This demonstration of a Pakistani Recipe shows the preparation of khakina which is an egg chutney. For this you will need a tomato, onion, red chili powder, black pepper, salt, eggs, cumin, green chili, coriander and oil in the mentioned amounts. Add cumin to a pan with oil followed by onions, chili powder, salt and the tomatoes as indicated and cover it for a while. Add in the red chili and eggs and mix it around. Add the black pepper followed by chili and coriander at the end. Take the pan ...

Custom optioned installation includes the following: Copy the files to an external hard disk before starting your installation, then you will reinstall your programs by hand by using the windows easy transfer and transfer the data into the hard disk.

Ever had your grandmother or grandfather say they miss the better days? Well if you follow the steps on this video you will see why and the reason why the 1940's and 1950's were years for glam. Drawing from inspiration from Drew Barrymore's character in Grey Gardens, you can achieve that truly glamorous looks that the mid 20th century woman personified. Don't think that just any makeup and eyeliner will do, closely follow the onscreen guide. Just follow the on screen guide and you will look f...

This video shows how to prepare flavorful and delicious grilled pork chops. Steps to follow:

Drive your way to success on The Saboteur for the Xbox 360. You need to floor the pedal in order to follow Dierker in the sixth mission in the Prologue: A Sunday Drive. It's payback time. Hop into the car with Jules and follow Dierker. Don't get too close to him or his paranoia meter will rise. If it fills up you will be caught and fail the mission. Likewise, if you loose sight of Dierker for too long you will fail the mission. Follow Dierker, just don't follow him too closely. He will lead y...

Studying to be a nurse? Then follow along with this nursing how-to video to learn how to start an IV on a live person. Starting an IV is an important and common part of a being a nurse. Follow along with this video to learn the proper technique and procedure for starting an IV line. Before starting, always make sure to double check your the doctors orders and have your materials handy.

Farmington (MN) HS head softball coach Heather Ballstadt demonstrates a drill for hitting, with a flat volleyball. Follow along for some essential hitting skills in softball. This flat volleyball drill is very easy to do. It allows for a strong follow through after you make contact with the ball. Try doing this hitting drill with a flat volleyball at home.

Created by Houdini Product Specialist Stephen Tucker, this crash course series focuses on the concept of Smooth Particle Hydronamics and how they work within Houdini. The following videos on Particle Fluids continue working with fluid dynamics in Houdini 9.5 and assume that the viewer is relatively familiar with how dynamic simulations work, or have been following along through the series. The basics are still covered including creating water from an object but also include more conceptual si...

Exterior lighting can add to the beauty of your home. Watch this how to video and wire exterior lighting yourself following these guidelines and safety tips. Before beginning any outdoor wiring project make sure to check with local utility companies and follow outdoor wiring codes for your area.

This is a tutorial on how to crochet a pen holder. This is a project that beginners should be able to follow. You will need a tin can, two colors of yarn, and a crochet needle. Follow the visual guidelines, accompanied by written instructions.This method works with all kinds of pen holders, baskets and containers. Have fun crocheting your own variations.

When you carry your baby in a sling it is very important to follow safety guidelines. This will ensure that you and your baby are safe. Watch as our host shows you to too support your baby while he or she is a sling.

In this golf lesson video, golf instructor Steve Bishop discusses some tips on how to perform a proper release and follow through of the golf club in a full swing.

Follow these steps to apply liquid eyeliner with ease.

Note that is always best to try and avoid a hangover in the first place by pacing yourself and drinking lots of water before sleeping. But if you find yourself hungover follow our directions for a faster route to feeling better.

Learn how to work on your back spin and follow-through with the help of this terrific free-throw basketball drill.

Learn how to play the soccer drill "follow the leader" in order to improve ball control. Keep your head up and stay as close as possible to the player in front of you.

Before hunting season you should spend some time in the woods tracking deer and wild hogs. This video discusses following a deer or wildlife trail.

