A convincing domain name is critical to the success of any phishing attack. With a single Python script, it's possible to find hundreds of available phishing domains and even identify phishing websites deployed by other hackers for purposes such as stealing user credentials.
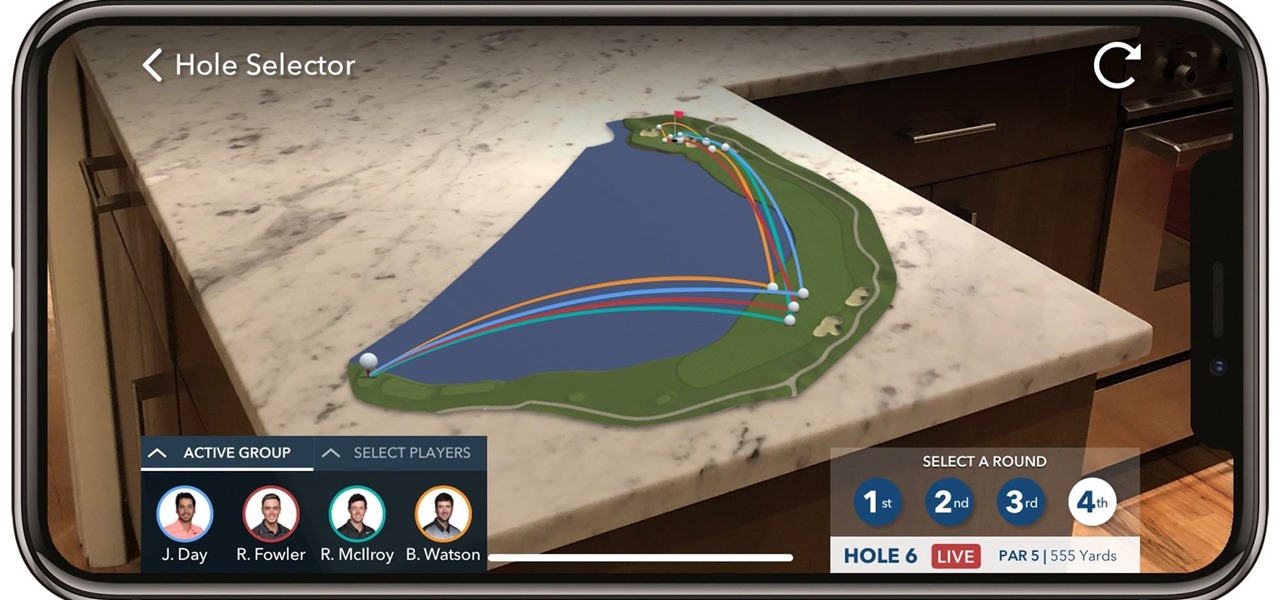
If you're a golf fan who can't attend the Arnold Palmer Invitational in person, you can still follow the next stop on the apparent Tiger Woods comeback tour in augmented reality with an iPhone or iPad.

In the previous article, we learned how to set up our VPS, configure our PHP server, and developed an in-depth understanding of how the payload works. With all that taken care of, we can get into disguising our payload to appear as an image and crafting the note in the greeting card being delivered to our intended target.

In just a few months, Binance has experienced explosive growth, overtaking its rivals to rank among the top three cryptocurrency exchanges in the world by trading volume. Without a doubt, Binance is now among the best sites for trading alt-coins like Ripple (XRP), Stellar (XLM), and NEM (XEM) to name a few.

Google just bought a huge chunk of HTC for $1.1 billion. They're bringing in around 2,000 employees, mostly from the hardware division, and these folks will presumably work under hardware chief Rick Osterloh. There's a massive patent portfolio involved, too, so stop me if you've heard this before — Motorola, anyone?

Recently, I ran across SecGen, a project which allows a user to create random vulnerable machines. I absolutely love vulnerable machines, since a vulnerable VM is a safe and legal way to practice hacking tactics, test out new tools, and exercise your puzzle-solving skills.

I spent just about my entire weekend trying to break the 800, 900, and 1,000 levels of Instagram — because it's a game, y'all — by playing around with my follower count. I shamelessly manipulated my IG account in such a way that was extremely time consuming and left many of my friends pretty pissed off at me as I spent most of my time glued to my phone. (Sorry, friends. I know I'm obsessed.)

