
How To: Make a Simple UDP_Flooder in C pt2
Alright so last time I gave you a homework assignment. This week we're gonna look at my version of the UDP-Flooder.


Alright so last time I gave you a homework assignment. This week we're gonna look at my version of the UDP-Flooder.
Hello Strangers, This is my first article for null-byte and its about staying anonymous on the Internet. But the question is why would you want to stay anonymous online?

Welcome back, my hacker novitiates! In previous guides, we have used one of the most powerful hacking platforms on the planet, Metasploit, to perform numerous hacks. They ranged from exploiting Windows XP and Windows 7/8 vulnerabilities, to installing a keylogger and turning on a webcam remotely. We have even been able to save the world from nuclear annihilation, see if our girlfriend is cheating, spy on suspicious neighbors, evade antivirus detection, and more.

Welcome back, my rookie hackers! The more we know about a system or network, the better our chances of owning it and not leaving a trace for investigators to follow. One of the often overlooked sources for information is the Simple Network Management Protocol (SNMP). Many rookie hackers are not even aware of it, but it can prove to be a treasure trove of information, if you understand how it works and how to hack it.

Welcome back, my greenhorn hackers! I recently began a series on scripting and have received such positive feedback that I'm going to keep this series going. As I've said before, to graduate from the script kiddie to the pro hacker, you'll need to have some scripting skills. The better you are at scripting, the more advanced your hacking. Ultimately, we are leading up to developing the skills to build your own zero day exploits.

MAC addresses (not to be confused with Macs) are unique identifiers assigned to network devices in order to access the internet. Hotels use these Mac addresses in order to check if a registered patron has agreed to their terms and conditions, how much bandwidth is being consumed, and of course, whether they've paid or not.

1. Describes how to setup a VPN connection on Windows XP. 2. Goto Start-> Control Panel-> Network connections.
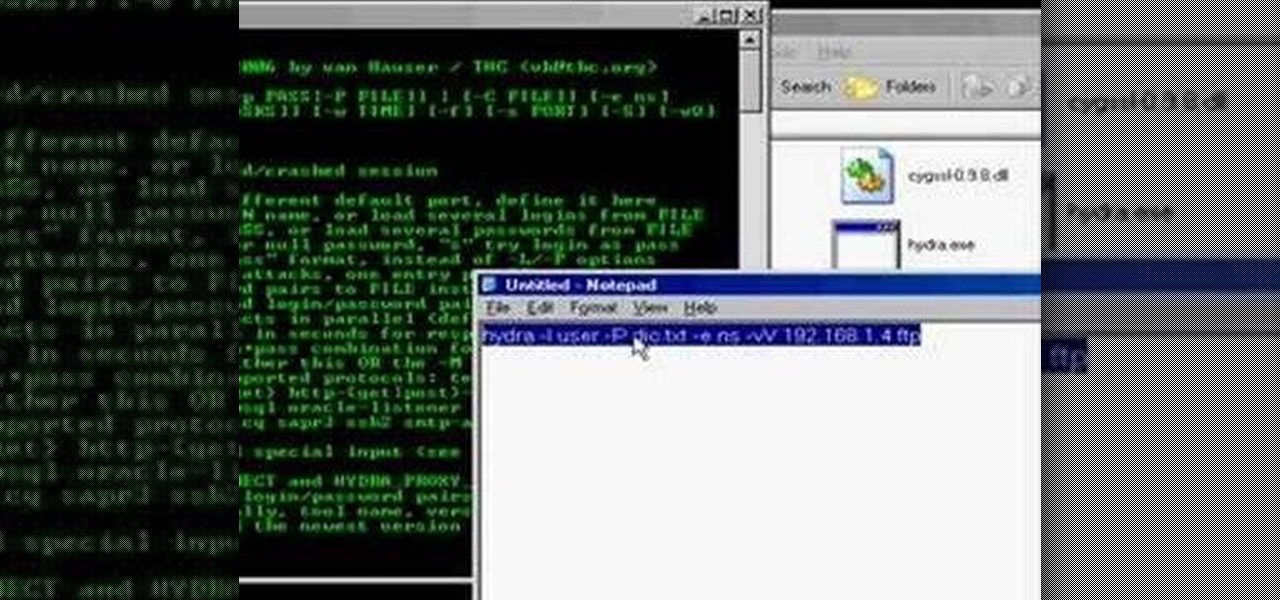
This is a how-to –video on using hydra 5.4 to crack FTP passwords. This video is intended for educational purpose only. It reveals the basics of hacking a FTP server using dictionary search technique. Here are the steps involved.

