Welcome back, my fellow hackerians! Today we'll be hacking Facebook profiles on your local network. You may think, "How is this useful, nobody but me is using my network." Well, you can use this on other Wi-Fi networks that are available for free (like at Starbucks) and crack their precious Facebook profile!

I'm not admitting to anything, but let's be honest, most of us download content on the Web from time to time. With copyright holders laying down the law more and more often, it can't hurt to do so with caution. And even if you aren't downloading copyrighted material, you still don't want companies snooping in on your online activities. So just how do you protect yourself when torrenting? Avoid "Open Communities"

Dropbox announced Tuesday that a recent security breach compromised a list that included the email addresses of certain Dropbox users. To avoid future complications, the service announced that it would be implementing two-factor authentication, and even more useful, a security page that lets you monitor all activity on your account. In light of this and other recent web security threats, you might also want to know that services like Gmail, Facebook, and Yahoo! Mail have similar pages where y...
In this video we learn how to use the address book in Windows XP. First go to Start, All Programs, Accessories, Address Book. You can choose to make it your default vCard viewer. Now in the address book, create a new contact by clicking new contact. Fill in the name and email address and click on add. Now there's an email associated with this record. You can also set up information about home address as well. It's important to put as much information as you know so it makes it easy to sort. W...
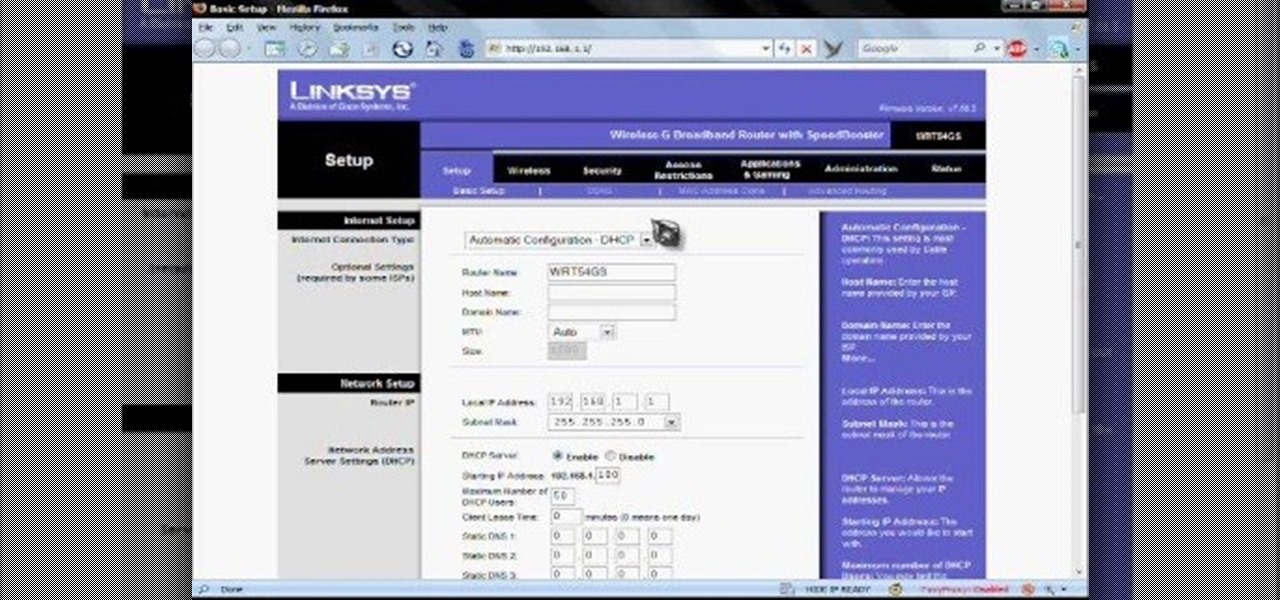
Learn how to force an IP change on a broadband connection with a linksys router.
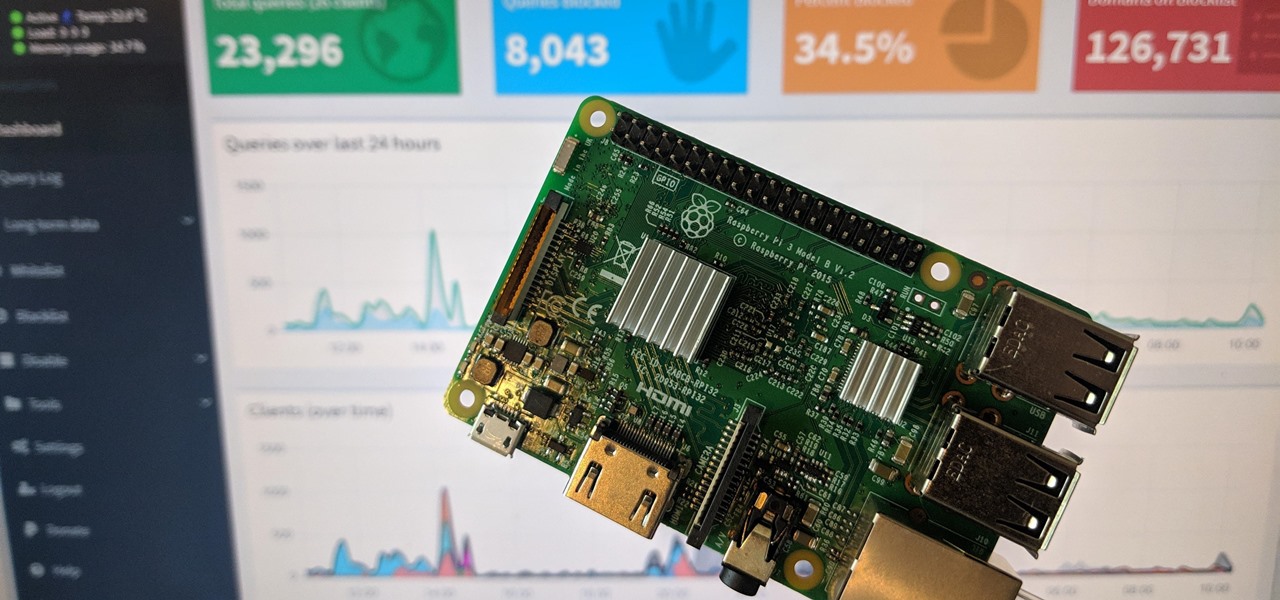
The Pi-hole project is a popular DNS-level ad blocker, but it can be much more than that. Its DNS-level filtering can also be used as a firewall of sorts to prevent malicious websites from resolving, as well as to keep privacy-killing trackers such as Google Analytics from ever loading in the browser. Let's take a look at setting a Pi-hole up and customizing a blacklist to suit your needs.