While the USB Rubber Ducky is well known by hackers as a tool for quick in-person keystroke injection attacks, one of the original uses for it was automation. In this guide, I'll be going the latter, explaining how we can use it to automate Wi-Fi handshake harvesting on the Raspberry Pi without using a screen or any other input.

UPDATE 5/12: According to Bloomberg, it looks like the merger is on. Anonymous sources claim discussions have already begun about consolidation. Looks like there might be a new 5G powerhouse after all.

In five short years, three generations of ultra-low-cost Raspberry Pi devices have challenged the boundaries of what a person can do with a $35 computer — especially with Kali Linux.

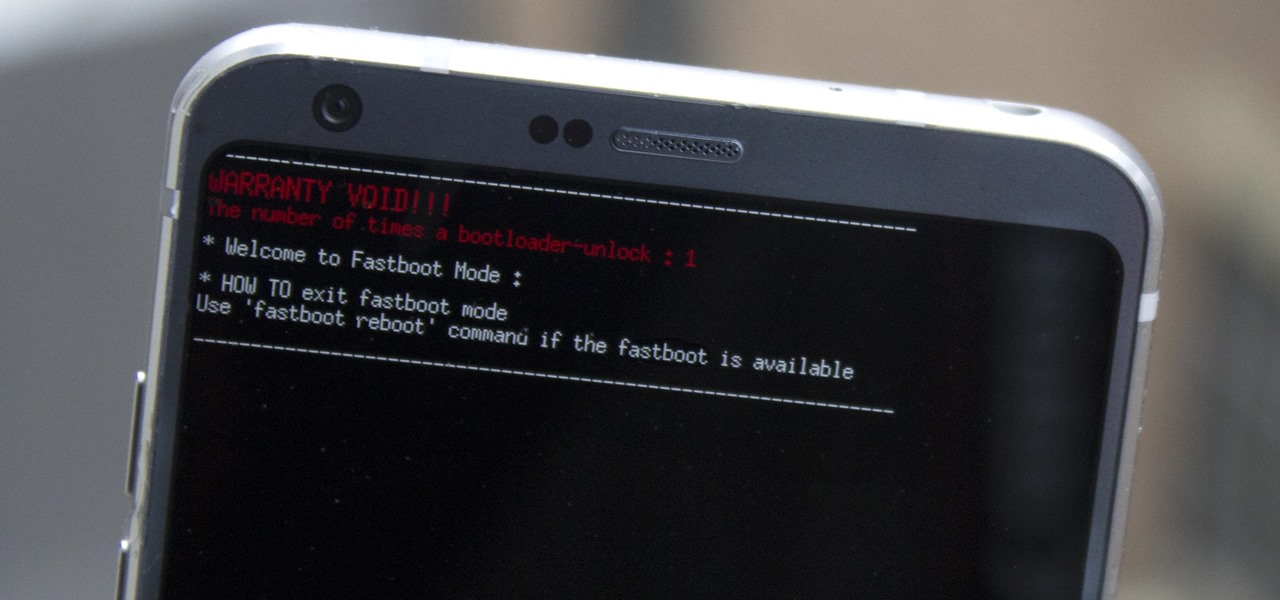
Preorders for the LG G6 have all been fulfilled, and the phone has been up for grabs at local cell phone providers for three weeks now. However, not every LG G6 was created and released equally. The T-Mobile variant of the LG G6 features an unlockable bootloader, while most other North American variants come with a tightly locked down bootloader, which effectively limits the full potential of your brand new fairly expensive phone.

Chrome version 56 is here to help you stop accidentally clicking ads when you're scrolling or tapping a link in a webpage on your phone. That's right, annoying page jumps while a site's still loading will finally come to an end with this new update.

For a long time, Apple has kept the upper hand on Android as far as app revenue is concerned. However, this tradition looks likely to change this year, as Android's app sales are expected to surpass Apple's.

Today is the day you've been waiting for. At 9:00 a.m. PDT (12:00 p.m. EDT), Google announced a number of new products, including the new #MadeByGoogle Pixel smartphones and the Daydream VR headset.

As first reported by Korean media outlet Yonhap News Agency, Samsung has issued a global recall for all of its Galaxy Note7 models (except China, it seems). This unprecedented move will surely do serious damage to the Note brand, and even Samsung itself.