In this how to video, you will learn how to speed up your Azureus Vuze program. First, open up Azureus Vuze. Next, go to advanced, option, and click preferences. Select preferences and change the port to a number between 49152 to 65535. Once it is changed, go to transfer and make sure that these are set to zero. Once that is done, open your web browser and type in your default gateway. To find this out, go to system preferences, network, and router. Next, enter your user name and password to ...
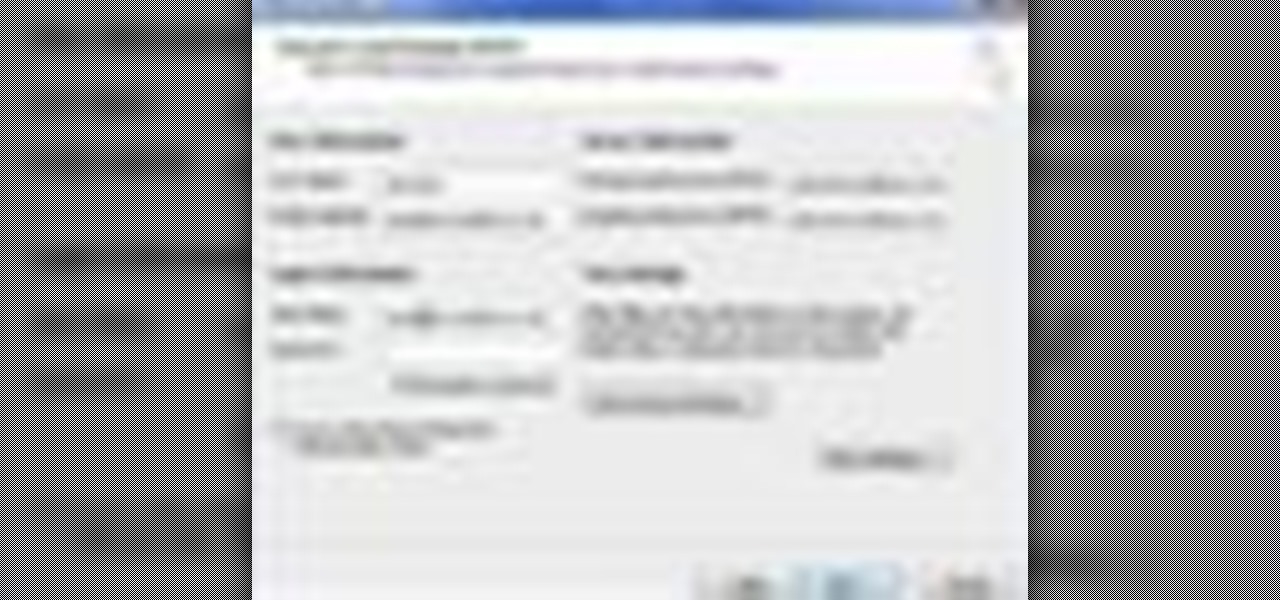
Tool is selected, followed by email accounts and a selection is made at the "add new email account" option , the "next" button is clicked. Pop3 is selected and the next button. The required information is filled in such as name, amail address, incoming and outgoing mail server, username; which is the same as the email address and the password is entered. The "remember password" option is selected, along with the "more settings" button. Within the more settings window, the company name and a r...

