This is a great solution if you need to get something off your computer, but you are not home. Want access to your files stored at home? How about hosting a home web server? Static IPs are expensive, if you can even get one. We set up Dynamic DNS instead!
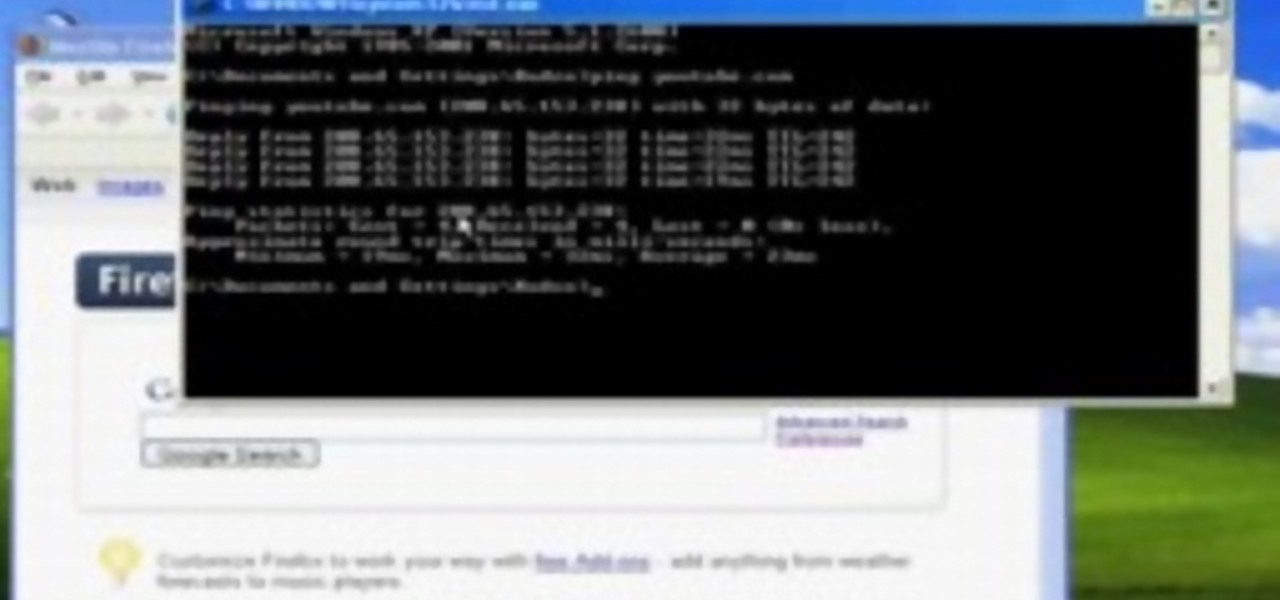
Get past your school's web filter without having to use a proxy server. Through the Start Menu, run the 'cmd' program. Then type in 'ping' plus the name of the site you want to visit. This will give you the IP address, which you can then use to get directly to the site you want to visit.

The first of a two part series on setting up your linux server and network for external access through your cable modem or DSL. Covers modifying the Linux servers network setting to a static IP address.

From booting into Fastboot mode with a single command to installing mods without root access, there's no shortage of reasons to use ADB. The catch, though, you had to be tied to a computer with a USB connection. However, a new feature in Android 11 finally allows you to run ADB commands over Wi-Fi instead of being tethered.

Hello, everyone. Stealth is a large part of any successful hack; if we don't get noticed, we're much less likely to be caught. In these next few articles, we'll be building a shell based on keeping us hidden from a firewall. There are many ways to stay hidden from a firewall, but we'll only be incorporating a couple into our shell. This article will outline and explain these evasion concepts and techniques.

Seldom in recent history has a cyber security event caused so much media stir (maybe because it happened to a media company?) and international relations upheaval. Cyber security breaches seem to take place daily of major corporations, but the Sony hack seems to have captured the American imagination and, for that matter, the whole world's attention.

Welcome back, my hackers novitiates! As you read my various hacking tutorials, you're probably asking yourself, "What are the chances that this hack will be detected and that I'll land behind bars, disappointing my dear mother who already thinks I'm a loser?"

FROMAN1115 teaches you how to change your NAT type to Open on your PlayStation 3. On the PlayStation 3, go to Settings-Network Settings-Settings and Connection Status List and write down your IP. Go to your PC and start your internet browser. Type in 192.168.1.1. This will bring up the router settings page. Go to Applications and games and then DMZ. Check the first box that says Enabled. Enter your IP address below and click ok. Your settings have been saved and you can enter a new internet m...