If you're looking to improve your browsing experience, then a VPN is the right way to go. If you're tired of censored or geographically blocked sites and wary of companies selling your data, then a good VPN can be your answer to a problem that limits every aspect of your experience online.

There are so many things in place that make browsing the internet difficult. From geographical walls to malicious software and spying — there's a lot to consider any time you do the most basic of functions online. VPN.asia: 10-Year Subscription is a VPN that can streamline your security process and make browsing the web so much easier, and right now, it's on sale for just $79.99.

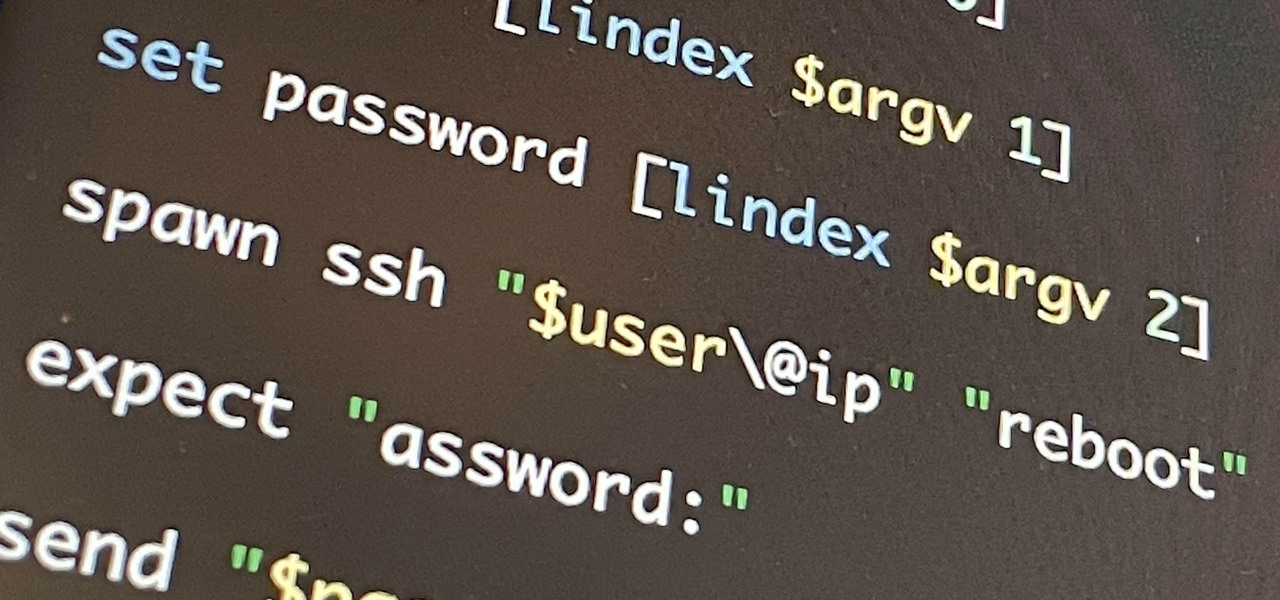
If you're getting into automation, Bash scripting is usually the way to go. However, there are a couple of limitations, and one of them is logging into another device like a Raspberry Pi and running a script automatically. To help in those situations, we're going to automate delivering an SSH payload with an "expect" script.

The first step to getting your life together? Getting your online security together. After all, security when you're shopping, video calling, and more means more than ever in a digital age when anyone can copy your info or try to pose as you on the web. This Premium Privacy Bundle featuring Zenmate and StartMail will give you a secure VPN and encrypt your emails, all at a bundled price. The security duo is on sale for 60% off for a limited time, which means it's just $44.99 (regularly $113).

Now that more and more people are working on their personal computers and smartphones as opposed to their work computers as a result of the coronavirus outbreak, hackers are having a field day. Unencrypted home networks and public WiFi connections make it incredibly easy for cybercriminals and even government agencies to access everything from your browsing history to your banking information, and a Virtual Private Network (VPN) is the only way to stop them.