HighQuality Tutorials demonstrates how to change your iPod Touch alpine default password. Changing the default password is useful when using your iPod Touch in a public setting to make it less vulnerable to hacking. To change the default password, first open up your internet connection and search for Putty. Download the Putty program. Open and run the Putty program. Your host name will be your IP address for your iPod Touch. Select port 22 and SSH and open up the program. Log in as root and c...
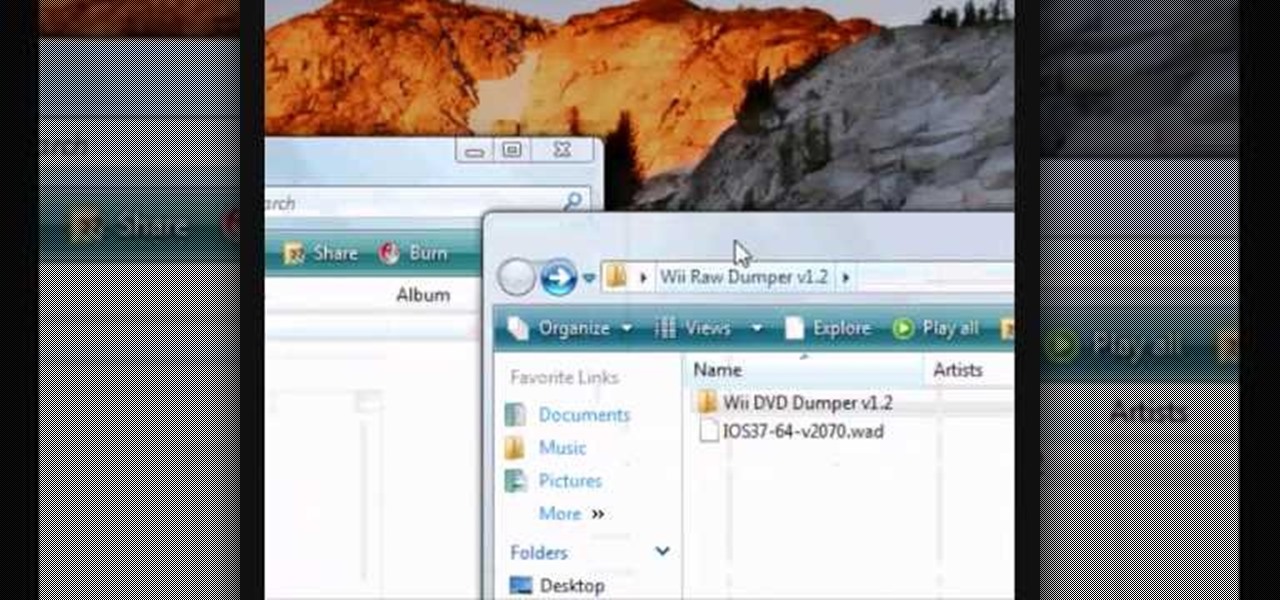
This video tutorial from noxad presents how to backup and burn games for Nintendo Wii game console.To setup game transfer from computer to your console you'll need any type of SD memory card. In this tutorial it's Lexor 1 GB SD card.Insert SD card into your computer card reader. Autoplay window will open, asking what action you want to perform. Select Open folder to view files.You can open SD card manually from My Computer window. (Start button-Computer).Make sure your SD card has folder name...
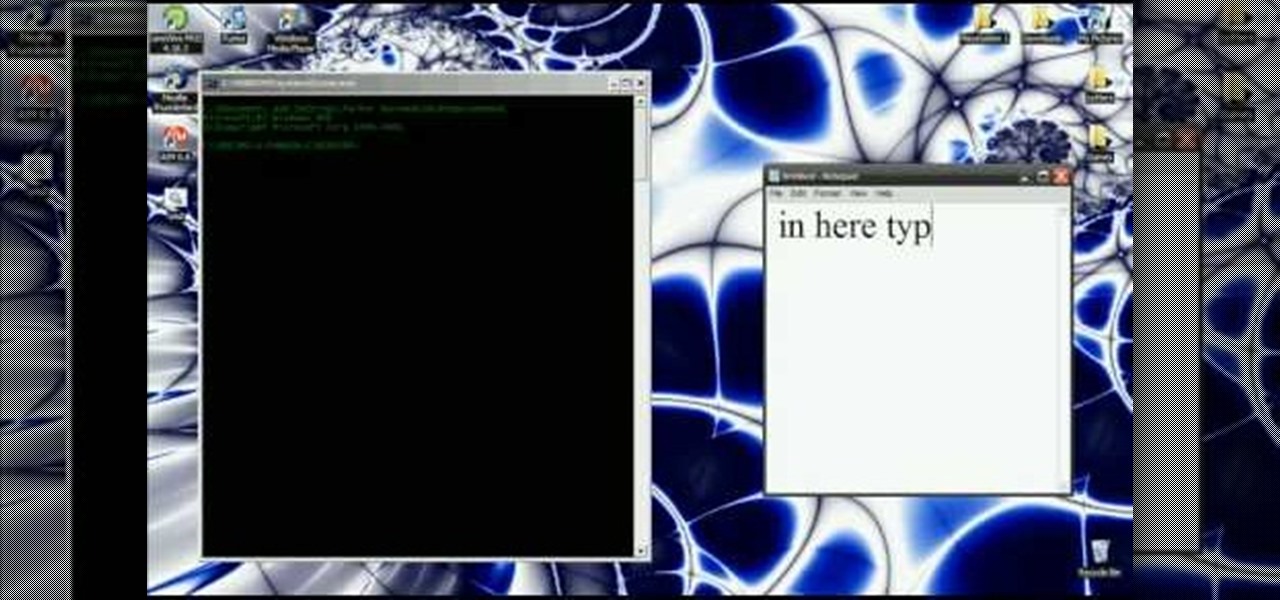
In this video you will learn how to get past website blocks on your school network. Some school computers have command prompts blocked. If this is the case then you will want to open a notepad. In the notepad type command, then save as something school related, making sure the file name ends with .bat. Do not save it on the desktop, but rather in a folder deeper on the unit. Once you've saved it, make sure no one is looking, then open the file. It will bring up a blank black window. In the bl...