This tutorial is for those who've purchased an account with Private Internet Access to hide your VPN and would like to set it up in Kali. Please note, you can chose to run your PIA service from your Windows computer without configuring it in linux as long as you'll be using a NAT connection. Using a NAT connection will allow your Windows machine and Kali Virtual Machine to use the same IP address, hence if your IP is hidden on one, it will be hidden on the other.

Why did I write this when they're tons of scanning tools available.

After finding and monitoring nearby wireless access points and devices connected to them, hackers can use this information to bypass some types of security, like the kind used for Wi-Fi hotspots in coffee shops, hotels, and in flights high above the ground. By swapping their MAC address for that of someone already connected, a hacker can bypass the MAC filter and connect freely.

Hello ladies and gentlemen, I'm back with another informative(hopefully) article for you all. Once again I would like to apologize for my absence for about a week or so. I have some stuff going on with my life and university and I haven't found enough time to make a fully in-depth article. In this article I'm going to walk you through one of the main networking protocols when it comes to communication across the Internet between programs, aka UDP(User Datagram Protocol).

In my last post I introduced how to use ncat to connect to your Pi remotely, but what's the point to if you can't actually hack? This tutorial I'm gonna show you how to use very simple tools for a much bigger purpose. With that said, boot up our Pi and lets wreck havoc.

Want the convenience of a throwaway email address without all the hassle? How about anonymous text messaging so you can get to know someone before giving them your real information? Gliph has you covered. Gliph is a service that lets you create an identity around a set of three to five symbols called "artifacts" instead of your name, phone number, or email address. You choose how much information you reveal, and anytime you communicate with someone else who has Gliph, the data is protected us...

In this video from rscp1050 we learn how to SSH into a jailbroken ipod touch or iphone. First go into Cydia and search for SSH. You need to download OpenSSH. Then also install Toggle SSH. After installed, restart the iphone. Now on your computer, download WinSCP. Once installed, open it. Type in your IP address which can be found by going to your settings on your iphone. Click wifi, and click the blue arrow next to your network. There is your IP address. Then, User name is root. Password is a...

This video tutorial from iTouchMaster2 shows how to SSH to iPod or iPod Touch using FileZilla application.

This video shows the method to SSH into iPod Touch 1G or 2G. You need an iPod touch 1G/2G with Firmware 2.2.1 or previous (Windows), a Windows based computer and a jailbroken iPod Touch which has Wi-Fi connectivity. Open Cydia, go to search and type OpenSSH and install it. Go to settings, Wi-Fi and click on the blue arrow next to the network. Copy down your IP address from the resultant window. Open WinSCP.net and go to Downloads, installation package. Install the package and open WinSCP from...

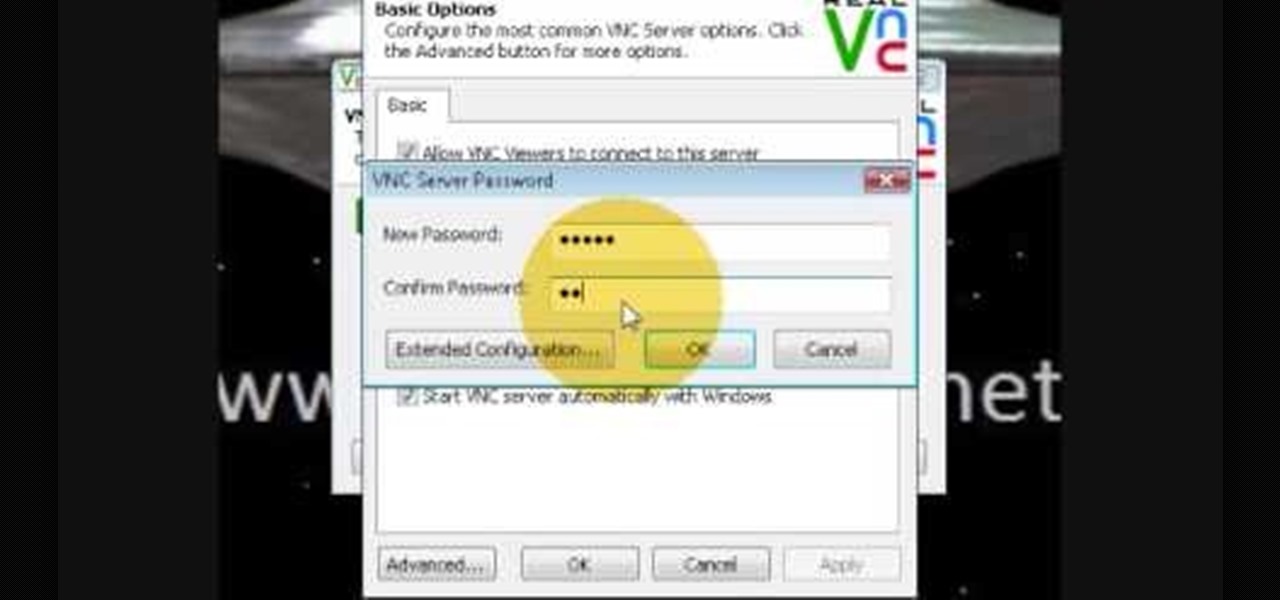
If you want to know how to monitor another computer screen with Real VNC, you must watch this video. Install Real VNC in your computer and computer that you're going to monitor. Remember the folder where you installed it and check the "Create a VNC Viewer desktop icon" checkbox. Write on a paper the IP address of the computer that you're going to monitor. On the VNC Server Status window, click Configure button. On the Authentication field, select VNC password and on the Encryption field, sele...