Although it's always been important to safeguard your data and private information in the digital age, privacy has recently taken on an entirely new meaning.

There are many considerations to make when choosing a web hosting plan. Storage space, performance, security, and reliability all matter. The cheapest option isn't always the best idea.

Celebrities and influencers learned how to leverage Instagram's platform to build their brands. While some effortlessly amassed a following, many had to do the legwork to reach a vast audience. Understanding their secrets will help you grow your own following.

A macOS computer can reveal a lot of information about the owner, including which Wi-Fi network they have permission to access. With an Arduino-based attack, we'll use a five-dollar setup to inject a rogue Wi-Fi network and steal the list of trusted Wi-Fi networks, allowing us to see where the computer has been.

It's new phone season — new handsets are releasing every few weeks, we're seeing endless software updates, and the holidays are right around the corner.

As excitement looms for Apple's annual parade of pomp and circumstance for its latest lineup of iPhones, some hidden hints in an internal build of iOS 13 has Apple enthusiasts salivating for what Cupertino is testing in the AR wearables realm.

After months of back and forth, ZTE is finally making their return to the United States. The last phone the Chinese company released here was the Axon 7 Pro, a low priced flagship phone that competed well against the OnePlus 3 and 3T at the time. Its successor is the Axon 10 Pro, which adopts the same strategy.

One of the most common web application vulnerabilities is LFI, which allows unauthorized access to sensitive files on the server. Such a common weakness is often safeguarded against, and low-hanging fruit can be defended quite easily. But there are always creative ways to get around these defenses, and we'll be looking at two methods to beat the system and successfully pull off LFI.

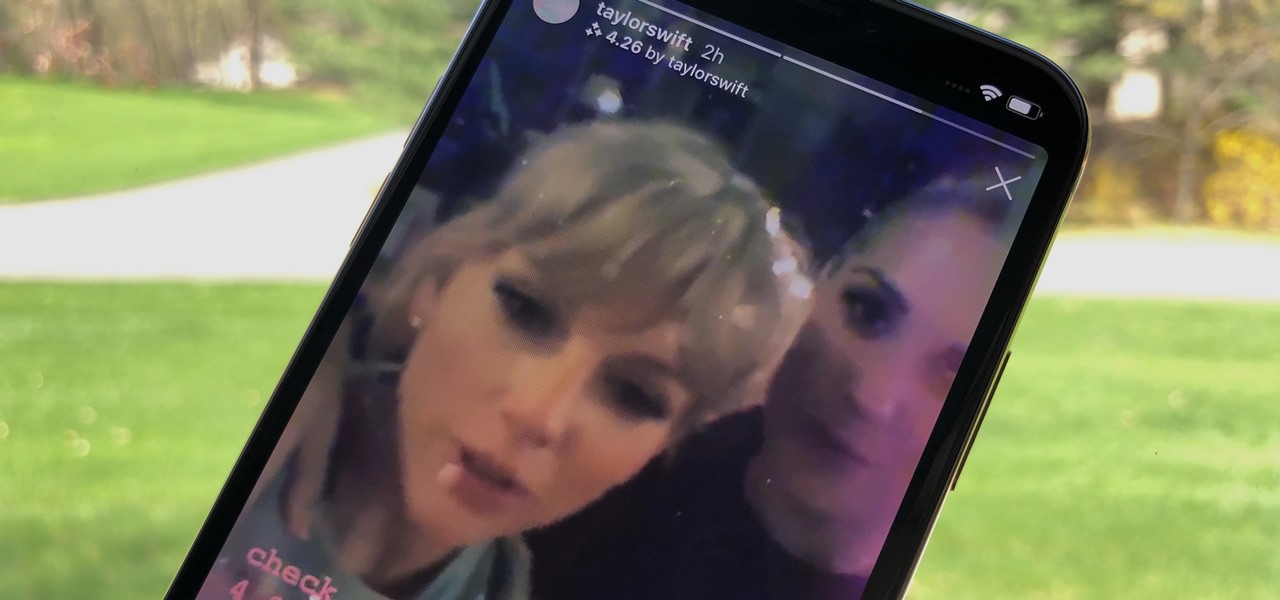
Is there a bigger name in pop music than Taylor Swift right now? Her 116 million followers on Instagram would probably argue, "No." As such, if you're one of these many followers, you might have seen Taylor advertising a new "4.26" filter on her story. Problem is, there's no clear instruction for actually using the filter. That's where we come in.