If you don't have a Wi-Fi network, you can still easily SSH into your iPhone. Just follow the steps outlined in this video tutorial. First, you will need a Mac or iPhone along with Fuju. Just download the program. Once you have all of this, click on the Wi-Fi bar and click on Create New Network. As a name, click on iPhone SSH and click Manual. This creates your new network, which you will see on the desktop. Double click on it and then look at your iPhone. Go to iPhone. Connect to the network...
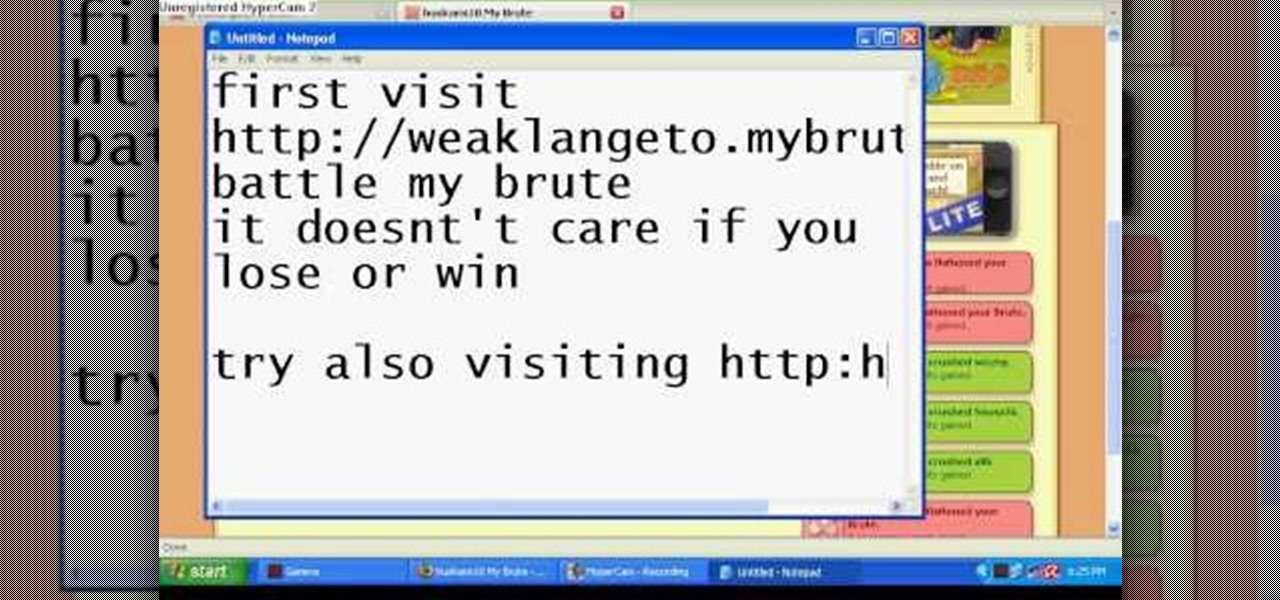
Hack mybrute with this mybrute cheat. MyBrute hacks, cheats, tricks. Watch this video tutorial to learn how to hack a wolf or bear in MyBrute (07/26/09). Without Cheat Engine!