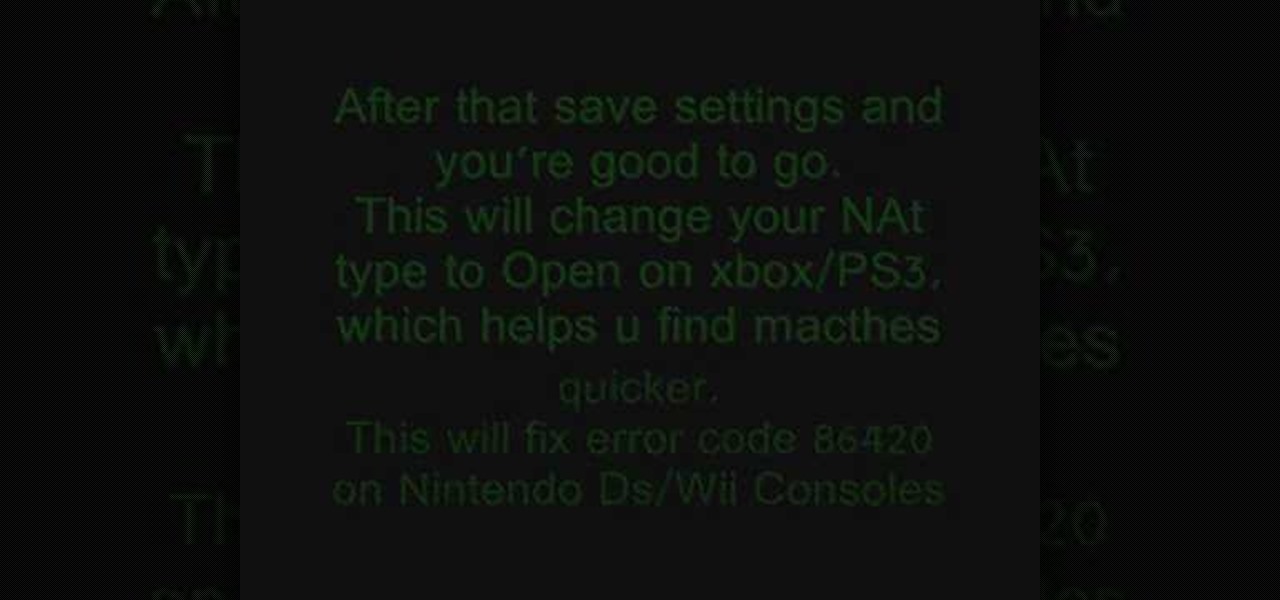
In this tutorial, we learn how to fix error code 86420 and change your NAT type to open. First, go to the website to change the settings for your Linksys router. Next, go to the applications tab that says "applications and gaming". After this, go to port range forwarding, then write in a name next to where it says "application name". Under "start" write the number 1 and under "end" write 6553, then keep "both" marked under protocol. Next, enter in the last 3 digits of your console's IP addres...