When setting up a Raspberry Pi, it's easy to overlook changing the default password. Like many IoT devices, the Raspberry Pi's default Raspbian operating system installs with a widely-known default password, leaving the device vulnerable to remote access. Using a tool called rpi-hunter, hackers can discover, access, and drop custom payloads on any weak Pi connected to the same network.

Websites and web applications power the internet as we know it, representing a juicy target for any hacker or red team. TIDoS is a framework of modules brought together for their usefulness in hacking web apps, organized into a common sense workflow. With an impressive array of active and passive OSINT modules, TIDoS has the right instrument for any web app audit.

As I've mentioned in recent days, it was refreshing to discover that Microsoft's HoloLens 2 stage production was every bit as accurate as presented (check out my hands-on test of the device for more on that).

The new iPhone XS and XS Max have more issues than just their hefty price tags. Customers have only had the phones for a handful of days, but some are already complaining of cellular and Wi-Fi connectivity issues on both models. If your experience is the same on your XS or XS Max, there are steps you can take to get your iPhone reliably back online.

Using Netcat to backdoor a macOS device has its short-comings. If the compromised Mac goes to sleep, the Netcat background process will occasionally fail to terminate correctly; This leaves Netcat running infinitely in the background and the attacker with no new way into the device. As an alternative, we'll use the lesser-known Tcl shell which can handle abrupt backdoor disconnections.

As Android bug bounty hunters and penetration testers, we need a properly configured environment to work in when testing exploits and looking for vulnerabilities. This could mean a virtual Android operating system or a dedicated network for capturing requests and performing man-in-the-middle attacks.

If you're using a mobile device, it's a pretty safe bet that your apps are sending lots of information back and forth from their servers. To make sure there is no inappropriate data collection going on, it's worth setting up a web proxy to spy on this traffic, so you know exactly which apps are "phoning home" and when.

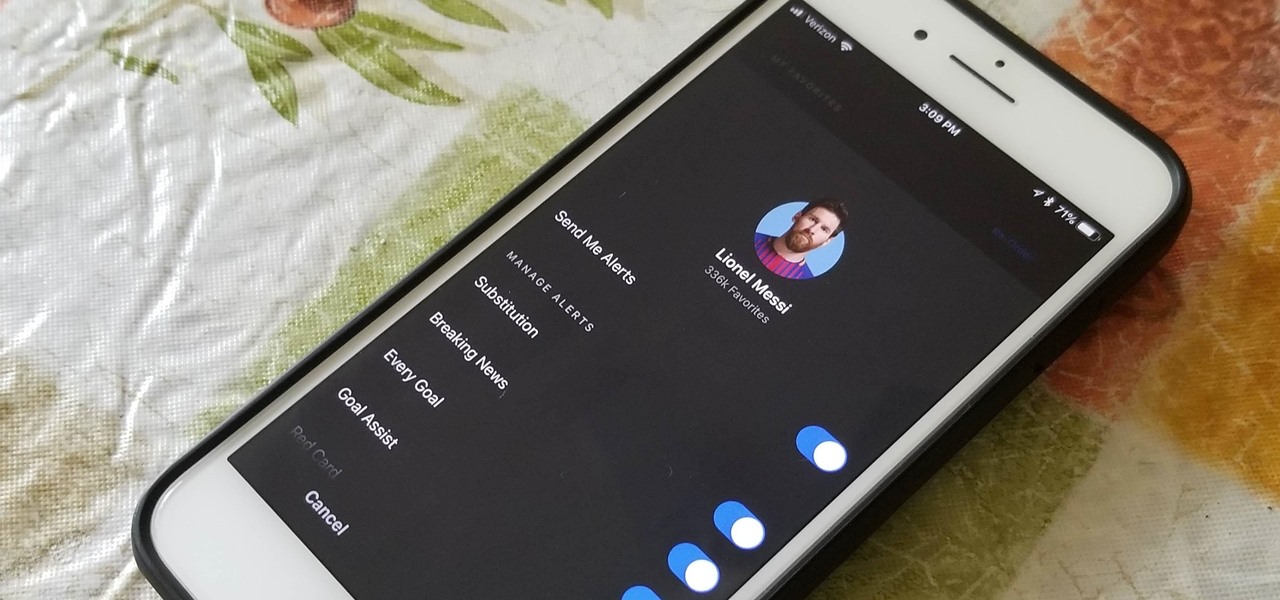
With the World Cup in Russia fast approaching, you're probably wondering how to keep track of your country (unless that country is the USA). While there are a ton of apps that do just that, there's one that stands above the rest if you're looking for World Cup coverage — and it's not ESPN, Yahoo, or CBS.