All you need to remotely access your computer's iTunes library is your iPhone. Control itunes with your iPhone with this Howcast guide.

All you need to remotely access your AppleTV library is your iPhone. Learn how to control Apple TV with your iPhone with this Howcast guide.
Tired of writing addresses on your outgoing letter mail? Well, you can start printing them out instead! But how!?! If you have Microsoft Word, it's a cinch, and it's not just about making envelope address labels, it's about adding your own personal, creative touch to each one.
Chrome has just introduced some new UI elements for web exploration. The new URL bar is not intuitive. But once you get to grips with it, you will be so much more efficient in your address bar editing, pasting, and navigation.

Samsung's not one to make drastic changes to what already works. They've continued on with the IP68 rating under IEC 60529 first given to the Galaxy S8 all the way to the the Galaxy Note 10. If you're a little confused as to what this rating means, don't worry, it's actually pretty simple once you get to the meat and bones of it.

With a tiny computer, hackers can see every website you visit, exploit services on the network, and break into your Wi-Fi router's gateway to manipulate sensitive settings. These attacks can be performed from anywhere once the attacker's computer has been connected to the router via a network implant.

While our time with the Protostar VM from Exploit Exercises was lovely, we must move on to bigger things and harder challenges. Exploit Exercises' Fusion VM offers some more challenging binary exploitation levels for us to tackle. The biggest change is that these levels are all network services, which means we'll write our first remote exploits.

Barrow's article on Pupy made me wish for a RAT that could target an OS frequently used by gatekeepers at startups, tech companies, and creative firms: macOS. Once run, a RAT can do severe damage by dumping a user's stored credentials for many accounts. The best loot lives in the Chrome Password cache, and EvilOSX, an OS X RAT, infiltrates macOS and dumps these credentials.

On your iPhone, your phone number and Apple ID email address are the default ways in which somebody can contact you on FaceTime. While you can't remove your phone number as an option, you can withdraw your Apple ID email account. More importantly, you can add any other email addresses you'd like to the list, so you never have to worry about a friend, family member, or coworker not being able to audio or video chat with you.

RouterSploit is a powerful exploit framework similar to Metasploit, working to quickly identify and exploit common vulnerabilities in routers. And guess what. It can be run on most Android devices.

Hello My Fellow Hackerzz.. This is my first How-to and i'll be updating the “Hacking Android Using Kali” to msfvenom and some FAQ about known problems from comments. So Here we GO!!