In this video tutorial, viewers learn how to protect their privacy online. Some information that is exposed every time you visit a website are your I.P. address, operating system and browser. To view what information that you are revealing to a website, visit the site provided in the video. This site will give you all the information that you are exposing in a website. This video will benefit those viewers who visit a lot of websites, and would like to learn how to view the their exposed info...

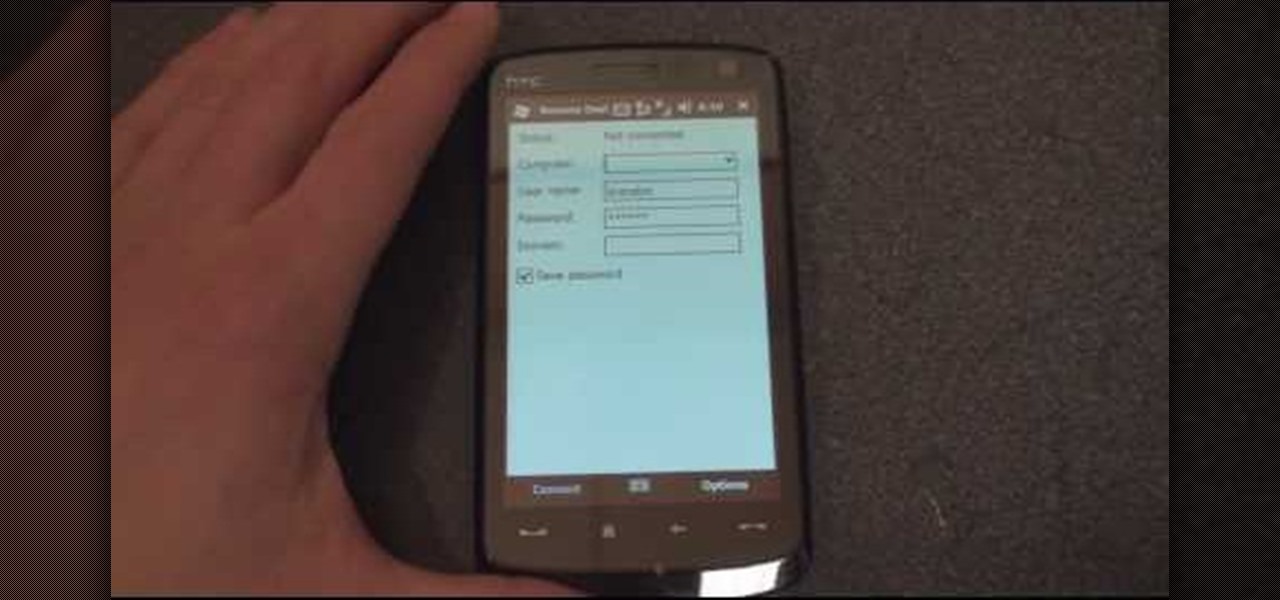
In this tutorial Brandon from Pocketnow.com will show you how to set up and use your remote desktop on a Windows mobile smart phone. Windows mobile remote desktop allows you to remotely access and control your Windows computer from your cellphone device, it is just like controlling your computer but in the palm of your hands. This guide will also show you how to get the Remote desktop software on your cell phone device if you don't already have it. The remote desktop requires for you to have ...

Welcome back, my rookie hackers! The Golden Fleece of hackers is to develop a zero-day exploit, an exploit that has not been seen by antivirus (AV) software or and intrusion detection system (IDS). A zero-day exploit is capable of skating right past these defenses as they do not contain a signature or another way of detecting them.

Social engineering is a pretty important item in a hacker's toolkit. In Mr robot there was a time, we saw Elliot using social engineering to gain access to his therapist's boyfriend's email and bank accounts by calling him and pretending to be someone from his bank, then Elliot asked him for some info that were really useful to gain access to his account, the target believed to be someone from the bank and gave him the info Elliot was looking for. But How Is It in the Real World?

Welcome back, my hacker noviates! In a recent post, I introduced you to Shodan, the world's most dangerous search engine. Shodan crawls the globe from IP to IP address, attempting to pull the banners of each web-enabled device and server it finds.

For people that live outside of the United States, how many times has this happened when surfing through U.S. streaming services? If you're outside of the U.S. market and want to stream stateside services like Hulu, MTV, CBS, Pandora, and others—you're in luck. Tunlr is an application that re-addresses certain data envelopes, tricking the receiver into thinking the data originated from within the U.S. by using its own DNS server's IP address. You can even watch some non-US shows stateside, li...

