartphones and tablets. Watch this video to learn how to use Heimdall to install firmware on your Samsung Android devices.

With OpenSSH installed on your device, you can run your iPad-only apps smoothly on your iPhone or iPod touch. You'll need to download iTelePad2Pod on your Mac to get those iPad apps working on your other iOS devices. Then follow the instructions in the video to make sure you always have your favorite apps on you, no matter what the Apple device. Take your iPad everywhere, even when you leave it at home!

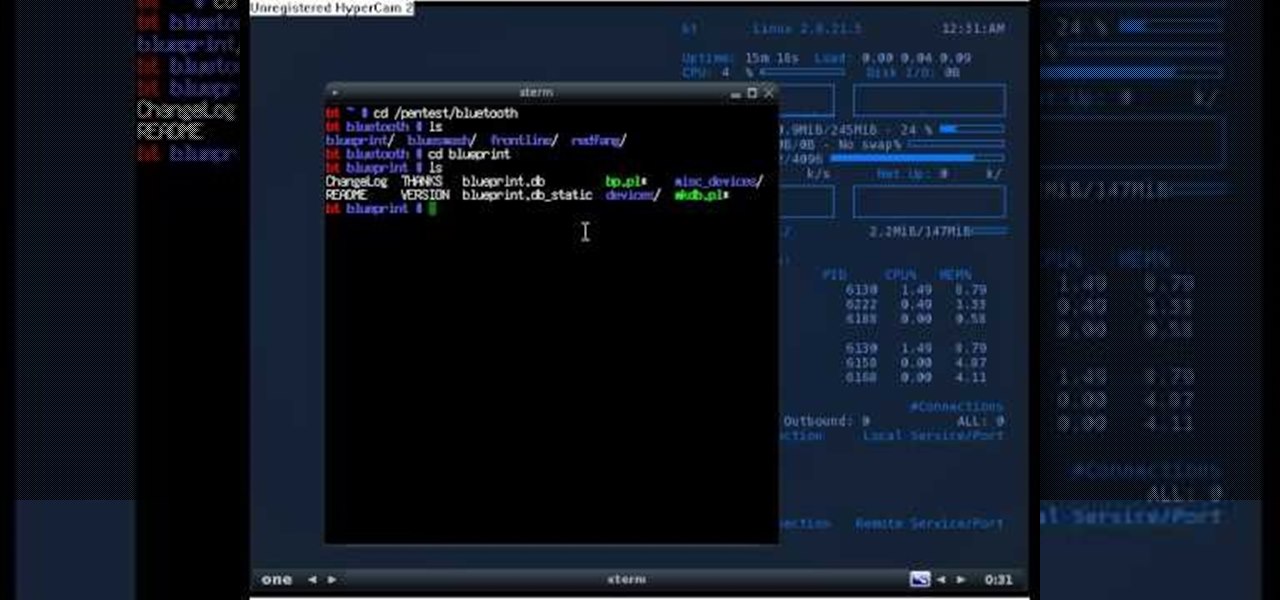
If you're new to the Bluetooth hacking world, here's a little background on using Linux BackTrack to hack a Bluetooh device: Linux Backtrack is a Live DVD device that offers security tools - like password crackers - that allow you penetrate networks.

Looking for a way to boost your iTouch device's wifi signal at home? The answer is rather simple - all you need is an Asian cooking wok! The shape of the pan functions like a satellite dish, boosting your signal!

Much like Mac OS X computers, Apple iOS mobile devices like the iPhone and iPad support VoiceOver, Apple's text-to-speech module. In this video clip, you'll learn how to turn it on and use it on your own iOS mobile device.

This tutorial shows you how to jailbreak your Apple touch device using blackra1n downloaded onto your computer. Make sure your iPhone or iPod touch is using version 3.1.2 of the operating software, then sync the device with your computer and run the blackra1n program. Now you can put apps from any publisher on your device, not just from the Apple store!