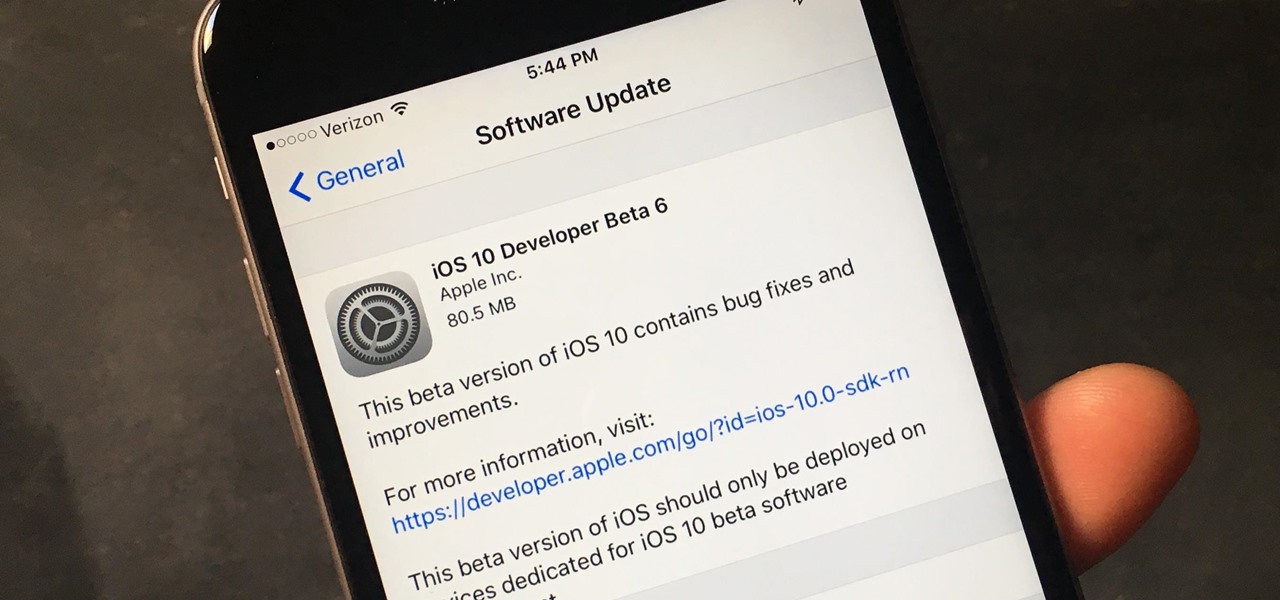
Apple has been aggressively smashing bugs with its last few updates to iOS 10, so it seems like all of the major work is done. With the iPhone 7 release date approaching fast, it's a good sign that the only remaining hurdles are relatively minor and cosmetic tweaks (though they still need to add the song lyrics they showed off a few months ago).

Last year's inaugural Amazon Prime Day may have been a bit of a bust, but the online retail giant seems to be making up for it this year with some killer deals.

Google switched things up this year by releasing a developer version of Android N far ahead of I/O, but that's not the only convention they've done away with this year. For the first time, Google will accept name suggestions from the public.

Hello people, I'm back for Part-3. In this part, as promised, we are going to create a client program and then we are going to test it with our server program made in Part-2.

Welcome back my, tenderfoot hackers! Many people come to Null Byte looking to hack Facebook without the requisite skills to do so. Facebook is far from unhackable, but to do so, you will need some skills, and skill development is what Null Byte is all about.

Welcome back, my hacker novitiates! If you have been following this new Snort series, you know that Snort is the world's most widely used intrusion detection/protection system. Now a part of the world's largest network equipment company, Cisco, it is likely to be found everywhere in one form or another. This makes a compelling argument for learning how to use it, as it will likely be a necessity in any security-related position.