With a cheap computer, smaller than the Raspberry Pi, an attacker can create a remote hacking device. The device can be attached to a target router without anyone's knowledge and enable the hacker to perform a variety of network-based attacks from anywhere in the world.

Welcome back my fellow hackers. Today I'm going to teach you how to preform an Idle Scan. You may be asking what is an Idle Scan. Its a very stealthy scan because you don't use your own ip you use a zombie (in computer terms).

Welcome back, my hacker wannabees! Most of my recent posts have addressed using Metasploit’s Meterpreter and what we can do once we have embedded it on the victim’s system. This includes remotely installing a keylogger, enabling the webcam, enabling the microphone and recording, disabling the antivirus software, among many other things. The list is almost unlimited.

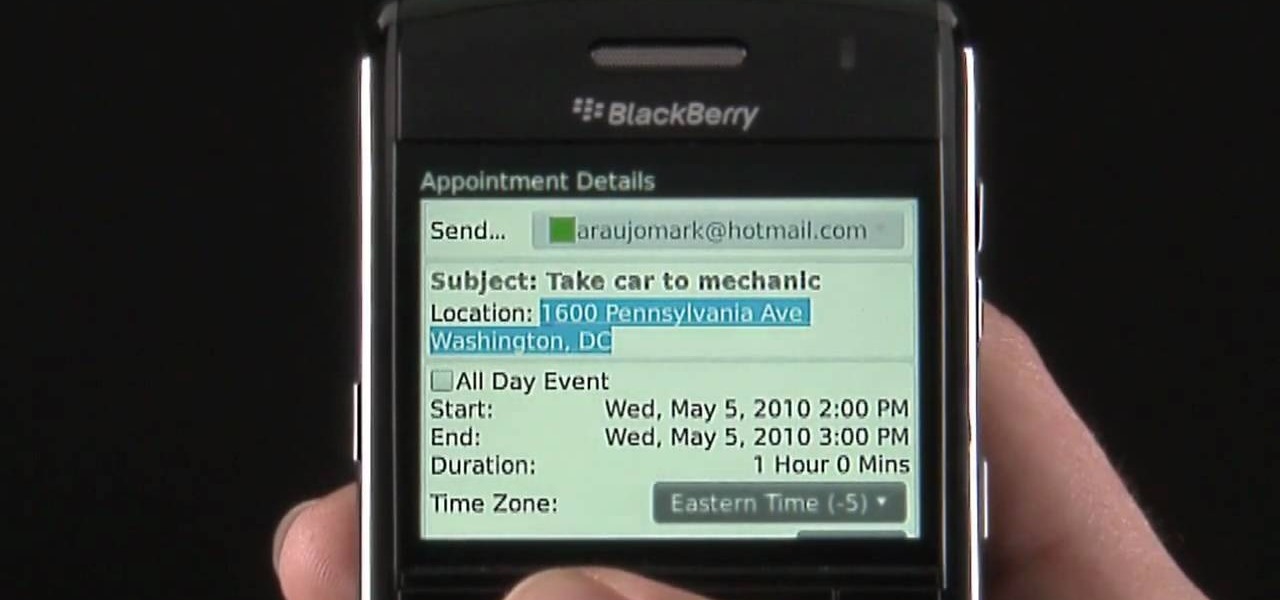
Learn how to take advantage of the Address Recognition feature built into the BlackBerry Bold 9650 phone. This clip will show you how it's done. Whether you're the proud owner of a BlackBerry smartphone or are merely considering picking one up, you're sure to be well served by this video guide. For detailed information, including step-by-step instructions, take a look.