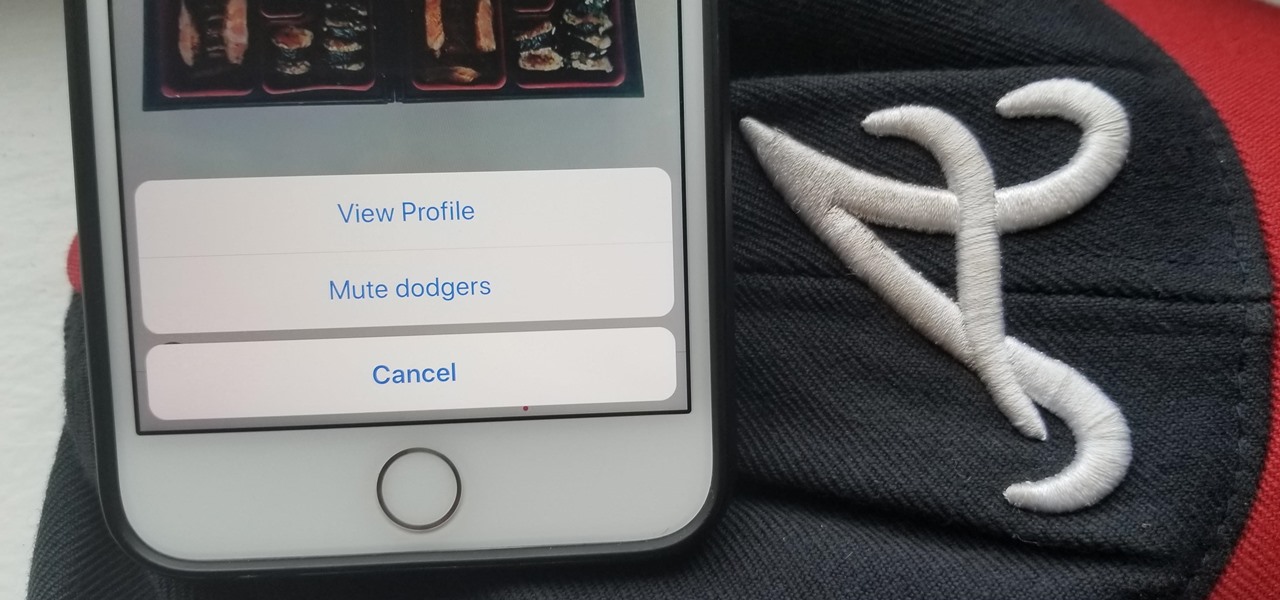
Instagram integrated Stories back in 2016, and it flew right by Snapchat as a whole, becoming a bigger success itself than the whole entire Snapchat app. Still, the constant bombardment of information can be tiring in Instagram, so much so that you may want to mediate what Stories are shown to you. Fortunately, there's a way to do just that — without unfollowing accounts or hashtags.