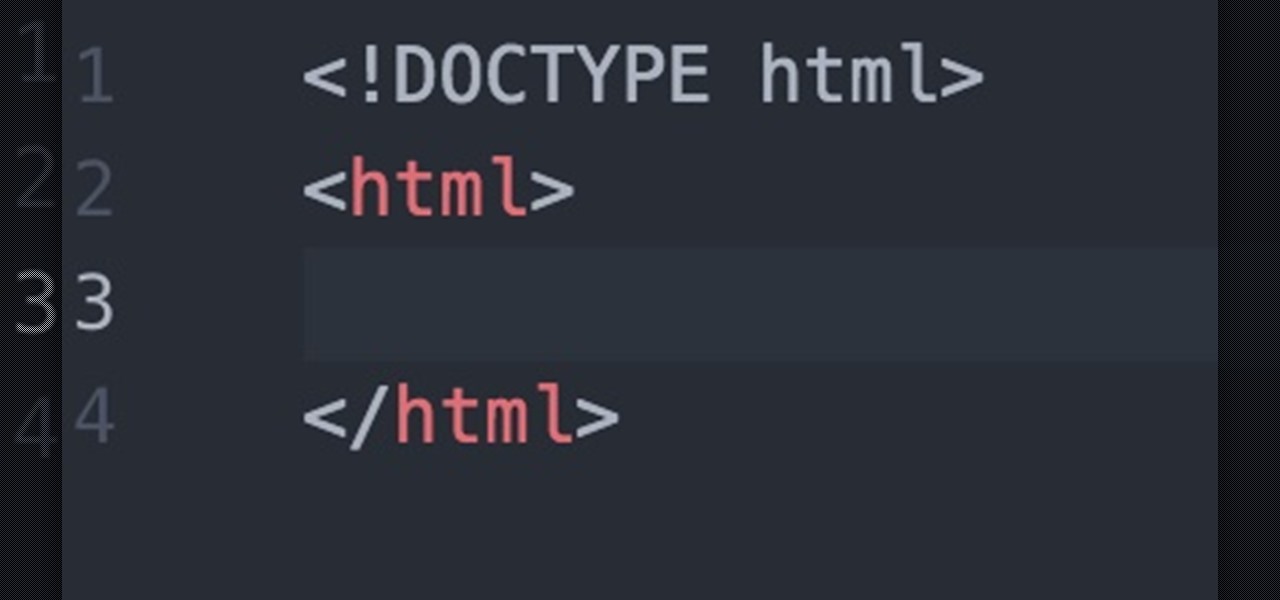
Hello fellow Null-Byters! In this "tutorial" we will be going basics of HTML. In the next tutorial, we will be going over CSS and then apply JavaScript.

Welcome back, my novice hackers! More and more, the world is turning to and adopting the smartphone platform as the digital device of choice. People are not only using smartphones for voice communication, but also web services, email, SMS, chatting, social networking, photography, payment services, and so on.

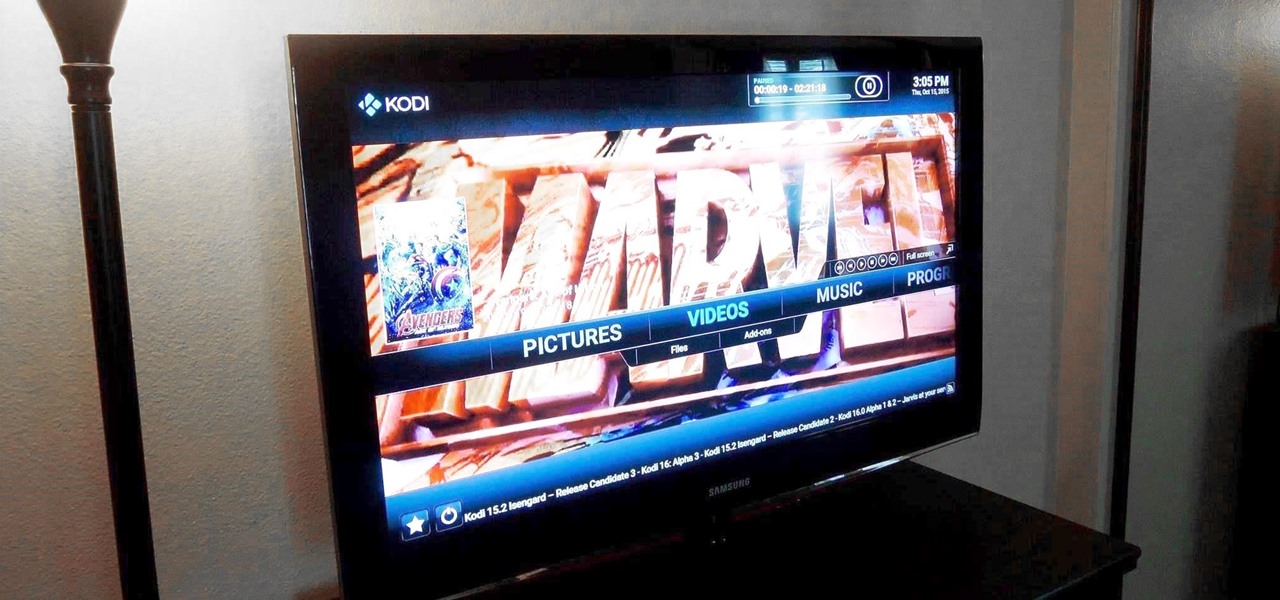
Amazon thinks that by simply removing an app from their Appstore, that they will stop users from accessing it. But with Android OS powering their Fire TV Stick and Fire TV, there really isn't anything they can do to prevent us from sideloading an APK onto the streaming media devices.