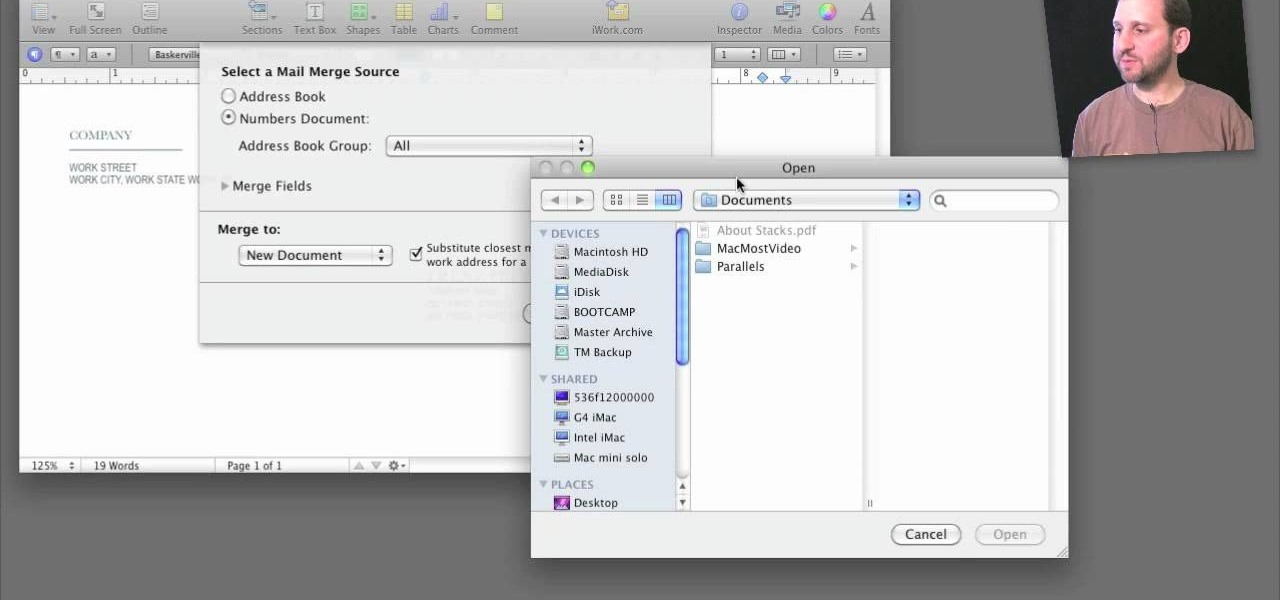
A step-by-step guide that will walk you through Mail Merge on a Mac computer. You will gain how to prep and print envelopes, letters or any document that you need to send to different names and addresses on each item. You can pull the data from your address book or from a Numbers Spreadsheet and will see how to modify and merge the information you will need to successfully set up your documents.