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

It seems like every day now that we see a new headline on a cyber security breach. These headlines usually involve millions of records being stolen from some large financial institution or retailer. What doesn't reach the headlines are the many individual breaches that happen millions of times a day, all over the world.
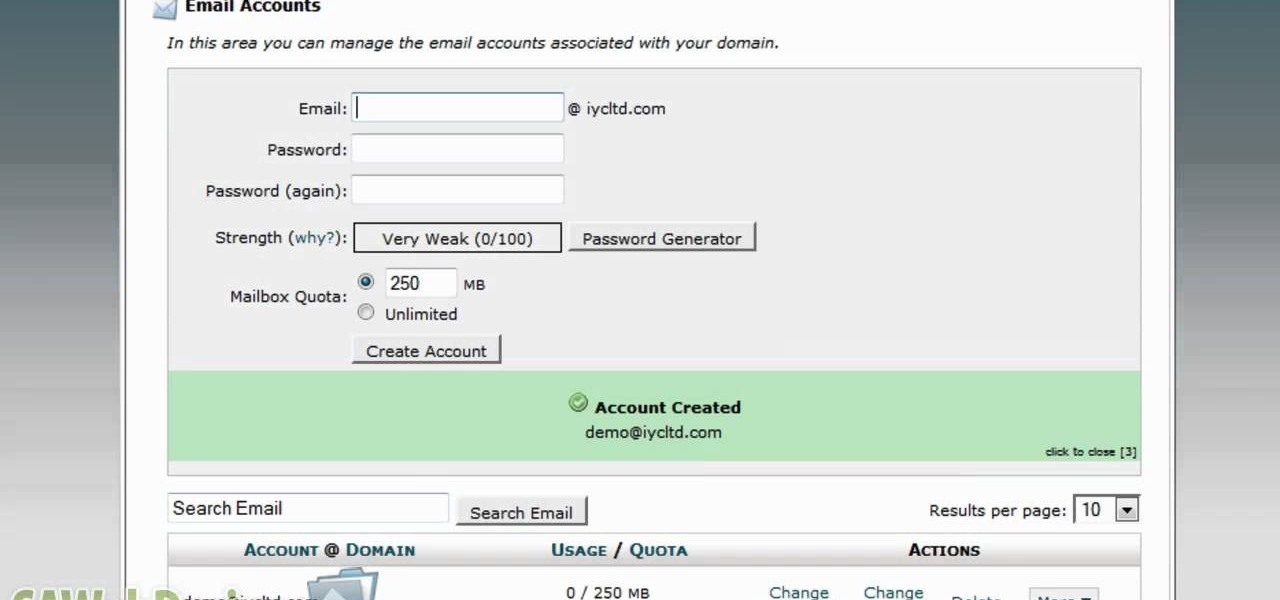
This tutorial is for people who are already using the cPanel Hosting account, and want to learn how to add a new email address to the existing account (such as for a new employee). It's an easy, quick process - this video shows you how!
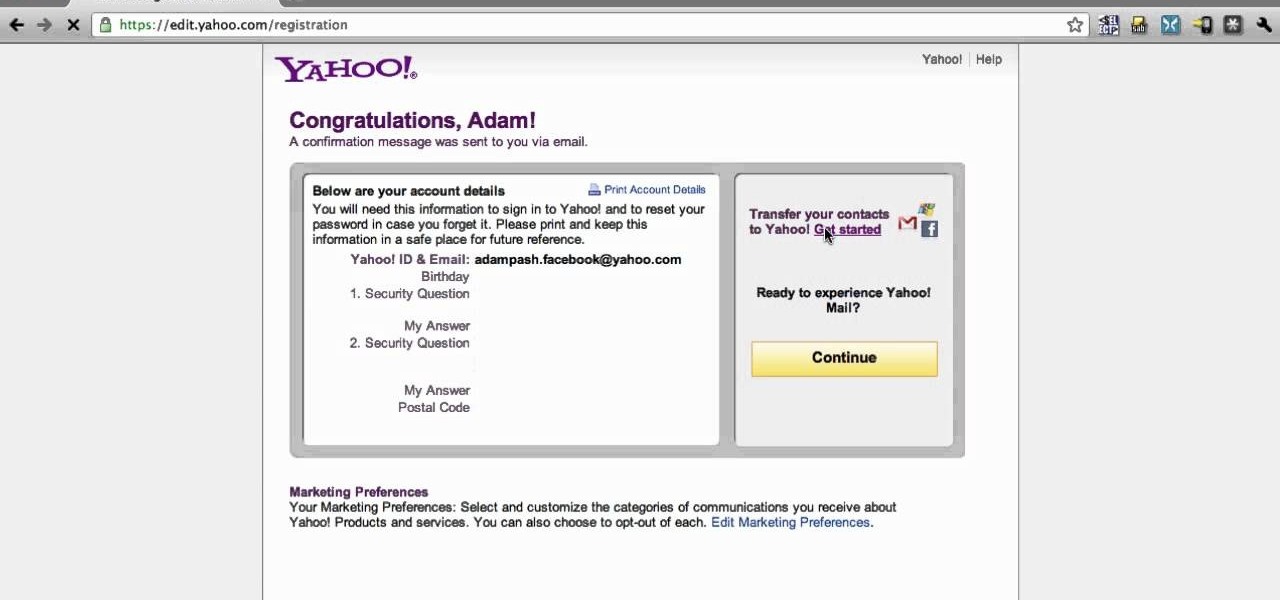
Facebook doesn't make it easy to export your contacts' email addresses from their site. But you can totally do it. And this clip will teach you everything you need to know. (Note: To follow along at home, you'll need to create a new Yahoo! Mail email account.)