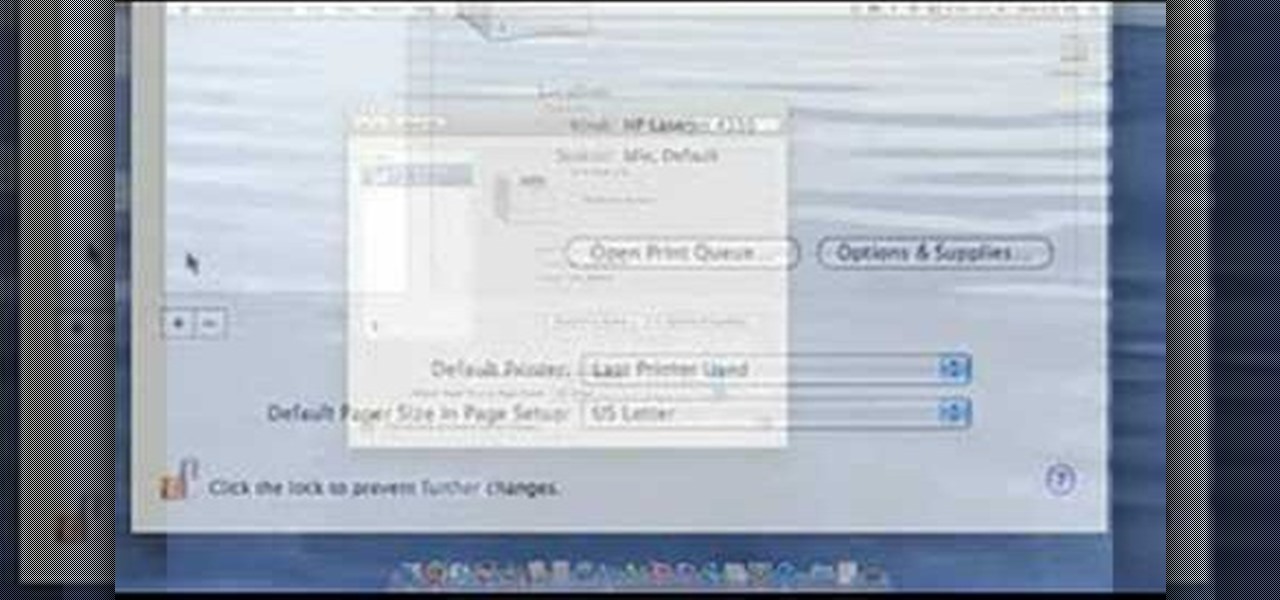
This video demonstrates how to setup a printer on a Macbook Pro.Open the document you wish to open. Go the File menu on the top bar menu and select Print. On the Print dialogue box, you will notice that no printer is selected. Click on the drop down menu to select Add A Printer. Click on the IP found on top of the window. Change the protocol to IPP or Internet Printing Protocol. On the address bar, type in the address of your printer then click on Add. Once done, you can now print your docume...

NetBIOS is a service that allows for communication over a network and is often used to join a domain and legacy applications. It is an older technology but still used in some environments today. Since it is an unsecured protocol, it can often be a good starting point when attacking a network. Scanning for NetBIOS shares with NBTScan and the Nmap Scripting Engine is a good way to begin.

Reconnaissance is the phase of an attack where a red team or hacker designs a strategy based on the information they can learn about the target, as well as what the available attack surface looks like. These scans can take time to discover relationships, but Raccoon OSINT scanner coordinates multiple automated scans to produce invasively detailed reports on a target with a single command.

If you're a U.S. expat living, traveling, or studying abroad, or just someone who typically uses virtual private networks (VPNs) in order to access the North American video libraries of services like Hulu or Netflix, you were probably surprised to see that these video streaming services don't work on your Chromecast or Chromecast 2.

Your English teacher is a creep. The way he looks at your girlfriend, the way he always spends ages with the girls in the class going over their work but not the boys, just the way he is.

In recent weeks, major bank websites around the world have experienced outages after being have been hit with Distributed Denial of Service (DDoS) attacks. Although few, if any, of these banks have been totally knocked offline, these DoS attacks have dramatically slowed the response time of their websites to legitimate customers. The most recent victim was the Royal Bank of Scotland. Due to this attack, RBS customers were unable to access their accounts for about an hour last week.