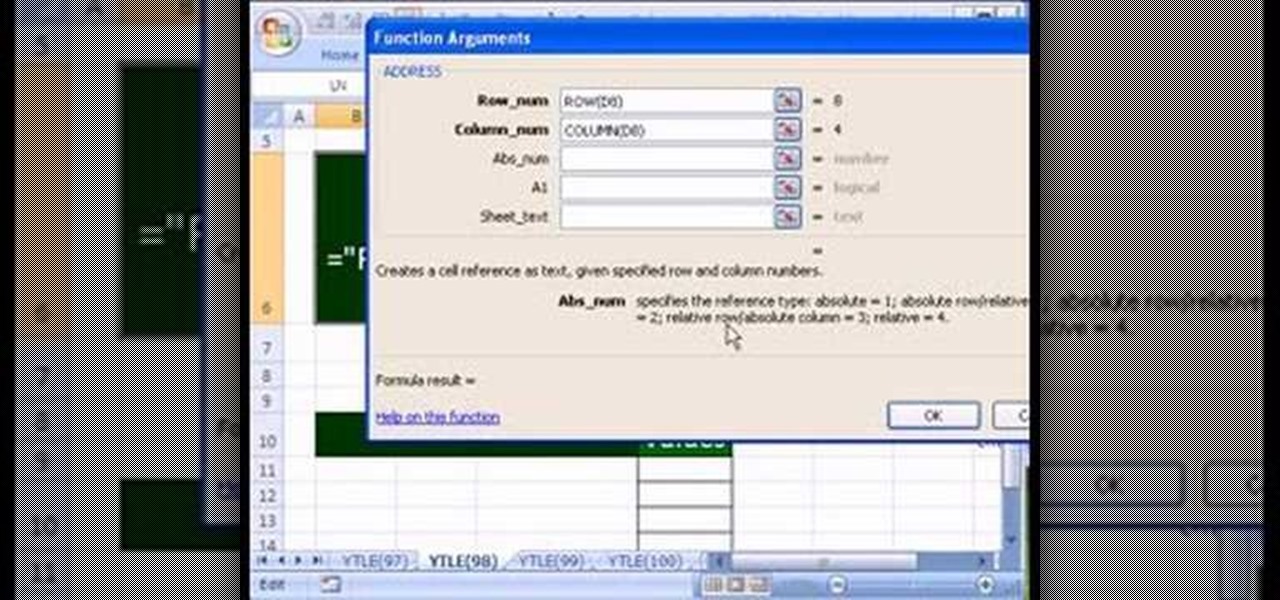
Love Microsoft Excel? This clip contains a tip that just might induce you to. With this free video tutorial from ExcelIsFun, the 98th installment of his "YouTubers Love Excel" or YTLE series of free video MS Excel lessons, you'll learn how to use the ADDRESS function to make labels in templates easier for users to understand.

Kevin Rose is joined by John Todd, a well known, leading Asterisk expert, to introduce you to the amazing VoIP (Voice over IP) world of Asterisk, the open source voip telephony toolkit. In this episode, Kevin and John take you through the installation and configuration of this powerful tool, and show how it can be used to give anyone complete control over their phone experiences, such as voice over wifi, eliminating phone costs, choosing from hundreds of VoIP providers, creating your own voic...

Now you can make sure your home address is in the right location on Google Maps. If it's not, you can move it to the correct spot. Try it at maps.google.com!!

In this tutorial, we learn how to quickly find your MAC address. This is the address that identifies your computer on a network. When you go to a campus, you will need to register your computer with a resnet so you can access the internet. To find the address, you will head to the Apple menu, then click 'about this MAC'. Click on the 'more' button and then click on 'network' and 'built in Ethernet'. This is the MAC address that you will need to register your computer, you may have a few of th...

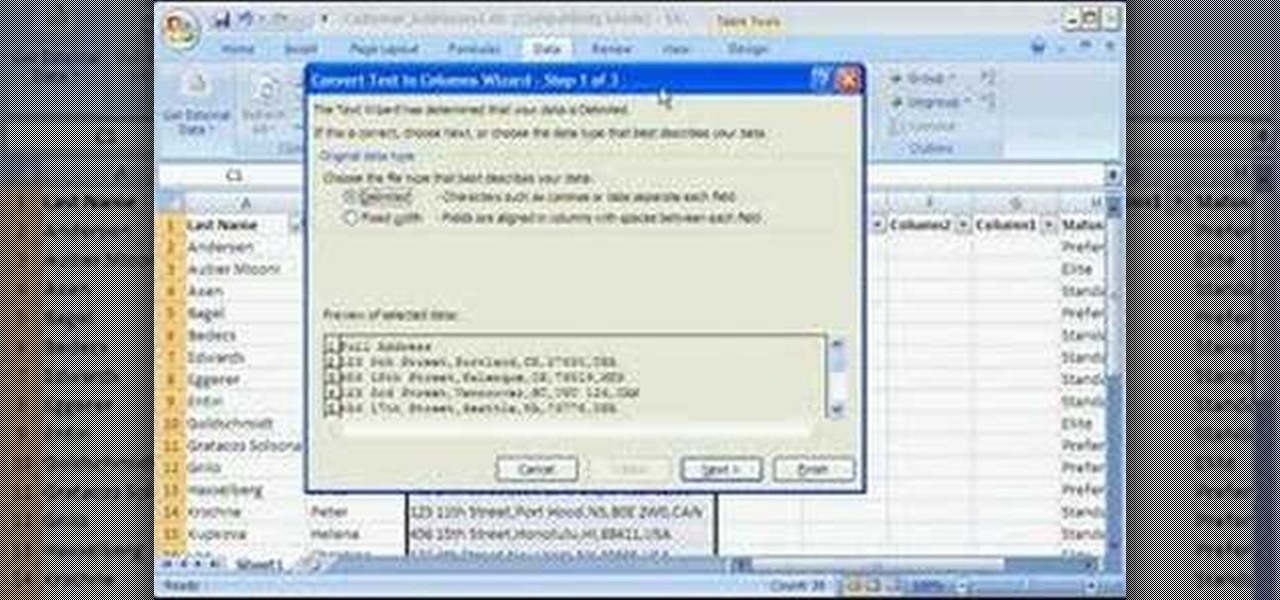
Storing information, such as a full address, in one column can limit what you can do with that information. For example, you can't easily filter or sort by part of the address, such as country/region or city. However, if you break up the address into its parts — street address, city, state/province, postal code, country/region — one for each column, you can remove those limits. Watch this instructional video to see how to use the Convert Text to Columns Wizard to automatically break up a sing...