In this tutorial, we learn how to import Facebook profile pictures into the Address Book on an Apple computer running the Mac OS X operating system. It's an easy process and this video presents a complete guide. For more information, including a full demonstration and detailed, step-by-step instructions, watch this helpful home-computing how-to.
A blind carbon copy (or BCC) is a way to send a mass email without letting your recipient see the other email addresses on your list. This computer skill is important in the business world, where privacy is prized. Hiding the addresses when sending your secret message is a useful technique you can use for any email program.

When you sign up with Gmail, Google gives you both an "@gmail.com" address and an "@googlemail.com" address. You can take advantage of this fact to reduce the amount of spam you receive. And this video tutorial from the people at CNET TV will show you how. Regain control of your Gmail inbox with this hacker's how-to.
The purpose of this video is to show an e-mail security flaw using telnet that allows hackers to send e-mails using anyone's e-mail address. Thankfully, many major e-mail providers have software that blocks this. My intention is to make people aware of this flaw so that other e-mail providers can protect themselves as well.

A flaw in WPS, or WiFi Protected Setup, known about for over a year by TNS, was finally exploited with proof of concept code. Both TNS, the discoverers of the exploit and Stefan at .braindump have created their respective "reaver" and "wpscrack" programs to exploit the WPS vulnerability. From this exploit, the WPA password can be recovered almost instantly in plain-text once the attack on the access point WPS is initiated, which normally takes 2-10 hours (depending on which program you use).

How to track an email address. Useful if you meet someone who says they are from somewhere e.g. LA as given in the video and you don't believe them. Go to the Rate a Bull site type in their email address and then hit return or 'find them'. The site will give you options to see information about them on the internet, MySpace, Facebook or other site or track the email. The site gives instructions on how to track the email via outlook, outlook express and other mail programs and the video shows ...

A hacker with privileged access to a Windows 10 computer can configure it to act as a web proxy, which allows the attacker to target devices and services on the network through the compromised computer. The probes and attacks appear to originate from the Windows 10 computer, making it difficult to detect the attacker's actual location.

With an inconspicuous Android phone and USB flash drive, an attacker can compromise a Windows 10 computer in less than 15 seconds. Once a root shell has been established, long-term persistence to the backdoor can be configured with just two simple commands — all while bypassing antivirus software and Windows Defender.

If you use Apple's email services and the "From:" field in your iPhone's Mail app is cluttered with @Mac.com, @Me.com, and @iCloud.com variations of the same address — along with third-party accounts — there's an easy way to declutter things and hide the addresses you don't use anymore.

If you need to do some hardcore multitasking on your Windows PC, a second monitor can go a long way towards getting things done. If you opt to "extend" your Windows desktop across a dual monitor setup, it's as if you have two computers side by side, with each display getting its own set of windows and programs that can be open simultaneously.