Welcome back, my fledgling hackers! A short while ago, I did a tutorial on conducting passive OS fingerprinting with p0f. As you remember, p0f is different from other operating system fingerprinting tools as it does not send any packets to the target, instead it simply takes packets off the wire and examines them to determine the operating system that sent them.

Welcome back, my greenhorn hackers! In a previous tutorial on hacking databases, I showed you how to find online databases and then how to enumerate the databases, tables, and columns. In this guide, we'll now exfiltrate, extract, remove—whatever term you prefer—the data from an online database.

Every Windows system includes command prompt; and while a lot of people on Null Byte and WonderHowTo in general know how to use it, some people don't know anything about it, even how to access it.

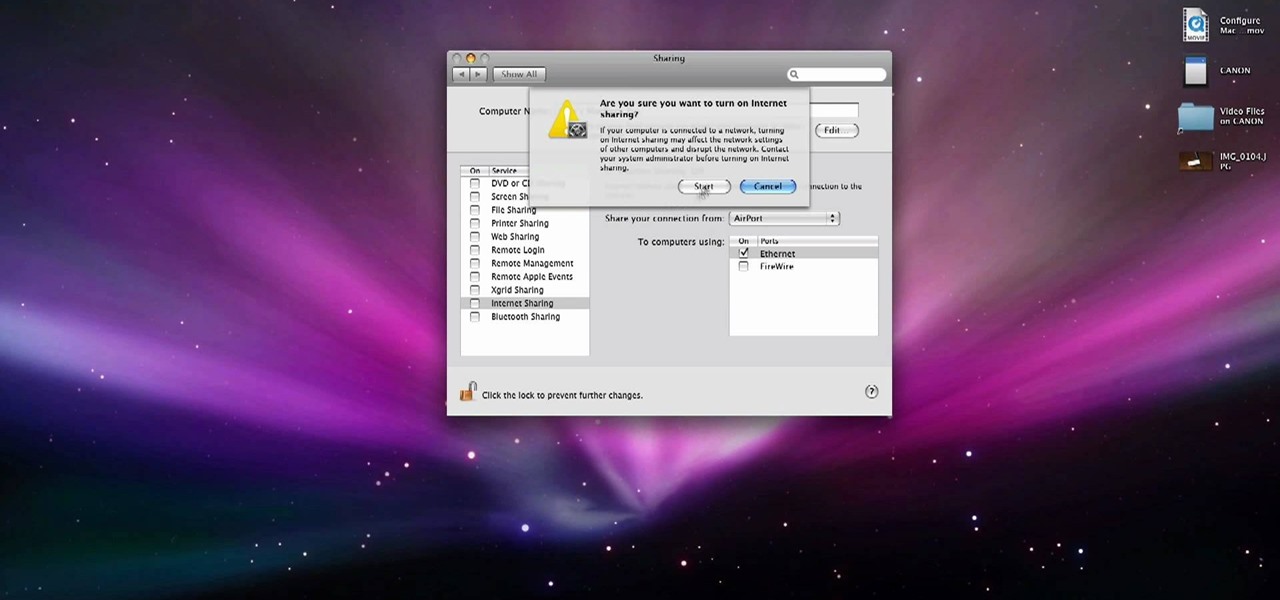
In this video, we learn how to use your Mac as a wireless adapter for Xbox Live. You will need: a Mac, monitor, Xbox, and Ethernet cord. Start out by going to system preferences, then going to the sharing folder. Go to internet sharing and make sure the Ethernet box and internet is selected. Then, click the box next to internet sharing and click "start". Now, go to the network option and go to advanced, TCIP, and then write down your sub maps and router IP address. After this, plug the Ethern...

In this video, we learn how to pull a compilation of computer pranks on a friend. The first trip is a mouse prank where you will open up the control panel and find the mouse settings. From here, you can switch the buttons from left to right and change the speeds of the mouse. Next, you can do network pranks by running cmd.exe as administrator. Then, go and see who is on the network and type in "msg /server:(ip address) and message". You can also do a ghost typing prank, which you will create ...

This is a short tutorial on how to use your iPhone as a remote control for your eeePC. First download touchpad from installer.app, as well as install VNSea if you don't have it.

This video includes instructions on how to get your PlayStation Portable (PSP) onto the BGSU wireless network.