Systm is the Do It Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. We will help you avoid pitfalls and get your project up and running fast.

This video will show you how to record video on your Apple iPhone 3G for free! This is a complete guide to installing the iPhone Video Recorder on your iPhone 3G, which also works on the First Generation iPhone.

When it comes to resistance to the elements, Samsung seems to believe in the old saying "if it ain't broke, don't fix it." They've carried over the IP68 rating under IEC 60529 that was first found on the S8 all the way to their tenth-anniversary flagship, the Galaxy S10. While this certainly sounds great on paper, it's natural to want to dig a little deeper and find out what the rating means.

It's not uncommon for hackers to attempt to move laterally between devices in proximity of a compromised device to maintain a prolonged presence in the network. Malware utilizing USB flash sticks to self-replicate and compromise air-gapped machines isn't a new concept.

Leaked databases get passed around the internet and no one seems to notice. We've become desensitized to the data breaches that occur on a daily basis because it happens so frequently. Join me as I illustrate why reusing passwords across multiple websites is a truly awful practice — and compromise hundreds of social media accounts in the process.

After numerous scandals like the Equifax data breach and the 2016 US election, cybersecurity has become a significant issue for Americans. Unfortunately, anytime we use our devices, we're open to a cyber attack — especially when we browse the web. However, there are ways that we can make it harder for hackers and data miners.

A router is the core of anyone's internet experience, but most people don't spend much time setting up this critical piece of hardware. Old firmware, default passwords, and other configuration issues continue to haunt many organizations. Exploiting the poor, neglected computer inside these routers has become so popular and easy that automated tools have been created to make the process a breeze.

OTW's great Tutorial Hack Like a Pro: How to Save the World from Nuclear Annihilation gives me the inspiration to try this on Win7 sp1.

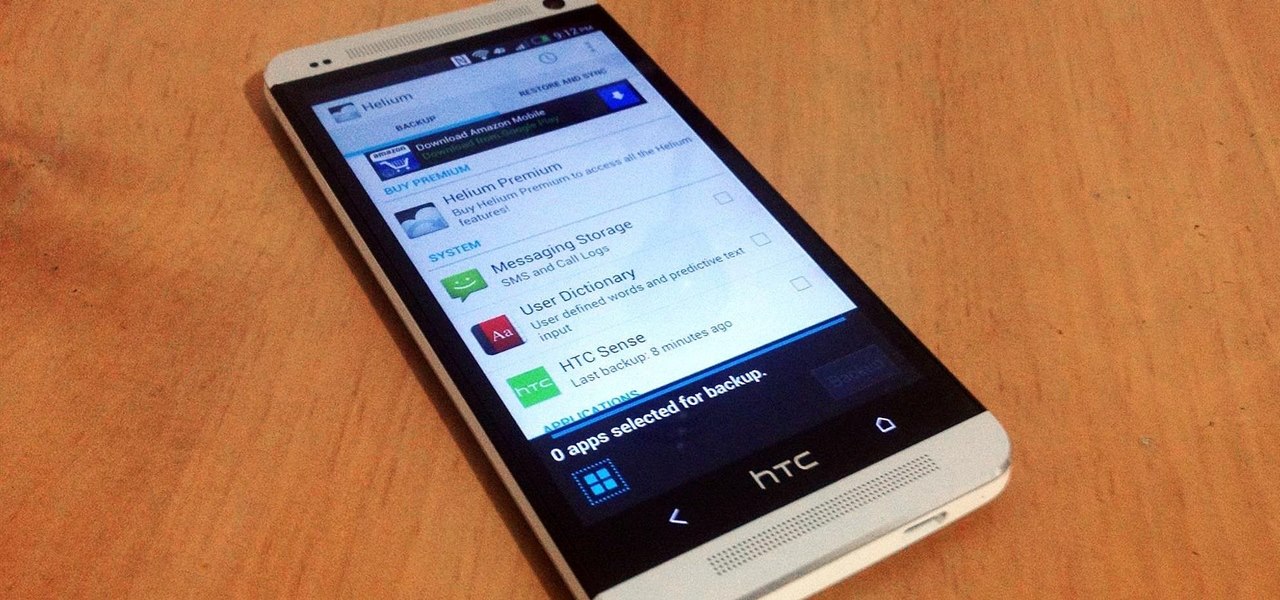
When you upgrade to a new Android smartphone like the HTC One, you can have browser bookmarks, Wi-Fi passwords, and other settings quickly transferred over from your old device using your Google Account backup. However, you'll still have to download apps individually from your Google Play list, and not all of your saved progress will be transferred over. Fortunately, there is a third-party app that will allow you to backup and restore your apps—with all their data.