It might be difficult to admit, but a lot of us are probably guilty of lurking on Instagram profiles, whether it be an ex you've been keeping tabs on or someone cute you literally just met.

Welcome back, my greenhorn hackers! Many new hackers come from a Windows background, but seldom, if ever, use its built-in command-line tools. As a hacker, you will often be forced to control the target system using just Windows commands and no GUI.

Welcome back, my hacker novitiates! There are many ways to hack databases, and most of these techniques require SQL injection (SQLi), which is a way of sending SQL commands back to the database from a web form or other input. In this tutorial, we will use SQL injection to get access to the underlying server. So instead of getting access to the database and its data, we will use the database as an intermediary to gain access to the underlying server.

WPA Enterprise is widely used in large corporations as it offers individual and centralized control through a server that authenticate the users (RADIUS server). In this tutorial I will show you how to break the barrier and obtain the user credentials.

While it seemed like jailbreaking methods were always one update behind the current build, the team over at Pangu have already released a jailbreak tool for iOS 9, and it works up to iOS 9.0.2. It is not available for iOS 9.1 through 9.2 yet, but we will update this guide when they are ready.

In the last iteration of how to train your python, we covered basic string manipulation and how we can use it to better evaluate user input. So, today we'll be covering how to take user input. User input is very important to scripting. How can we do what the user says if we can't tell what the user wants? There are multiple ways to take input, we can give the user a prompt and take input from them directly, or we could use flags/switches, and take their input before the script is even execute...

Welcome back, my tenderfoot hackers! A number of you have written me telling me how much you enjoy the Mr. Robot series on USA Network. I am also a huge fan! If you haven't seen it yet, you should. It may be the best show on TV right now.

bObsweep robotic vacuums automatically clean whenever instructed to do so by an owner or because of a pre-programmed schedule.

Welcome back, my tenderfoot hackers! A short while ago, I started a new series called "How to Spy on Anyone." The idea behind this series is that computer hacking is increasingly being used in espionage and cyber warfare, as well as by private detectives and law enforcement to solve cases. I am trying to demonstrate, in this series, ways that hacking is being used in these professions. For those of you who are training for those careers, I dedicate this series.

Welcome back, my hacker novitiates! Eluding and evading antivirus software and intrusion detection systems is one of the most critical tasks of the hacker. As soon as a new exploit is developed and discovered, the AV and IDS developers build a signature for the attack, which is then likely to be detected and prevented.

Welcome back, my tenderfoot hackers! Those of you who have been reading my posts here for awhile know how much I emphasize good reconnaissance. Novice hackers often jump into a hack/exploit without doing proper recon and either fail or get caught. Experienced and expert hackers know that 70-80 percent of a good and successful hack is dependent upon successful and accurate reconnaissance.

Welcome back, my aspiring hackers! Those of you who use Windows in a LAN environment understand that Windows machines can share directories, files, printers, etc. using "shares." This protocol dates back to the 1980s when the then dominant computer firm, IBM, developed a way for computers to communicate over the LAN by just using computer names rather than MAC or IP addresses.

This is a extremely easy to follow tutorial which will allow you to learn to how to build a sugar cane farm.

When the Chromecast first came out about a year ago, developers were quick to find a way to root the streaming device. Google was almost as fast, however, in updating the Chromecast's firmware to close the loophole that this method used.

Welcome back, my budding hackers! We've spent a lot of time learning to compromise Windows systems, and we've successfully compromised them with Metasploit, cracked their passwords, and hacked their Wi-Fi. However, very little time was spent developing ways to extract the information from the system once inside.

Welcome back, my budding hackers! In my continuing effort to build your basic Linux skills for hacking, I want to show you how to build a secure "tunnel" to MySQL.