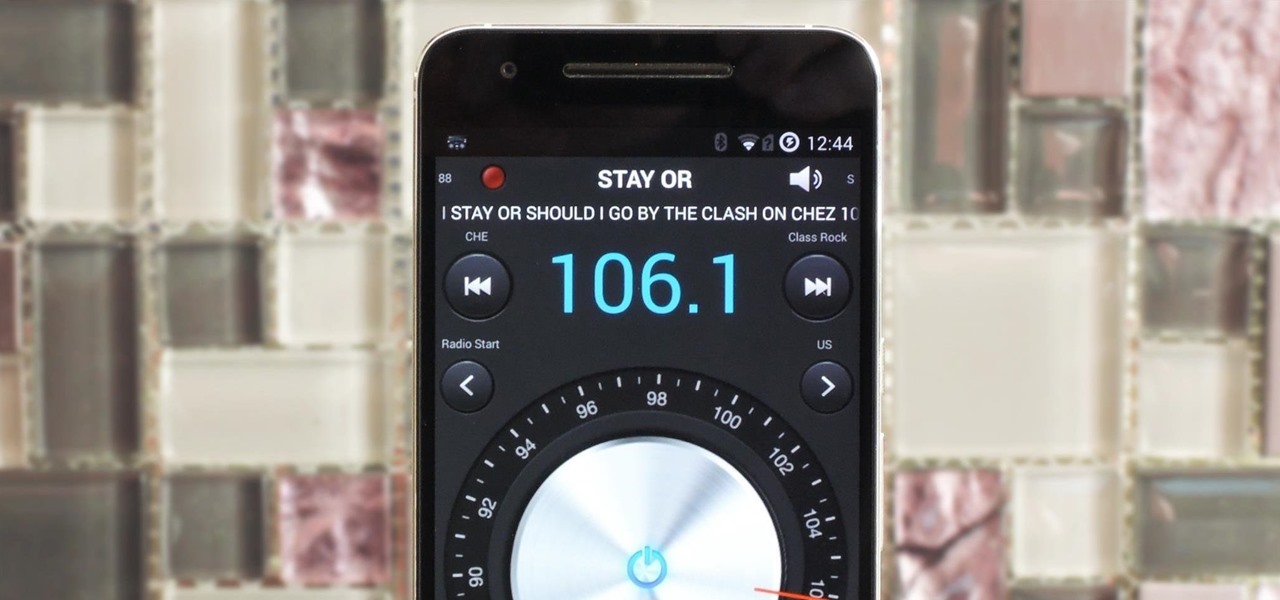
Android smartphones have all sorts of connectivity chips built in, including Bluetooth, Wi-Fi, GPS, NFC, and mobile data. But what about AM or FM radio, two of the most common methods of wireless communication?

Jeremy teaches us how to unbrick an iPod touch in this tutorial. First, hold the bottom button and top button simultaneously until the device shuts off. Hold these together until the logo comes on the device, then let go. The Apple logo will stay around for several seconds, maybe even minutes. Once the logo has disappeared, your regular screen should come back on the device. Now you will be able to resume using your device. If the logo stays on the screen for a long time, don't get worried, i...

DO you have an iPod Touch, but not know how to use Bluetooth devices with it? This video is here to show you the way. It features a simple demonstration of how to connect a Bluetooth device to an iPod touch using it's internal menus. Wireless headphone, playing your music in your car, and all other sorts of Bluetooth functions are now part of your iPod Touch's repertoire!

In this video, the instructor shows us how to tell if a device (cell phone or other device) is tethered or un-lockable. Before you begin, you must download a tool called f0recast onto your laptop or desktop computer. After the application is downloaded, you must plug in your device to your computer (Windows only). Once you've done this, a window will show up from F0recast that will show you all of your phone's information. This includes if it's lockable, if it's tethered, the serial #, model ...

This video demonstrates how to restore your iPhone or iPod Touch if you are experiencing freezing or errors. You will need to restore your device if you experienced problems after attempting to have a jailbroken device. First, you have to make sure the device is turned on and plugged into your computer and connected to iTunes. To start restoring the phone, you want to hold onto the "home" button and the "unlock" button at the same time and continue to hold it until the device turns off. Next,...

In this video we learn how to disassemble a T-Mobile G1 HTC phone for repair. First you want to make sure to wear an ESD wrist strap and make sure it's secure around your wrist. Then remove the battery from the device. Next unfasten the screws from the back of the housing on the G1. Then separate the housing from the device and then the speaker from the housing. Next unplug the UMTS cable and the GPS coaxial cable. Then remove the UMTS board and GPS boards from the device. Then disconnect the...

If you own an Apple iPod or iPhone, and you want to unbrick it, you'll need to prepare the device first. This video will show you how to put your Apple iPod or iPhone into DFU mode, which means Device Firmware Update. You'll need to attach the Apple device to your computer for iTunes. If you're looking to jailbreak the iPod, this will help you get to that step.

With .Mac Sync, you can ensure your contacts, bookmarks and other information is synchronized between all of your Apple devices. For more, and to learn how to synchronize your own Apple devices using .Mac Sync, watch this video tutorial from Apple.

Want to play old school Nintendo on your Windows Mobile devices, such as smartphones? Well, this video tutorial will show you how to install the NES emulator on that Windows Mobile electronic touchscreen device. Just sync up your cell phone, and download the software off of the Internet. Just think, you could be playing Mario in the palm of your hand, on your mobile phone.

I have never had any device that is easier to update the firmware than my iPhone. For anyone who may not be sure, firmware is basically the 'software' that runs a device's hardware. That's the easiest way I can think of to put it.

In this video tutorial, viewers learn how to use the Nokia N97 phone. The power button is located on the top of the phone to turn on/off the device. The menu key will open a list of applications for use. The call key will allow the users to make a phone call. The end key will bring the user to a previous screen or end a call. There is a headphone jack at the top of the device. One the side there is a Micro connector, and lock key. This video will benefit those viewers who are just using the N...

If you just purchased an Android enable mobile device with Bluetooth, then one of the main objectives you'll have on your to-do list is to set it up in your vehicle for hands-free dialing and phone calls. Activating Bluetooth inside your car is easy, and all you need to remember is a little number called zero. Actually, you need to remember it 4 times — Best Buy has answers. The Best Buy Mobile team explains how simple it is to activate Bluetooth settings on an Android cell phone.