If you are are creating a new computer network connection and aren't sure which IP range to use, watch this video. It will explain the differences between the three IP address ranges and which one would work best for a network of your size.

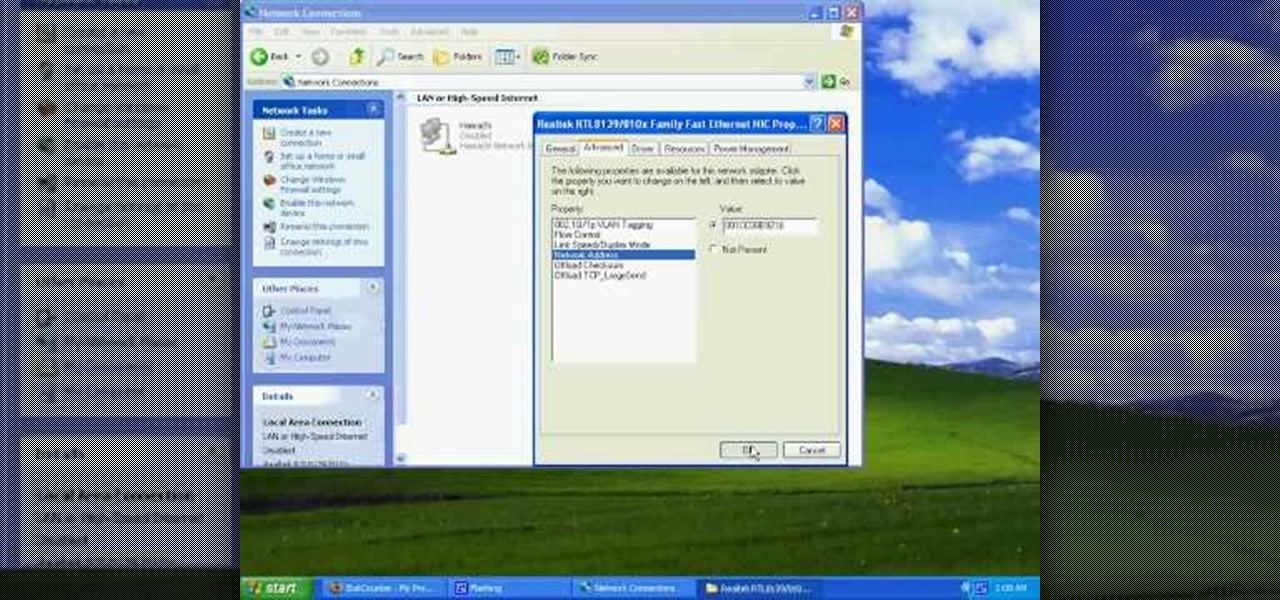
This video tutorial from tarunkumarsinghal shows how to change Mac address on Windows XP. Click Start menu and then Control Panel. Make sure control panel window is in classic view mode. If not, change it to classic from the left pane.

This is a simple and easy way to change your NAT settings to open. First, open the command prompt. Type ipconfig, and then look for an IP next to default gateway. Make sure that you remember it. Type that IP in your browser. Enter your router information. Go to the administration tab, and enable UPnP. If you did this right your NAT settings should be open. You will see a significant change. You will be able to join and play games easier, and matches will be made quicker. This is a very easy p...

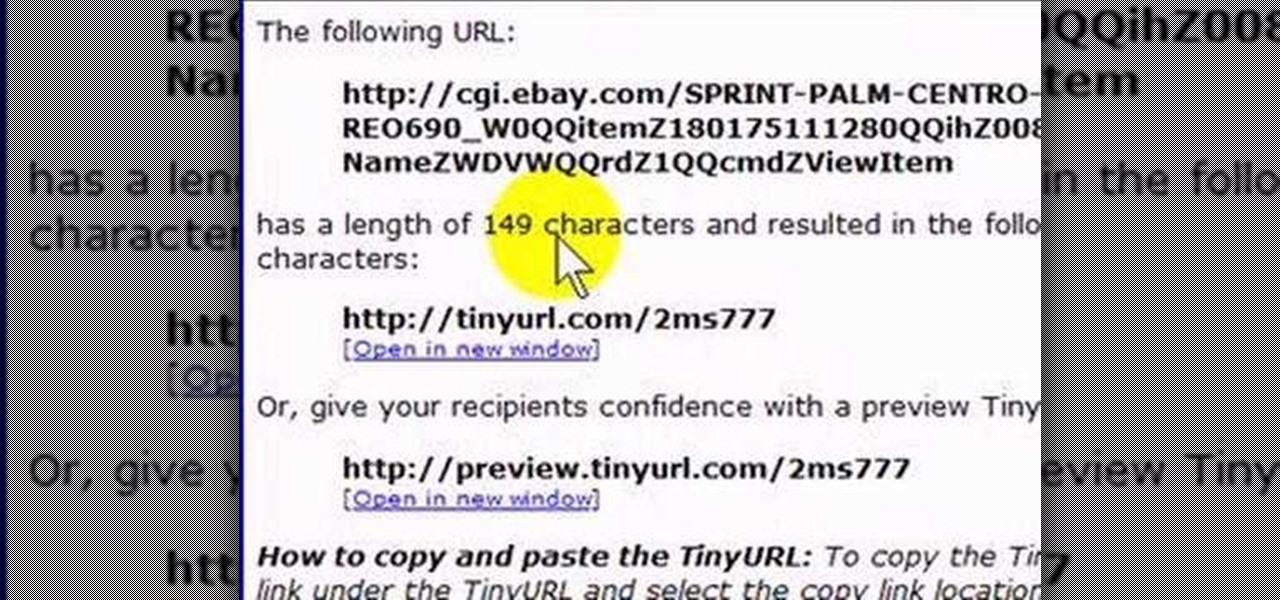
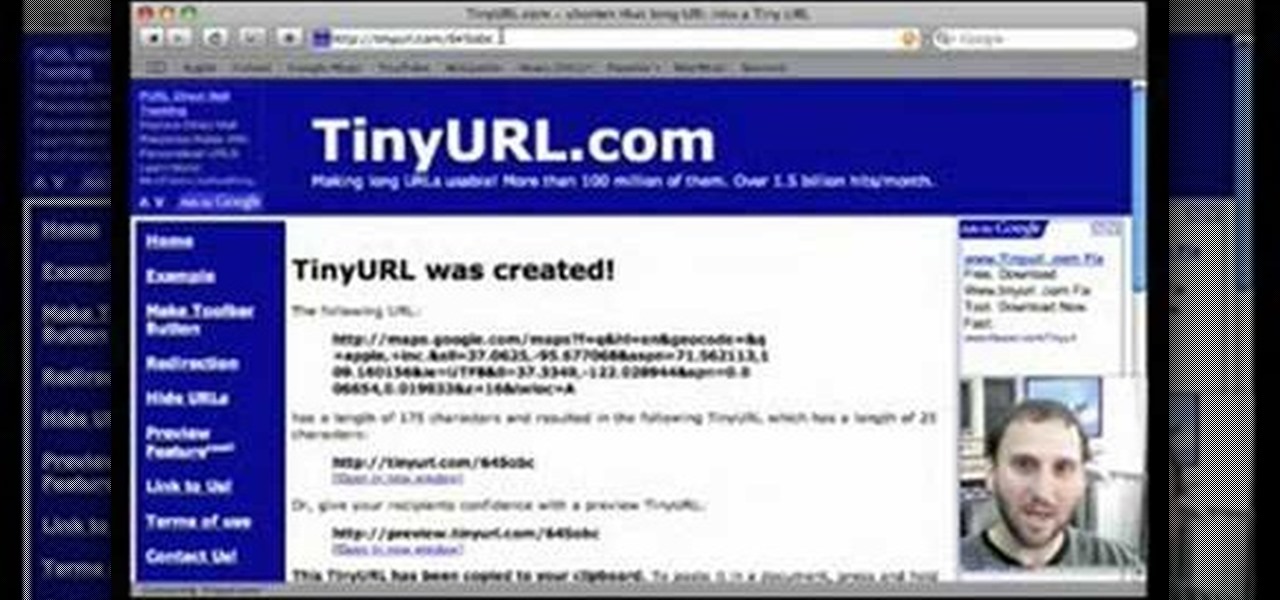
If you like to share websites via email, are a writer who needs to share email in her stories, or just need to make a quick written note of a website address, you need to know how to use web address shorthand. Some URLs can be hundreds of characters long and therefore too tedious to reproduce in writing. To make an easier-to-communicate link, you'll need to use a URL minimizer, like TinyURL. Learn how with this address-minimizing how-to!

In this tutorial, Gary Rosenzweig of MacMost.com takes a look at two tiny, but nevertheless very useful, Web services. The first, tinyurl.com, will take a long Web address and shorten it to make it easier to send in email. The second, http://tinymail.me, will hide your email address. For more information consult this great how-to.