From "Butterscotch" tutorial Michael Callahan walks you through updating your driver for Windows 7 operating system. This will help to improve communication between your printer, scanner, or any other devices digitally connected to your Personal Computer. Simply by going through the "start" menu you can then search and find out if there is new drivers for your devices. After that it will tell you and assist you downloading the new driver. Leaving you with the best driver software for your dev...

iPhone arena teaches viewers how to Jailbreak and iPhone or iPod touch using REDSN0W. This will work for both Mac and PC. First, you need to download is your device firmware file. Make sure it is 3.0 and restore you iPhone next. Now download the Redsn0w pack and launch it. Now, open Redsn0w and browse for the 3.0 firmware. Now, click next and there will be a bootloader file and browse for the file so you can unlock your device. Now, turn off your device and slide to power off. Now click next,...

In this how-to video, you will learn how to downgrade an iPhone or iPod Touch to 3.1.2. First, download the correct firmware model. Hold the home button and power button. Release the power button when the screen turns off. Make sure the device is plugged in while doing this. This will put the device in recovery mode. In iTunes, hold shift and click restore in the device screen. Next, navigate to the firmware you downloaded and click okay. This will downgrade the device to the firmware you dow...

In this video tutorial, viewers learn how to sync contacts between a Mac and Windows mobile device. Users will need to download and install the program, Sync Mate 2. Begin by opening the program and connecting the device to the computer. Under Synchronization in Plug ins, check the Contacts box. Then select the Synchronization direction, Surname and name order and select which contact groups to sync. Then click on Delete all contacts and select to delete the contacts on the computer or mobile...

This video demonstrates the steps to restore your iPhone or iPod Touch to original factory settings. This is a way to undo or repair any damage to your phone caused by downloading unauthorized files or corrupt files. Be aware that this will delete all the files that are on your device including music, pictures, videos and contacts, so use this method when all others fail. First connect the device to a computer via USB and select the device in iTunes as shown. Go to the device's information pa...

Dr. Allen Bridges shows how to incorporate the use of the CIDR (controlled intra-vaginal drug releasing devices) in a synchronization program for beef cattle. CIDR devices can be used to manage the reproductive cycles of female cows. Learn how to insert and CIDR devices and how to manage the estrus cycles of female cows for farming convenience, by watching this instructional video.

In this video, the author explains how you can use software called "Pinnacle Video Transfer" to convert your audio and video files to other audio, and video forms. This is so that you can carry them on whatever devices you want, and play them whenever you want. This video takes you through all those steps to convert your favorite audio and video files to different file formats. You would get a clear idea as to how you can easily capture videos by watching this great tutorial.

TWRP is the premiere custom recovery for Android because of how many devices it supports and how simple it is to use. But installing it in the first place hasn't always been the easiest thing to do — until now. With the help of a Magisk module, you can finally use one Android device to flash TWRP on another.

The biggest hurdle to rooting is that it usually requires a computer. Things get complicated when you're trying to use a desktop operating system to exploit a mobile OS, and the connection isn't always reliable. But with the help of Magisk, you can now use one Android phone to root another.

While many people may use Bluetooth every day, the majority don't know how it works or that it can be hacked. Bluetooth hacking gives a clear window into the world of the target. Nearly every device has Bluetooth capabilities, and people store a great deal of personal info on their phones and tablets. Hack their Bluetooth connection, and you may be able to access all of that data.

Apple's latest updates to its operating systems add another security feature to its Find My service, so you have an even better chance at locating your lost iPhone, iPad, or Mac should it ever happen. As long as you have the option enabled, you can leverage other Apple users' devices to find yours on the map.

Anyone who has been within a block of any wireless brick and mortar store or tech conference in the last couple of years has no doubt seen banners, posters, and videos promoting 5G high-speed wireless services on the way.

Returning to the spotlight after its debut at last year's CES, augmented reality smartglasses maker Rokid is back with a new update.

As Android device partners ship new products, Google has been diligent in its efforts to ensure that users can enjoy ARCore apps once they boot up their new toys.

Hacking Wi-Fi is a lot easier than most people think, but the ways of doing so are clustered around a few common techniques most hackers use. With a few simple actions, the average user can go a long way toward defending against the five most common methods of Wi-Fi hacking, which include password cracking, social engineering, WPS attacks, remote access, and rogue access points.

The world around us keeps getting smarter. Not only do we have advanced AI services like the Google Assistant, but now we've got the Internet of Things connecting physical objects to the digital world. It's amazing when you think about it, but the real sci-fi stuff starts to happen when these two technologies intersect.

Sharing your Wi-Fi password is like giving an unlimited pass to snoop around your network, allowing direct access even to LAN-connected devices like printers, routers, and security cameras. Most networks allow users to scan and attempt to log in to these connected devices. And if you haven't changed the default password on these devices, an attacker can simply try plugging them in.