A short tutorial on how to use the ip deny manager to deny the access to website from particular IP address using cPanel. This Video is provided to you by scandicsoft,(wwww.scandicsoft.fi)

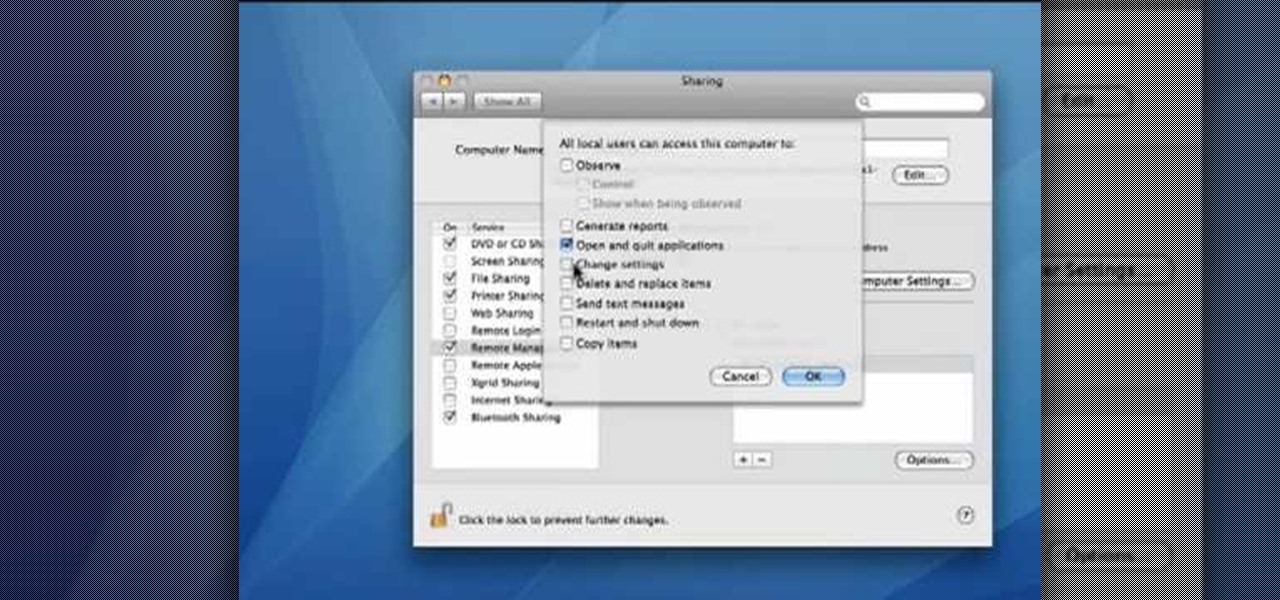
This video demonstrates how to set your Mac up to accept VNC connections.First we open up the "system preferences". Double click on Sharing and then go down to remote management and check this. We can see some options . Check the options Open and quit the application, Change settings, Delete and replace items, Send text messages, Restart and shutdown and Copy items. Then select "OK". Over here we can see "allow access for" and check "only these users". Remote management is now On. We can mana...

Check out this instructional language video to learn how to address someone in Russian. Learn basic Russian grammar with Viktor Dmitriyevich Huliganov in his 2nd lesson. Some other objectives in the lesson include 1a verbs and common adverbs. Watch this tutorial video that is great for language nerds and advanced Russian speakers who need to polish their skills or looking to improve their proficiency in Russian.

SSH, or the secure shell, is a way of controlling a computer remotely from a command-line interface. While the information exchanged in the SSH session is encrypted, it's easy to spy on an SSH session if you have access to the computer that's being logged in to. Using a tool called SSHPry, we can spy on and inject commands into the SSH sessions of any other user logged in to on the same machine.

UnrealIRCd is an open-source IRC server that has been around since 1999 and is perhaps the most widely used one today. Version 3.2.8.1 was vulnerable to remote code execution due to a backdoor in the software. Today, we will be exploiting the vulnerability with Metasploit, examining the underlying code to understand it, and creating our own version of the exploit in Python.

Websites are often misconfigured in ways that allow an attacker to view directories that are not ordinarily meant to be seen. These directories can contain sensitive information such as private credentials or configuration files that can be used to devise an attack against the server. With a tool called Websploit, hackers can scan targets for these hidden directories without difficulty.

Transferring hundreds of screenshots, webcam recordings, keystroke logs, and audio recordings between your VPS and a local Kali machine can be tricky. Services like Dropbox don't always have the best privacy policies and suffer data breaches just like any other website. To mitigate these risks, we'll use a secure, open source, and decentralized alternative.

While there are a variety of privacy-focused search engines available like StartPage and DuckDuckGo, nothing can offer the complete trust offered by creating one's own search engine. For complete trust and security, Searx can be used as free metasearch engine which can be hosted locally and index results from over 70 different search engines.

Having your home and work addresses set in Apple Maps makes them incredibly easy to navigate to no matter where you're located. If you move to a new house, stay in a hotel or resort while vacationing, report to a different office, or have multiple job sites to visit regularly, updating these addresses isn't only straightforward — there's more than one way to do it.